
TrendMicro security researchers discovered a sophisticated phishing effort that used DRACOON.team, a secure file-sharing tool, to trick users into disclosing Microsoft 365 login credentials.
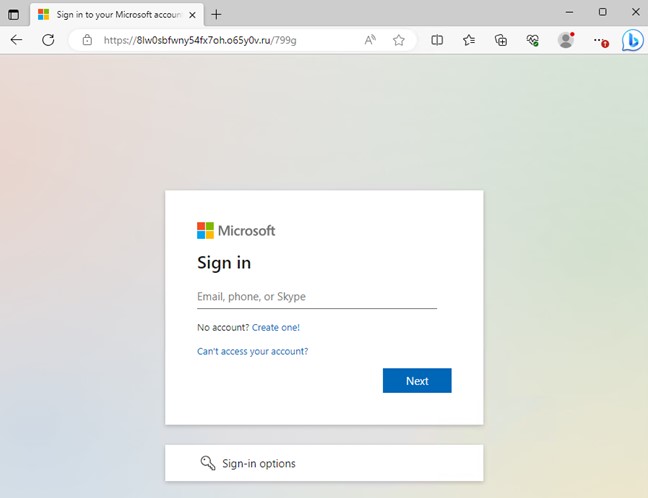
Threat actors use DRACOON as a host for a PDF document that, when accessed, leads users to an attacker-controlled server posing as a Microsoft 365 login site in this sophisticated operation.
The reverse proxies controlled by the attackers serve as intermediates, intercepting login requests and capturing victims’ passwords and session cookies.
This, in particular, allows threat actors to circumvent multi-factor authentication (MFA). Once penetrated, the stolen credentials are used to get automated access to victims’ mailboxes, allowing subsequent phishing emails to be distributed to contacts in the victim’s address book.

Unlike earlier phishing campaigns, this one employs an intermediary link within hosted documents, making it difficult to detect and avoid typical email security measures.
Phishing emails are extremely convincing because they are frequently sent from hijacked accounts within the victim’s supplier firm, making them appear trustworthy.
TrendMicro notified DRACOON of the situation, which resulted in the removal of suspected phishing attachments hosted on their server. Accounts responsible for posting these attachments have been flagged for deletion owing to a violation of the rules of service.
The research delves into the phishing email, the redirection process via DRACOON, and the attackers’ use of a bogus Microsoft 365 login page.
Researchers have also identified a malicious JavaScript (myscr759609.js) that is responsible for credential harvesting and subsequent data posting.
The researchers successfully traced the compromised accounts and gave critical data into the impact of the phishing assault by leveraging Trend Micro Vision One and Microsoft 365 sign-in events.
The study also discovered further DRACOON linkages inside the campaign, all of which impersonated Microsoft 365 and targeted victims with different subject lines.
This rigorous investigation emphasizes the need of robust incident response measures and the need for enterprises to resolve compromised accounts as soon as possible.
TrendMicro advises impacted users to update their passwords to reduce the dangers connected with this phishing effort.
