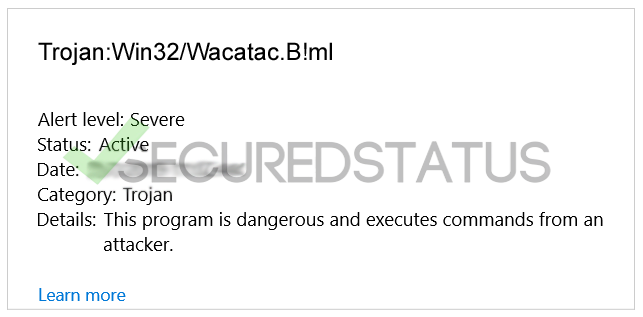
Trojan:Win32/Wacatac.B!ml is the detection name assigned to specific threats exhibiting identical malicious behavior, as identified by antivirus programs.
This category of threat is considered harmful and capable of executing undesirable actions on the compromised computer.
Your antivirus has alerted you of this threat because it discovered the specific malware on your computer during the program's system scan.
These detection warnings should not be taken lightly since it means that your computer is vulnerable and can be exploited by malicious actors.
You should take appropriate actions once your antivirus software notices these types of threats on your device. It is always best to get rid of it before it can do much harm to the computer.
Impact of Trojan:Win32/Wacatac.B!ml on the system
These threats are often acquired through spam emails, infected websites, or by clicking on a link in an email. Once it is installed on the computer system, Trojan:Win32/Wacatac.B!ml will begin to spread across your PC via Windows System files.
Hackers may be able to access all of your data on the computer and take over its operation once they have been deployed on the system.
Threats like these should not be allowed to remain on the computer for an extended period because they may result in irreparable harm.
Users who have their computer infected with the Trojan:Win32/Wacatac.B!ml threat will most likely face the following issues:
- Unexpected issues with the internet connection and certain programs.
- The computer experiencing freezing and performance slowdowns.
- Having trouble accessing or opening documents and files.
- Unwanted pop-up advertisements appear while browsing the internet.
- Increased CPU consumption and the computer experiencing overheating.
These kinds of threats are particularly risky since they can be used to attack unsuspecting users online by stealing their financial information, privacy passwords, and other important data.
Harmful malware detections can damage your computer and user data. As previously mentioned, it is crucial to remove them promptly if you haven't already done so.
Trojan:Win32/Wacatac.B!ml Removal Instructions
The methods provided below will assist you in removing the Trojan:Win32/Wacatac.B!ml detection.
Removing malware from the system should be thorough and carefully executed; therefore, please follow every step provided.
We made the instructions below easy to understand so non-tech-savvy users can still remove the computer threat without needing help from tech support or a computer technician.
Method 1: If Trojan:Win32/Wacatac.B!ml was detected as a software
The steps below are for if the detected threat is a part of a software or is a software then users will have to uninstall the said program.
Your antivirus detection results would have shown the exact file and its directory to know if it is part of a program or not.
To remove the detected Trojan:Win32/Wacatac.B!ml malware from your computer, we have provided two ways to do so: one is through normal uninstallation, and if that does not work, we also provide an advanced uninstall method to make sure it will be removed without issues.
Remove Trojan:Win32/Wacatac.B!ml via Control Panel
The most common way to remove the trojan virus from your computer is to uninstall the program through the Control Panel. You may view all of your installed apps as well as the developer's name in the list of applications.
1. From the Windows search bar at the bottom of your screen, search for Control Panel and click the result that matches the same application.
2. You will see different options, such as System and Security, as well as User Accounts. But what you want to click is the Uninstall a program under the Programs section. Depending on your Windows version, hovering over the uninstall section will be relatively the same.
3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed.
4. Right-click the program that was detected as Trojan:Win32/Wacatac.B!ml and click Uninstall to get rid of it (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed.
There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
It is widely known to be enough to remove malicious programs that are evading uninstallation. If you encounter such an issue when proceeding to uninstall the app, you may utilize the uninstaller to do the job for you.
Remove Trojan:Win32/Wacatac.B!ml via Revo Uninstaller
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a handy tool for Windows users.
This uninstaller not only removes programs from the computer but also deletes their changes from the Windows Registry, Host File, etc. Following the steps below will guide you on how to install and use Revo Uninstaller to get rid of the Trojan:Win32/Wacatac.B!ml detection.
1. Click the button below to proceed with installing Revo Uninstaller on your computer since we have made an in-depth guide on how to use it on the following page. On the other hand, you can also head over to Revouninstaller.com and download it from there.
2. After the setup file (revosetup.exe) has finished downloading, run the installation wizard, read the license agreement, and click agree to proceed to the next step of the installation. Follow the procedure and wait until the installation of the software is complete.
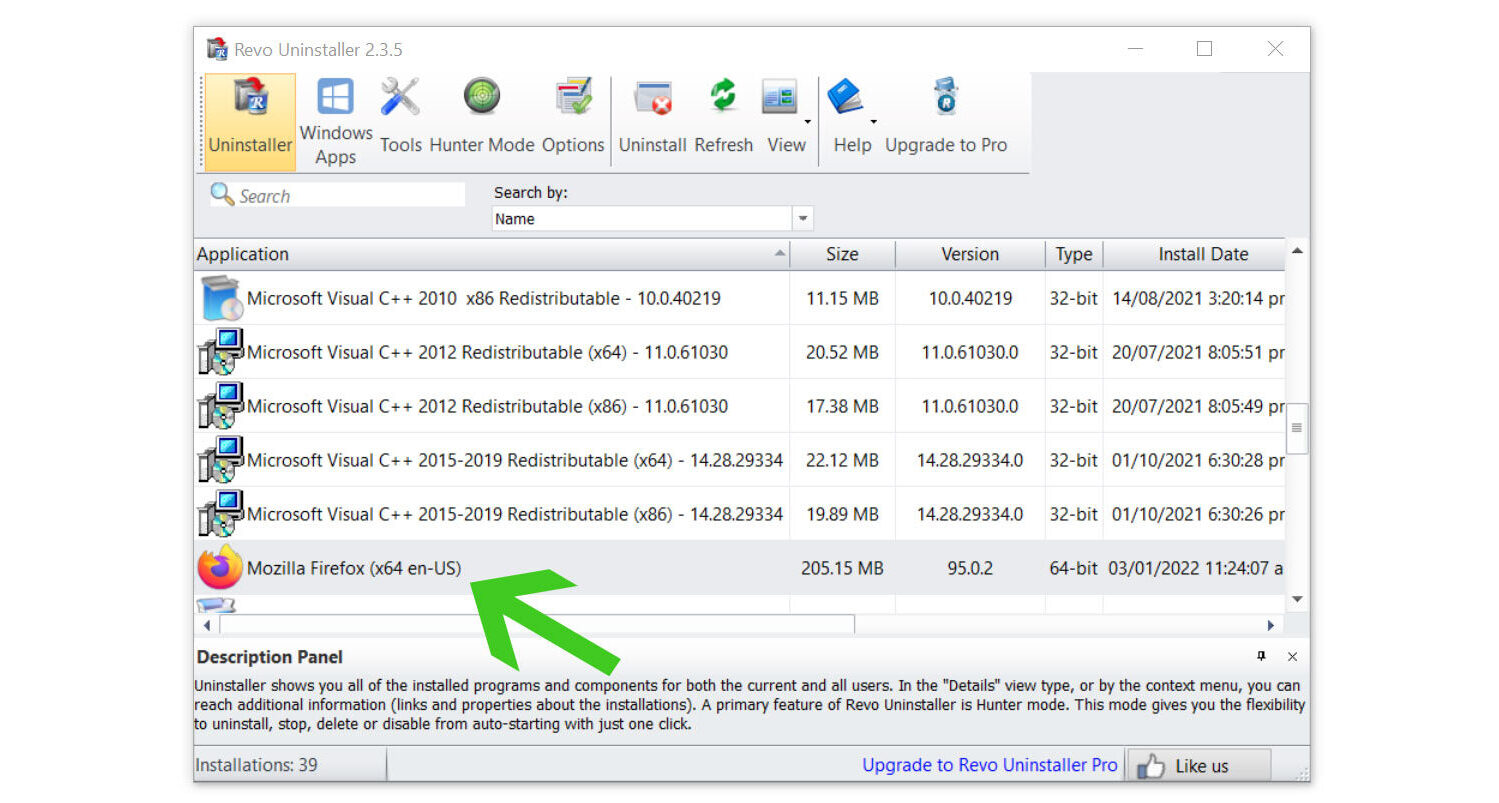
 3. Once the software has launched, find the harmful Trojan:Win32/Wacatac.B!ml detection and double-click the program to uninstall it.
3. Once the software has launched, find the harmful Trojan:Win32/Wacatac.B!ml detection and double-click the program to uninstall it.
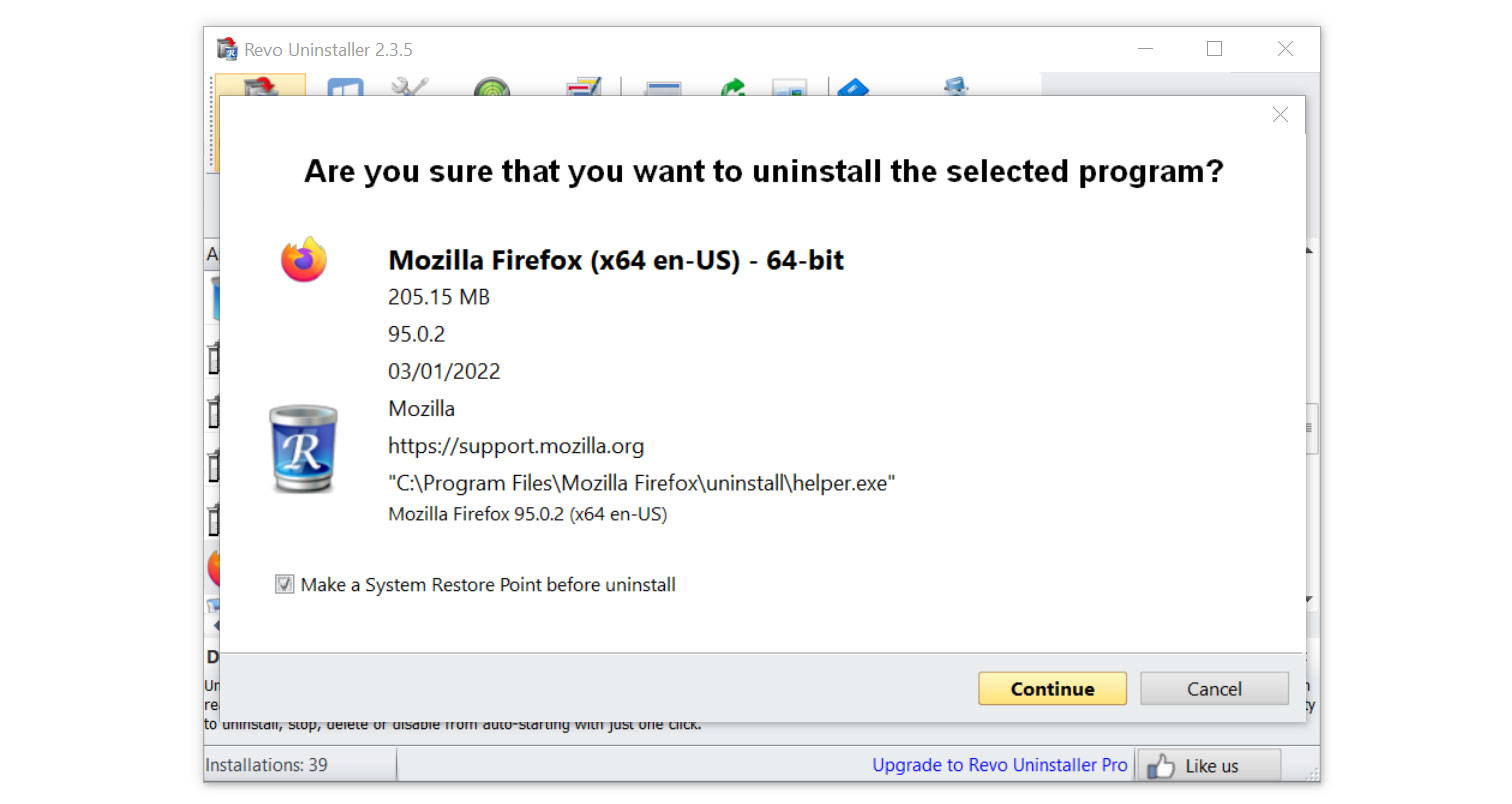
4. Click on the Continue button and follow the procedure to start uninstalling the detected Trojan:Win32/Wacatac.B!ml threat. It is also advised to make sure that a System Restore Point is made before the uninstallation, just in case. (We will be using Firefox as a demonstration.)
5. You will be prompted to choose a scanning mode. From the three options available, select Advanced mode, then click Scan.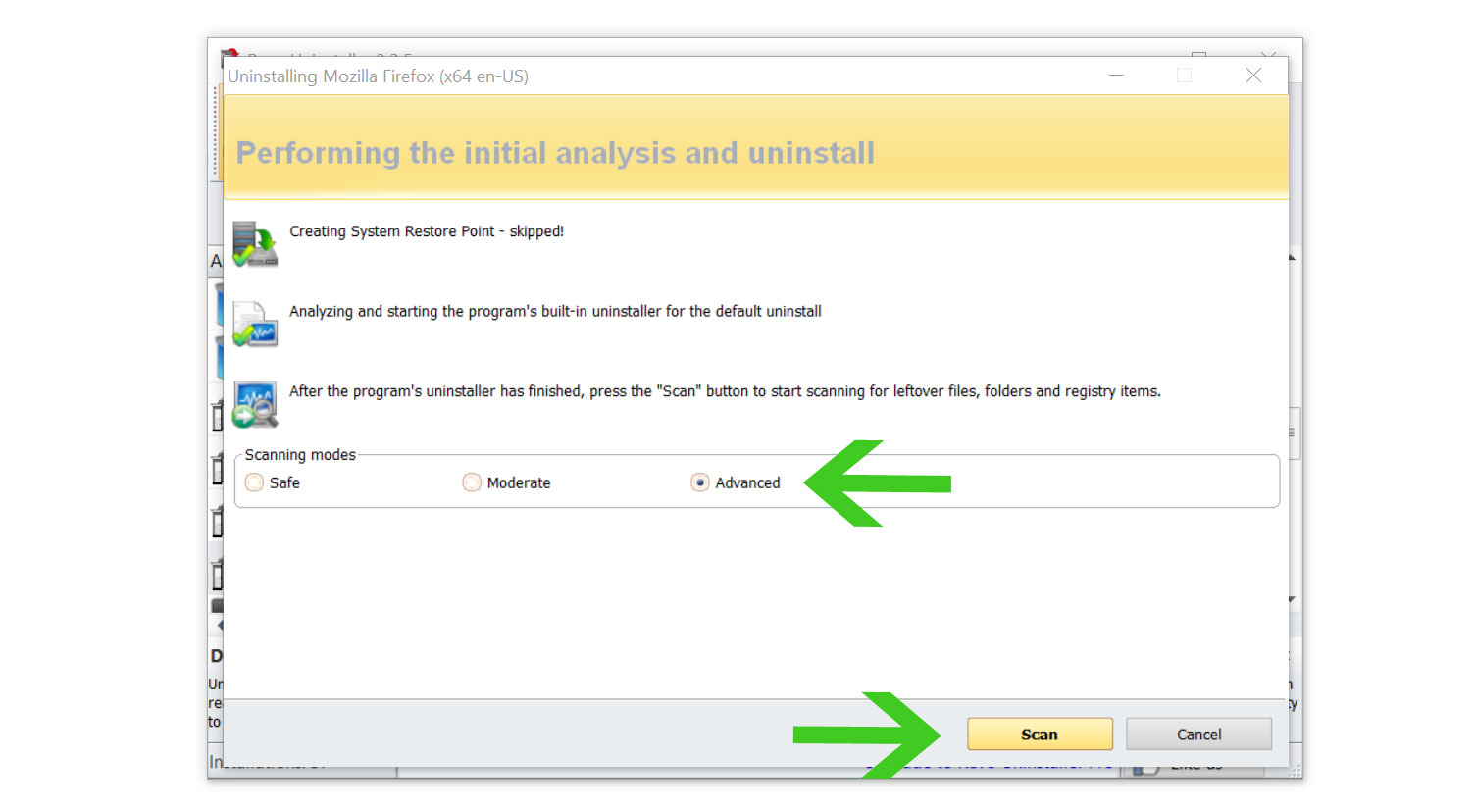 6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
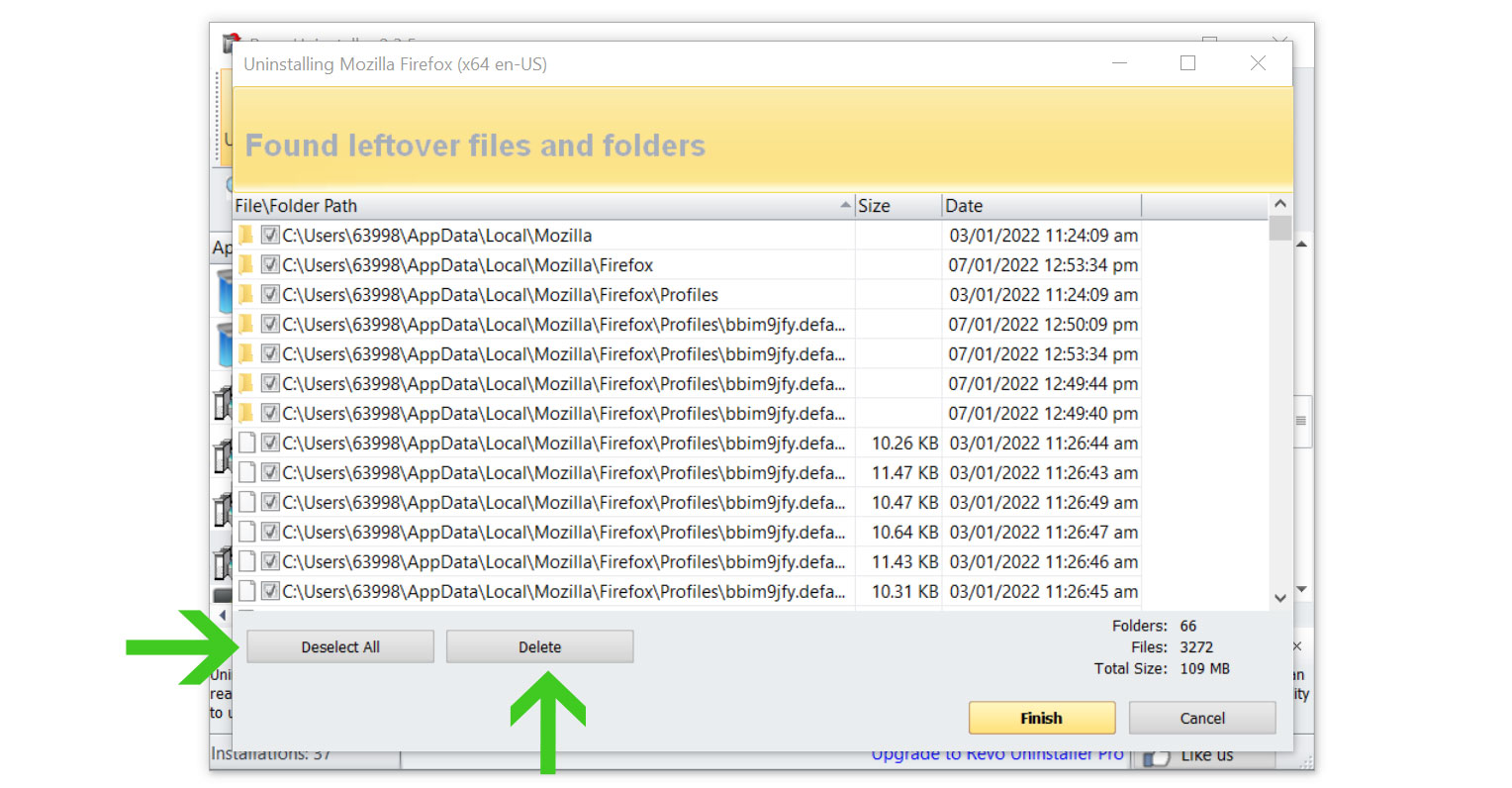
Once the window closes, you have successfully removed the detected Trojan:Win32/Wacatac.B!ml from your computer system.
Method 2: If Trojan:Win32/Wacatac.B!ml was detected as a single file
There is a chance that the detected Trojan:Win32/Wacatac.B!ml may not be an installed Windows program but rather a single executable file that is hiding in the computer. If this is the case, then you can remove it by locating the source of the file and deleting it from there.
Please follow the instructions below to find and delete the detected Trojan:Win32/Wacatac.B!ml threat manually from the computer.
1. When the trojan virus is causing your computer to overheat, launch task manager by simultaneously pressing the Ctrl, shift, and Esc buttons. Another option is via the Run program by pressing the Windows key and R, then typing taskmgr.
2. Check the antivirus results to determine the location of the detected Trojan:Win32/Wacatac.B!ml file. Then, go to the reported directory and delete the malicious file that was found there.
If the file refuses to be deleted because the process is running as well as if certain programs are preventing it from being uninstalled, simply enter Windows Safe Mode and delete it from there.
Before doing so, please remember the directory where the detected Trojan:Win32/Wacatac.B!ml threat is located because Safe Mode prevents non-essential files from running on the computer.
To boot into Safe Mode, first, open the system configuration by pressing Windows Key + R button then type "msconfig.exe".
Once the System Configuration window appears, click Boot next to General then check the Safe Boot from Boot options. Below that, tick the Network option to allow internet within the Safe Mode then click Apply, once everything is done and the computer should be restarted into safe mode.
After booting into the said mode, go to the directory where Trojan:Win32/Wacatac.B!ml is located and delete it. It should be able to be deleted now that the configurations preventing it from being removed are blocked in Safe Mode.
Method 3: Scan with powerful malware removal software
The Trojan:Win32/Wacatac.B!ml detection may be hard to delete and for users who are not knowledgeable about their technology, it is best to utilize a program dedicated to removing such threats from the computer.
For these virus threats, we recommend running a full system malware scan with Malwarebytes Anti-Malware. This program is widely known and recognized by security experts when it comes to removing viruses from the system.
Remove Trojan:Win32/Wacatac.B!ml with Malwarebytes Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked many known computer threats as shown from our tests, and we assure you that it can remove the Trojan:Win32/Wacatac.B!ml detection as well as other malware hiding on your computer.
Not to mention, it is free to use and does not come at any cost to remove the viruses it finds on your computer.
To use Malwarebytes and remove malicious threats from the computer, follow the steps below:
1. Download Malwarebytes by clicking the button below, as we have made an additional and in-depth tutorial on how to use it. Otherwise, you may go to their official website via Malwarebytes.com (Avoid misspelling as it may lead to scams).
Download Malwarebytes Anti-Malware
2. Visit their download section and start a Free Download to begin installing the software on your computer.
3. Once the Malwarebytes setup file (MBsetup.exe) has finished downloading, open the executable file in File Explorer, then right-click the setup and select run as administrator to give the highest system authority and make sure Malwarebytes is installed correctly.
4. Make sure to carefully follow the installation setup wizard's instructions and provide the relevant information it requires. You will be prompted with questions such as Personal or Business Use, Email Address, and others.
5. From the application's home screen, go to the scan tab and begin running a system scan. This will scan the whole computer, including memory, startup items, the registry, and the file system. This is done so that not only the Trojan:Win32/Wacatac.B!ml trojan but also other malware hiding in the system will be detected.
6. Since it can take a while, you should either relax and wait for it to finish or find something else to do. The length of the scan depends on the size of the files you have and the hardware capabilities of your computer. Here are some ways to make scanning faster.
7. Once the scan is finished, Malwarebytes will show the malicious viruses and threats it found on your PC. Trojan:Win32/Wacatac.B!ml will show up on the detection results, and it will show up in a different threat name such as TrojanCrypt.Generic, and many more.
8. Select all the detected files from the report and click the quarantine button to remove the malicious items from the computer into the protected safe quarantine zone of the anti-malware program so that they would not affect and do malicious actions to the PC again.
9. After placing the virus files in the program’s quarantine, it may prompt you to restart the computer to finalize the full system scan procedure. Please restart your computer if prompted, as it is essential. After the restart, Malwarebytes will open and display a message that the scan was complete.
Note: Don't forget to delete the quarantined files afterward.
Simply quarantining the malware files is not enough to make sure they are completely removed. This is a very common misconception: once you click the quarantine button, it is all good and gone.
But, while its effects and harmful activities are halted, the malware is still in the system, only placed in the anti-malware program's quarantine folders. To completely remove it from the computer, go to Detection History from the home screen, select all Quarantined items, and click Delete.
You have successfully removed the Trojan:Win32/Wacatac.B!ml detection as well as other hidden threats on your computer. Rest assured they would not resurface again since Malwarebytes offers a premium trial for 14 days, so you could take advantage of it for free and prevent malware from infecting your system.
While the detection and removal of malware is free for Malwarebytes, the premium versions include real-time protection that ensures your computer is safe all the time. Although we encourage you to use the premium trial, you are free to purchase the full version if you find it useful.
The program is an anti-malware that removes harmful threats like trojan horses, worms, stealers, miners, keyloggers, and many other forms of malware and computer viruses.
For a better and safer web browsing experience, we've provided a few security measures and advice below that will safeguard your browser and computer from harmful threats like worms, malware, trojans, keyloggers, stealers, and other kinds of computer viruses that will harm user data.
Protective measures for better overall security
Removing the Trojan:Win32/Wacatac.B!ml detection and other malware from the computer is one thing; keeping it secure for the future and for a long period is a different thing and will require certain things to make sure you are secured, especially if you do not know most of the ins and outs of the device you are using.
Cybercriminals are always stepping up their game to make sure they infect users and extract data and money from them.
We encourage you to take the actions listed below to ensure complete security before leaving this page because we strongly promote web security and having a secure online presence.
Safeguard your data and privacy online by using a VPN application
VPNs, also known as virtual private networks, guarantee your safety and complete anonymity while you browse the internet.
In contrast to a firewall, which monitors and blocks potentially harmful connections in the network, A VPN hides the user's connection via a tunnel so that it would appear to third parties as a different IP address and location.
This ensures that your data won't be leaked because the program hides it. Be aware that visiting infected websites may cause your IP address and location to be disclosed; however, if you use a VPN, this will prevent your true IP address from being revealed to malware actors.
Use a firewall to prevent cyber attacks
A security firewall is required for every internet connection that is made. It is an essential tool that enhances security and stops online attacks.
Through a security mechanism, it controls incoming and outgoing network connections on your system and network and filters the undesirable ones. Consider it a further barrier against malicious assaults and zero-day exploits.
Bottom Line
While this may appear to be typical advice, we recommend users not visit illegal streaming or torrenting websites and more importantly, download anything from them because doing so may result in the installation of malware and viruses.
Additionally, make sure that your device is protected against sneaky exploits and stealthy cyberattacks. While taking precautions and avoiding dubious websites are crucial, having a solid line of defense is essential to ensuring the security of your network and data.
If you experience another computer issue, please visit our website to find a solution for your problem or get in touch with us, and SecuredStatus will be happy to assist you once again.

