Malware in Windows PC?
Malware also known as malicious software is the term used to describe all the threats that are harmful to the computer system.
When a computer is infected with malware, it can do harmful behaviors such as stealing your login data and other sensitive information.
Users who have malware on their devices are most likely to face the following problems.
- Sudden issues with internet connection and applications
- Freezing or slowdowns in computer performance
- Difficulties opening documents or accessing files.
- Pop-ups appear online or when browsing.
- Overheat and high CPU usage.
Effects of Malware on the Computer
Malware represents a very high risk to the computer and, depending on the payload and type of malware they inject, it may cause great damage to every file present in the system.
Rarely, ransomware can be downloaded and will lock all files in every directory. Prevent you from using your computer by preventing you from getting past the boot screen.
On the other hand, a miner virus may be downloaded into your computer, which would cause it to overheat and cause your system to suddenly slow down.
Not to mention how the infection affects your financial and personal accounts. It can look for crucial information that can then be provided to cyber criminals.
They can have access to all of your accounts if you have previously entered or logged them in your browser because they can steal the cache and access it from there.
Another case is where it can track your keystrokes while hiding in the background without the user noticing it.
When this is the case, whenever you logged in to certain accounts or enter your credit card details, cybercriminals will be able to see whatever you were typing on your computer.
It can also be viewed as a privacy violation because everyone you communicate with or email can be monitored by cybercriminals. In addition to that, Trojan viruses may also contain spying software.
This malware can access the webcam and audio device of the computer and record users’ activities, which hackers can then use against them to demand money.
How malware can infect the computer
Computer virus causes a lot of issues for the infected individuals, however, this occurs because they are unaware of the source of these kinds of harmful software. Below are a few ways malware could infect a computer.
Spam email attachments
The most common and widely used method of spreading malware is through malicious email attachments. Its objective is to get unsuspecting victims to download malicious software that is attached to the attackers’ emails.
Some emails might appear legitimate but do not be deceived by them and always look at the sender’s email if you recognize it. The files inside are either packaged together or shown in the attachments like papers, videos, and voicemails.
Drive-by Download
A drive-by download takes place when an individual visits a compromised or hacker-owned website. The webpage could have been infected with a malicious script that downloads an unknown piece of software.
Even though the user does not interact with the website’s contents, the malicious program can still be downloaded automatically without the user’s permission. Individuals should be careful considering the approach appears to be tricky and can infect users easily.
Torrent files
It is used by millions of pirates all around the world to obtain pirated movies and records, and even cracked versions of premium software, to share with those who are interested.
If you’re downloading from a torrent website, it’s important to take a look at the file extension because it’s fairly common to discover that a pirated movie or music is infected with a virus if it’s in the .exe format.
Additionally, hackers can deceive you into installing a harmful program by posing as a movie or cracked software. Therefore, torrent files should be scanned for malware right after they are downloaded.
Avoid torrenting or, if you have to, always ensure that you are safe while torrenting. You can learn how to do this by reading this article.
Outdated Software
Another strategy used by cybercriminals to spread malware is to take advantage of software flaws. Hackers can use security holes in outdated software and operating systems to get unauthorized access to a system.
Due to the lack of updates and patches for advanced malware, criminals have a significant edge over users who run older or obsolete software, making their systems more susceptible to malware and cyberattacks. These are also known as zero-day exploits because they can be used to sneakily install unwanted software.
Commonly installed computer malware
Depending on the type of malware that was installed in the computer, the malicious behaviors can range from a minor security concern to a serious one that can ruin the computer and everything inside of it. Below are the types of malware known to be installed on the Windows computer.
Coin Miner
Miner virus is a malicious program that is used to mine digital currency such as Bitcoin, Ethereum, and Monero. It can lead to several problems including overheating and slowing down of your computer.
Since mining from your device is very resource-consuming, the hardware is to their advantage by using it to mine crypto for them.

This type of software can usually be downloaded through software bundling, where it is included alongside a free application.
Miner malware forces the GPU and CPU to operate at their highest capacity due to mining activity, and doing so may result in graphical issues and overheating of the computer.
| Recently Found Miner Malware |
|---|
| Perfctl Discovered in March 4, 2023 by Millan Nava |
- 1
It will be challenging for a typical laptop or PC with limited RAM and storage to mine cryptocurrency. Additionally, it consumes a lot of electricity.
That is the reason why cybercriminals are persistent in developing crypto-jacking software that can maliciously mine cryptocurrency using the power of their victims’ devices. They can generate even more income by using this method, the more computers infected, the higher the crypto mined.
Ransomware
Ransomware is a harmful malware infection that encrypts the files of the infected user and renders them inaccessible. Threat actors created it to take advantage of flaws in victims’ computers and request ransom money in exchange for the recovery and decryption of the data they encrypt.
Since so many people have essential documents and files on their devices, those infected with ransomware are compelled to pay the ransom requested by cybercriminals in exchange for their data.
How does ransomware work?
Ransomware works in three phases, the initial phase wherein you downloaded the malicious executable file containing the ransomware and run it on your computer which begins the initiation of the second phase.
This is where your files are being searched in every directory of the computer for the ransomware to encrypt which then leads to the aftermath of the ransomware process.
Wherein new files can additionally be encrypted as well and they can also drop other types of malware alongside the ransomware.
Initial phase
Almost every other sort of computer virus enters a device in the same way. They only remain dormant until the file that contains the malware is executed.
One of the most notable methods of how ransomware gets downloaded on the computer is through drive-by downloads, which occur when a user visits an infected website that has been infected with a malicious script that causes a random piece of malware to be downloaded.
Torrent files are also one of the most common ways to acquire this threat, as they are utilized by millions of pirates around the world to download pirated movies and music, as well as cracked versions of premium software. Since then, cybercriminals have spread their malicious software through the torrent community.
Infection phase
Different ransomware variants each have their methods for configuring the computer, but practically all ransomware will disable the antivirus software so it could carry out its operations without having to worry about the computer’s security.
Ransomware will also make changes to the computer’s system such as the host file and the registry files. It takes advantage of adding registry entries to Windows system locations so that the malware will persist even after a reset of the computer.
After these actions, the ransomware virus will now scan the computer system for valuable files such as videos and documents.
After scanning the system for files, it will then encrypt the files to make them useless and unable to be opened. When you are infected with ransomware, your files may suddenly have an additional extension such as .locked, .encrypted, etc.
Once the encryption of files is finished, the ransomware will leave behind a ransom note stating that it demands money in Bitcoin for the decryption of the files.
Post-infection phase
After the ransomware has finished encrypting the file and dropping the ransom note on the desktop. Any of the new files you create or download to the computer may be encrypted as well since you have not removed the virus from the computer yet.
In addition to that, additional malware installation is possible since ransomware can also be used as a downloader or dropper so that cybercriminals can take advantage of the computer much more rather than simply encrypting the files.
They may install harmful stealers and keyloggers that can monitor the user’s behavior and eventually capture sensitive data and login information.
| Recently Found Ransomware Threats |
|---|
 X101 Ransomware
Discovered in September 20, 2022 by Millan Nava X101 Ransomware
Discovered in September 20, 2022 by Millan Nava
|
- 1
Notable Ransomware Families
There are some malware families and groups that stand out in the field of ransomware and infect millions of users every day with their cutting-edge encryption technologies.
Here are some of the most well-known ransomware organizations that have been infecting users ever since and still do today.
Phobos Ransomware
Phobos ransomware was first identified in December 2018 and it was widely known to have been targetting small businesses.

Consequently, the typical ransom demand for a Phobos attack is $18,755 since the ones they target do not have much capital to pay a big amount of money.
Some of the ransomware extensions that were used by Phobos are .steel and .fopra, which people and businesses alike are still getting infected today.
MedusaLocker Ransomware
In September 2019, the MedusaLocker ransomware was discovered for the first time. Since then, MedusaLocker has infected and encrypted systems in a variety of industries, primarily the healthcare industry.

Users as well as organizations have been affected by the aforementioned ransomware, which they may have downloaded from unscrupulous and dubious sources.
One of the known variants of the MedusaLocker we have covered on our website appends the .allock extension to the infected computer.
Petya and NotPetya Ransomware
Petya ransomware encrypts data on the computer system, then asks for a ransom in exchange for the key to unlock them.
It is quite similar to most ransomware however, Petya can lock up your entire hard drive, preventing your computer from booting at all, whereas many other ransomware strains target private files like documents or images.

Beginning in early 2016, Petya spread through phishing emails. The attachment would install malware on the victim’s PC after being downloaded and opened.
Before expanding to Europe and the US in 2017, the latest variation of Petya, known as NotPetya, ravaged Ukrainian institutions like the National Bank of Ukraine where over $10 billion in losses were brought.
How do I decrypt ransomware?
Finding a working decryption tool for ransomware-infected data may be difficult, if not impossible. Because there may not be much information on a virus that appears to be new, it may take time to create a decryption.
However, you can check Emsisoft’s Ransomware Decryption Tools page on their official website to see if a decryption program for the ransomware in question is available. In addition, you can also try Avast’s Free Ransomware Decryption Tools to see if they offer one that works as well.
Note that these sites may not have one available at present, therefore you may also want to try the file recovery applications that are shown below.
File Recovery Programs to Try and Use:
Here are programs you may use to restore your files from a ransomware attack. Note that the tools mentioned below do not guarantee the decryption of ransomware-infected files.
Shadow Explorer
ShadowExplorer is a file recovery program that allows you to recover prior versions of files that have been altered or overwritten. The application accesses the location in which the documents or files are located and retrieves them from there.
For your information, Windows saves a copy of the files you updated with its restore points, but you won’t be able to access them until you have the feature turned on. Restoring your data with software like ShadowExplorer, on the other hand, can be a lifesaver especially when facing a ransomware virus.
In a matter of seconds, the application will display all of the recovered copies. Whatever sort of file you need to restore, ShadowExplorer will find the overwritten copies in any format. This application is extremely useful since it could simply pull up a backup copy of the infected data and get it back. It would be as if it wasn’t infected at all, as long as there is a shadow copy of the files it could do just that.
PhotoRec
Photo Rec is primarily a photo recovery program. It allows you to recover photographs from a variety of digital devices, including laptops, video cameras, mobile phones, external drives, and more.
The tool can also recover corrupted photos, making it suitable for occasions such as ransomware attacks.
Since corrupted photos can be lost or unrecoverable. PhotoRec comes in handy here. The application is a digital picture recovery utility that allows you to recover photographs and images from a variety of devices, even if they have been corrupted by system or file damage.
The program is open-source and free. It recovers missing files from a system using text-based data recovery algorithms. However, do note that this application cannot ensure that your infected photos will be completely decrypted.
Adware
Adware, also known as advertisement-supported software is used by cybercriminals to show advertisements to user’s computers.
It will display unwanted content and can also function as spyware, gathering user information that will eventually be sold. Since it displays intrusive advertisements and slows down your device, it may be annoying for users.
When a user browses the internet or uses their computer, adware displays users suspicious and harmful advertisements. Once an individual downloads third-party programs and does not uncheck the installer option for additional programs, adware gets installed.
By displaying unwanted adverts, adware generates revenue for its developers. In addition, the data that was monitored and stolen from the user is often sold to third-party advertising companies.
| Newly Discovered Adware |
|---|
 Fast Pc Prof
Discovered in September 27, 2022 by Millan Nava Fast Pc Prof
Discovered in September 27, 2022 by Millan Nava
|
 Weather Zero
Discovered in September 26, 2022 by Millan Nava Weather Zero
Discovered in September 26, 2022 by Millan Nava
|
 Viewndow
Discovered in September 22, 2022 by Millan Nava Viewndow
Discovered in September 22, 2022 by Millan Nava
|
 RAV VPN
Discovered in September 5, 2022 by Millan Nava RAV VPN
Discovered in September 5, 2022 by Millan Nava
|
- 1
- 2
How do cybercriminals utilize adware?
By placing adverts on the user’s computer, cybercriminals make money. Adware may have been developed by someone other than the advertisers, and it only displays the advertisements that the advertisers desired the users to see.
It is also used by hackers to gain control over a user’s browser. They use this to lead individuals to specific websites without their authorization, and to websites that display unwanted advertisements.
Furthermore, it redirects users to websites that collect data about users. They can also keep tabs on an individual’s surfing habits and preferences, using this data to determine the kinds of advertisements that will be displayed to the user.
They can make money not only from the adverts but also from other methods, like data collection and browser customizations that benefit the people who paid the cybercriminals. Additionally, they also earn by having to install dangerous programs other than adware.
Different types of adware
As more varieties of adware have been identified over the years, below are some of the most frequent and new types of adware.
This kind of program can be installed on a computer without the user’s knowledge. The following are the most widespread kinds of applications that are often installed.
Potentially Unwanted Programs (PUA)
This is one of the types of adware that can be installed onto a device without the user’s knowledge. It is commonly downloaded together with an application that the user has installed.
![]()
Potentially unwanted programs like Pinaview, WebCompanion, and PixelSee are often downloaded in the background along with the program that the user knowingly downloaded for users not notice.
However, since these tools are already included in the Windows operating system and the majority of them have considerably more reliable downloads available in addition to the one you download to your computer, there is no need for such programs to be installed on the PC.
Rogue cleaner/security software
These kinds of applications can also be installed using third-party installers, and there are several that fit this description. It is also possible to install fake cleaners and malware removal tools, although these aren’t any more effective than standalone Windows Defender and the built-in cleaner.
Once they are installed on the computer, it may show warnings stating that your device is infected with malware and other harmful threats.

Even worse, it could cause your device to slow down, corrupt important documents, and even install malware onto your computer that can steal your data.
Applications like OneSafe PC Cleaner, and Global PC Cleaner will falsely alert you to the presence of a virus infection; however, to remove it, you must purchase the full version of the program that includes the feature that can remove the virus.
Adware with browser-hijacker traits
There are such programs that are considered legitimate, however, have the ability to alter the default web browser and search engine. Being able to display intrusive adverts and send users to a sponsored website makes it very bothersome.
Adware can also have browser hijacker characteristics such as the case with Ouroboros Browser, PC App Store, and TenBrowser.

They switch your browser’s default search engine and browser to the one their software utilizes. It might be a legitimate search engine, but it isn’t any more effective than Google or the search engines you’re already utilizing.
This is what makes it undesirable since users have no incentive to suddenly switch to a different browser and search engine if it entails downgrading because the default browser and search engine will have more features than the one being advertised to you.
Unwanted utility programs
Unwanted utility programs are similar to rogue cleaners in particular, but when they are installed on a computer, they operate uniquely. Instead of displaying false detections that rogue cleansers and antivirus utilize to deceive users, it displays computer issues like issues with your hard disk.
Users will be duped into believing that their computer has problems and that they must use the software to fix them by displaying these fake warnings on the computer’s notification panel. However, here’s where the trick lies: to start fixing the problem, users must pay for the premium version of the program; otherwise, all it will do is display errors.
Additionally, the errors it displays are completely fake and were exclusively created by the utility program’s developers to deceive users into purchasing their application when, in fact, their PCs have no problems at all.
Unwanted utility programs like PC HelpSoft, PC Booster, Quick Driver Updater, and PC Accelerate Pro aren’t malicious, however, once installed, it immediately causes your entire device to slow down.
Trojan
Trojan viruses are computer threats that are known for disguising under a legitimate program or process name for they do not get detected by the user.
The Trojan virus imitates trusted system processes and popular programs that many people use to carry out its harmful activities in the background of the computer without anybody being aware of them, much like the Greeks would disguise a horse as a gift before it was later discovered to have several warriors inside it.
This malware can be acquired via email attachments from unknown senders as well as from downloading files from suspicious torrenting platforms and websites that offer cracked software.
What does the Trojan virus do?
Trojan viruses can steal the data of the user whether it is login details that are stored in the system files of the computer or saved account details cached in the web browser.
Dealing with such a virus can be harmful since it can lurk among the computer files and scan them for something with value that can be stolen by the cybercriminals who developed them.
In addition to that, they can also implement other types of malware that can not only steal data from the computer but use the infected computer as a botnet or use it to mine cryptocurrency which will be directed to the malware actor’s wallet.
It can also lock the computer’s sensitive data, making them useless. If the files are particularly vital, like old recollections and highly valued work-related information, this can be a disaster of an event.
| Recently Found Trojan Viruses |
|---|
 Gtservices.exe
Discovered in May 25, 2023 by Millan Nava Gtservices.exe
Discovered in May 25, 2023 by Millan Nava
|
- 1
Types of Trojan viruses
Here are some of the types of Trojan viruses known to be installed on the computer.
Rootkit
A rootkit is a sort of trojan that hides its presence on a computer while giving cybercriminals privileged, root-level access to your system. Simply defined, it is a nasty form of malware that can seriously harm the operation of your PC and pose a security risk to your personal information.
Ransomware
Ransomware is a type of malicious threat that encrypts every file in the user’s computer making it useless and unable to be opened. It appends a certain extension and utilizes a highly complex algorithm so simply renaming the file extension back to normal would not solve the problem.
They would leave a ransom note on the computer alongside a crypto address to which you would have to send money if you want your files back. We highly recommend against paying the ransom price since there is no guarantee that your files will be decrypted back by the ones who did it in the first place.
Stealer
Information-stealing malware, commonly referred to as stealer malware, is a type of malicious software intended to gather data from the victims’ computers and send it to the hackers who created it.
They target and collect information explicitly, including login credentials, bank account information, credit card numbers, and other crucial data that can be exploited.
Miner
A miner virus is used to mine cryptocurrencies and is secretly installed on a system without the user’s consent while using a system process name to avoid the user being suspicious about the miner software.
Attackers utilize the machines they infected to mine certain cryptocurrencies such as Bitcoin, Ethereum, and Monero because such crypto mining activities require a lot of hardware power.
The malicious actor will then receive the cryptocurrency they mined from the user’s computer and it will then be sent to their wallets.
Downloader
Trojans and other harmful software can be downloaded and launched by downloaders. This type of threat is used to download additional malware to the user’s computer which can pose more security risk to the system.
Downloaders are typically employed as a gate to install as much malware as the cybercriminals want on the infected computer. The downloader malware is frequently installed via suspicious websites that may contain malware downloads.
Please follow the instructions below if you think your computer has malware on it to get rid of it and make sure your Windows system is no longer being taken advantage of by cybercriminals.
How to Remove Malware From Windows Computer
The methods provided below will assist you in removing potential malware, trojans, rootkits, and viruses from the computer.
Removing malware from the system should be thorough and carefully executed; therefore, please follow every step provided.
We made the instructions below easy to understand so non-tech-savvy users can still remove potential malware without needing help from tech support or a computer technician.
Step 1: Uninstall suspicious programs from the computer
To remove adware, trojans, and other form of malware from your computer, we have provided two ways to do so: one is through normal uninstallation, and if that does not work, we also provide an advanced uninstall method to make sure it will be removed without issues.
How will I know what to uninstall?
Giving the exact name of the malicious program may be complicated, but there are ways to make it easier to detect it. One of which is to simply remove all unknown programs you do not recognize or think you have not installed. You may have applications that you don’t even know the use for; that is a sign that they can be malware.
Unless it is a system process, which you can see by checking the developer of the application, some trojan viruses also use recognized and legitimate names to obfuscate their programs. If the publisher name or source of the program is unknown to you, it is best to uninstall it.
As we have previously mentioned, another thing is to look at the version number; the majority of adware and dangerous programs will have version 1.0 because they don’t need to be updated and are merely running as background applications.
To remove malicious programs from your computer, we have provided two ways to do so: one is through normal uninstallation, and if that does not work, we also provide an advanced uninstall method to make sure it will be removed without issues.
Remove software via Control Panel
The most common way to remove malware from your computer is to uninstall the program through the Control Panel. You may view all of your installed apps as well as the developer’s name in the list of applications.
1. From the Windows search bar at the bottom of your screen, search for Control Panel and click the result that matches the same application.

2. You will see different options, such as System and Security, as well as User Accounts. But what you want to click is the Uninstall a program under the Programs section. Depending on your Windows version, hovering over the uninstall section will be relatively the same.
 3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed.
3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed. 4. Right-click suspicious programs you did not install and click Uninstall to get rid of them (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed.
4. Right-click suspicious programs you did not install and click Uninstall to get rid of them (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed. There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
It is widely known to be enough to remove malicious programs that are evading uninstallation. If you encounter such an issue when proceeding to uninstall the app, you may utilize the uninstaller to do the job for you.
Remove unwanted programs via Revo Uninstaller
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a handy tool for Windows users.
This uninstaller not only removes programs from the computer but also deletes their changes from the Windows Registry, Host File, etc. Following the steps below will guide you on how to install and use Revo Uninstaller to get rid of the malicious software.
1. Click the button below to proceed with installing Revo Uninstaller on your computer since we have made an in-depth guide on how to use it on the following page. On the other hand, you can also head over to Revouninstaller.com and download it from there.
2. After the setup file (revosetup.exe) has finished downloading, run the installation wizard, read the license agreement, and click agree to proceed to the next step of the installation. Follow the procedure and wait until the installation of the software is complete.
 3. Once the software has launched, find the suspicious application and double-click the program to uninstall it.
3. Once the software has launched, find the suspicious application and double-click the program to uninstall it.
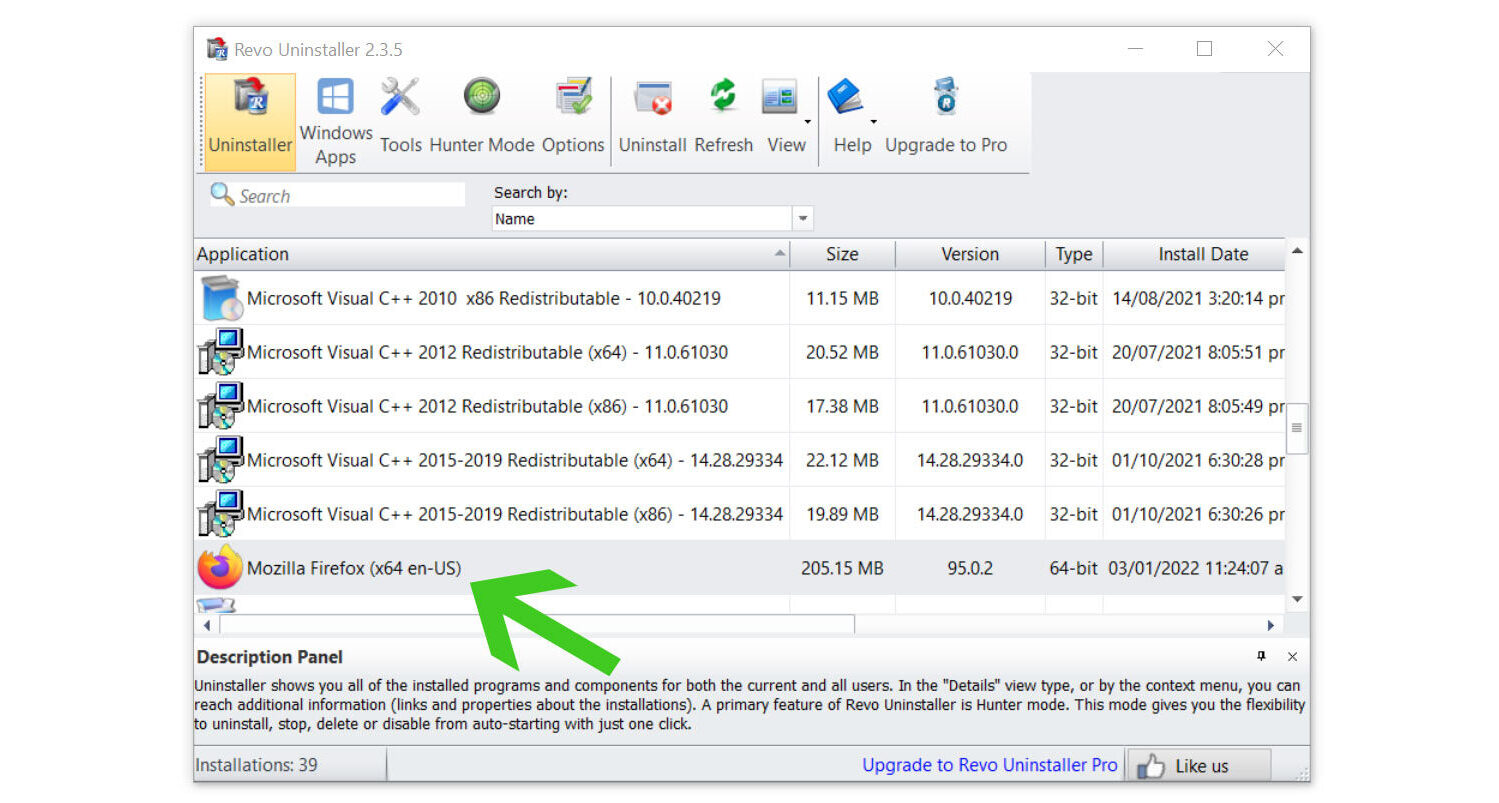
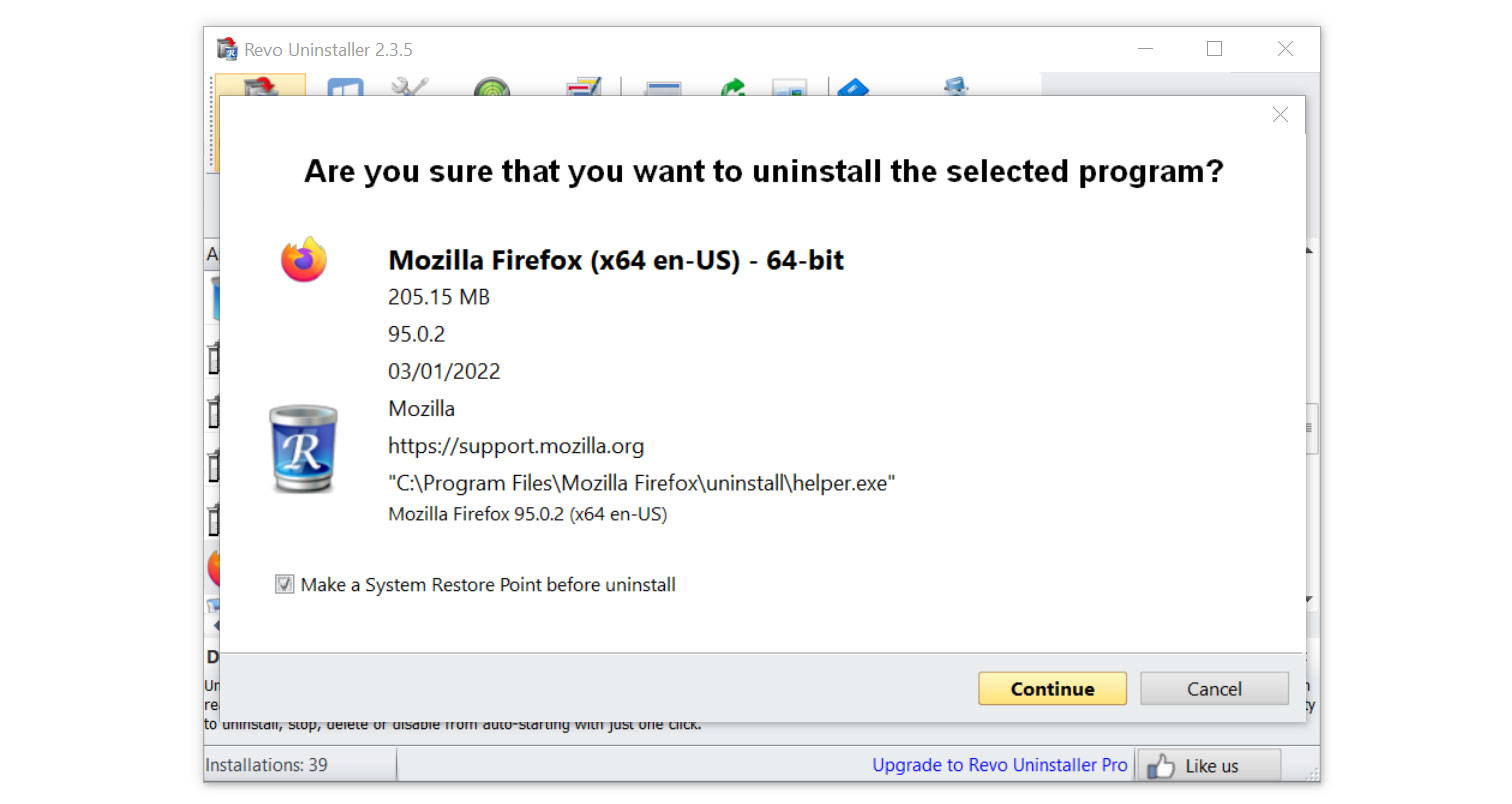
4. Click on the Continue button and follow the procedure to start uninstalling the suspicious program. It is also advised to make sure that a System Restore Point is made before the uninstallation, just in case. (We will be using Firefox as a demonstration.)
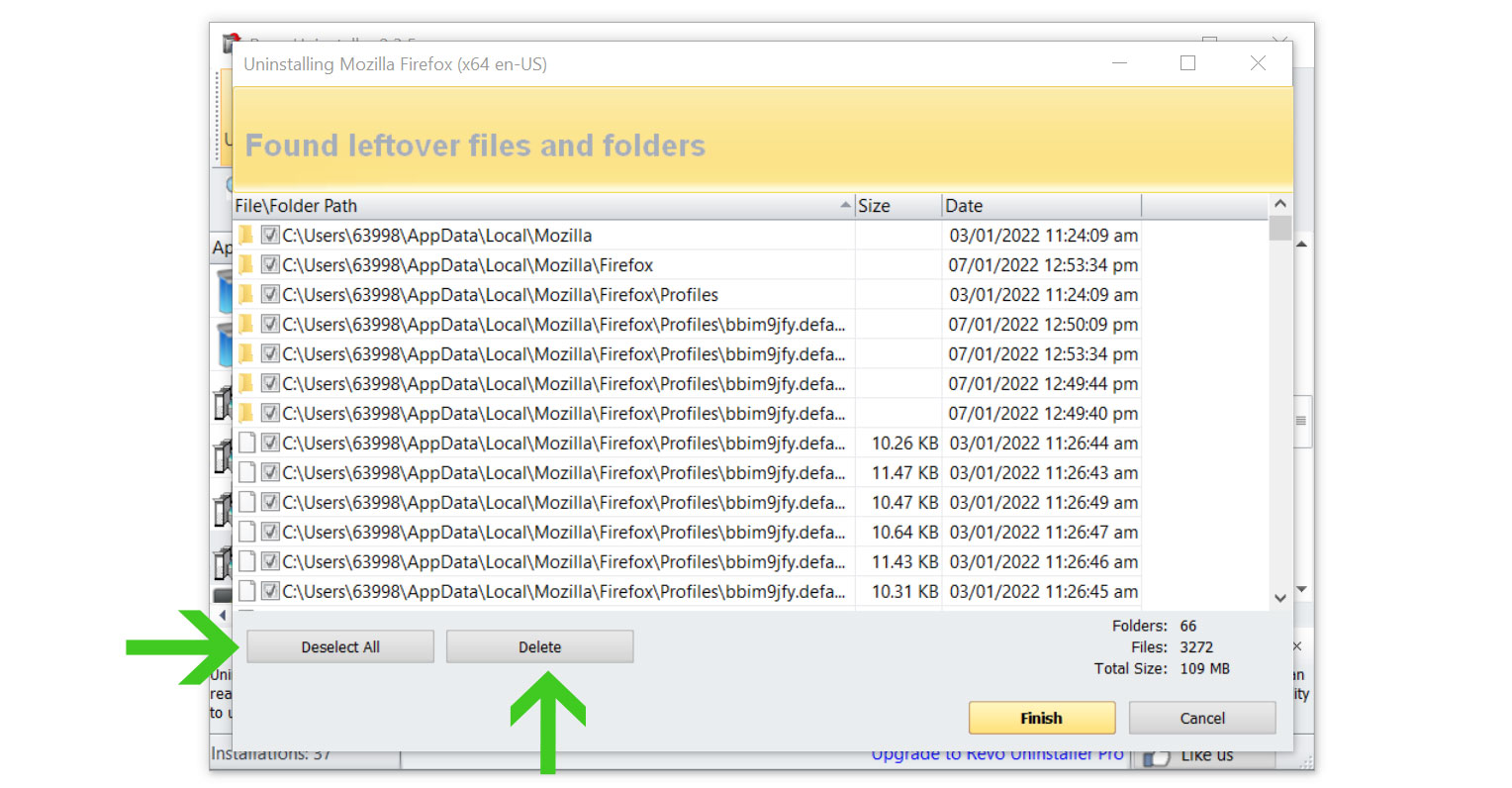
5. You will be prompted to choose a scanning mode. From the three options available, select Advanced mode, then click Scan.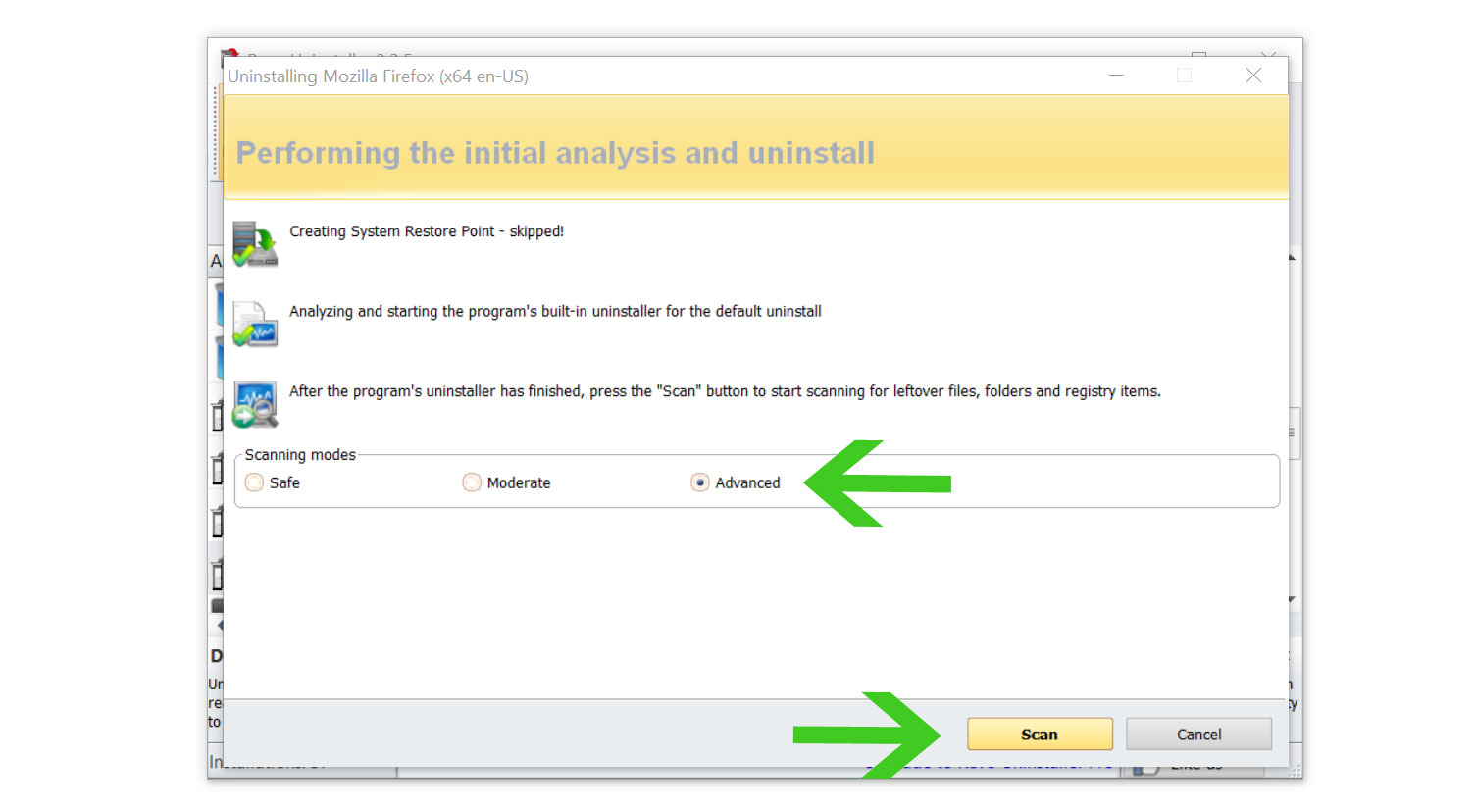 6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
Once the window closes, you have successfully removed malware from your system.
Step 2: Remove browser extensions you did not install
Please follow the steps below to remove suspicious extensions from your web browser and stop the suspicious and harmful behaviors that may endanger the user’s data and privacy.
The browser may be controlled by an organization, making it impossible to remove the browser extension when you try to do so. It indicates that the virus has set up a specific configuration to prevent removal. If that’s the case, please use the steps in this article to fix the problem.
Note: The extension used in this step is not malicious and is simply being used as a demonstration of how to get rid of browser extensions.

Google Chrome
1. Open the browser and click on the three horizontal lines at the upper-right corner of the window screen. Once the drop-down menu opens, hover over Extensions and select Manage Extensions on the submenu. On the other hand, you may also type chrome://extensions on the URL bar to directly access the browser extension page. 2. The extensions page will then open in a new tab, showing all installed plugins on the browser. Find unknown extensions you do not recognize, and deactivate the browser extension by toggling the blue switch below its name and description (We will be using AdBlock as an example). After which, you may now click the remove button to get rid of the extension virus from the Chrome browser.
2. The extensions page will then open in a new tab, showing all installed plugins on the browser. Find unknown extensions you do not recognize, and deactivate the browser extension by toggling the blue switch below its name and description (We will be using AdBlock as an example). After which, you may now click the remove button to get rid of the extension virus from the Chrome browser. 3. If the switch is disabled, then you will need to remove it directly from the extensions folder of the browser. To do this, first, you have to select the plugin and look at its ID as shown in the URL bar. (See the image below for an example.)
3. If the switch is disabled, then you will need to remove it directly from the extensions folder of the browser. To do this, first, you have to select the plugin and look at its ID as shown in the URL bar. (See the image below for an example.) 4. Open File Explorer and go to the folder where Chrome stores the suspicious browser extension. The default location will be at:
4. Open File Explorer and go to the folder where Chrome stores the suspicious browser extension. The default location will be at:
C:\Users\YOUR NAME\AppData\Local\Google\Chrome\User Data\Default\Extensions
 5. You will see a list of folders, each with different hashes. Find the folder matching the ID of the malicious extension, then right-click and delete it. Make sure the browser is closed before proceeding to delete the folder.
5. You will see a list of folders, each with different hashes. Find the folder matching the ID of the malicious extension, then right-click and delete it. Make sure the browser is closed before proceeding to delete the folder.
 The next time you open the Google Chrome browser, you will see that the extension has been removed.
The next time you open the Google Chrome browser, you will see that the extension has been removed.

Mozilla Firefox
1. Launch the Firefox browser and open the menu by clicking the three horizontal lines, which can be located in the upper-right corner of the program. Once the drop-down menu opens, click on Add-ons and Themes. On the other hand, you may also type about:addons on the browser URL bar to enter the Add-ons Manager. 2. From the left-side menu, go to the Extensions page and view all of your browser extensions installed on Firefox. Toggle the blue switch near the suspicious extension to deactivate the plugin, then click the three horizontal dots beside the toggle and select Remove to get rid of it from the browser (We will be using Adblock Plus as an example).
2. From the left-side menu, go to the Extensions page and view all of your browser extensions installed on Firefox. Toggle the blue switch near the suspicious extension to deactivate the plugin, then click the three horizontal dots beside the toggle and select Remove to get rid of it from the browser (We will be using Adblock Plus as an example). 3. If the toggle is locked or unable to be removed, then you will have to manually remove the extension from the browser’s extension file directory. Open File Explorer and go to the following directory where Mozilla Firefox keeps its browser extensions; this can be located via:
3. If the toggle is locked or unable to be removed, then you will have to manually remove the extension from the browser’s extension file directory. Open File Explorer and go to the following directory where Mozilla Firefox keeps its browser extensions; this can be located via:
C:\Users\Your Username\AppData\Roaming\Mozilla\Firefox\Profiles
 4. You will be seeing Mozilla Firefox profiles, and depending on how many browser profiles you have, go to the default ones you have, such as default-release in some cases, and click on the extensions folder inside the profile.
4. You will be seeing Mozilla Firefox profiles, and depending on how many browser profiles you have, go to the default ones you have, such as default-release in some cases, and click on the extensions folder inside the profile. 5. It will be difficult to determine the extensions of the folders you see because they have generated IDs. To make things simple, you should delete every .xpi extension file and make sure the Microsoft Edge browser is closed when doing so.
5. It will be difficult to determine the extensions of the folders you see because they have generated IDs. To make things simple, you should delete every .xpi extension file and make sure the Microsoft Edge browser is closed when doing so. When you open the browser, every extension you have will have been removed. After the virus has been wiped out, install the extensions that you frequently use again.
When you open the browser, every extension you have will have been removed. After the virus has been wiped out, install the extensions that you frequently use again.

Microsoft Edge
1. Open Microsoft Edge and enter the following URL to enter the extensions manager page of the browser: edge://extensions on the other hand, you may click the horizontal three-dot menu and click Extensions from the multiple options shown. Then a small window of extensions will show; click on the Manage extensions to enter the same page. 2. The page will then show all of your installed extensions within the Microsoft Edge browser. Find the suspicious extension and disable it by toggling the blue switch (We will be using the AdBlock extension as an example). Then proceed to uninstall it by clicking the remove button right next to Details.
2. The page will then show all of your installed extensions within the Microsoft Edge browser. Find the suspicious extension and disable it by toggling the blue switch (We will be using the AdBlock extension as an example). Then proceed to uninstall it by clicking the remove button right next to Details. 3. If you were unable to remove the malware plugin, then you will have to head over to the browser’s extension files via File Explorer to remove it manually. To do so, please head over to the extensions tab first, and now click the details next to the remove option.
3. If you were unable to remove the malware plugin, then you will have to head over to the browser’s extension files via File Explorer to remove it manually. To do so, please head over to the extensions tab first, and now click the details next to the remove option. 4. Open File Explorer and head over to the following directory where all browser plugins within Microsoft Edge are stored:
4. Open File Explorer and head over to the following directory where all browser plugins within Microsoft Edge are stored:
C:\Users\Your Username\AppData\Local\Microsoft\Edge\User Data\Default\Extensions
 5. Now find the folder with the same extension ID as the suspicious plugin. It indicates that the following folder contains the files for the particular virus extension: Right-click it and delete it.
5. Now find the folder with the same extension ID as the suspicious plugin. It indicates that the following folder contains the files for the particular virus extension: Right-click it and delete it.
 When you open the browser again, the malicious extension has now been completely removed.
When you open the browser again, the malicious extension has now been completely removed.
Step 3: Scan with powerful malware removal software
For these virus threats, we recommend running a full system malware scan with Malwarebytes Anti-Malware. This program is widely known and recognized by security experts when it comes to removing viruses from the system.
Remove malware with Malwarebytes Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked many known computer threats as shown from our tests with the software, and we assure you that it can remove every malware hiding on your computer.
 Not to mention, it is free to use and does not come at any cost to remove the viruses it finds on your computer.
Not to mention, it is free to use and does not come at any cost to remove the viruses it finds on your computer.
To use Malwarebytes and remove malicious threats from the computer, follow the steps below:
1. Download Malwarebytes by clicking the button below, as we have made an additional and in-depth tutorial on how to use it. Otherwise, you may go to their official website via Malwarebytes.com (Avoid misspelling as it may lead to scams).
Download Malwarebytes Anti-Malware
2. Visit their download section and start a Free Download to begin installing the software on your computer. 3. Once the Malwarebytes setup file (MBsetup.exe) has finished downloading, open the executable file in File Explorer, then right-click the setup and select run as administrator to give the highest system authority and make sure Malwarebytes is installed correctly.
3. Once the Malwarebytes setup file (MBsetup.exe) has finished downloading, open the executable file in File Explorer, then right-click the setup and select run as administrator to give the highest system authority and make sure Malwarebytes is installed correctly. 4. Make sure to carefully follow the installation setup wizard’s instructions and provide the relevant information it requires. You will be prompted with questions such as Personal or Business Use, Email Address, and others.
4. Make sure to carefully follow the installation setup wizard’s instructions and provide the relevant information it requires. You will be prompted with questions such as Personal or Business Use, Email Address, and others. 5. From the application’s home screen, go to the scan tab and begin running a system scan. This will scan the whole computer, including memory, startup items, the registry, and the file system.
5. From the application’s home screen, go to the scan tab and begin running a system scan. This will scan the whole computer, including memory, startup items, the registry, and the file system. 6. Since it can take a while, you should either relax and wait for it to finish or find something else to do. The length of the scan depends on the size of the files you have and the hardware capabilities of your computer. Here are some ways to make scanning faster.
6. Since it can take a while, you should either relax and wait for it to finish or find something else to do. The length of the scan depends on the size of the files you have and the hardware capabilities of your computer. Here are some ways to make scanning faster.
7. Once the scan is finished, Malwarebytes will show the malicious viruses and threats it found on your PC. Every malware will show up on the detection results, and it will show up in a threat name such as PUP.Optional.OpenCandy, and many more. 8. Select all the detected files from the report and click the quarantine button to remove the malicious items from the computer into the protected safe quarantine zone of the anti-malware program so that they would not affect and do malicious actions the PC again.
8. Select all the detected files from the report and click the quarantine button to remove the malicious items from the computer into the protected safe quarantine zone of the anti-malware program so that they would not affect and do malicious actions the PC again. 9. After placing the virus files in the program’s quarantine, it may prompt you to restart the computer to finalize the full system scan procedure. Please restart your computer if prompted, as it is essential. After the restart, Malwarebytes will open and display a message that the scan was complete.
9. After placing the virus files in the program’s quarantine, it may prompt you to restart the computer to finalize the full system scan procedure. Please restart your computer if prompted, as it is essential. After the restart, Malwarebytes will open and display a message that the scan was complete.
Note: Don’t forget to delete the quarantined files afterward.
Simply quarantining the malware files is not enough to make sure they are completely removed. This is a very common misconception: once you click the quarantine button, it is all good and gone.
But, while its effects and harmful activities are halted, the malware is still in the system, only placed in the anti-malware program’s quarantine folders. To completely remove it from the computer, go to Detection History from the home screen, select all Quarantined items, and click Delete.

You have successfully removed malware from your computer. Rest assured they would not resurface again since Malwarebytes offers a premium trial for 14 days, so you could take advantage of it for free and prevent malware from infecting your system.
While the detection and removal of malware is free for Malwarebytes, the premium versions include real-time protection that ensures your computer is safe all the time. Although we encourage you to use the premium trial, you are free to purchase the full version if you find it useful.
The program is an anti-malware that removes harmful threats like trojan horses, worms, stealers, miners, keyloggers, and many other forms of malware and computer viruses.
We suggest Malwarebytes if you are looking for a removal tool and as a second opinion scanner, but if you want full-fledged antivirus software, we believe that the built-in Windows Defender is sufficient for computer security, or if you want something with a more sophisticated system and better protection: Kaspersky Free.
If you choose to uninstall Malwarebytes, you may suddenly see that Windows Defender Real-Time Protection is turned off. This is a common issue that users may face when uninstalling the software. To fix this issue, you may refer to this article.
Alternative: Kaspersky Free Antivirus
After removing malware from your system, you may want to install antivirus software to protect your system against malware.
More importantly, running an additional scan with a different program’s threat database will alert you to hidden Trojan viruses and rootkits that were not removed from the prior scan with Malwarebytes. Kaspersky is a widely known antivirus software that has been on the market for as long as the field of cybersecurity has existed. It is acclaimed by professionals in the field and is one of the most effective antivirus programs available. With its advanced internet security protection, it can also remove additional malware from the computer.
Kaspersky is a widely known antivirus software that has been on the market for as long as the field of cybersecurity has existed. It is acclaimed by professionals in the field and is one of the most effective antivirus programs available. With its advanced internet security protection, it can also remove additional malware from the computer.
What is the difference between anti-malware and antivirus? Anti-Malware software is designed to specifically remove malware and its variants. In addition, it employs heuristic-based detection by picking up harmful code from files.
On the other hand, an antivirus uses signature-based detection, which examines data for attacks to protect users from dangerous viruses, including keyloggers, loaders, worms, trojans, and others.
Malwarebytes and Kaspersky are identical, but Kaspersky is a better overall program since Malwarebytes’ main purpose is to remove malware, but Kaspersky has been known for comprehensive computer security protection ever since.
 Based on our experience removing malware, when two different programs are used to scan, various threats are identified by one software but not by the other. Given that their threat databases differ from each other, it might be able to capture harmful viruses, rootkits, and trojans that Malwarebytes has missed.
Based on our experience removing malware, when two different programs are used to scan, various threats are identified by one software but not by the other. Given that their threat databases differ from each other, it might be able to capture harmful viruses, rootkits, and trojans that Malwarebytes has missed.
Please be aware that if you decide to use Kaspersky, you should first uninstall Malwarebytes because having both security programs installed will cause a conflict. If you choose to do so, please remove Malwarebytes first, as it is essential to do so before we get started.
1. Click the button below to start downloading Kaspersky Antivirus on your computer. On the following page, we have provided clear details on how to install it on the computer. On the other hand, you may go to their official website by searching for the software on your web browser or typing Kaspersky.com (Beware of misspellings since cybercriminals typically use these as exploits to redirect users to malicious webpages).
2. Go to the download page for Kaspersky Free Antivirus. Before clicking download, you will be prompted to choose your continent and where your country is located. This is very important, and you should not choose a different country because you will be met with a “Not supported in your region” message during installation. 3. Once you click download, a setup file (startup.exe) will be downloaded on the computer. After it has finished downloading, open its file location, right-click the executable file, and then select Run as administrator. This will ensure that Kaspersky’s installation will be smooth and will not result in certain errors.
3. Once you click download, a setup file (startup.exe) will be downloaded on the computer. After it has finished downloading, open its file location, right-click the executable file, and then select Run as administrator. This will ensure that Kaspersky’s installation will be smooth and will not result in certain errors. 4. The Kaspersky installation wizard will launch, and you can then proceed to install Kaspersky Free by following the setup instructions. If a UAC prompt appears, simply accept it and proceed with the installation.
4. The Kaspersky installation wizard will launch, and you can then proceed to install Kaspersky Free by following the setup instructions. If a UAC prompt appears, simply accept it and proceed with the installation. 5. Please be patient while Kaspersky is being installed on your computer. The speed and length of the installation process will depend on your computer’s specifications. Kaspersky also mentioned that sluggishness or dark displays during the installation of their program are normal and should not be worried about.
5. Please be patient while Kaspersky is being installed on your computer. The speed and length of the installation process will depend on your computer’s specifications. Kaspersky also mentioned that sluggishness or dark displays during the installation of their program are normal and should not be worried about.
6. To use the antivirus program, you must first create an account on the sign-in page that appears after the antivirus application has been successfully installed on the computer. If you’re looking for the sign-up button, simply enter your email exactly as it appears; if you don’t already have an account, one will be created for you. 7. Kaspersky will ask you to decide which plan to use. It will be either the Standard version or Kaspersky Plus. In this case, the standard version is all you need for now. If you want to try the premium version of Kaspersky, you may opt for Kaspersky Plus to try the features for free. You do not have to add a payment method to get started, and after the trial ends, you will be downgraded to the Standard version unless you pay for it.
7. Kaspersky will ask you to decide which plan to use. It will be either the Standard version or Kaspersky Plus. In this case, the standard version is all you need for now. If you want to try the premium version of Kaspersky, you may opt for Kaspersky Plus to try the features for free. You do not have to add a payment method to get started, and after the trial ends, you will be downgraded to the Standard version unless you pay for it. 8. You will be asked if you want to install additional applications, namely Kaspersky Password Manager and a VPN. Feel free to opt for a program you might want to use; otherwise, install both, or choose not to if you do not need them.
8. You will be asked if you want to install additional applications, namely Kaspersky Password Manager and a VPN. Feel free to opt for a program you might want to use; otherwise, install both, or choose not to if you do not need them. 9. Kaspersky will ask you to scan for viruses in the background. Simply choose not to do so because we will be doing a full system scan later; on the other hand, doing a scan now will only initiate a quick scan. However, if you want to be safe, you can run the background scan now and proceed with a full system scan after.
9. Kaspersky will ask you to scan for viruses in the background. Simply choose not to do so because we will be doing a full system scan later; on the other hand, doing a scan now will only initiate a quick scan. However, if you want to be safe, you can run the background scan now and proceed with a full system scan after. 10. Once the antivirus application has opened, go to the security tab and click the choose a scan button. You will be presented with several different scans; go for the full system scan to ensure full computer security. Always remember to update the database because this will ensure that Kaspersky can detect newly discovered threats and exploits.
10. Once the antivirus application has opened, go to the security tab and click the choose a scan button. You will be presented with several different scans; go for the full system scan to ensure full computer security. Always remember to update the database because this will ensure that Kaspersky can detect newly discovered threats and exploits. 11. A full system scan will take a long time to finish since it will look into all the files on the computer, including the registry, memory, startup applications, and many more. The scanning time will depend on how many files there are on the computer and how big the files are. Additionally, the computer’s hardware and specs will also play into how long the scan will take.
11. A full system scan will take a long time to finish since it will look into all the files on the computer, including the registry, memory, startup applications, and many more. The scanning time will depend on how many files there are on the computer and how big the files are. Additionally, the computer’s hardware and specs will also play into how long the scan will take.
12. After the full system scan is finished, it may detect remnants of the malware as well as other viruses hiding in the computer, showing its location along with a detection name (Trojan.Win32.Generic, Exploit.Win32.Generic, etc.) given to it. Go ahead and proceed to disinfect and restart the computer. 13. The Advanced Disinfection process will then start, and depending on the amount of RAM the computer has, it could take some time. It will then request a computer restart to complete the operation.
13. The Advanced Disinfection process will then start, and depending on the amount of RAM the computer has, it could take some time. It will then request a computer restart to complete the operation. Your computer will now have finished the entire system scan after restarting. By doing this, you can be sure that all forms of malware and viruses have been wiped from your computer.
Your computer will now have finished the entire system scan after restarting. By doing this, you can be sure that all forms of malware and viruses have been wiped from your computer.
You shouldn’t be concerned if the scan turned up no instances of malware or viruses, which indicates that there isn’t any malware on your computer. If two independent programs declare your computer safe, then that’s probably the case.
Step 4: Reset the browser to its default settings (Optional)
Resetting the browser includes complete reversal and wiping out history, homepage settings, default search engines, and browser permissions, which may be used by cybercriminals to hijack the browser.
In addition, the browser reset does not include the favorites tabs, bookmarks, or saved passwords in some cases. To reset your browser to its default settings, please follow the steps below for the browser you are using.

Google Chrome
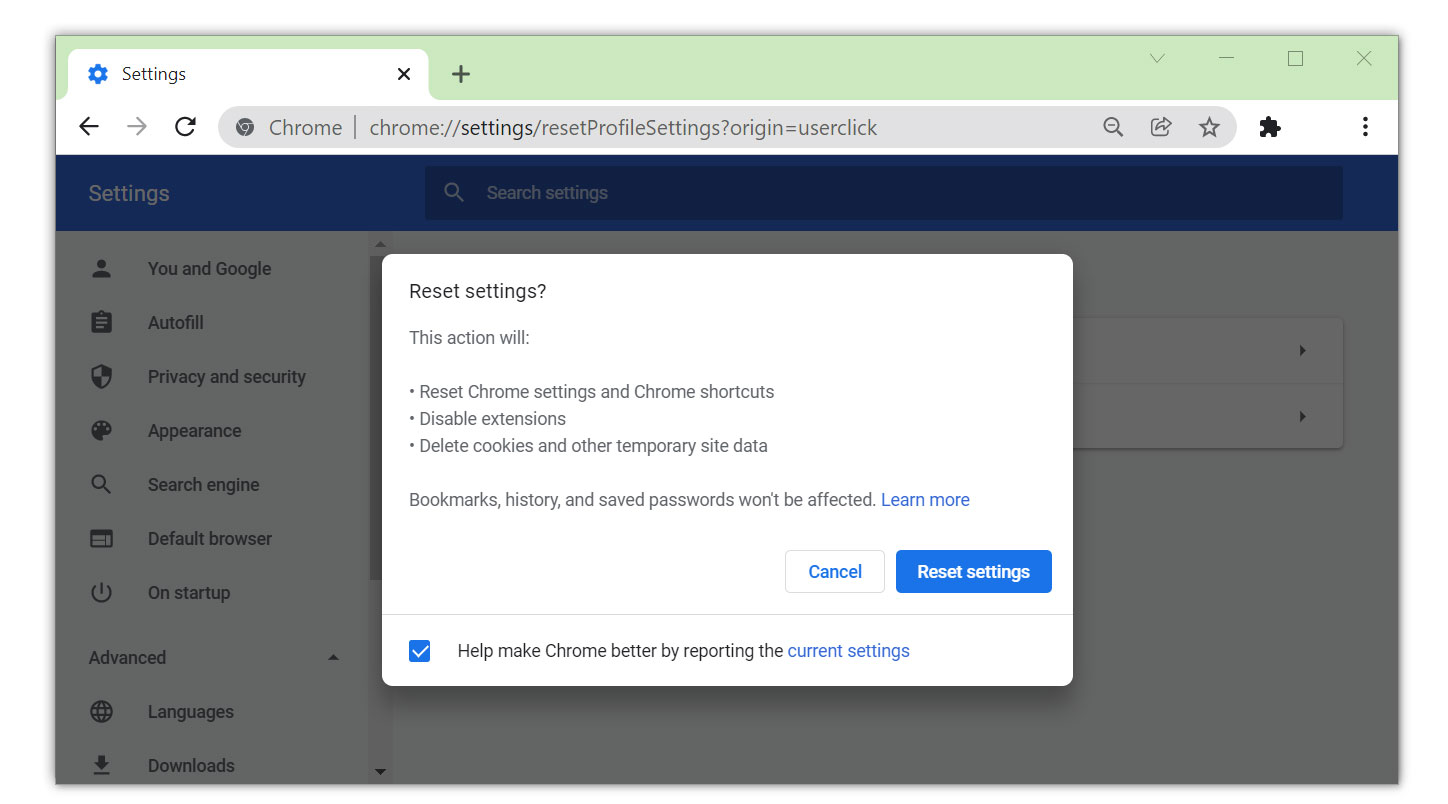
1. Open the Google Chrome browser and click the three dots in the upper-right corner of your screen to access the drop-down menu.
2. From the menu presented, select the Settings button, then click the Advanced menu on the left side of the screen from the settings.
3. On the drop-down menu presented on the screen, select Reset and Clean up.
4. Click on the Restore settings to their original defaults.
5. Then a small confirmation window will appear; click the Reset Settings.

Mozilla Firefox
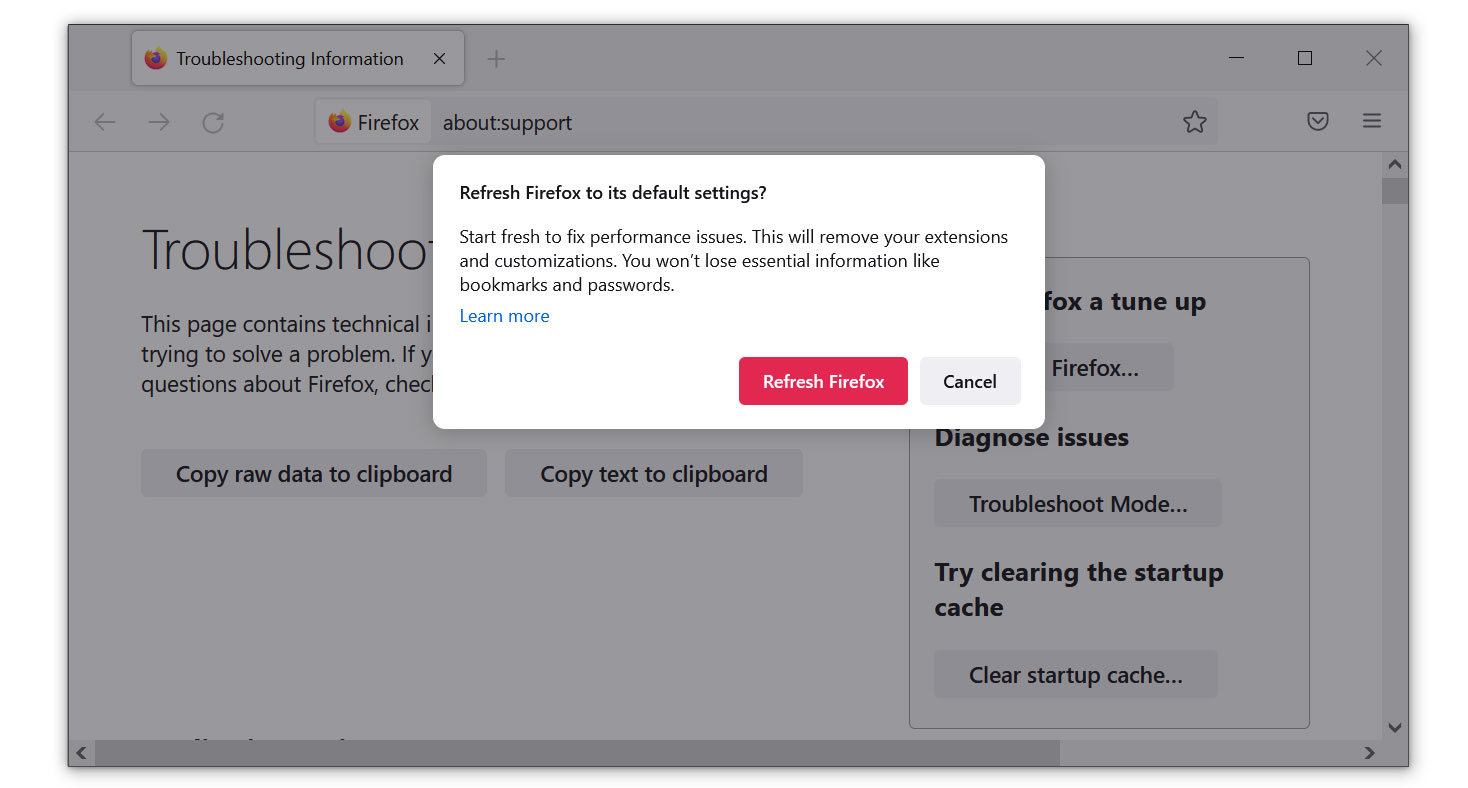
1. Launch the Mozilla Firefox browser, then open the menu by clicking on the three horizontal lines located in the upper-right corner.
2. Navigate down and click Help, then select More Troubleshooting Information from the options given.
3. Select the Refresh Firefox button. Then click Refresh Firefox on the confirmation window that appears.

Microsoft Edge
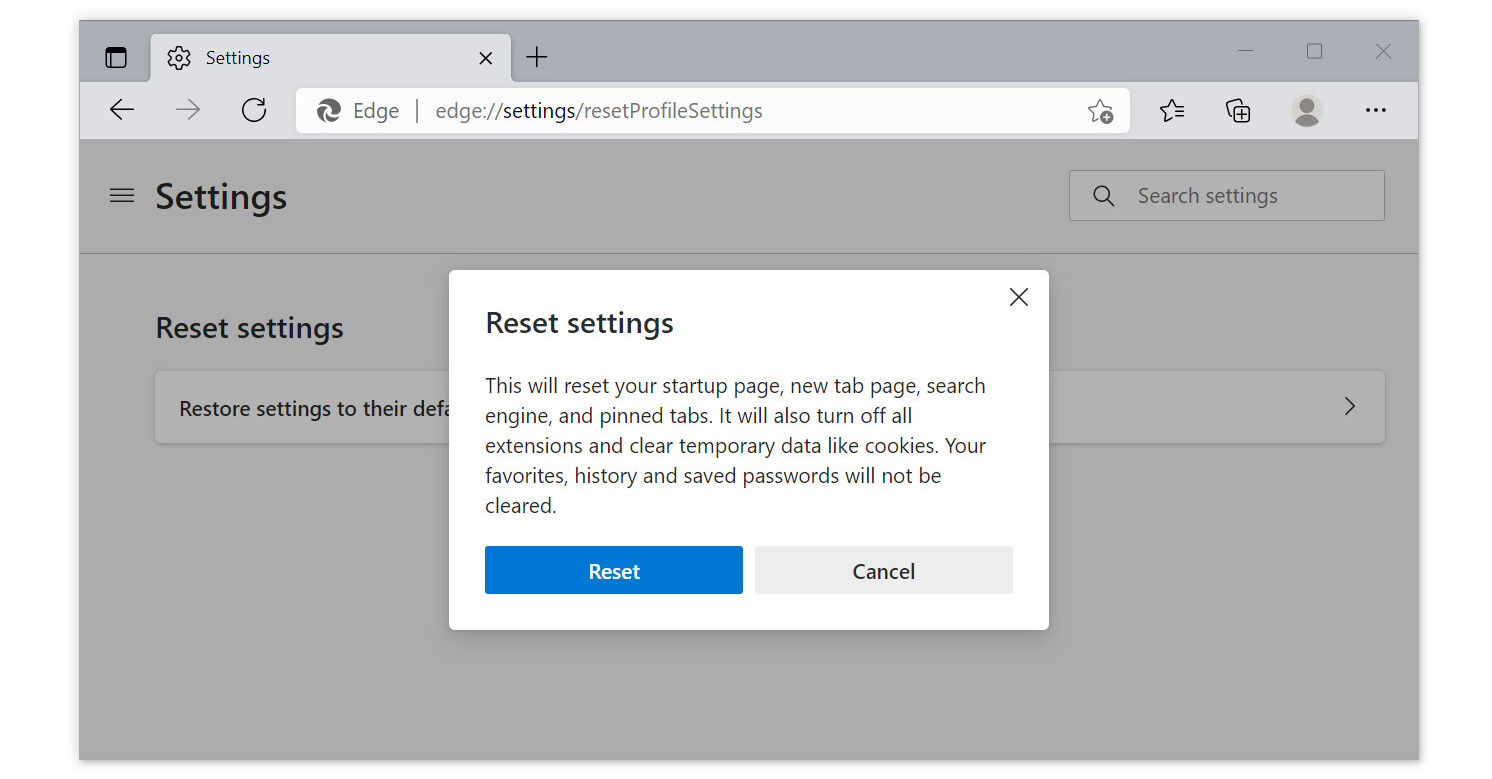
1. Run Microsoft Edge on the computer and click the three-dot icon in the upper-right corner.
2. Click on the Settings button from the drop-down menu.
3. Find and click Reset Settings from the left sidebar. Then click on the option Restore settings to their default values.
4. A warning window will appear, telling you that you are about to reset the browser. Click Reset, and the browser should return to its default settings.
The configurations added by the malware have all been removed, and your browser has now been entirely reset to the settings it had when you initially installed it.
For a better and safer web browsing experience, we’ve provided a few security measures and advice below that will safeguard your browser and computer from harmful threats like worms, malware, trojans, keyloggers, stealers, and other kinds of computer viruses that will harm user data.
Protective measures for better overall security
Removing unwanted programs and malware from the computer is one thing; keeping it secure for the future and for a long period is a different thing and will require certain things to make sure you are secured, especially if you do not know most of the ins and outs of the device you are using.
Cybercriminals are always stepping up their game to make sure they infect users and extract data and money from them.
We encourage you to take the actions listed below to ensure complete security before leaving this page because we strongly promote web security and having a secure online presence.
Safeguard your data and privacy online by using a VPN application
VPNs, also known as virtual private networks, guarantee your safety and complete anonymity while you browse the internet.
In contrast to a firewall, which monitors and blocks potentially harmful connections in the network, A VPN hides the user’s connection via a tunnel so that it would appear to third parties as a different IP address and location.
This ensures that your data won’t be leaked because the program hides it. Be aware that visiting infected websites may cause your IP address and location to be disclosed; however, if you use a VPN, this will prevent your true IP address from being revealed to malware actors.
If you already had Kaspersky installed from the previous step, you had the choice to install its integrated Virtual Private Network, which is a good tool that we also advise.
However, if you decide against doing so and instead download a VPN-only program to cloak your web browsing activity, Mullvad, and AirVPN are excellent choices for fast connections and better privacy.
Mullvad VPN

Since user privacy is the main focus of a virtual private network program, Mullvad VPN excels at putting users’ privacy first. You do not need to enter your email address while registering to download their application because they maintain anonymous accounts.
If you wanted to hide or didn’t want your credit card information to be disclosed, they also accept Bitcoin payments. According to their website, they support a free internet that is devoid of surveillance and censorship.
They have also been announcing new server locations to guarantee users a fast connection anytime they want to connect to various areas throughout the world.
AirVPN
AirVPN seeks to provide customers with access to the real internet, in contrast to Mullvad, which promises to offer users a free internet. Along with masking your IP, they also don’t monitor or log any user data, which is good.
You can use it for a long time without worrying about being disconnected because they don’t impose a traffic or time limit when connecting to their network. In addition, there are infinite, cost-free server changes with physically fast servers in many different nations.
Additionally, when registering for their program, you are not required to enter your email address. They also offer strong encryption and Perfect Forward Secrecy to ensure that it is difficult to determine the user’s connection.
Utilize an adblocker when browsing the internet
Installing an adblocker on the browser is the best way to prevent malicious software.
Additionally, by blocking malicious websites before users can even access them, it is possible to prevent malware from being downloaded.
In this case, we recommend uBlock Origin, which is an open-source AdBlock extension that comes at no cost and is free forever. It is one of the most reliable plugins out there, ensuring that every advertisement on a webpage will be blocked.

For Google Chrome
1. Go to the Chrome Web Store and search for the browser extension, or click here to go directly to the extension page.
2. Click the Add to Chrome button. Then click Add extension when the confirmation window appears.
3. uBlock Origin is now installed in Google Chrome. The adblocker is turned on by default; you can click the power button if you wish to turn it off for a while. The menu can be found by clicking the puzzle icon in the upper-right corner next to the search bar.

For Mozilla Firefox
1. Visit the Firefox Add-ons Store and search for uBlock Origin, or click here to automatically go to the extension’s webpage.
2. Click Add to Firefox, and after that, a confirmation window will appear stating the permissions it will grant the addon. Finally, to add it to the browser, click Add.
3. Mozilla Firefox now has uBlock Origin installed. The adblocker is activated by default; if you want to disable it for some reason, simply click the power button. The menu can be found in the upper-right corner of the web browser, next to the search bar.

For Microsoft Edge
1. Go to the Edge Addon Store and search for the said browser extension. You can also click here to go directly to the plugin page of the Adblocker.
2. Click the Get button, and a confirmation window will appear. Continue installing the extension by selecting Add extension.
3. Now that uBlock Origin is installed on the browser, you can choose to disable the Adblocker by clicking the power button. The menu can be accessed by hovering over the extension’s icon next to the search bar.
The majority of pop-up advertisements, whether they include malware or not, will be filtered by the extension and no longer be displayed to you. Currently, uBlock Origin is not available for Mac or iOS users, but there are plenty of free options on the market, such as AdBlock for Safari.
Use a firewall to prevent cyber attacks
A security firewall is required for every internet connection that is made. It is an essential tool that enhances security and stops online attacks.
Through a security mechanism, it controls incoming and outgoing network connections on your system and network and filters the undesirable ones. Consider it a further barrier against malicious assaults and zero-day exploits.
You don’t need to do anything if you installed Kaspersky in the previous step because the program we installed earlier comes with a built-in firewall that is turned on by default.
On the other hand, if you prefer a standalone, fully functional firewall utility application that is exclusively focused on securing the network, we recommend these top two firewall solutions for personal computers: Comodo and ZoneAlarm.
Comodo Personal Firewall

Comodo Firewall is a well-known software program for securing your network and computer. It is a sophisticated tool with a wide range of features.
It is simple to use and doesn’t require complicated configuration to set up. It also functions by being aware of your computer usage habits to avoid interfering with your work.
Additionally, it claims to offer the highest levels of protection against both inbound and outbound threats. It secures the ports on your computer from hackers and prevents rogue software from sending your sensitive data over the internet.
ZoneAlarm Free Firewall
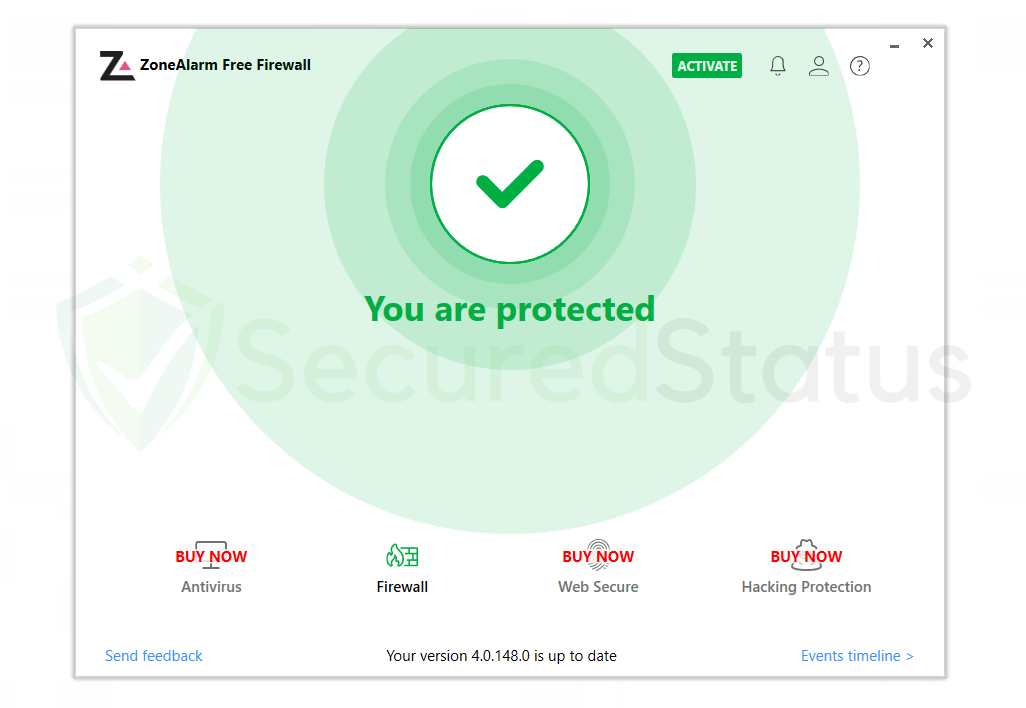
You can also opt for ZoneAlarm Free Firewall as your first line of defense between your device and the internet. The program safeguards your network and blocks any dangers, and you can use the free version of it without paying anything.
It provides a robust two-way protection solution that guards against spyware from disclosing your data online while also hiding your PC from nefarious hackers.
With its cutting-edge anti-bot protection, it also protects your computer from automated cyberattacks in real-time.
Additionally, it protects your computer against spam, dubious websites, and many others. Lastly, it provides real-time defense against automated cyberattacks with its cutting-edge anti-bot security.
Bottom Line
While this may appear to be typical advice, we recommend users not visit illegal streaming or torrenting websites and more importantly, download anything from them because doing so may result in the installation of malware and viruses.
Because these websites are illegal, they are unable to make a profit from legitimate advertising. As a result, they host questionable advertisements from unidentified marketers that want to publicize their contents, which are most likely dangerous codes being propagated by cyber criminals.
Always make sure that your device is protected against sneaky exploits and stealthy cyberattacks. While taking precautions and avoiding dubious websites are crucial, having a solid line of defense is essential to ensuring the security of your network and data.
If you experience another computer issue, please visit our website to find a solution for your problem or get in touch with us, and SecuredStatus will be happy to assist you once again.



