Perfctl is a malicious threat that disguises it’s name to avoid being discovered. It may cause slowness and overheat to the infected computer and server as well. It can use the compromised system’s hardware for the attacker’s own gain by using it to mine crypto.
Since server-based systems have superior hardware than conventional computers, it is most frequently known to infect non-Windows operating systems like Linux and other similar programs.
A coin miner typically spread in the same way that most computer viruses do. Perfctl can infiltrate a system in a number of methods, but the following are the most typical ones:
Malicious website extensions: The malicious miner may potentially get installed on a server by infected website plugins. Webmasters should exercise caution while installing untrusted plugins on their servers. In addition, other executables may also be the source of malware.
Spam email attachments: It is the most common and widely used strategy. It deceives the intended recipient into downloading malicious software that is attached to the attackers’ email. The files are either bundled together or disguised as documents, movies, and voicemails in the attachments.
Drive-by Download: It occurs when a person visits an infected website that has been injected with a malicious script that causes a random piece of software to be downloaded. Hackers can then use these flaws to obtain unauthorized access to targets’ systems once they’ve been clicked.
Torrent files: It is used by millions of pirates all over the world to obtain pirated movies and records, as well as cracked versions of premium software. If you’re downloading from a torrent site, it’s worth checking the file extension because it’s usual to find that a pirated movie or music is contaminated with a virus if it’s in the.exe format. Moreover, torrent files should be scanned for malware after download.
How does Perfctl miner virus work?
Crypto mining malware is a type of harmful virus in which cybercriminals gain access to computers and server access in order to install malicious software. This malware takes use of the computer’s processing power and resources to mine for cryptocurrencies or perhaps even steal cryptocurrency wallets from users who unintentionally downloaded their bait file.
Cryptocurrency mining refers to the process of generating or merely mining new coins of a certain cryptocurrency. It is quite simple to accomplish, but the resources required for mining must have excellent specifications and a powerful hard drive. If several processors and computers mine at the same time, the total number of mined cryptocurrency increases.
That is why cyber thieves are resolute in developing cryptojacking software to unwittingly mine cryptocurrency using the power of their victims’ hardware. People infected with the coin miner malware are likely to encounter high CPU utilization, slow processes, and system overheating.
Perfctl Miner Malware Removal Procedure
This procedure will assist you in removing Perfctl as well as any dangers related with the mining infection. You can rest assured that the information provided below has been tried and tested.
For Linux-based servers
It is crucial to take the appropriate measures to remove the miner virus because there are instances where it has root access.
To begin with, the cron job for the miner malware Perfctl needs to be deleted in the first step. You can delete lines that are connected to or include the Perfctl virus using the crontab -e command.
Also, if you have a C-panel installed, you may delete from there by going to Cron Jobs.
After doing the necessary steps, you can now delete the Perfctl miner malware-related files from your server.
Although we should be aware that the Perfctl miner may be located in a different location depending on the directory of your server, the following code is believed to have completely eradicated the miner virus.
~rm /usr/bin/Perfctl
rm /root/.config/cron/Perfctl
rm /etc/cron.*/perfclean
rm /etc/cron.*/Perfctl
reboot
If the malware is not on the said directory, you can search for the malware files using the find command. For instance, you can run “find / -name Perfctl” to locate all files and directories containing the word “Perfctl“.
Additional Note: If your website is powered by WordPress, a malware scanner like MalCare or WordFence can help you quickly get rid of the virus.
Your hosting company should offer technical assistance if you submit a ticket if you are having trouble eliminating a virus.
For Windows System
The instructions below should help you remove any malware that has infected your Windows PC, including miner malware and other related threats.
Find and Remove Unwanted Program
Since this type of computer threat takes the appearance of an application, it’s essential to try and locate the malicious program and remove it from the system as soon as possible to avoid further harm.
It’s worth noting that locating the program can be tricky because many adware programs disguise as legitimate programs or system files. In that case, using an antivirus scanner will be of help to detect the threat from the computer and eliminate it. An antivirus guide may be found below for a quick malware removal, but first here are the methods to remove the app manually.
Method 1: Remove Program via Control Panel

- Search Control Panel in the Windows search bar then click it.
- The Control Panel should open, from there click Programs then Programs and Features.
- A list of installed software will show on the screen after a moment.
- Scroll down and find Perfctl or any suspicious programs you did not download then right click the application and select Uninstall
Method 2: Utilizing Revo Uninstaller
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a very useful tool for Windows users.
This uninstaller not only removes programs from the computer but it also deletes their changes from the Windows Registry, Host File and etc.
- Using your browser, head over to their official website (click here) and download the latest software that is compatible with your system.

- Open the downloaded file and it should guide you through the setup.
- Follow the installation procedure and wait until the installation of the software is complete.
- After the installation is finished, tick the box that says Launch Revo Uninstaller then click finish.
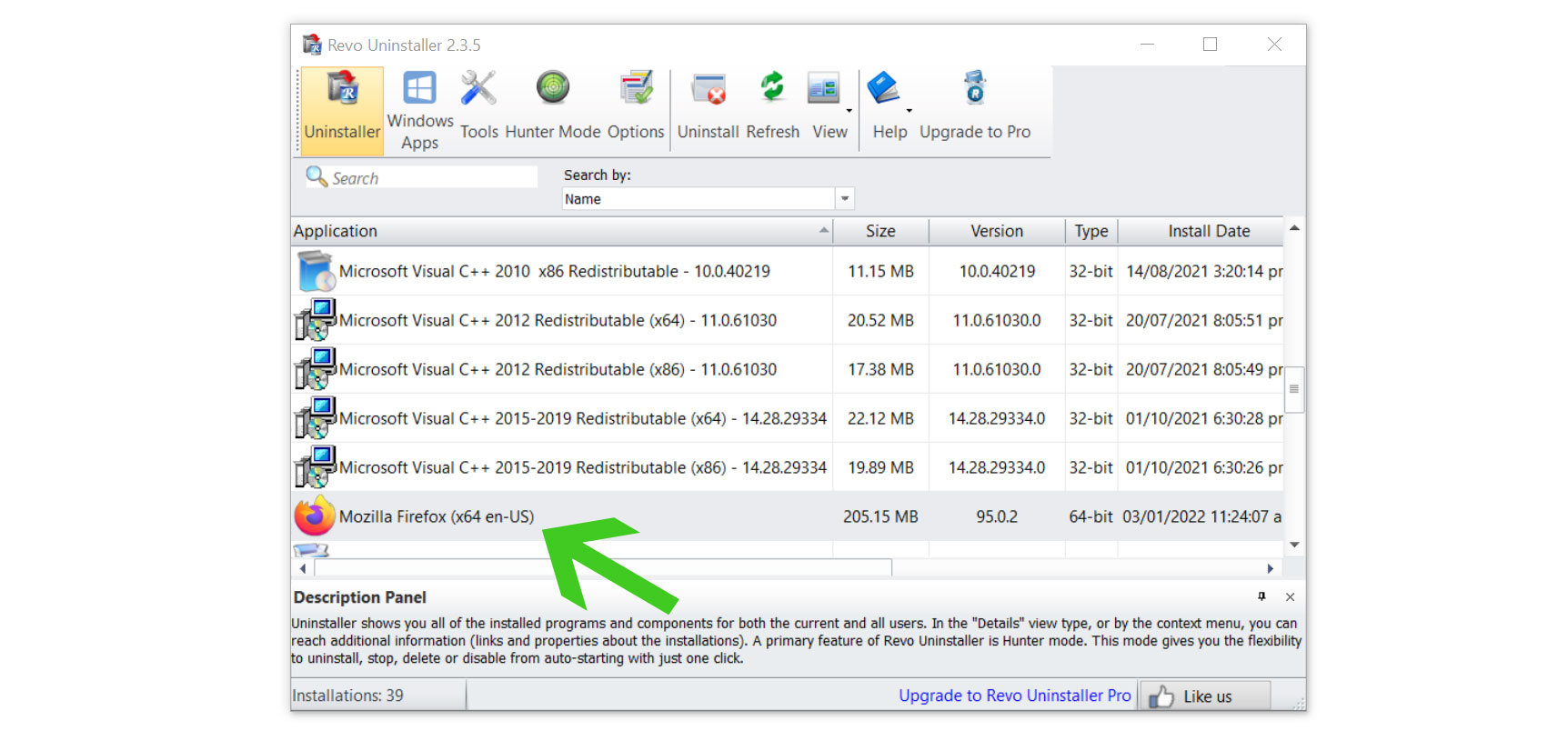
- Once the software has launched, find the unwanted application that is needed to be removed, double click the program to uninstall.
- Click on the Continue button and follow the procedure to start uninstalling the program.
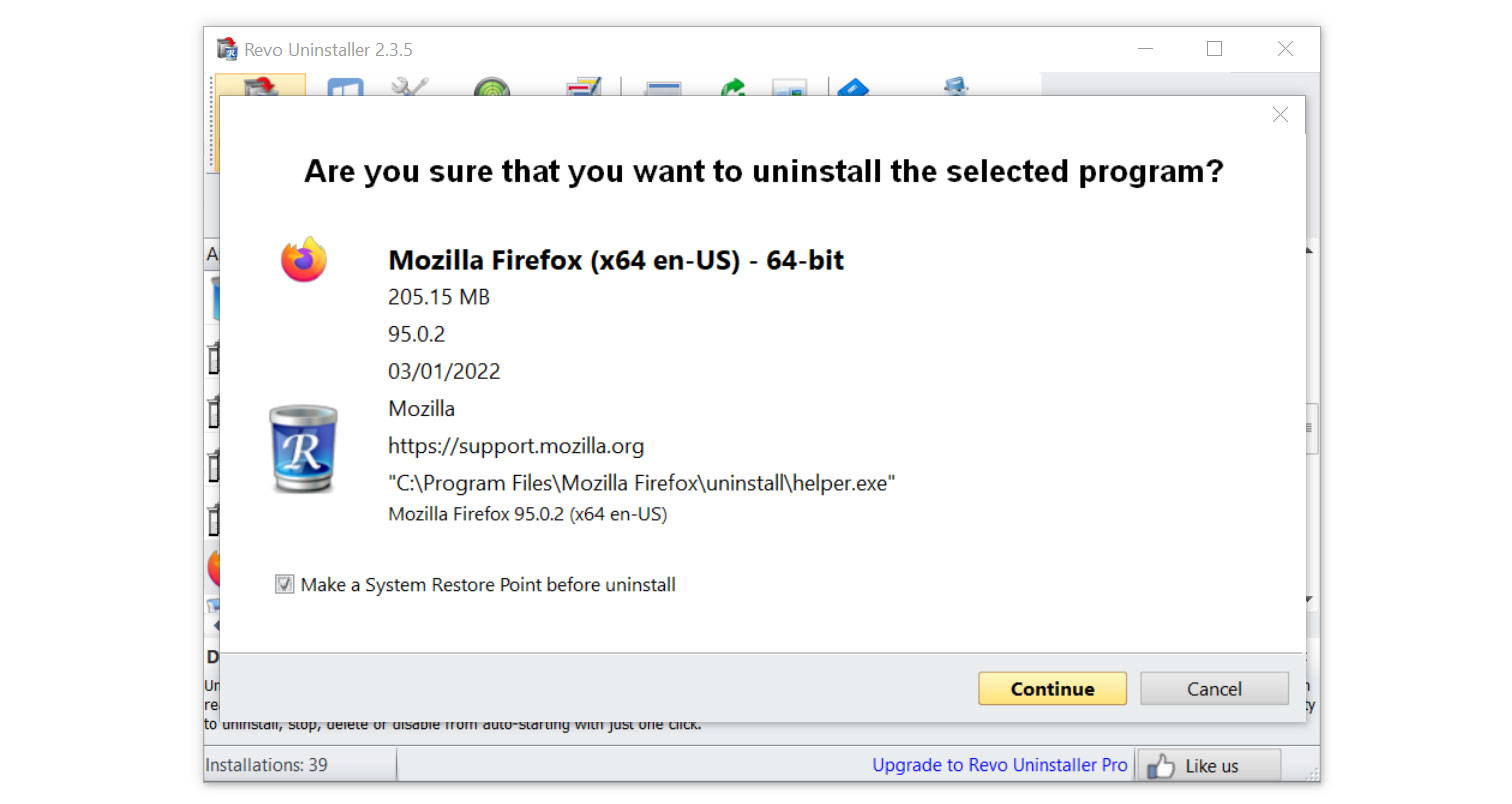
- Once it is uninstalled, a window will pop-up. Select the Advanced option for the scanning mode then click Scan to find remnants of Perfctl.
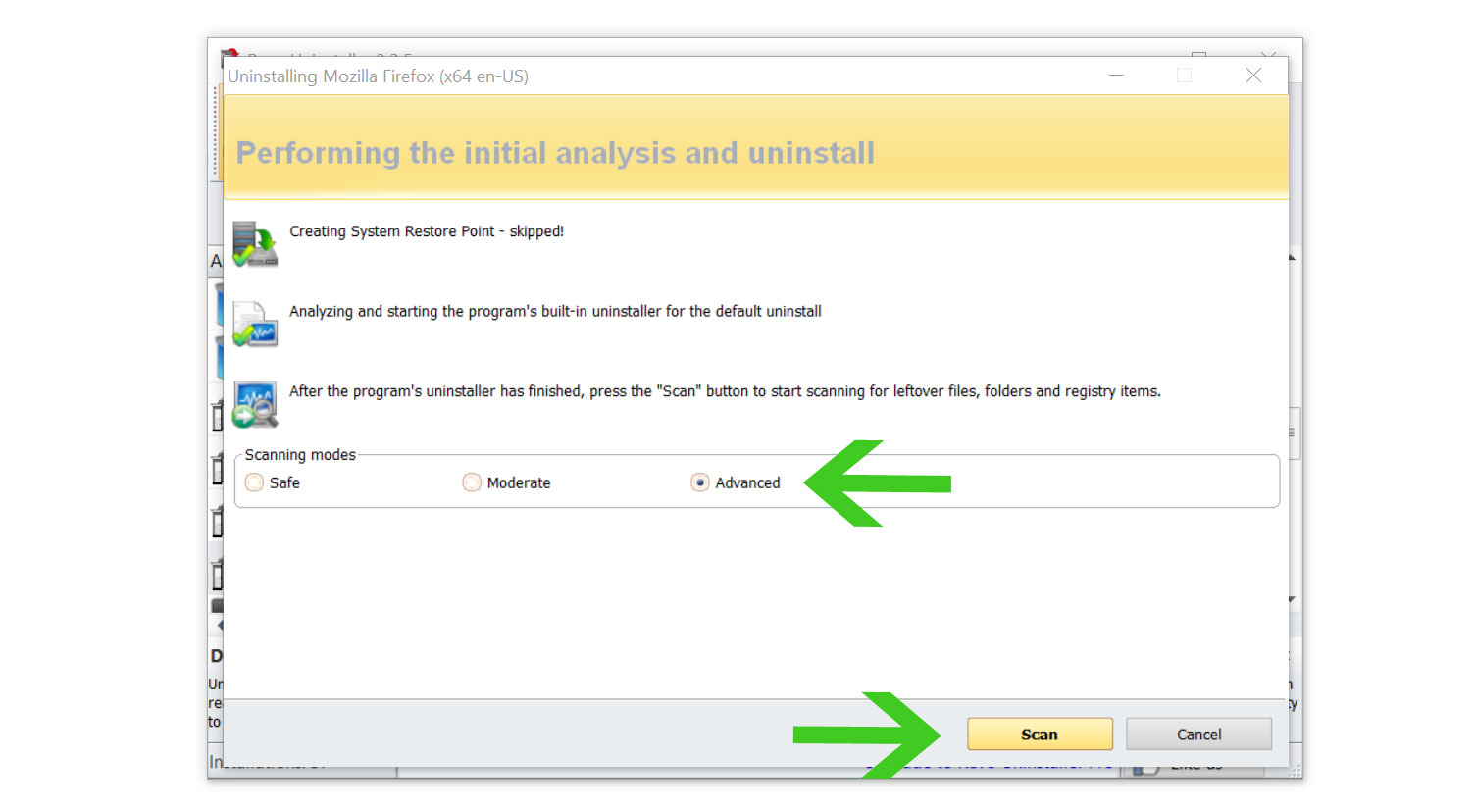
- A window will pop-up and show all of the leftovers and changes made by the program uninstalled a while ago.
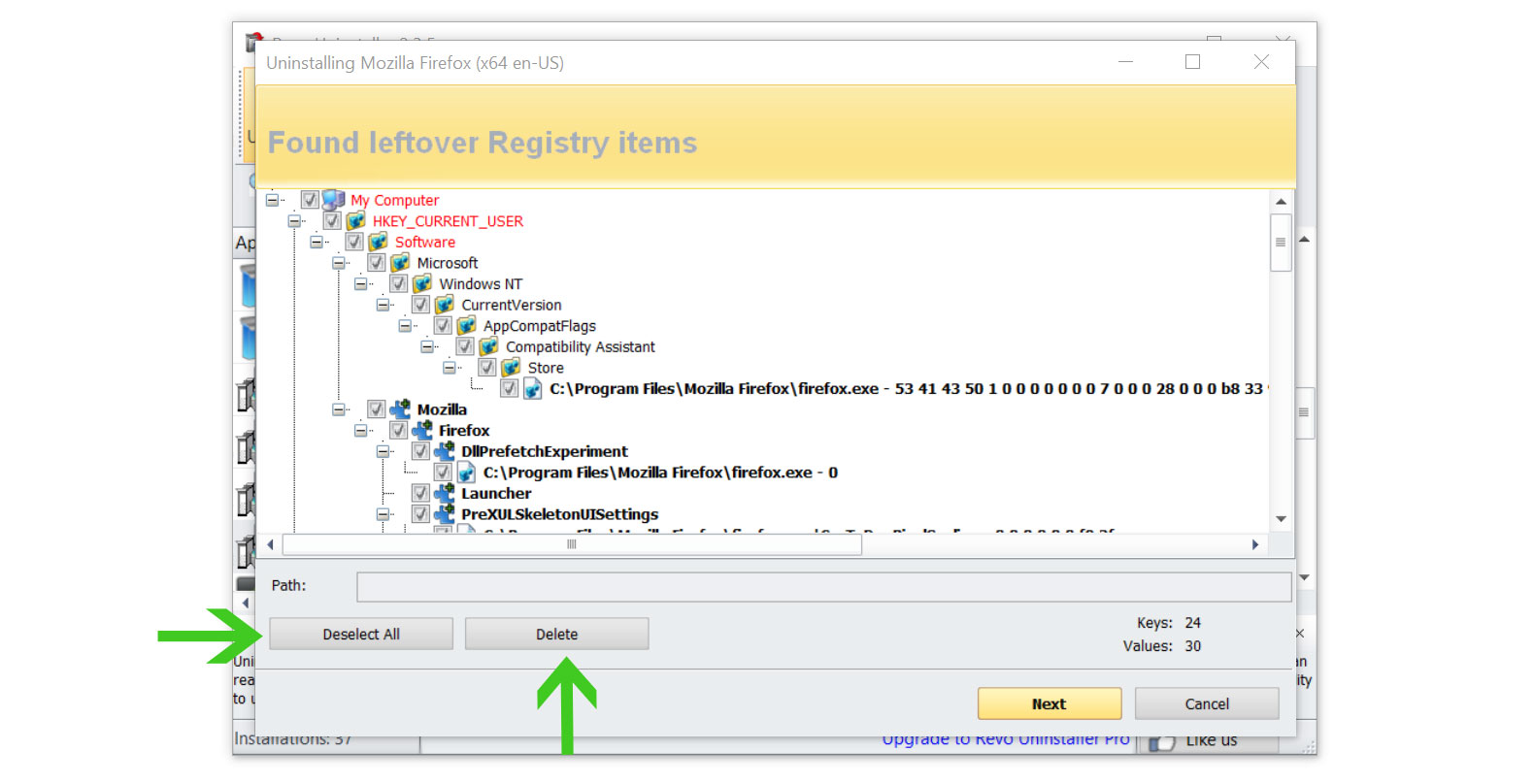
- Click the Select All button and hit Delete to remove the leftovers found on the Windows Registry.
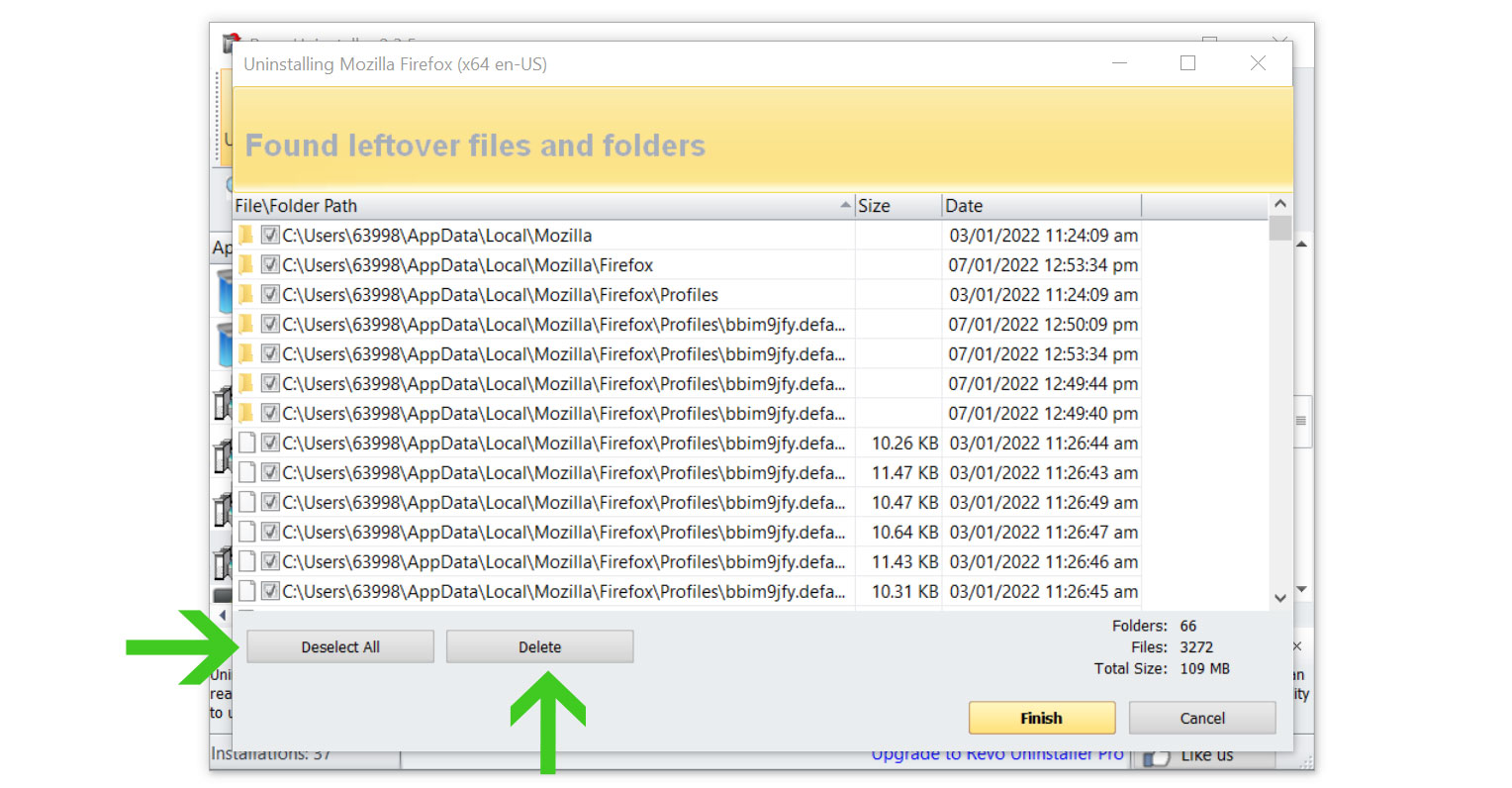
- Some leftover files may be found, click Select All then Delete them as well.
- Once the window closes, you have successfully removed the adware threat from your system.
Utilize Malwarebytes Anti-malware
This program is one of the most effective anti-malware programs available.  They have some of the greatest threat detection software, ensuring that any unwanted threats on your computer are totally eliminated. If the provided programs cannot remove the threat, you can utilize this antivirus program to complete the task. Furthermore, even if Perfctl is completely removed from the computer, we recommend that you run a complete scan just in case.
They have some of the greatest threat detection software, ensuring that any unwanted threats on your computer are totally eliminated. If the provided programs cannot remove the threat, you can utilize this antivirus program to complete the task. Furthermore, even if Perfctl is completely removed from the computer, we recommend that you run a complete scan just in case.
- Visit the antivirus website or click the button above to download the most up-to-date version of the software that best suits your requirements.
- Follow the software installation instructions until they are completed.
- Run a complete malware scan on the machine and wait for it to finish.
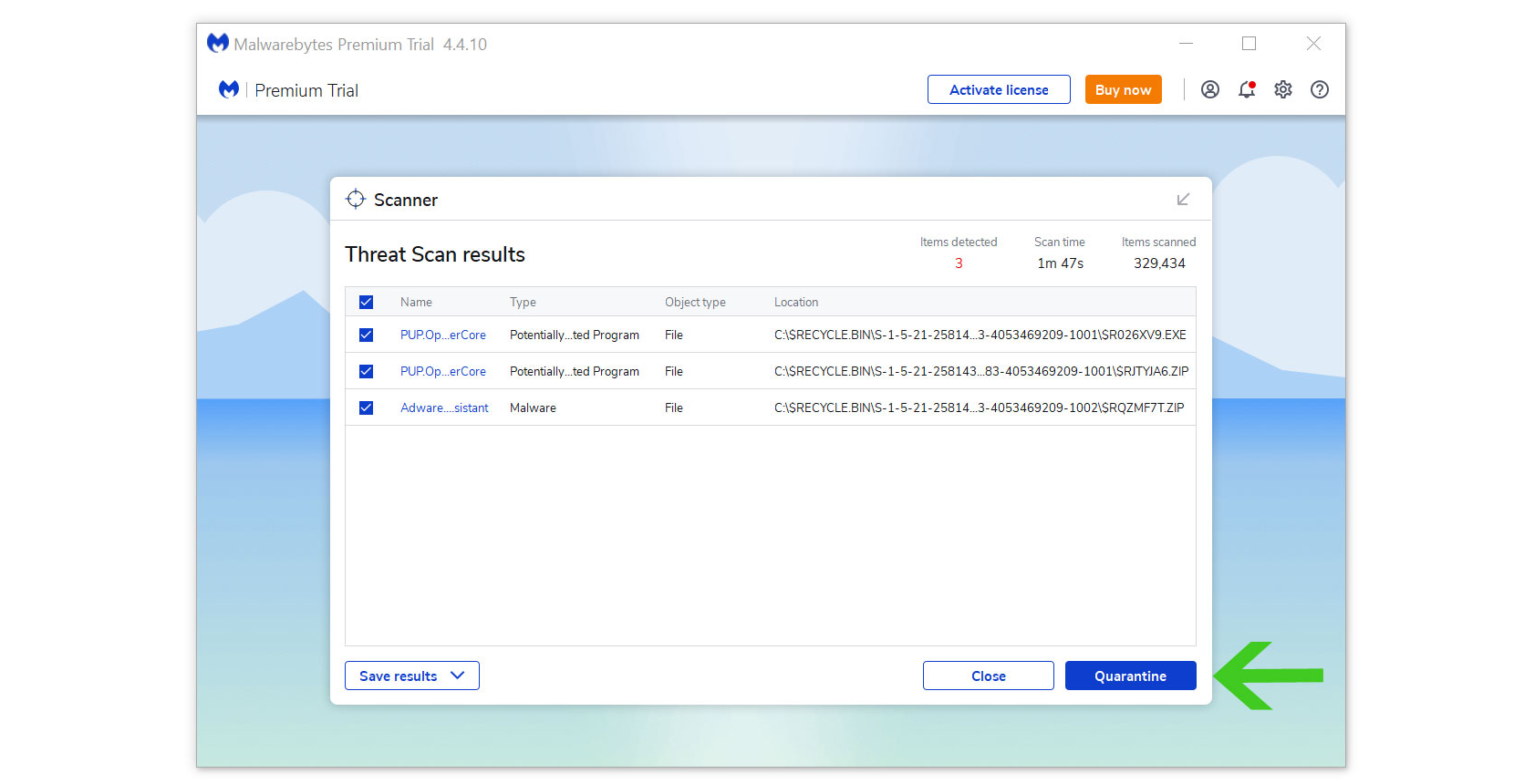
- All the detected threats found on the computer will be shown on the screen and clicking the “quarantine” button to remove them.
Perfctl, as well as any other harmful threats discovered on the computer, should be eliminated once the process is complete. We also recommend to use Malwarebytes Real Time Protection, which will secure your machine and detect any threats as soon as they appear.
