
A recent report from AhnLab sheds light on a concerning evolution in cyber threats, particularly involving the notorious LockBit ransomware.
Previously known for its conventional distribution methods, LockBit has now adapted to impersonating resumes, a tactic accompanied by the simultaneous deployment of the Vidar Infostealer.
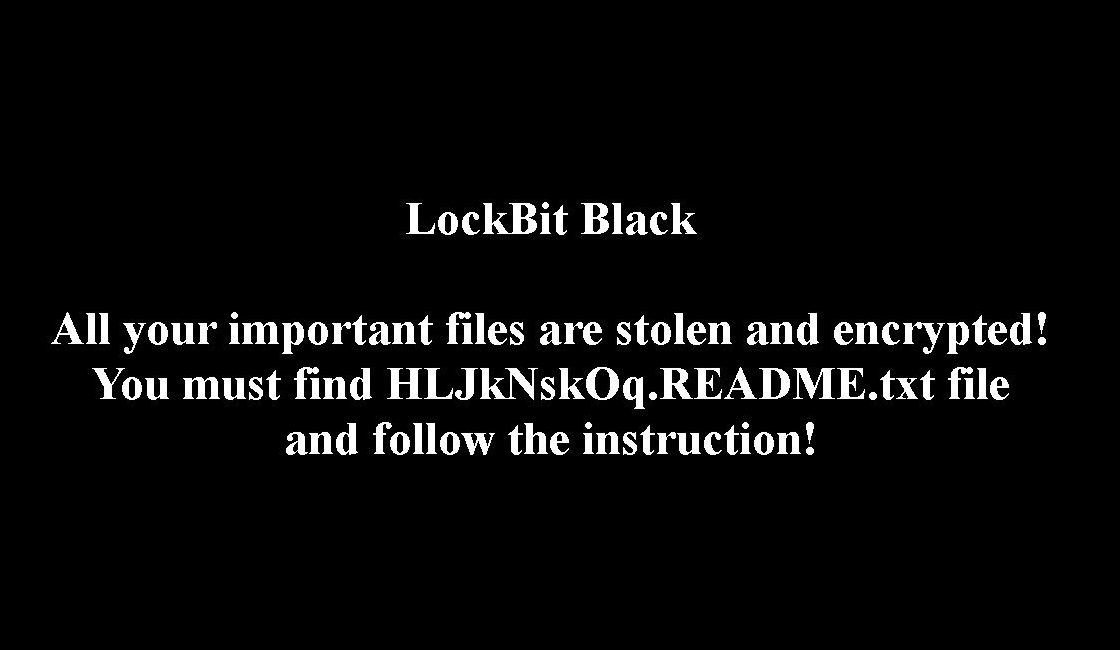
Lockbit Ransomware and Vidar Infostealer
LockBit ransomware is a type of malicious software that is aimed to prevent users from accessing computer systems in exchange for a ransom payment.
LockBit will automatically scan a network for valuable targets, disseminate the infection, and encrypt all network-accessible computer systems. This malware is used to launch highly targeted assaults on businesses and other organizations.
Vidar malware is normally sent via email, but in recent campaigns, it has also been delivered as an ISO file, which is a disk image file type often used by malware developers to package their malware.
The malicious ISO was hidden in false installers for legitimate applications like as Adobe Photoshop and Microsoft Teams in Vidar’s case, supplied via the Fallout exploit hit, and sent as an attachment to phishing emails.
Once on an infected PC, the malware employs a variety of ways to avoid detection. Among these are the usage of a huge executable file meant to fool antivirus scanners, as well as files digitally signed with outdated and potentially compromised digital certificates.
Distribution Method: Resume Impersonation
The ASEC Blog, in a post from February, detailed the emergence of a new distribution technique employed by LockBit ransomware.
This method involves the use of deceptive emails containing attachments posing as resumes. Concealed within these seemingly innocuous files are the LockBit ransomware, camouflaged as a PDF, and the Vidar Infostealer, disguised as a PPT file.
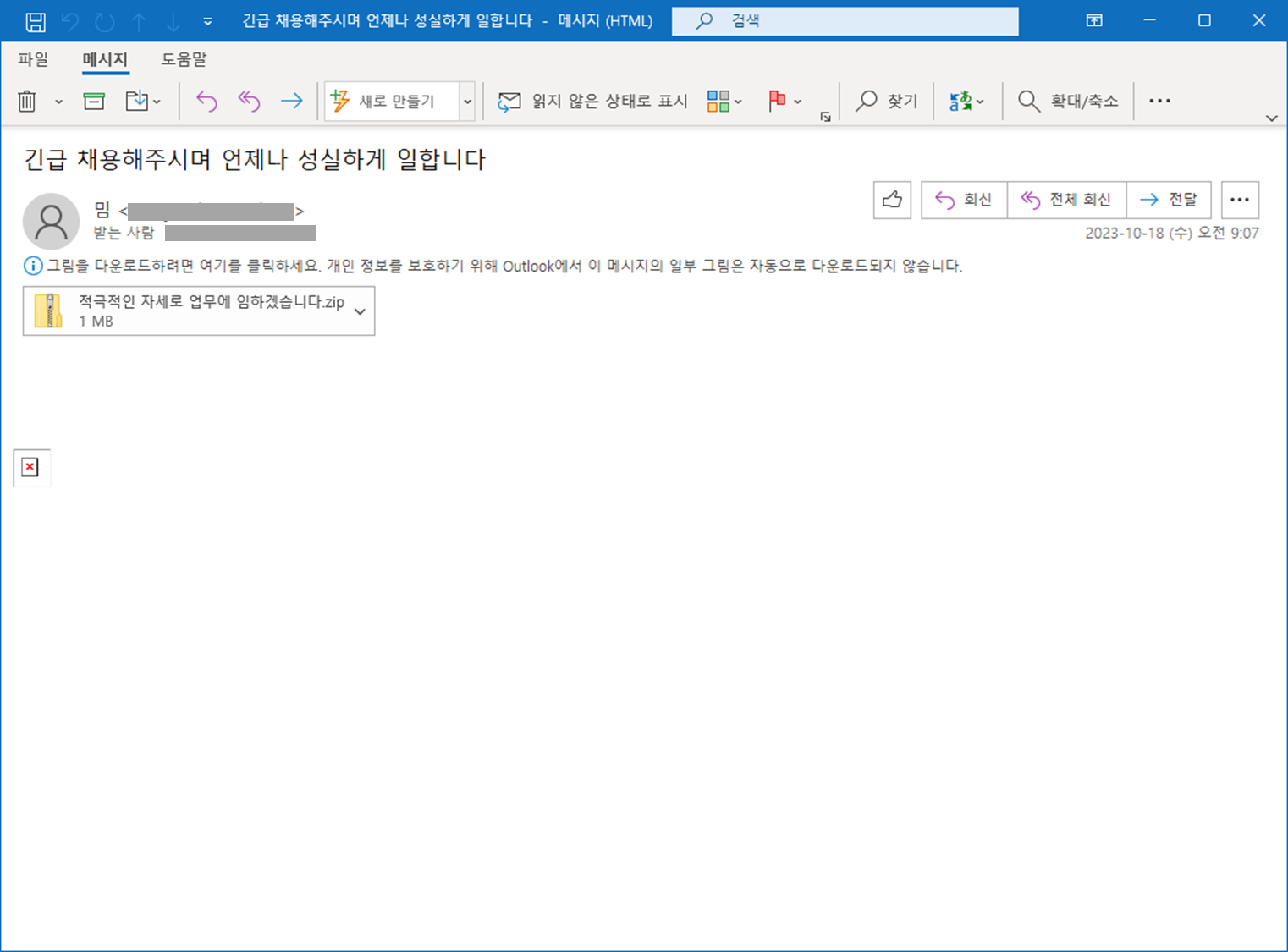
The image above displays the malicious software that was attached to an email delivered in Korean.
Technical Insights
| Description | |
|---|---|
| Attachment | ‘Resume16.egg’ conceals LockBit ransomware (PDF) and Vidar Infostealer (PPT). |
| Compressed File | Contains executables, specifically LockBit 3.0, which excludes PE files. |
| LockBit 3.0 | Manifests through an infection screen and a ransom note. |
| Vidar Infostealer | Connects to a Telegram channel named “twowheelfun” before initiating C2 communication. Downloads DLL files from the C2 server for malicious activities. |
| C2 Response Setting | Illustrates the complexity of Vidar’s communication network. |
AhnLab’s V3 anti-malware software identified these threats through aliases such as Trojan/Win.Generic.R613812, Ransom/MDP.Event.M4353, and Win-Trojan/MalPeP.mexp.
In addition, it is recommended that major corporations bolster their cybersecurity protocols in response to these evolving threats.
