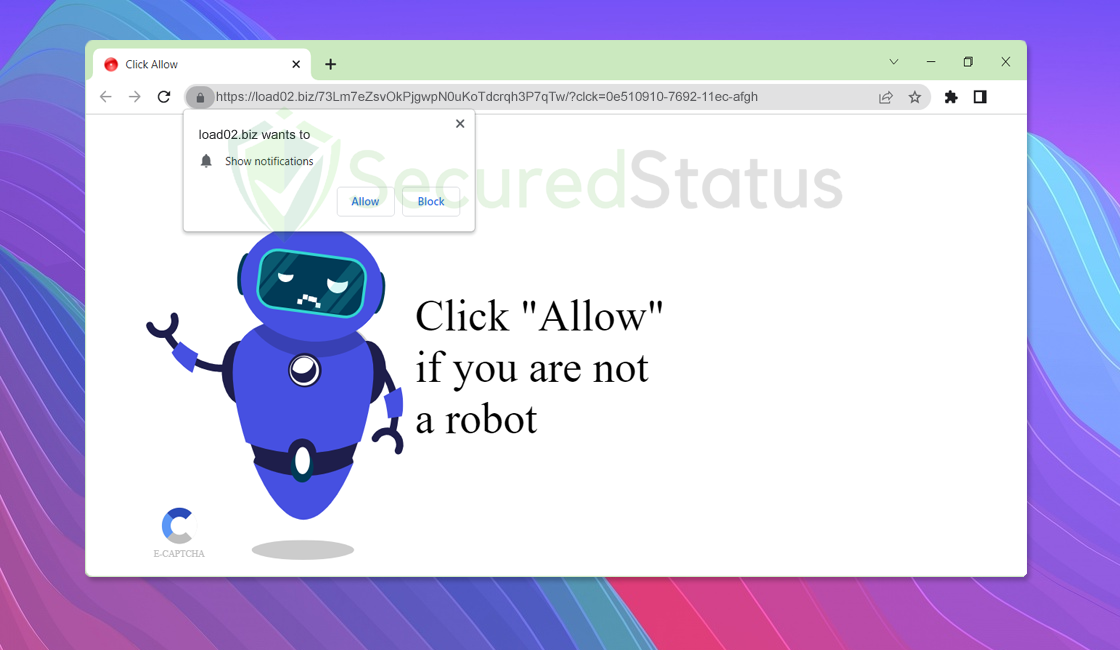
How to Remove Load02.biz Pop-up Ads
Load02.biz is a website that shows unwanted advertisements appearing as web browser notifications. When you first visit this site, you […]

Load02.biz is a website that shows unwanted advertisements appearing as web browser notifications. When you first visit this site, you […]
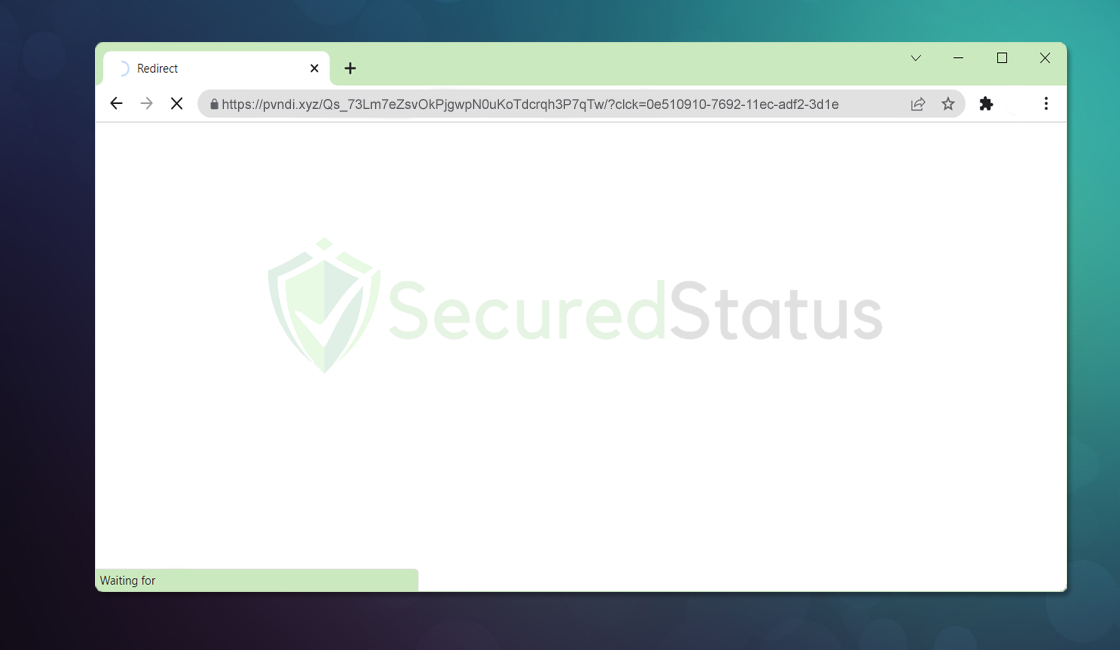
Pvndi.xyz is a domain that is used to lead web users to different websites. When redirected to Pvndi.xyz, users should be […]
G0-gt3-s0me.net is a domain that is used to lead web users to different websites. When redirected to G0-gt3-s0me.net, users should be […]
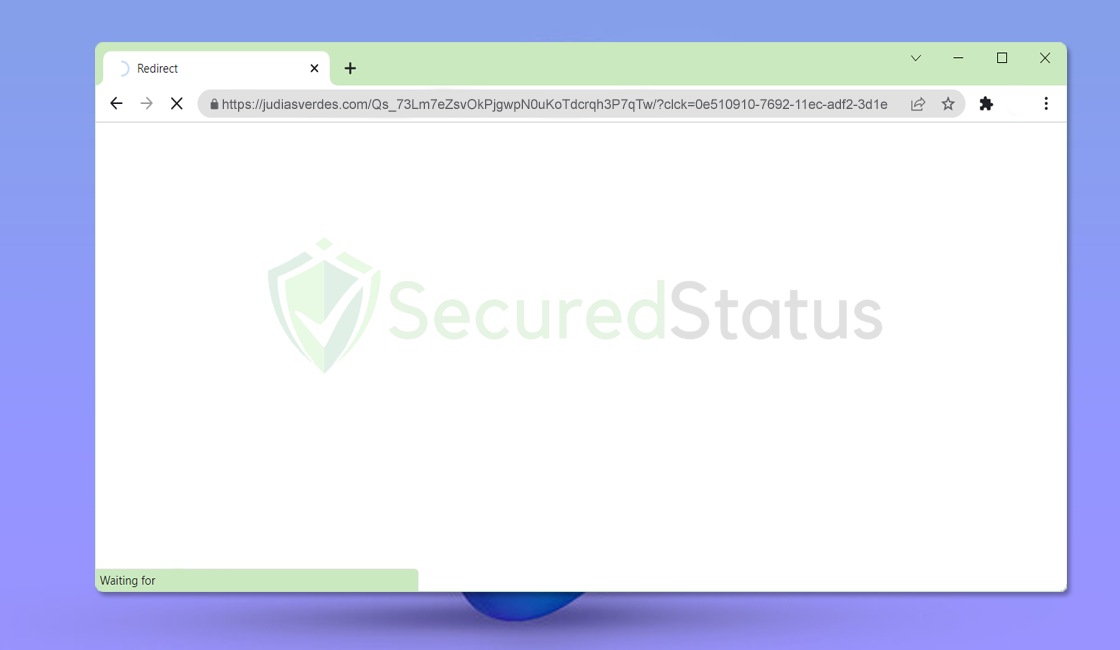
Judiasverdes.com is a domain that is used to lead web users to different websites. When redirected to Judiasverdes.com, users should be […]
Davonevur.exe – What you need to know Davonevur.exe is a legitimate file name used by respected programs, but fraudsters exploit […]
Greenlinecards.com displays invasive adverts disguised as web browser notifications. When you first visit this site, you will be invited to […]
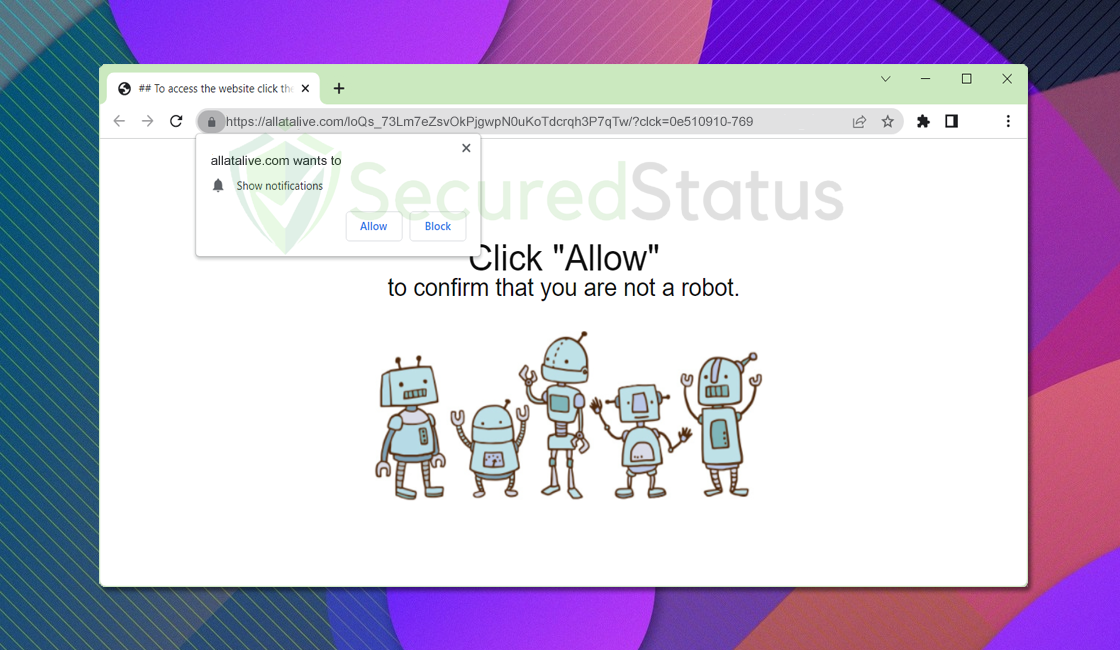
Allatalive.com displays invasive adverts disguised as web browser notifications. When you first visit this site, you will be invited to […]
Gouvevop.com is a dubious website that asks people to complete surveys and forms. Many people have fallen for this type […]
Ademinetworkc.com is a website that shows unwanted advertisements appearing as web browser notifications. When you first visit this site, you […]
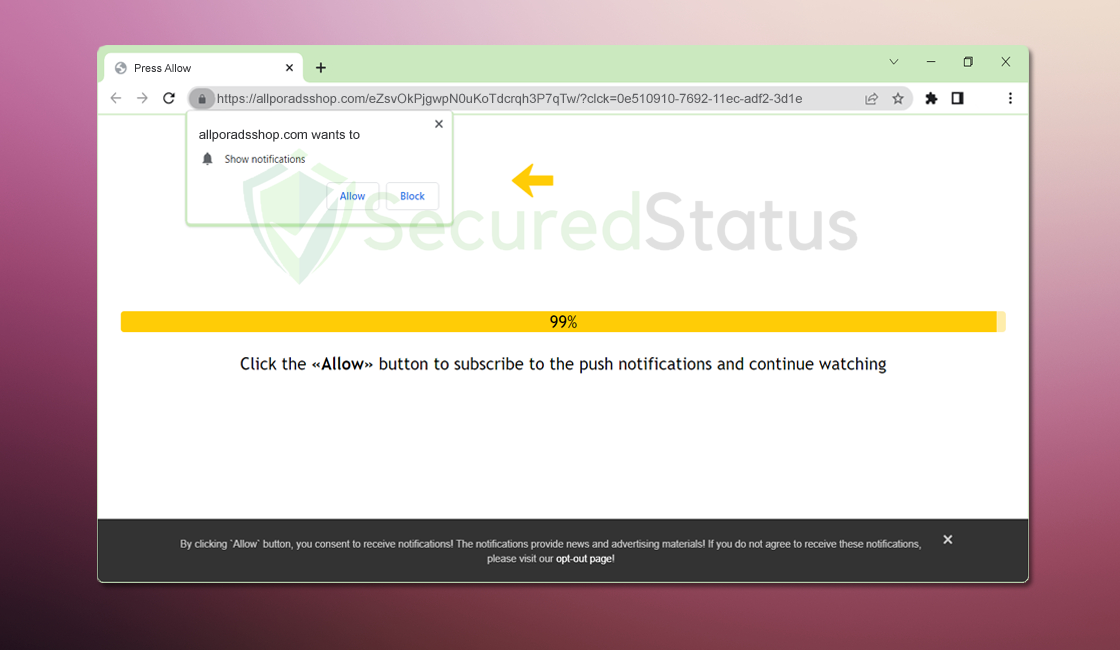
Allporadsshop.com is a website that shows unwanted advertisements appearing as web browser notifications. When you first visit this site, you […]