Many people use their ASUS TUF computer for a variety of professional and personal objectives. Given the constant advancement of technology, computers have become as common in our daily lives as mobile phones.
However, because of its widespread use in our daily lives, having the ASUS TUF infected with malware might have serious effects. This is especially concerning because these devices frequently hold sensitive data, and an infection might impair normal day-to-day operations.
In this article, we will look at how to remove malware from your ASUS TUF computer. This will ensure that you can use your device safely and avoid the negative consequences of malware infections.
ASUS TUF malware infection
Many users rely on their computers for business and school, with ASUS TUF being a common everyday choice. Malware infestations, unfortunately, can have a considerable influence on your daily life.
Unwanted pop-up advertisements, overheating, and crashes, for example, can impede your work if you’re using your computer to attend classes and take lecture notes.
But the worries don’t end there. Malware can go above and beyond by following, recording, and spying on you. Cybercriminals may obtain access to your camera, microphone, and other crucial hardware components in the event of a ASUS TUF system infection, posing a major threat to your privacy and security.
Signs that your ASUS TUF is infected
It is relatively simple to distinguish between an infected ASUS TUF and one that is malware-free. Malware exhibits similar actions throughout its several known variations, consistently exploiting the user’s computer.
Here are some common signs of malware infection:
- Pop-up ads appearing, launched by the user’s browser or operating system.
- Unauthorized attempts to get elevated access privileges within your system may be detected.
- A sudden drop in system performance, with the machine slowing down for no apparent reason.
- The mouse or keyboard acting on their own without user intervention.
- Your computer experiences sudden spikes in CPU or GPU usage, indicating cryptocurrency mining activities.
- Unexpected computer shutdowns or restarts without user input.
- Changes to your browser’s homepage or start page.
- System becomes unstable, with crashes or spontaneous reboots occurring without user intervention.
- Redirected searches to unknown domains.
- Your system’s firewall or antivirus being turned off without your involvement.
If you can recognize and observe a few of these common signs of malware on your ASUS TUF computer, it indicates that it is infected with malware.
Potential risks of having your ASUS TUF infected
An infected ASUS TUF does more than just cause problems with your computer; it frequently allows fraudsters to access your data, making it a main means of malware infection.
As previously stated, this disruption can be especially troublesome when utilizing ASUS TUF for instructional purposes. However, the situation might become even more grave if you use your computer for business and work-related purposes.
A malware infection at work can drastically limit your productivity, negatively compromising your professional life. Furthermore, if you use your ASUS TUF at work, the malware can spread across the office, potentially inflicting harm to your entire organization.
We underline the broad threats involved with malware if it is allowed to remain on your computer without being removed. Given these risks, it’s critical to remove the malware from ASUS TUF as soon as possible.
ASUS TUF malware threat summary
Below is a threat summary of ASUS TUF malware infection, providing essential details and the recommended course of action.
| Computer Description | ASUS TUF laptop running Windows 10 & 11. |
|---|---|
| Malware Infection Details | Infection Source: Likely from downloading a malicious file from an untrusted website or opening an infected email attachment. Symptoms: Sluggish performance, unexpected pop-up windows, increased network traffic, unauthorized access, and possible data loss or theft. |
| Threat Assessment | Risk Level: High Data at Risk: Personal and sensitive information, including login credentials, financial data, and personal documents. Potential Impact:– Data Theft: The malware may be stealing personal and financial information. – Data Loss: Data corruption or deletion could occur. – System Compromise: The attacker could gain control of the computer. – Privacy Invasion: Your personal activities and sensitive information may be monitored. |
| Recommended Actions | Scan and remove the malware using an updated antivirus or with the built-in Windows Defender. It is also suggested to utilize Microsoft’s Malicious Software Removal Tool (MRT). |
To prevent the harm associated with an infected ASUS TUF, it’s crucial to remove the malware as soon as possible. This action ensures the best possible outcome and ensures the long-term safety and cleanliness of your computer.
Please follow the step-by-step tutorial below to remove the malware from your ASUS TUF and guarantee a malware-free computer.
Remove malware from ASUS TUF
The steps below will help you through the process of removing malware from your ASUS TUF computer. Following these procedures will help you ensure the safety and security of your device.
 100% Tested, Working and Up-to-Date
100% Tested, Working and Up-to-DateWe are committed to providing people with accurate methods of protecting their devices against malware. We prioritize prevention and assess our instructions on a regular basis to ensure their effectiveness. Furthermore, our guides are always unbiased and free. (Learn more)
Please inform us using our Contact Page if you come across a method that does not appear to be working. We value the feedback you provide and will address the issue as soon as possible.
Remove malware with a click by using an antivirus software
Antivirus software provides a comprehensive solution for malware protection. It works as both a preventive and a removal tool, detecting and eliminating malware from your computer efficiently.
If you suspect that your ASUS TUF has been infected with malware, running an antivirus scan will take care of everything for you. Any hidden malware on your computer will be detected and removed as soon as you start the check.
This is accomplished through heuristic and signature-based scanning, in which the antivirus software examines your computer for files that have the potential to do destructive behaviors. It effectively detects and removes all malware.
Furthermore, if malware tries to infect your computer, the antivirus software will intercept it, preventing downloads from even initiating.
Having antivirus software on your computer provides several key advantages:
- Identification, blocking, and automatic removal of a wide range of malware, from less harmful adware to highly dangerous ransomware.
- Providing warnings and alerts for potentially harmful websites, helping you steer clear of online threats.
- Regularly updating its threat database, ensuring immediate detection of new malware and enhancing your device’s security.
- Maintaining the integrity of your operating system by safeguarding all files on your computer, ensuring their safety and reliability.
But which antivirus should I use?
The answer is dependent on how you use your computer, as different antivirus software on the market has benefits and drawbacks. We recommend selecting your choice of antivirus based on how you use your computer since almost all available software can detect and eradicate malware at the same pace.
For example, if you use your computer for resource-intensive applications such as video editing, you may want to avoid antivirus software that consumes a lot of resources.
Fortunately, there are numerous reviews that provide extensive comparisons of the advantages and cons of each antivirus. For the best of all worlds, we recommend one of the antivirus programs indicated below:
The majority of free versions are already enough for malware removal and prevention on your PC. Some antivirus software also provide free trials so you may learn more about their capabilities before making a purchase decision. However, in most cases, the free version has everything required for removing malware.
Alternative option: Scan your computer with Windows Defender
Windows Defender is a trustworthy built-in system security utility software. Although it is not the best option, it is capable of removing a large number of well-known malware threats, including those that often infect computers, such as the ASUS TUF.
If you’re not sure how to use Windows Defender to scan for malware, please follow the steps below:
1. Press the Windows key on your keyboard to open the Start menu.
2. Type Windows Security and select it from the search results. This will open the Windows Security app.
3. In the Windows Security window, click on Virus & Threat Protection from the left-hand menu.
4. Under the Virus & Threat Protection section, locate and click on Scan options to expand the options.
5. You’ll see options for different types of scans. Select Full Scan. A full scan will thoroughly check your entire system for malware, which may take a longer time than a quick scan.
6. After selecting Full Scan, click on the Scan Now button to begin the process.
7. Windows Defender will now scan your entire system for malware, including files, programs, and system settings. This process may take some time, depending on the size of your system and the number of files it needs to scan.
8. Once the full scan is complete, Windows Defender will display the results. If it finds any threats, it will list them in the scan results. If malware or threats are found, you will have to take various actions, such as removing or quarantining them.
You’ve run a comprehensive scan of your computer to look for any potential malware that may have infected your ASUS TUF.
What’s the point of a complete scan? This is due to the speed with which malware can spread and infect numerous folders and system functions.
Nonetheless, if you’re still concerned about the presence of malware on your ASUS TUF, even after scanning with Windows Defender, don’t be.
We still have measures to follow to get rid of malware from your ASUS TUF computer, which you may follow below.
Remove malware from ASUS TUF manually
There is a small probability that malware escaped detection by antivirus software and Windows Defender.
So, to prevent malware from escaping and ensure that it is completely deleted from the computer, you can manually remove malware on your computer in addition to employing software to check the ASUS TUF machine for malware.
Please follow the step-by-step manual removal method below.
Step 1: Remove unwanted programs from your computer
1. From the Windows search bar at the bottom of your screen, search for Control Panel and click the result that matches the same application.
2. You will see different options, such as System and Security, as well as User Accounts. But what you want to click is the Uninstall a program under the Programs section. Depending on your Windows version, hovering over the uninstall section will be relatively the same.
3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed.
4. Right-click the suspected virus program and click Uninstall to get rid of it (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed.
There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
Alternative: Remove the program with Revo Uninstaller
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a handy tool for Windows users.
This uninstaller not only removes programs from the computer but also deletes their changes from the Windows Registry, Host File, etc. The steps below will guide you on how to install and use Revo Uninstaller to get rid of the source of ASUS TUF redirection.
1. Click the button below to proceed with installing Revo Uninstaller on your computer since we have made an in-depth guide on how to use it on the following page. On the other hand, you can also head over to Revouninstaller.com and download it from there.
2. After the setup file (revosetup.exe) has finished downloading, run the installation wizard, read the license agreement, and click agree to proceed to the next step of the installation. Follow the procedure and wait until the installation of the software is complete.
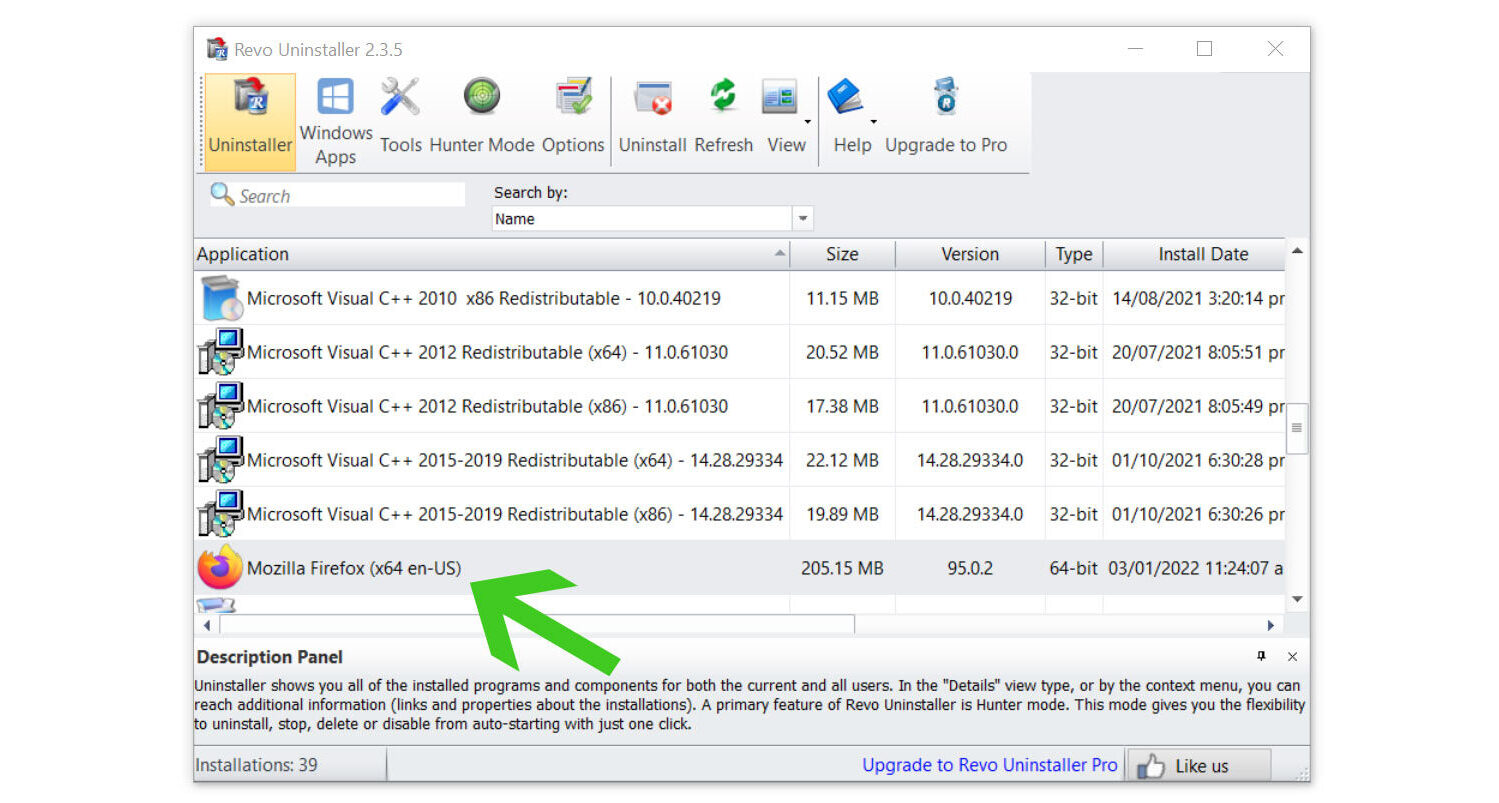
3. Once the software has launched, find the unwanted application that needs to be removed and double-click the program to uninstall it. (We will be using the Mozilla Firefox browser as a demonstration.)
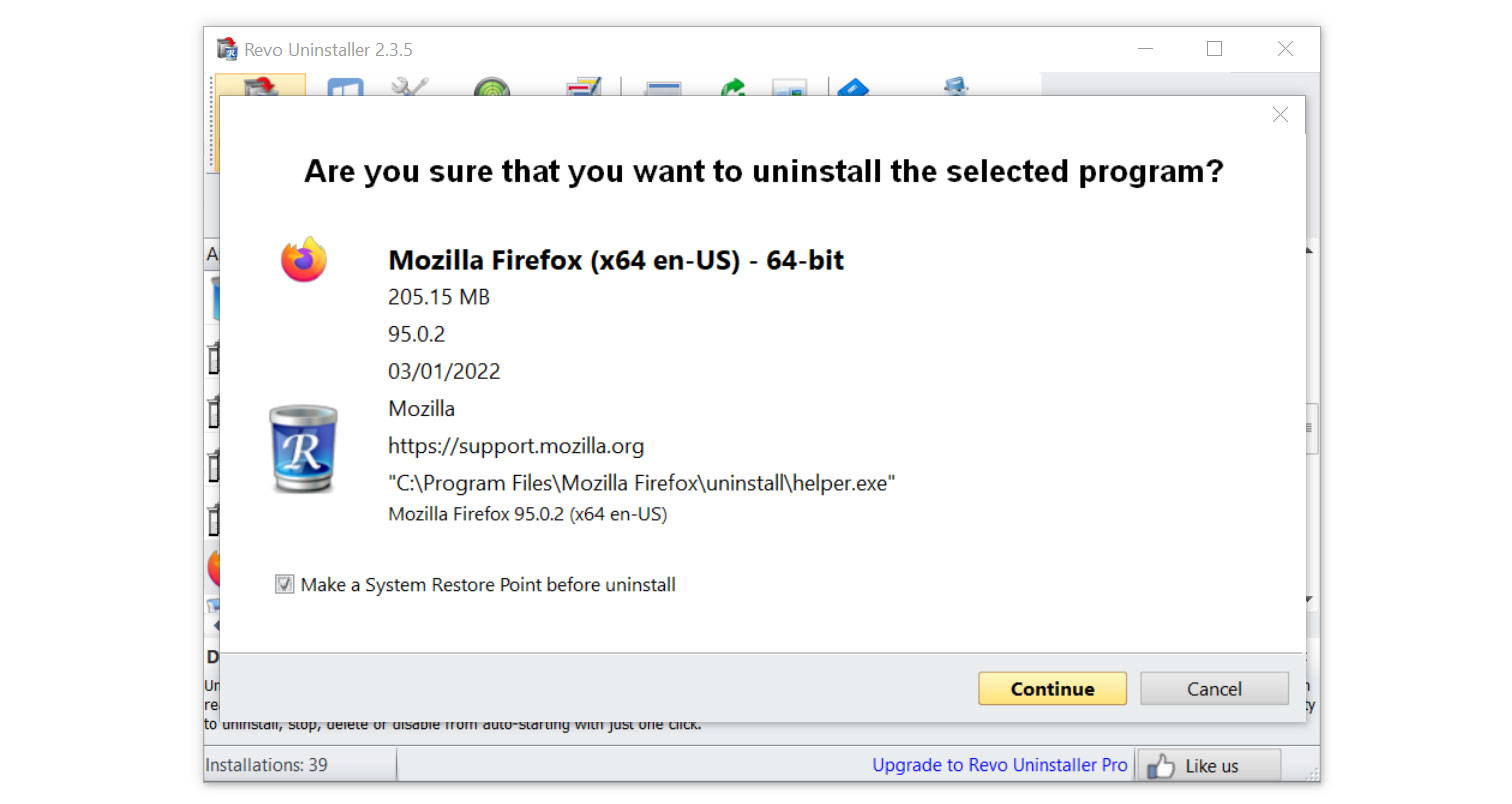
4. Click on the Continue button and follow the procedure to start uninstalling the program. It is also advised to make sure that a System Restore Point is made before the uninstallation, just in case.
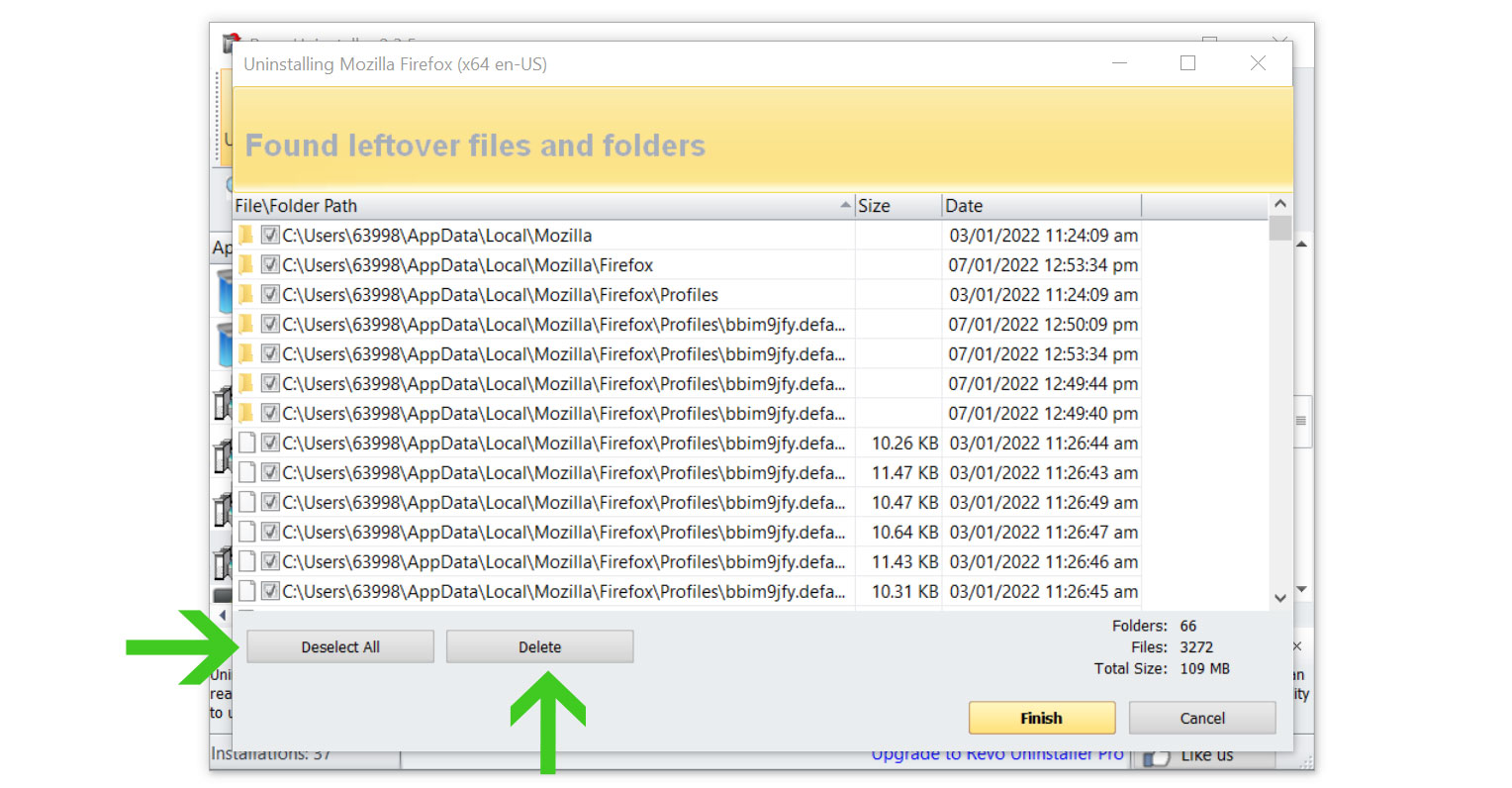
5. You will be prompted to choose a scanning mode. From the three options available, select Advanced mode, then click Scan.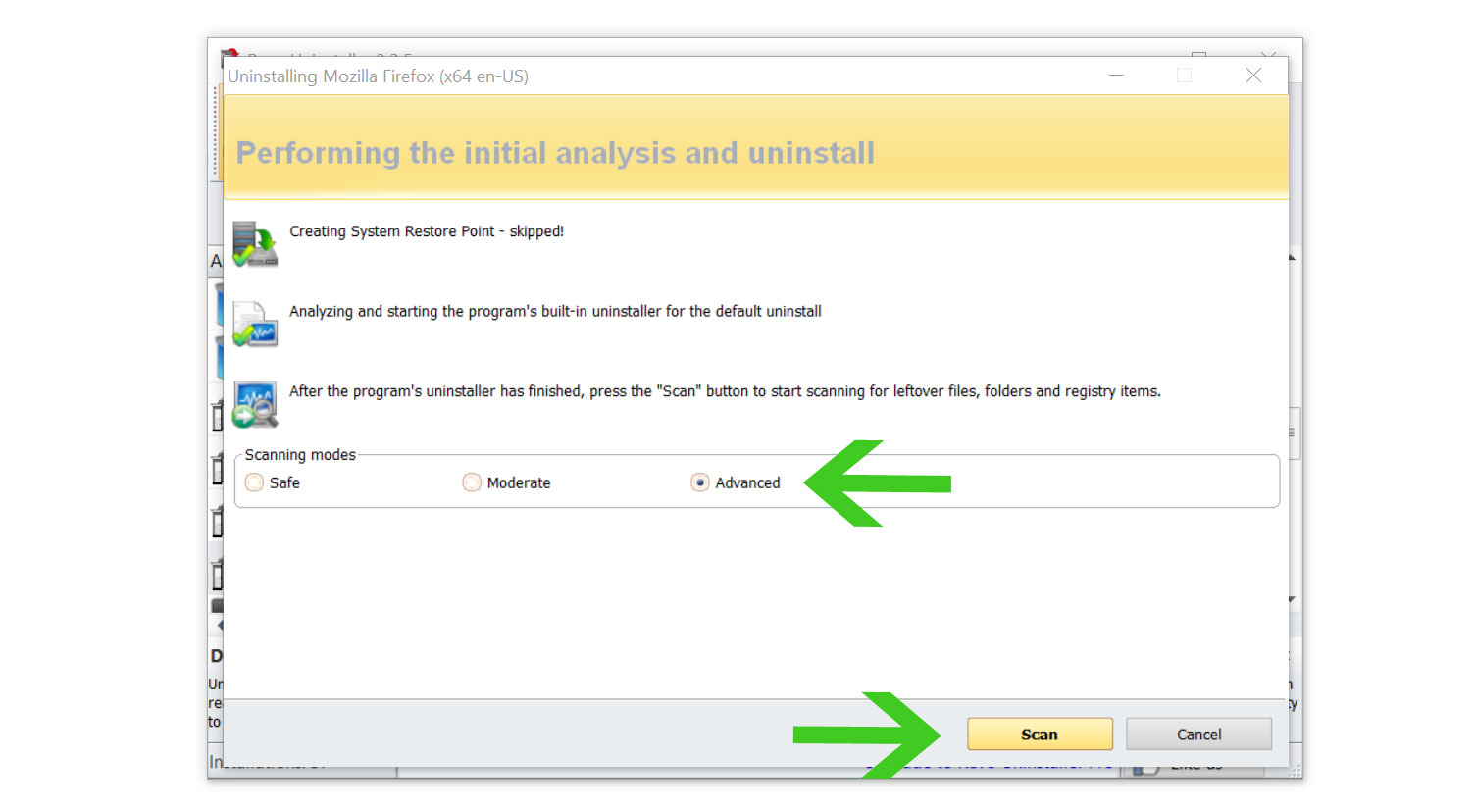 6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
Once the window closes, you have successfully removed the detected ASUS TUF from your computer system.
Step 2: Delete browser extensions you do not recognize
 For Google Chrome:
For Google Chrome:
1. Open the browser and click on the three horizontal lines at the upper-right corner of the window screen. Once the drop-down menu opens, hover over Extensions and select Manage Extensions on the submenu. On the other hand, you may also type chrome://extensions on the URL bar to directly access the browser extension page.
2. The extensions page will then open in a new tab, showing all installed plugins on the browser. Find ASUS TUF, and deactivate the browser extension by toggling the blue switch below its name and description (We will be using AdBlock as an example). After that, you may now click the remove button to get rid of the extension virus from the Chrome browser.
3. If the switch is disabled, then you will need to remove it directly from the extensions folder of the browser. To do this, first, you have to select the plugin and look at its ID as shown in the URL bar. (See the image below for an example.)
4. Open File Explorer and go to the folder where Chrome stores the ASUS TUF browser extension. The default location will be at:
C:\Users\YOUR NAME\AppData\Local\Google\Chrome\User Data\Default\Extensions5. You will see a list of folders, each with different hashes. Find the folder matching the ID of the malicious ASUS TUF extension, then right-click and delete it. Make sure the browser is closed before proceeding to delete the folder.
 For Mozilla Firefox:
For Mozilla Firefox:
1. Launch the Firefox browser and open the menu by clicking the three horizontal lines, which can be located in the upper-right corner of the program. Once the drop-down menu opens, click on Add-ons and Themes. On the other hand, you may also type about:addons on the browser URL bar to enter the Add-ons Manager.
2. From the left-side menu, go to the Extensions page and view all of your browser extensions installed on Firefox. Toggle the blue switch near ASUS TUF to deactivate the plugin, then click the three horizontal dots beside the toggle and select Remove to get rid of it from the browser (We will be using Adblock Plus as an example).
3. If the toggle is locked or unable to be removed, then you will have to manually remove the extension from the browser’s extension file directory. Open File Explorer and go to the following directory where Mozilla Firefox keeps its browser extensions; this can be located via:
C:\Users\Your Username\AppData\Roaming\Mozilla\Firefox\Profiles4. You will see Mozilla Firefox profiles, and depending on how many browser profiles you have, go to the default ones you have, such as default-release in some cases, and click on the extensions folder inside the profile.
5. It will be difficult to determine the extensions of the folders you see because they have generated IDs. To make things simple, you should delete every .xpi extension file and make sure the Microsoft Edge browser is closed when doing so.
 For Microsoft Edge:
For Microsoft Edge:
1. Open Microsoft Edge and enter the following URL to enter the extensions manager page of the browser: edge://extensions on the other hand, you may click the horizontal three-dot menu and click Extensions from the multiple options shown. Then a small window of extensions will show; click on the Manage extensions to enter the same page.
2. The page will then show all of your installed extensions within the Microsoft Edge browser. Find ASUS TUF and disable it by toggling the blue switch (We will be using the AdBlock extension as an example). Then proceed to uninstall it by clicking the remove button right next to Details.
3. If you were unable to remove the malware plugin, then you will have to head over to the browser’s extension files via File Explorer to remove it manually. To do so, please head over to the extensions tab first, and now click the details next to the remove option.
4. Open File Explorer and head over to the following directory where all browser plugins within Microsoft Edge are stored:
C:\Users\Your Username\AppData\Local\Microsoft\Edge\User Data\Default\Extensions5. Now find the folder with the same extension ID as the ASUS TUF plugin. It indicates that the following folder contains the files for the particular virus extension: Right-click it and delete it.
When you open the browser again, the malicious extensions have now been completely removed.
Step 3: Run a disk cleanup
1. Type Disk Cleanup in the search box on the taskbar and press Enter.
2. Choose the drive you want to clean up (usually “C:”) and click OK.
3. In the Disk Cleanup dialog box, select the file types you want to clean up.
4. Click OK after selecting the desired file types.
5. A confirmation prompt will appear. Click Delete Files to proceed.
6. Disk Cleanup will start deleting the selected files. Once the cleanup is complete, the program will now close, indicating that the process is finished.
Step 4: Delete prefetch and temporary files
1. Press Win + R on your keyboard simultaneously. This will open the Run dialog.
2. In the Run dialog, type prefetch and click OK or press Enter.
3. A new window will open showing the contents of the C:\Windows\Prefetch folder.
4. Select all the files within this folder (you can press Ctrl + A to select all) and press Delete.
5. In the Run dialog again, type temp and click OK.
6. Again, select all the files within this folder (press Ctrl + A) and press Delete.
7. In the Run dialog once more, type %temp% and press Enter.
8. Lastly, select all the files within this folder (press Ctrl + A) and press Delete.
Step 5: Run the Windows Malicious Software Removal Tool
1. Press the Windows key on your keyboard or click on the Windows logo in the taskbar to open the Start Menu.
2. In the search bar, type cmd or Command Prompt.
3. Right-click on Command Prompt in the search results and select Run as administrator. This will ensure that you have the necessary permissions to run the tool
4. In the Command Prompt window that opens, type mrt and press Enter.
5. The Windows Malicious Software Removal Tool will start, and the graphical user interface will appear. Click Next to proceed.
6. You will be presented with the option to perform a Quick scan or a Full scan. A Full scan scan is usually the most efficient for most users. Select Full scan and click Next.
7. The tool will start scanning your computer for known malware. This may take some time, depending on your computer’s speed and the number of files on your system.
8. Once the scan is complete, the tool will display a summary of the results. If no malware is found, it will inform you that your computer is clean. If malware is detected, it will provide details about the malware found and you can take action by removing it.
9. Click Finish to exit the Windows Malicious Software Removal Tool.
Following the methods outlined above, your ASUS TUF should now be secure and malware-free. Rest assured that we have taken critical steps to scan for and remove malware using the most efficient methods available.
However, it is still necessary to exercise caution in order to keep your ASUS TUF from becoming infected again. We’ve offered some safety advice and precautionary steps to help you avoid malware in the future to help you stay safe.
How to keep your ASUS TUF safe
Malware infections on the ASUS TUF can pose a considerable risk to both the computer and the user, especially when users are uninformed of the potential harm this malware might cause once the system is hacked.
Here are some important guidelines, safety measures, and best practices that all users should be aware of to ensure user safety and prevent further malware infections that could infect the ASUS TUF and the files and data contained within.
Do not surf on unreputable websites
Taking preventative measures, such as avoiding accessing dubious websites, can dramatically minimize your risk of malware infection.
Illegal streaming platforms, pirating websites, and other sites that host unfiltered and uncontrolled adverts are examples. The advertisements displayed on these websites may result in malware infections.
Simply avoiding such websites would keep you safe from potentially hazardous adverts. This efficiently rids your computer of malware because the possibilities of downloading malware when browsing the web are lowered to zero.
Make sure Windows Defender is active
This tip may appear simple, but it is quite important because many users will overlook it. When it comes to protecting your computer, Windows Defender should always be active and activated.
Since it runs in the background, users may not check the Defender settings very often to see if it is actively safeguarding their system. A software flaw or specific computer setups can mistakenly disable Windows Defender, stopping it from detecting malware.
Even if you’re not aware of it, it’s a good idea to check the Windows Defender settings on a regular basis to ensure that your computer is always safe.
Do not open files from unknown sources
This warning has been repeated numerous times by cybersecurity pros and experts, and we cannot stress it enough: Do not open files from unknown sources, particularly if they arrive by email from unknown recipients and include potentially dangerous content.
Such approaches are frequently used by cybercriminals to deceive users into fast clicking on attachments, which typically include malware.
The same caution should be exercised when downloading unauthorized materials or torrents from the internet. The risk of malware infection from such downloads is significant, and we highly advise users to avoid them entirely.
Combining this precaution with the others outlined above can help you keep your computer safe and improve your overall internet security.
