What is a Ransomware Virus and How does it Operate?
Ransomware is a harmful malware infection that encrypts the files of the infected user and renders it inaccessible. Cybercriminals create it to take advantage of flaws in a victims ’ computers and request ransom money in exchange for the recovery and decryption of the data they encrypt.
Since so many people have essential documents and files on their devices, those infected with a ransomware are compelled to pay the ransom requested by the cyber criminals in exchange for their data.
The majority of the new forms of this file locker malware are impossible to decrypt on your own, and even professionals are having trouble recovering these encrypted files, which is why most individuals are choosing to pay the attackers for their files.
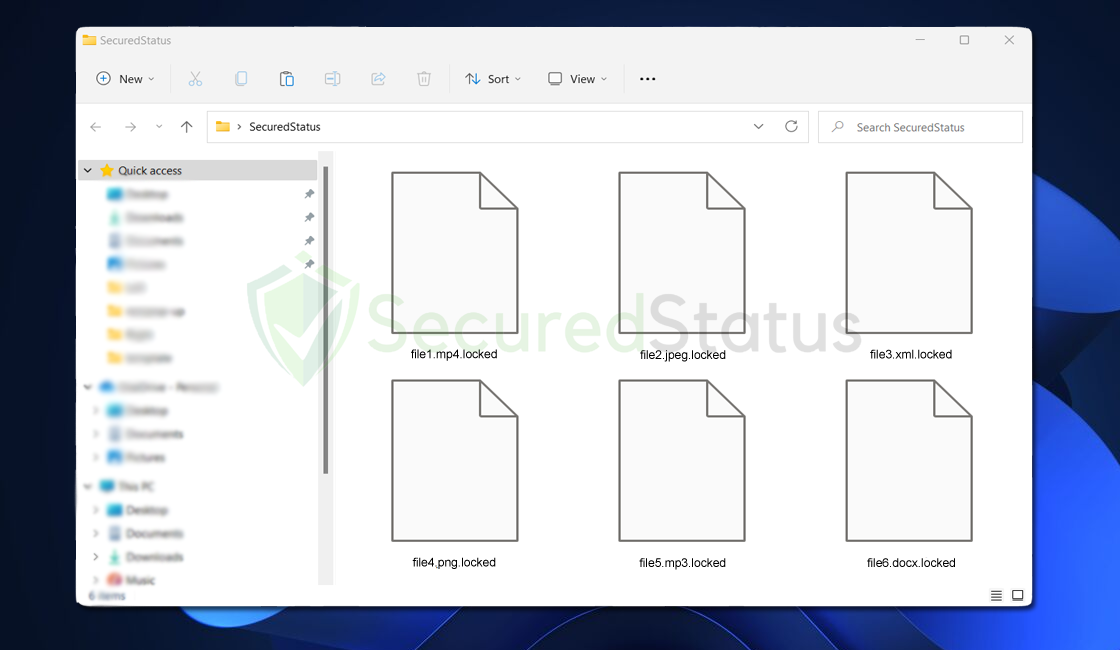
Being infected with a severe virus like ransomware can be extremely damaging to a computer system and its networked devices. It can also migrate from one computer to another via the internet. If a device is infected and linked to a network, the virus can spread to other devices on the same network.
When a computer gets hacked, it’s best to disconnect it from the network as quickly as possible, or at the very least boot it into safe mode with networking.
The Purpose of Ransomware Malware
A ransomware virus encrypts files on affected systems and demands a ransom payment to unlock them. The ransom is usually paid in Bitcoin or other cryptocurrencies to avoid being tracked, and the ransomware operators typically claim that the files will not be released until the ransom is paid.
By encrypting vast numbers of files and demanding large ransom payments, the ransomware perpetrators can make a lot of money. Because the files that are encrypted can be highly valuable in some situations, a hefty ransom can be asked.
After paying the ransom as suggested by the attackers, the victim is given a decryption key that can be used to restore their files.
The decryption key is a one-of-a-kind digital code that decrypts files encrypted by the ransomware virus.
No, because in the case of a ransomware infection, a successful ransom transaction and decryption is not always the case. It’s not just right to put your trust in the people who encrypted the data in the first place. Because doing so may have the reverse effect and cause extra damage to your computer, as well as the data being destroyed entirely.
How is Ransomware Distributed?
All viruses have the same tendency to spread in a similar manner to ransomware viruses. There are several ways a ransomware virus can enter a computer system, however the following ones are the most common ones:
Email Spam Attachments
The most popular and extensively utilized tactic is using spam email attachments. By tricking them into installing malicious software that is attached to the attackers’ email, it tricked the intended recipient. The files are either bundled together or presented in the attachments like papers, videos, and voicemails.
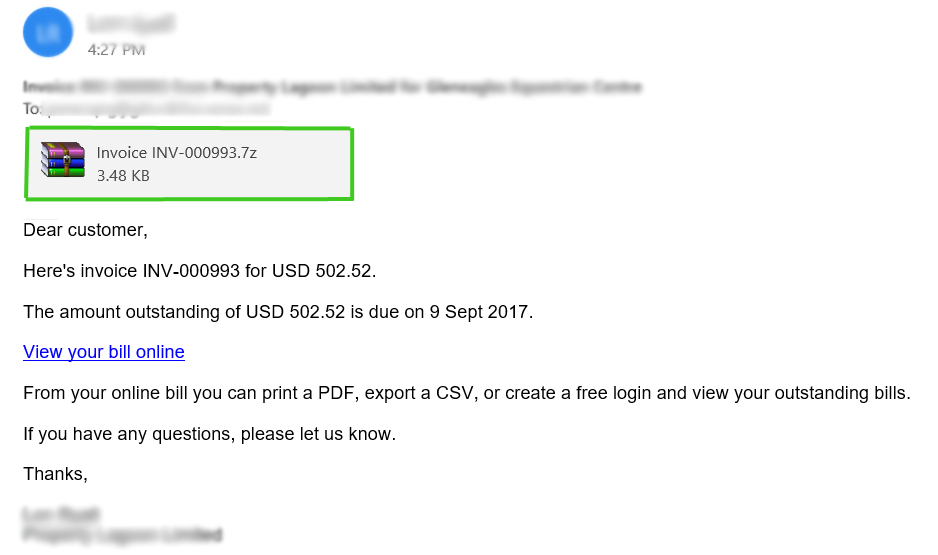
When the victim opens the file, a malicious script infects the machine, starting the file encryption process. In addition to encrypting crucial data, certain dangerous types can also compromise antivirus software, steal confidential information, and spread to other networked devices.
Drive-by Download
When someone accesses a website that has been infected with a malicious script, a random piece of software is downloaded as a result. Once they’ve been clicked, hackers can leverage these weaknesses to gain unauthorized access to targets’ systems.
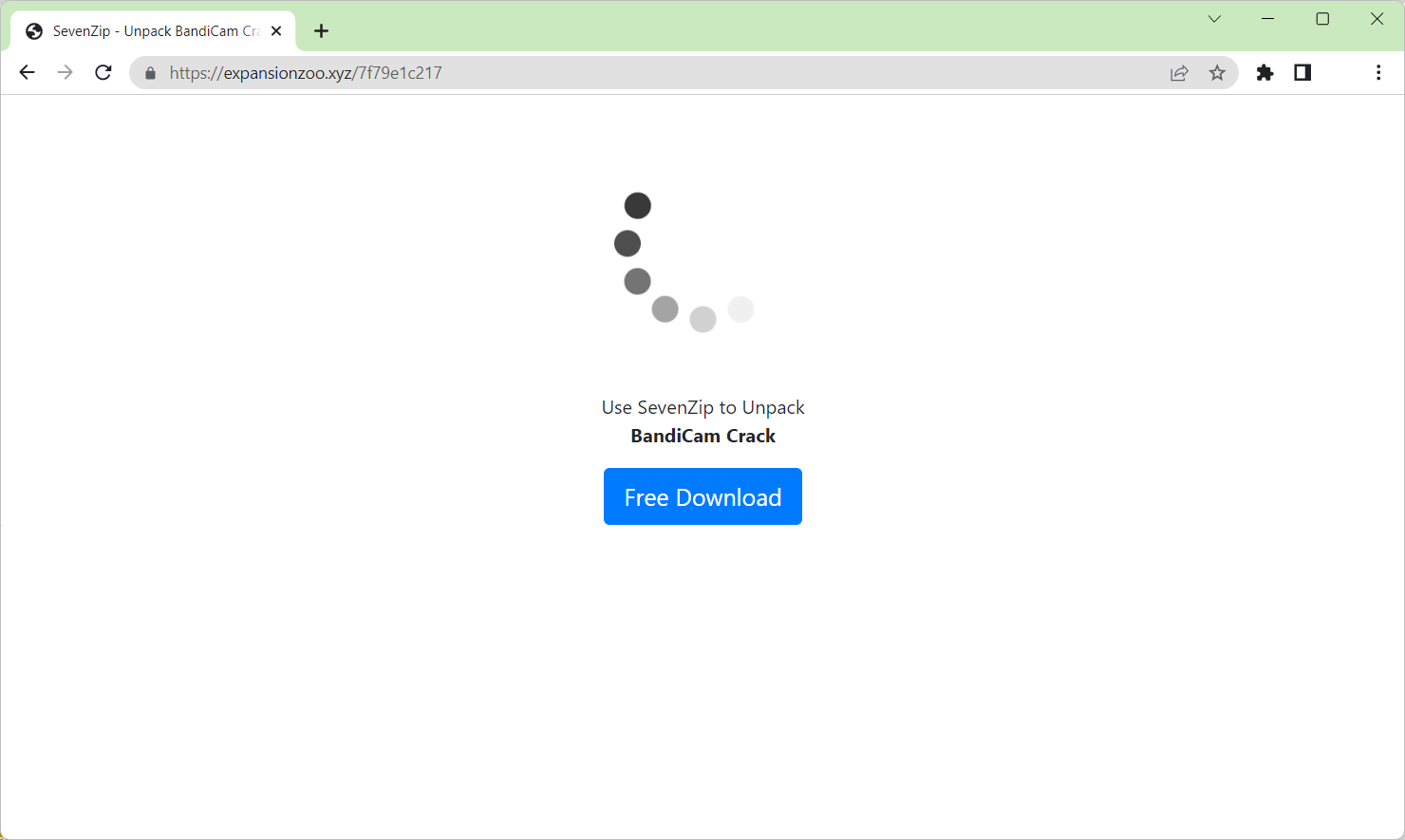
Drive-by downloads are frequently linked to the installation of potentially unwanted programs (PUPs) or adware, but they have also been connected to the infection of consumers with hazardous ransomware.
Infected Torrent Files
Millions of pirates around the world use torrent files to download illegal copies of popular software, pirated music, and movies. You must take care when downloading any kind of file from a torrent site.
Since then, cybercriminals have spread their hazardous software using the torrent community. Torrents are almost certainly contaminated, especially.exe files. Therefore, it’s important to check the file extension while downloading from a torrent site because it’s common to discover that a pirated movie or piece of music is infected with a virus if it’s in the.exe format.
Tens of thousands of people become infected with a ransomware virus every single day. Everyone should exercise caution by avoiding visiting unusual websites, downloading malicious files, and checking their email for attachments from shady senders because the developers of this ransomware use a number of techniques to infect a web user’s machine.
Ransomware Virus Removal Instructions
This procedure will assist you in removing any type of ransomware as well as any dangers related with the malware infection. You can rest assured that the information provided below has been tried and tested.
Step 1: Remove the Virus with Malwarebytes
When dealing with malware, it is much better to rely on an antivirus application because it is much easier to utilize, especially because not everyone on the internet is adept in technology.
One of the most powerful anti-malware tools available is Malwarebytes Anti-Malware. They have some of the best threat detection tools, ensuring that any malicious malware on your computer is completely removed.

In order to download the application while on safe mode, you must have networking allowed in order to use the internet. Unless you have Malwarebytes installed on your computer already, please follow the instructions below:
1 Visit the official anti-malware website or click the button above to download the most up-to-date version of the software that best suits the requirements of your computer. You will also be getting a 14-day trial of the premium program as you download the application for the first time.

2 When prompted to choose between personal and organizational use, click the personal option unless you are downloading it within your company. From then on, follow the installation procedure given on your computer’s setup screen.
3 After following the software setup instructions, wait for the application to finish installing.

4 Once the application is installed, run your first computer scan and wait for it to finish.
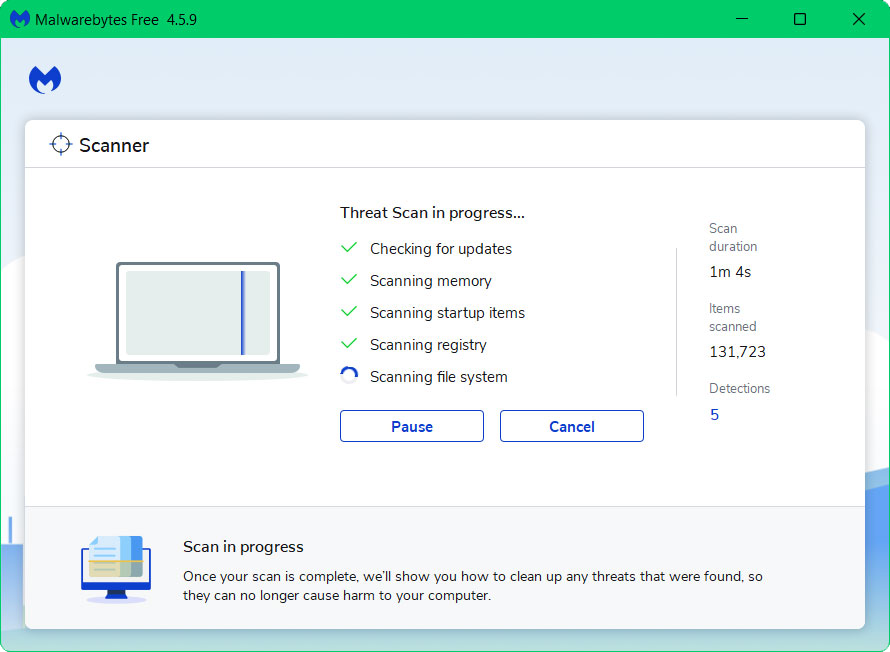
5 All discovered malware on the computer will be displayed on the screen, and you can eliminate them by pressing the “quarantine” button.
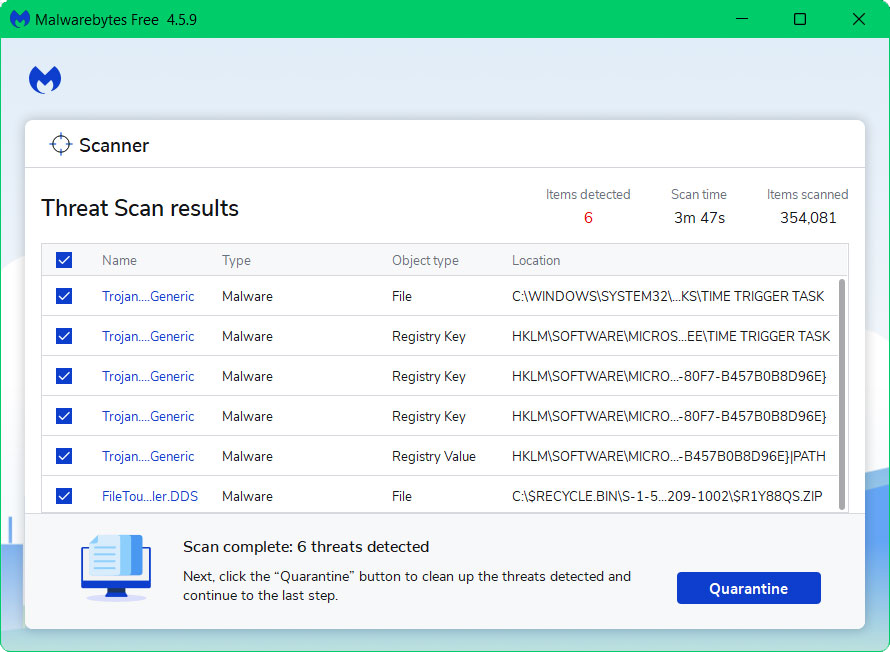
Once the process is complete, the ransomware virus, as well as any other malicious threats found on the computer, should be removed. Activating Malwarebytes Real Time Protection is also recommended, as it will secure your computer and detect potential threats as soon as they surface.
Step 2: Find a Decryption Tool
Finding a working decryption tool for ransomware-infected data may be difficult, if not impossible. Because there may not be much information on a virus that appears to be new, it may take time to create a decryption.
However, you can check Emsisoft’s Ransomware Decryption Tools page on their official website to see if a decryption program for the ransomware in question is available. In addition, you can also try Avast’s Free Ransomware Decryption Tools to see if they offer one that works as well.
Note that these sites may not have one available at the present, therefore you may also want to try the file recovery applications that are shown below.
File Recovery Programs to Try and Use:
Here are programs you may use to restore your files from a ransomware attack. Note that the tools mentioned below does not guarantee the decryption of infected files.
Shadow Explorer
ShadowExplorer is a file recovery program that allows you to recover prior versions of files that have been altered or overwritten. The application accesses the location in which the documents or files are located and retrieves them from there.
For your information, Windows actually saves a copy of the files you updated with its own restore points, but you won’t be able to access them until you have the feature turned on. Restoring your data with a software like ShadowExplorer, on the other hand, can be a lifesaver especially when facing a ransomware virus.
In a matter of seconds, the application will display all of the recovered copies. Whatever sort of file you need to restore, ShadowExplorer will find the overwritten copies in any format. This application is extremely useful since it could simply pull up a backup copy of the infected data and get it back. It would be as if it wasn’t infected at all, as long as there is a shadow copy of the files it could do just that.
PhotoRec
Photo Rec is primarily a photo recovery program. It allows you to recover photographs from a variety of digital devices, including laptops, video cameras, mobile phones, external drives, and more.
The tool can also recover corrupted photos, making it suitable for occasions such as a ransomware attack.
Since corrupted photos can be lost or unrecoverable. PhotoRec comes in handy here. The application is a digital picture recovery utility that allows you to recover photographs and images from a variety of devices, even if they have been corrupted by system or file damage.
The program is open-source and free. It recovers missing files from a system using text-based data recovery algorithms. However, do note that this application cannot ensure that your infected photos will be completely decrypted.
Step 3: Final Precautionary Measures (Optional)
Before returning to normal Windows mode, make sure the computing device is safe and malware-free. You don’t want another ransomware attack to occur once you reboot.
Cybercriminals utilize a variety of methods to obtain access to their victims’ devices; individuals who have recently been hacked should ensure that their device’s security is tight to prevent hackers from gaining access again.
Here are a few things to do to keep the computer safe against another ransomware attack or any other dangerous threats.

Use the Controlled Folder Access Feature
Controlled folder access should be used if you’re running Windows 10 or 11. It helps safeguard sensitive data from malicious threats, such as ransomware malware.
Turning it on will limit access to the specified folders to just those applications that have been given permission to open them. Please follow the procedures below to enable controlled folder access unless you already have it enabled.
1 Open the Windows Start Menu and search Windows Security then click the application.

2 Once the Windows Security application shows up, click on Virus & threat protection from one of the options shown.

3 Scroll down and find the Ransomware protection section, then click the Manage ransomware protection as shown.

4 Turn on the Controlled folder access by toggling it On.

5 From the Protected folders button, you can add the folders you want protected and only apps with permission are only allowed to access it.

Although not every file on the computer can be safeguarded, but all valuable files should be retained and placed in a protected folder. Malware like ransomware won’t be able to infect and encrypt files within a protected folder thanks to the Controlled folder access functionality.
It’s a very helpful feature to have, but you should be cautious about which apps you provide access to protected folders. There may be viruses disguised as genuine programs that could try and take advantage of this, therefore be cautious when giving permission to programs and double-check that they are valid.
![]()
Setup OneDrive for File Recovery
One of the most important precautions, according to many computer experts, is to periodically backup your files so that you have a copy in case of a ransomware attack. The damage would be lessened if files were backed up to a cloud or a USB stick, but many individuals do not make it a routine to back up their files.
After getting hit by ransomware, one would undoubtedly learn their lesson and perform regular backups. Cloud storage is one of the best ways to back up your files because it is accessible from anywhere with an internet connection.
Fortunately, OneDrive has a computer file backup feature, and you should back up your files now as a precaution in case of another attack. OneDrive is preinstalled for Windows 10 and later versions, so if you are using an older system, you have to download the application first (click here).
1 To access One Drive, open the Windows Start Menu and search OneDrive then click the application.

2 Once OneDrive application/website opens up, fill in the required information needed to sign up if you haven’t done it yet.

3 Backup the files that are in Desktop, Pictures and Documents by making sure there is a check mark on the upper right of their icons. Click Continue to proceed with the next steps and finish the introduction.

4 As you can see, OneDrive is a folder and if you want to add more items to safeguard, simply copy and paste that item into this designated folder. Files that are backed up will have a check mark beside them. Those with the cloud icon means that they are only available when there is internet connection.

Once your files are safe, it will greatly limit the chance of being damaged during another malware attack since you can just pull a backup from the OneDrive cloud.
Now you may use your computer once again and boot back to normal mode. Addition to that, you may read below some safety tips on how to browse the internet safely and prevent encountering malicious threats.
Best practices for preventing ransomware infection
Because no one knows what kind of vital data was lost as a result of the infection, a ransomware virus attack is disastrous for both the computer system and the victim. This malware’s primary objective is to encrypt files and demand a ransom payment to decrypt them, as implied by its name.
Paying the ransom encourages online criminals to carry on with their evil deeds as long as they can continue to make money from it. It is better to avoid financial loss even though a victim who pays the ransom would never know what is in store for them.
Here are a few well-known and efficient techniques to prevent a ransomware virus from invading your system if you’ve already been the victim of one or don’t want to do so again:
Have a recent data backup
Maintaining a recent backup is essential since data loss is dangerous, especially during a ransomware attack. Backups are important since data that has been encrypted has a very slim chance of being recovered.
Restoring from a previous backup is the simplest approach to safeguard yourself against ransomware attacks or any other sort of data loss in the future.
In the event of a calamity, backing up your data can help you save time and money. Your most crucial data will be safe if you save backup copies of it in a different location in case something goes wrong with your computer.
Utilizing an Antivirus to protect the computer
Having a reliable and effective antivirus is crucial today. In this day and age, it is impossible to tell what risks are concealed by the internet.
Aside from the great built-in anti-malware application (Windows Defender) that comes with every PC, adding additional anti-virus software would offer stronger defense against dangerous threats.
A decent antivirus program does much more than merely scan for and eliminate problems. As soon as a virus enters a computer, it can find it and track it while also offering real-time security. Antivirus software needs to be set up and updated frequently.
Keep the Operating System up-to-date
The operating system must be updated on all supported machines since it fixes bugs and vulnerabilities. Cybercriminals will need to locate another gap or vulnerability to gain access to a machine because the most recent Windows patch updates fix these flaws. In order to circumvent system protections, ransomware developers typically target security flaws.
If you don’t upgrade your version of Windows, harmful malware may be able to attack your machine by utilizing security holes and system weaknesses that have been resolved in a more current update. If a new Windows patch update is issued, it is crucial to update to the most recent version as quickly as possible.
Final Thoughts
It is better to prevent data loss than to sob uncontrollably once it has happened. Protecting data from this file-locking malware requires understanding how it works and developing a plan to prevent it. You may be confident that if you heed the preceding instructions, you won’t likely ever run across it.


