The Hosts file, which is an essential component of the Windows operating system, acts as a local mapping of IP addresses to hostnames.
It is critical in resolving domain names to IP addresses and assisting your computer in locating and connecting to websites. Despite its importance, the Hosts file is vulnerable to malicious attacks.
The accessibility of the Hosts file is the key reason it becomes infected. It can be altered by both normal apps and, unfortunately, malware because it is located deep within the system files.
When malware acquires access to the Hosts file, it can divert your web traffic to malicious sites, capture critical information, or even prevent access to genuine websites.
Malware typically exploits system vulnerabilities or takes advantage of user behavior, such as downloading infected files or accessing hacked websites.
Once inside, the virus attempts to compromise the Hosts file as part of its strategy to control and modify the behavior of your system.
What you need to know about the Hosts file
The Hosts file, occasionally referred to as ‘hosts.txt,’ is a plain-text file with no extension. It acts as a local DNS (Domain Name System) resolver, storing IP address-to-hostname mappings.
When you type a URL into your browser, the operating system first looks in the Hosts file before requesting external DNS servers.
If an entry is found, the accompanying IP address is used to connect to the website instead of going through the DNS query process.
The Hosts file, which is located in the C:\Windows\System32\drivers\etc directory, is an important component in the network connection process.
Users and apps can change this file manually, adding custom mappings or redirecting specific domains.
Malware uses the Hosts file to manipulate a user’s internet experience in a sneaky and effective manner. Attackers might fool users into inputting important information on bogus sites by redirecting frequently frequented websites to malicious IP addresses. This technique, known as DNS spoofing or pharming, is commonly employed in phishing assaults.
Furthermore, malware may modify the Hosts file to prohibit users from visiting security-related websites, preventing them from upgrading their antivirus software or accessing internet resources that could aid in malware removal.
In some situations, attackers may utilize the Hosts file to disable security mechanisms, making it more difficult to identify and remove malware.
Remove Malware From Hosts File (Hosts.txt)
Our team has attempted and tested each of the techniques listed below because this issue may have numerous primary causes. Try the following one if the first doesn’t work for you until the issue is resolved.
Step 1: Open and review Hosts file
1. Press the Windows key + E to open File Explorer. Navigate to the C: drive, then open the Windows folder.
2. Inside the Windows folder, locate and open the System32 folder. Within the System32 folder, find and open the drivers folder.
3. Inside the drivers folder, locate and open the etc folder. In the etc folder, look for a file named hosts with no file extension.
4. Right-click on the hosts file. From the context menu, select Open with and choose a text editor like Notepad. Ensure you choose Run as administrator to grant the necessary privileges.
5. Carefully examine the content of the file. Legitimate entries consist of IP addresses followed by hostnames.
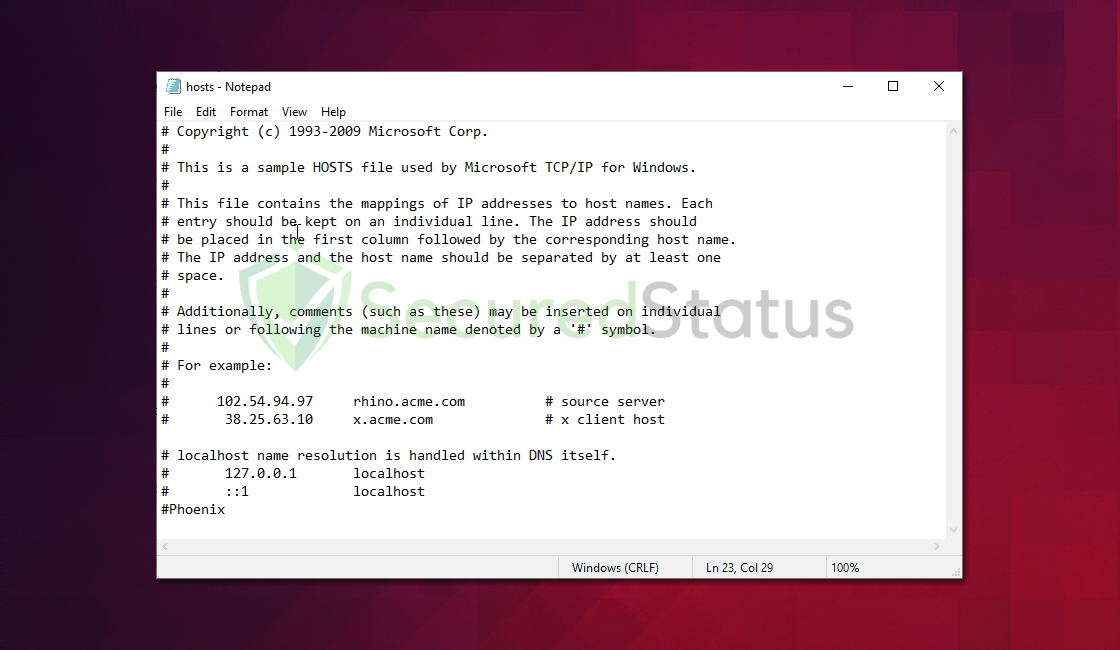
6. If you want to restore the Hosts file to a clean state, use the provided plain Hosts file template:
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to hostnames. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding hostname.
# The IP address and the hostname should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
#
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
7. Copy the content above and paste it into Notepad, which you opened with administrator privileges.
8. After reviewing, removing, or restoring entries, save the changes to the Hosts file.
9. Click File in the Notepad menu. Select Save to save the changes. Close Notepad to complete the process.
Step 2: Scan your computer with an antivirus software
If malware configures the hosts file, it shows that malware is present on the computer; therefore, it is critical to eliminate it, and the easiest method to do so is to scan with a powerful antivirus software and remove it with a single click.
An antivirus program is your all-in-one solution for dealing with malware. It serves as a preventive and corrective step, quickly detecting and eliminating malware from your device.
We cannot emphasize enough the significance of using antivirus software especially when facing downloading files from unknown sources in the internet.
Having antivirus software on your computer offers several significant benefits, including:
- Detection, filtering, and automatic removal of malware ranging from harmless adware to extremely severe ransomware.
- Providing caution and notifications for possibly risky websites that you may visit, helping you in mitigating online risks.
- Antivirus threat databases are regularly updated to ensure the detection of new viruses and the protection of your device.
- Keeping your operating system clean by protecting all files on your computer, assuring their safety and integrity.
Which antivirus should I use?
The answer is dependent on how you use your computer, as several antivirus applications on the market offer benefits and drawbacks. Because most of them identify and remove malware at the same rate, we recommend choosing your choice based on research.
For example, if you use your computer for resource-intensive applications such as video editing, you might want to avoid resource-consuming antivirus programs.
Fortunately, there are numerous publications that provide extensive comparisons of each antivirus’s merits and cons. However, for the best of all worlds, we recommend one of the following antivirus programs:
The majority of free versions are already sufficient for removing and blocking viruses from your computer. Some antivirus products also provide free trials that allow you to learn more about their capabilities before making a purchase choice. However, in the end, the free version usually provides everything needed to remove malware.
Protective measures for better overall security
Removing trojan viruses and malware from the device is one thing; keeping it secure for the future and for a long period is a different thing and will require certain things to make sure you are secured, especially if you do not know most of the ins and outs of the device you are using.
Cybercriminals are always stepping up their game to make sure they infect users and extract data and money from them.
We encourage you to take the actions listed below to ensure complete security before leaving this page because we strongly promote web security and having a secure online presence.
Safeguard your data and privacy online by using a VPN application
VPNs, also known as virtual private networks, guarantee your safety and complete anonymity while you browse the internet.
In contrast to a firewall, which monitors and blocks potentially harmful connections in the network, A VPN hides the user’s connection via a tunnel so that it would appear to third parties as a different IP address and location.
This ensures that your data won’t be leaked because the program hides it. Be aware that visiting infected websites may cause your IP address and location to be disclosed; however, if you use a VPN, this will prevent your true IP address from being revealed to malware actors.
Utilize an adblocker when browsing the internet
Installing an adblocker on the browser is the best way to prevent hijacker viruses such as $$custom_field:vname$$ as well as other threats such as pop-ups, redirects, and unwanted toolbars.
Additionally, by blocking malicious websites before users can even access them, it is possible to prevent malware from being downloaded.
In this case, we recommend uBlock Origin, which is an open-source AdBlock extension that comes at no cost and is free forever. It is one of the most reliable plugins out there, ensuring that every advertisement on a webpage will be blocked.
The majority of pop-up advertisements, whether they include malware or not, will be filtered by the extension and no longer be displayed to you. Currently, uBlock Origin is not available for Mac or iOS users, but there are plenty of free options on the market, such as AdBlock for Safari.
Use a firewall to prevent cyber attacks
A security firewall is required for every internet connection that is made. It is an essential tool that enhances security and stops online attacks.
Through a security mechanism, it controls incoming and outgoing network connections on your system and network and filters the undesirable ones. Consider it a further barrier against malicious assaults and zero-day exploits.
