What is RAV Endpoint Protection?
RAV Endpoint Protection is the same program as RAV Antivirus as they are both programs developed by Reason Labs.
Many have reported that the two programs have been suddenly getting installed into their computers, that is because RAV Endpoint Protection is often bundled along with other applications when they are installed.
Although this application is an antivirus program and is safe to use, getting software suddenly installed into the computer is something people may not want which is why it is often branded as a PUP (Potentially Unwanted Application).
One of the main ways of getting into the computer is through software bundling wherein the program is tagged along in legitimate software like Android emulators and utility programs. So when the user installs the program, the said program will be injected into the system as well.
Please head over to the next section below and follow the removal guide presented to uninstall RAV Endpoint Protection from the computer system.
How to remove RAV Endpoint Protection
This procedure will assist you in removing RAV Endpoint Protection as well as any software that is bundled along with the potentially unwanted application. You can rest assured that the information provided below has been tried and tested.
Step 1: Find and Remove Unwanted Program
An automatic uninstallation guide may also be found below for quick removal, but first here are the methods to remove the app manually.
Method 1: Remove the Program via Control Panel 

- Search Control Panel in the Windows search bar then click it.
- The Control Panel should open, from there click Programs then Programs and Features.
- A list of installed software will show on the screen after a moment.
- Scroll down and find RAV Endpoint Protection or any suspicious programs you did not download then right-click the application and select Uninstall
Method 2: Utilizing Revo Uninstaller 
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a handy tool for Windows users.
This uninstaller not only removes programs from the computer but also deletes their changes from the Windows Registry, Host File, etc.
- Using your browser, head over to their official website (click here) and download the latest software that is compatible with your system.

- Open the downloaded file and it should guide you through the setup.
- Follow the installation procedure and wait until the installation of the software is complete.
- After the installation is finished, tick the box that says Launch Revo Uninstaller then click Finish.
- Once the software has launched, find the unwanted application that is needed to be removed, double click the program to uninstall.
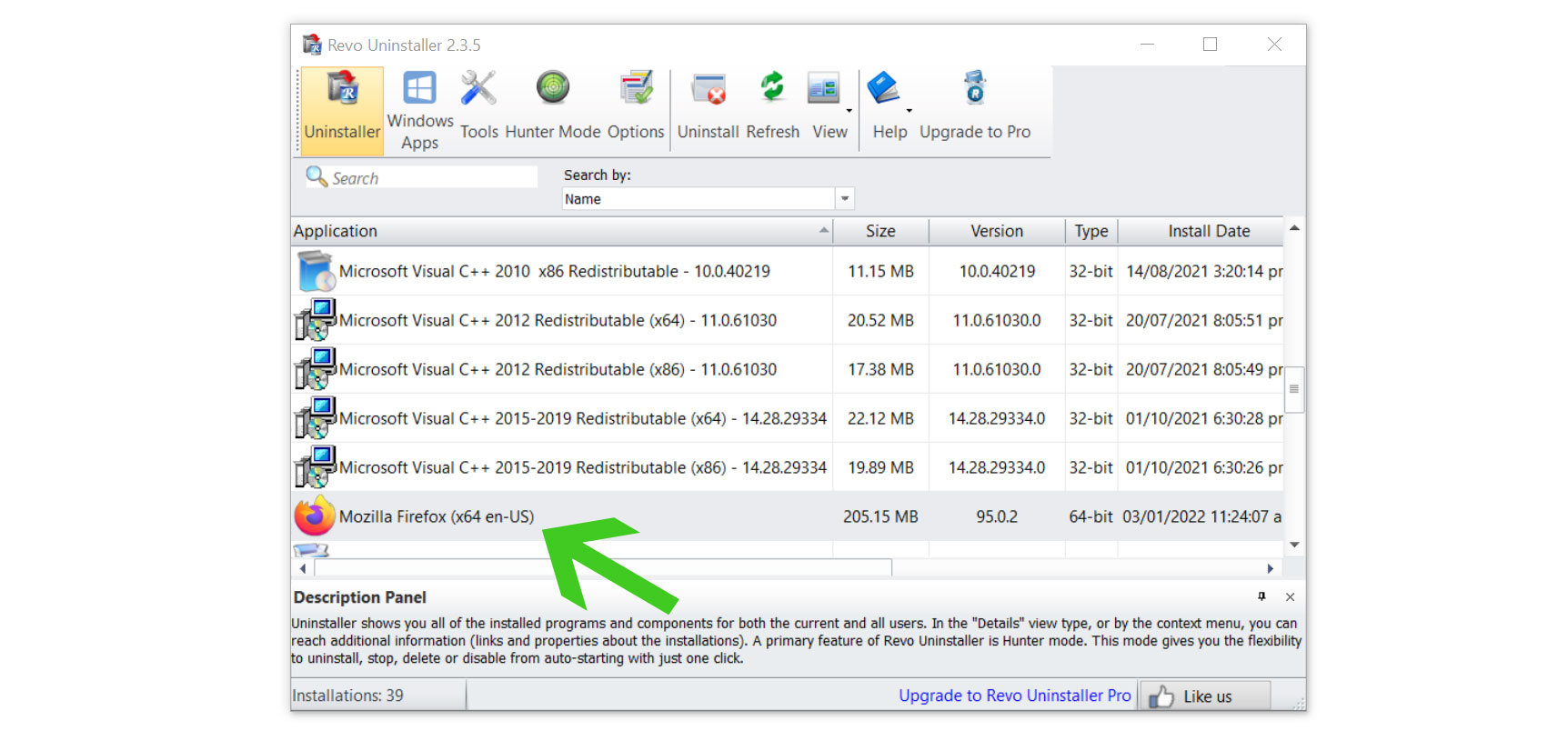
- Click on the Continue button and follow the procedure to start uninstalling the program.
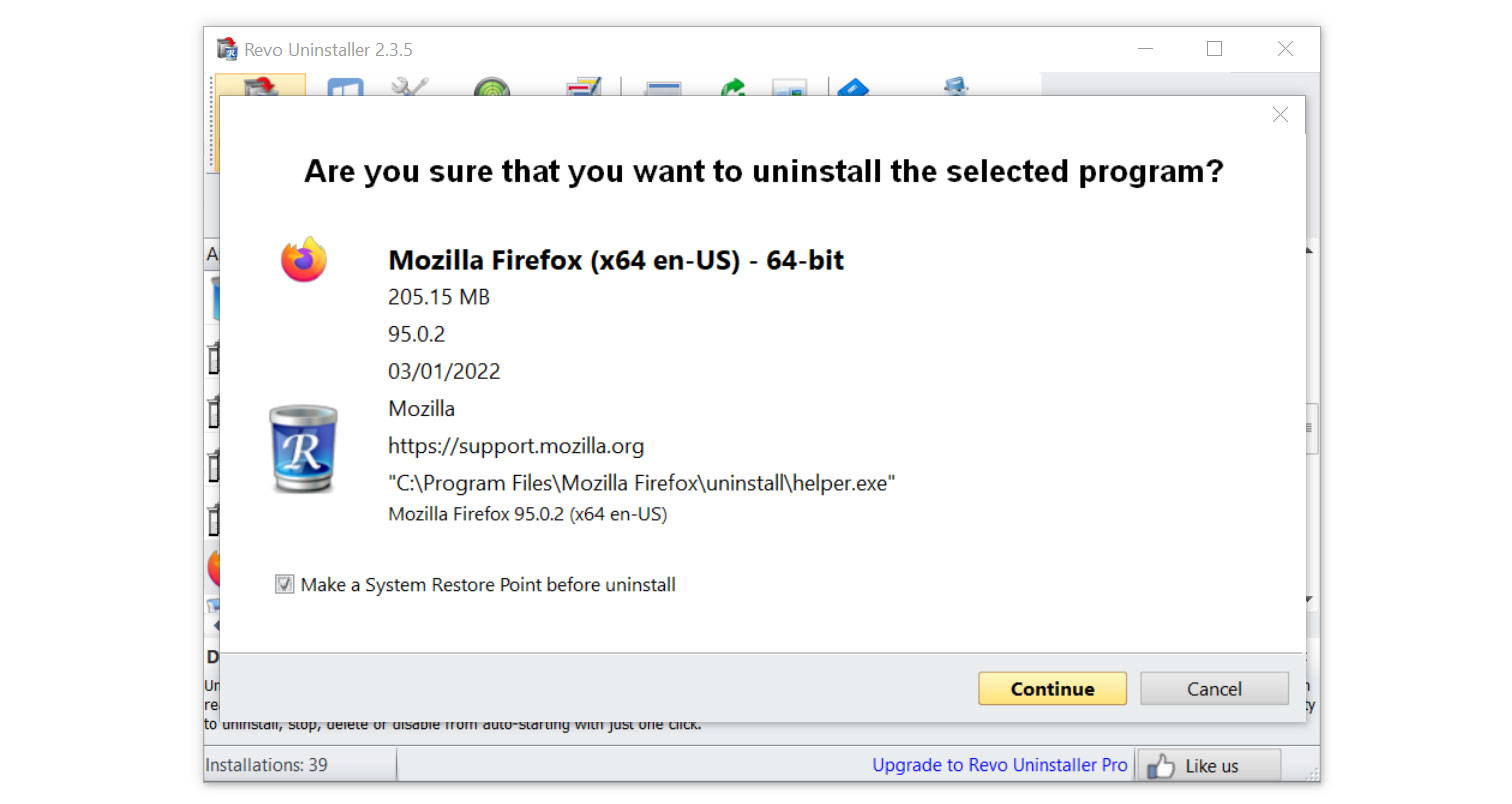
- Once it is uninstalled, a window will pop up. Select the Advanced option for the scanning mode then click Scan to find remnants of RAV Endpoint Protection.
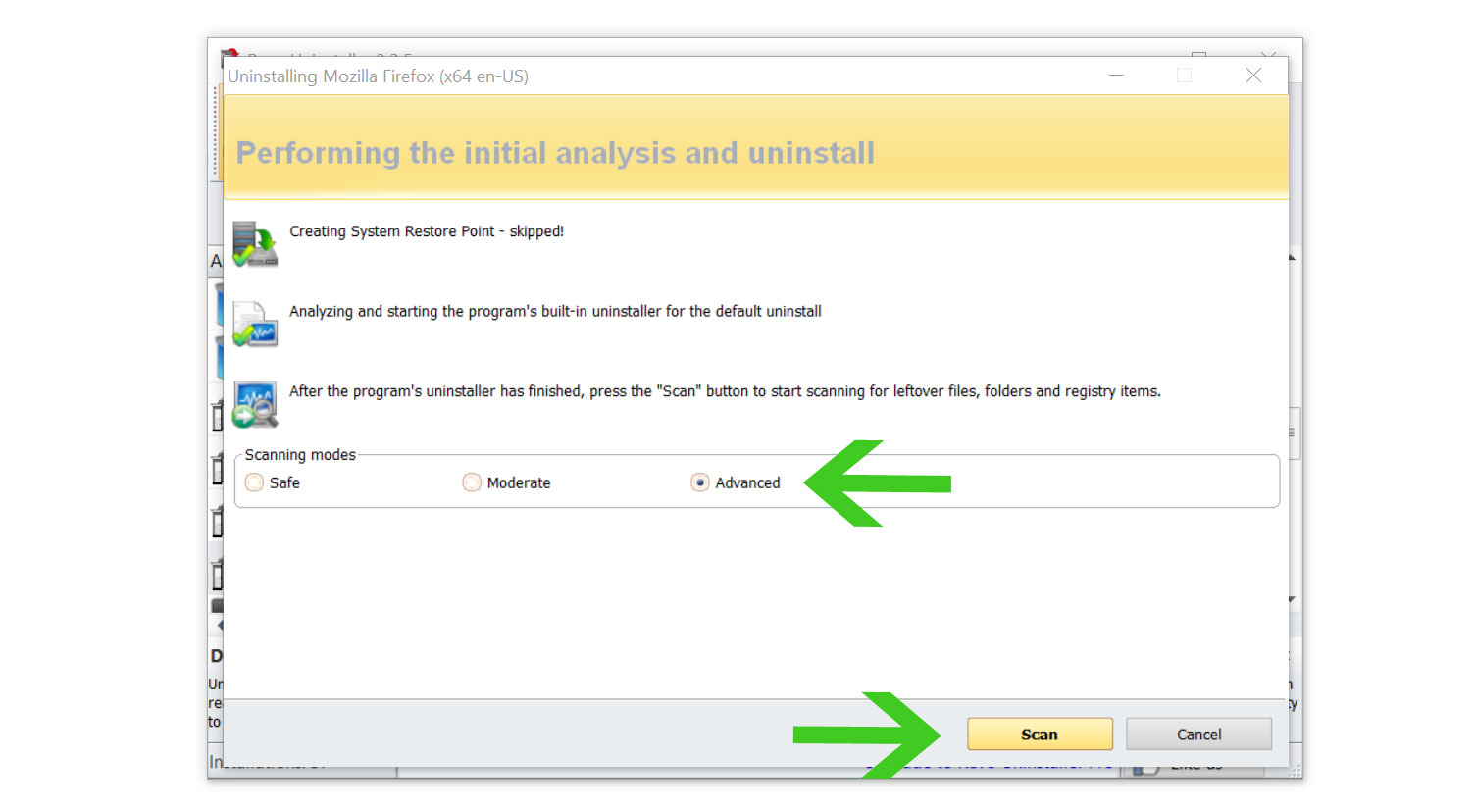
- A window will pop up and show all of the leftovers and changes made by the program uninstalled a while ago.
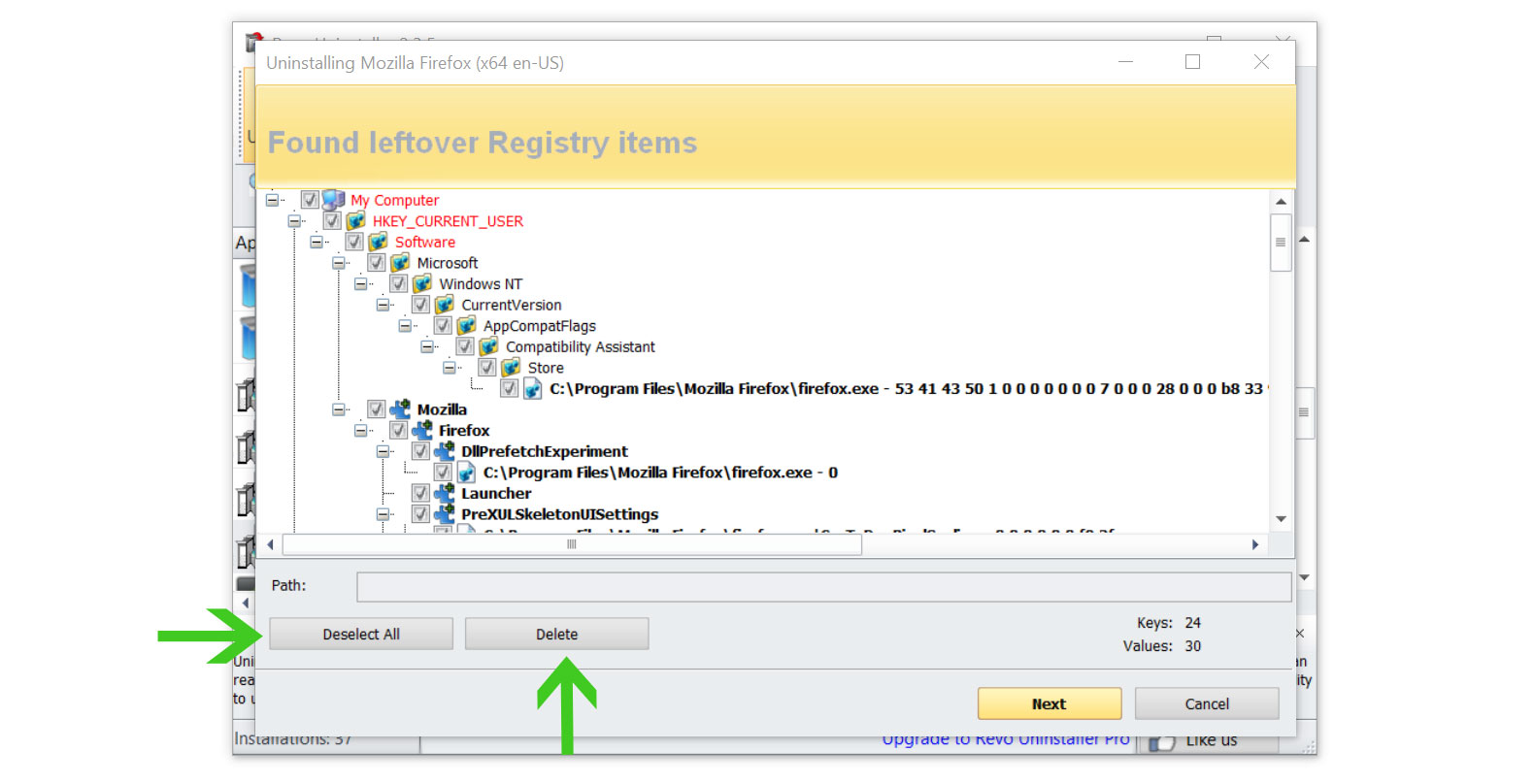
- Click the Select All button and hit Delete to remove the leftovers found on the Windows Registry.
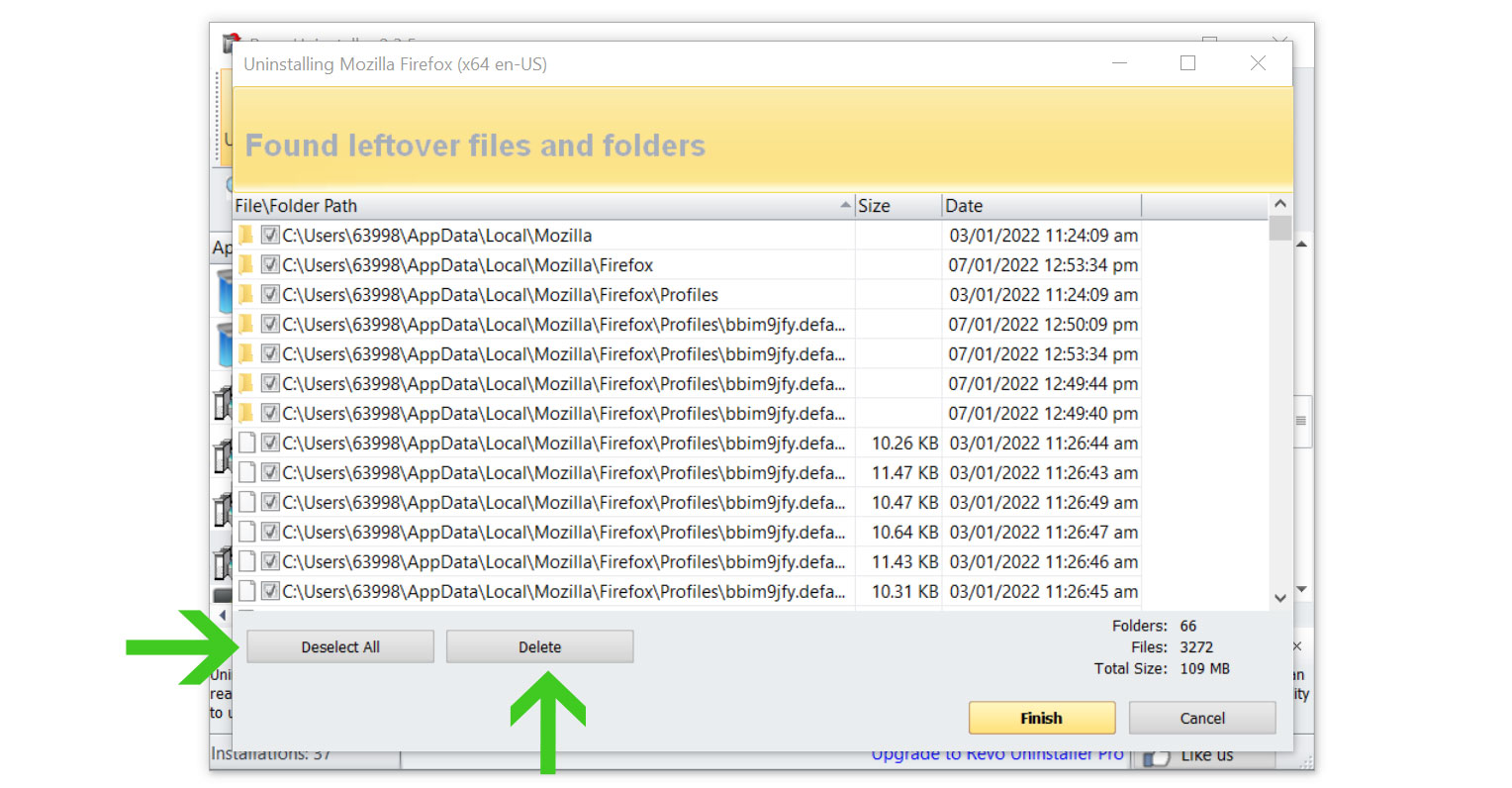
- Some leftover files may be found, click Select All then Delete them as well.
Once the window closes, you have successfully removed RAV Endpoint Protection from your system.
Simple tips to be safe online
- Never acquire software or programs from unknown sources, as this is one of the most common ways for adware and other types of malware to attack your computer. Only download from reputable and legitimate websites. To be safe, stay away from torrent downloads and cracked software download sites, as there will always be malware in the files.
- Using a firewall is one of the most foolproof ways to be safe online. It serves as a first line of defense against dangerous websites, shielding visitors from potential risks. It protects the user’s network and device from intruders. A firewall will safeguard a user from the threats hiding on the vast internet in today’s age.
- It is essential to keep anti-virus software up to date on a computer since hundreds of new malware threats are released every day that target the machine’s vulnerabilities to infect it. Anti-virus updates include the most recent files required to counter new threats and safeguard your machine.
- Only visit websites that have a secured connection. A site with an HTTP connection does not encrypt the data it receives and therefore is not considered secure. Entering personal information such as email addresses, phone numbers, and passwords on a website with an HTTP connection is risky since it could be compromised and your information was stolen. Websites with HTTPS connections, on the other hand, are secure since data is encrypted and attackers are unlikely to gain access to information exchanged within the site.
- Backups are critical for ensuring the safety of your data. Without a thorough backup of the data, several computer dangers and irreversible damage can arise. Backing up your data is a crucial step in ensuring the safety of your information. Having a backup copy of the system and data will be extremely useful in the event of a harmful malware attack.
