Comodo Personal Firewall is an exceptional security tool that can help prevent malware from entering the user’s computer through the network.
Basically, anything that is connected to the internet will be monitored by the program, which will filter out the malicious traffic it has detected, making sure you are safe from browser exploits and cyberattacks.
When you are doing anything online, the program secures all connections and stops nearly all internet attacks.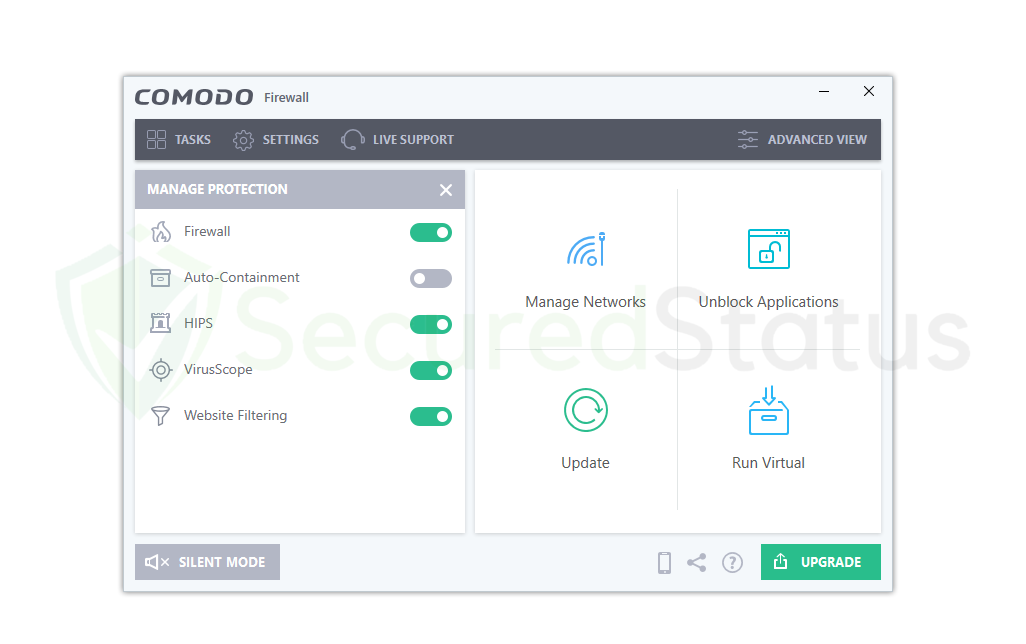 This covers inbound and outbound connections where malware stealers and keylogging data won’t be delivered, cybercriminals cannot access your computer with Remote Access Trojans, and you won’t even become infected in the first place.
This covers inbound and outbound connections where malware stealers and keylogging data won’t be delivered, cybercriminals cannot access your computer with Remote Access Trojans, and you won’t even become infected in the first place.
Why you should use Comodo Firewall?
In essence, it all comes down to network and computer security. The digital world as we currently understand it consists mostly of the online spaces we frequently visit and just half of the devices we use.
The majority of the applications we use depend on internet connectivity, and without it, we could be left with little choice except to play dinosaurs in the Chrome browser.
Now, we largely rely on an antivirus program to protect your computer, but what about the last component, our internet connection? Surely we still need to protect that as well. As malicious individuals can access our gadgets through the internet connection.
Although firewalls are essential, Comodo Firewall has more to offer than simply shielding the device’s network from potential malicious threats.
It has a user-friendly interface
The main application itself features a highly attractive graphical user interface that is user-friendly and simple to use.
Even if you are not tech savvy, you will be able to know how Comodo Firewall functions and even experiment with it because the menu and buttons are conveniently located for people to use.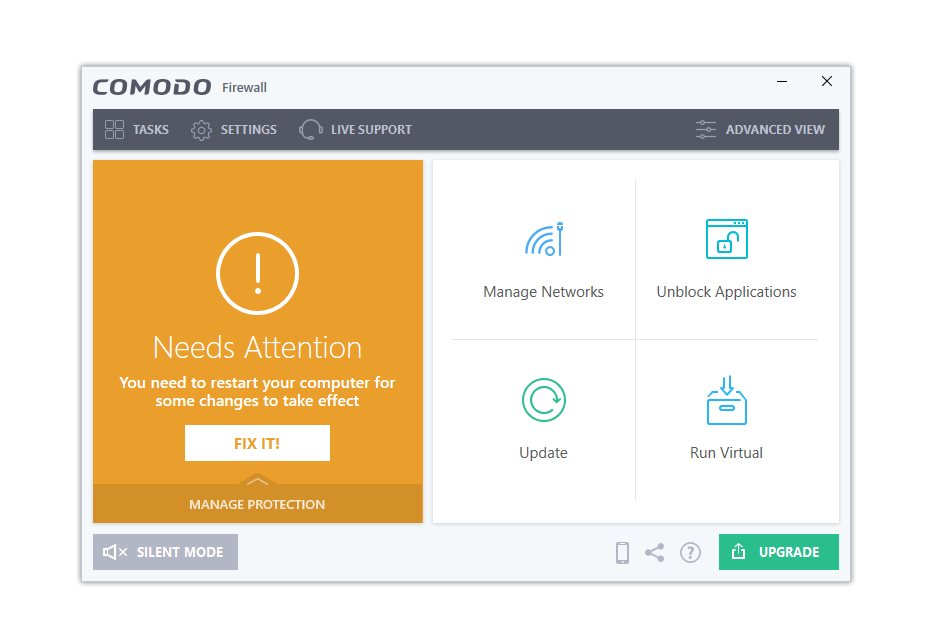 There are simply a few buttons and options, including the tasks, settings, and a live support section where, if you have any questions about the application, a member of their support staff will be able to assist you.
There are simply a few buttons and options, including the tasks, settings, and a live support section where, if you have any questions about the application, a member of their support staff will be able to assist you.
The button for turning on the firewall is the biggest, making it very obvious and straightforward to do so.
For people to understand that Comodo Firewall is turned on, it will show that your system is secure and that it is running and active against a green background.
There are buttons next to it for administering the network, which are more technical in nature. Users don’t even need to configure it because it is more geared toward tech-savvy individuals.
On the other side, users might want to click the update button because it’s important to make sure the Firewall is updated to the most recent version.
No complex configuration needed
Once Comodo Firewall is installed, you only need to enable the application. You don’t need to fiddle with the program to get it up and running because all the hard work has already been done.
Additionally, they assert that utilizing and installing their product won’t result in any complicated configuration problems.
It may highlight problems and suggest actions, but none of them are very difficult or require coding; instead, most difficulties may be resolved by selecting a few configuration options from the program.
They also demonstrate the actions you must take in order to resolve the issue. Not to mention, if you require more assistance from a real person on their tech support, you can use the live support option.
Learns user behavior to deliver better personalized security
In order to provide the highest level of personalized internet security, Comodo Firewall also learns and studies how the user uses all applications, the internet, and other resources.
Additionally, it is done this way to avoid disturbing the user, especially while work-related, and to ensure that it runs in the background without causing any interference with hardware or system operations.
This is actually a very useful feature because it learns how the user interacts with the device and uses the internet.
It also becomes familiar with the typical outbound and inbound connections within the network, making it easier to spot any suspicious or unusual traffic that is not frequently seen.
Many configuration options for tech-savvy users
Users don’t need to take any action because Comodo Firewall may be started with just a few clicks, as we’ve already explained.
However, the application actually offers users a large number of options to tinker with, should they choose to do so if they were techies and wanted to set the application in the manner they desired.
Some of these features include manually designating a trusted device or network and automatically blocking particular networks.
Additionally, there are other functions like endpoint cleaning, examining previously quarantined files, and reviewing the connections that the application has logged. The application’s advanced menu has all of this information and many additional choices.
Features of Comodo Firewall
The Comodo Firewall is not your typical firewall; it contains a number of useful features that could aid users in protecting their computer, including a virus scanner that can serve as a second opinion scanner and a sandbox where users can try out questionable programs without getting their computer infected.
General Features
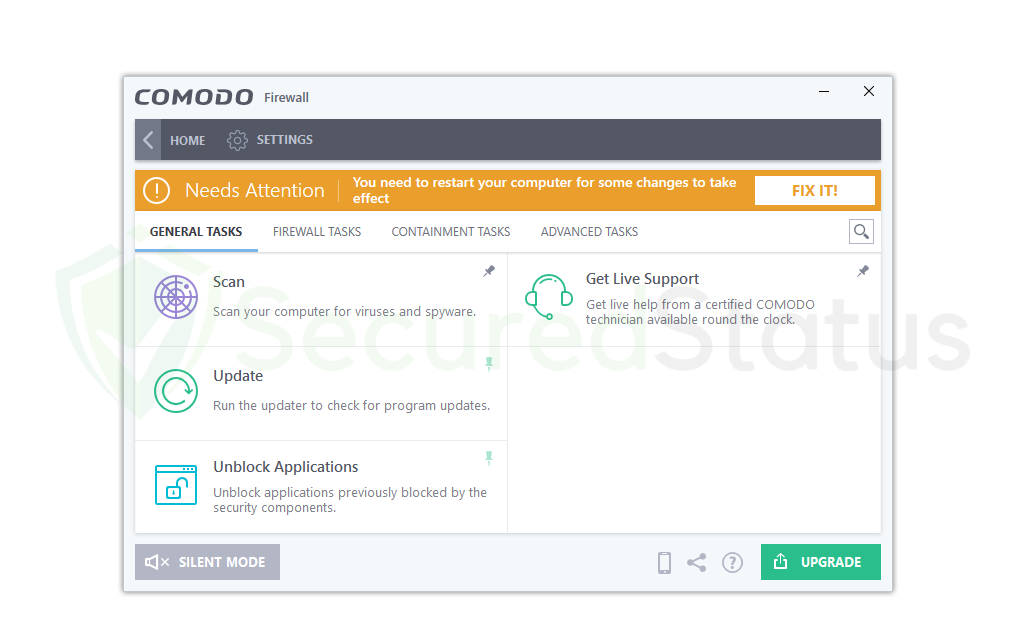
Scan & VirusScope:
It has a capability that is comparable to antivirus software in that it scans the computer for potential viruses and malware and removes them.
It is a useful function for people who might require a second scanner or who occasionally want to scan their PC. However, if you already have an antivirus program like Kaspersky, Malwarebytes, or another one set up on your computer. As the VirusScope feature could interfere with your antivirus program, you might want to disable it.
Get Live Support:
Comodo Firewall doesn’t require a lot of configuration, as we’ve already indicated; at most, a few configurations may be required, but everything only requires a few clicks to complete. If you are an experienced user, you might want to use the program’s advanced features.
You can get assistance from an authorized Comodo technician if you make a mistake or do not know how to resolve a specific problem. You can contact them at any time by just hitting the Get Live Support button on the application. They are accessible around the clock.
Firewall Features
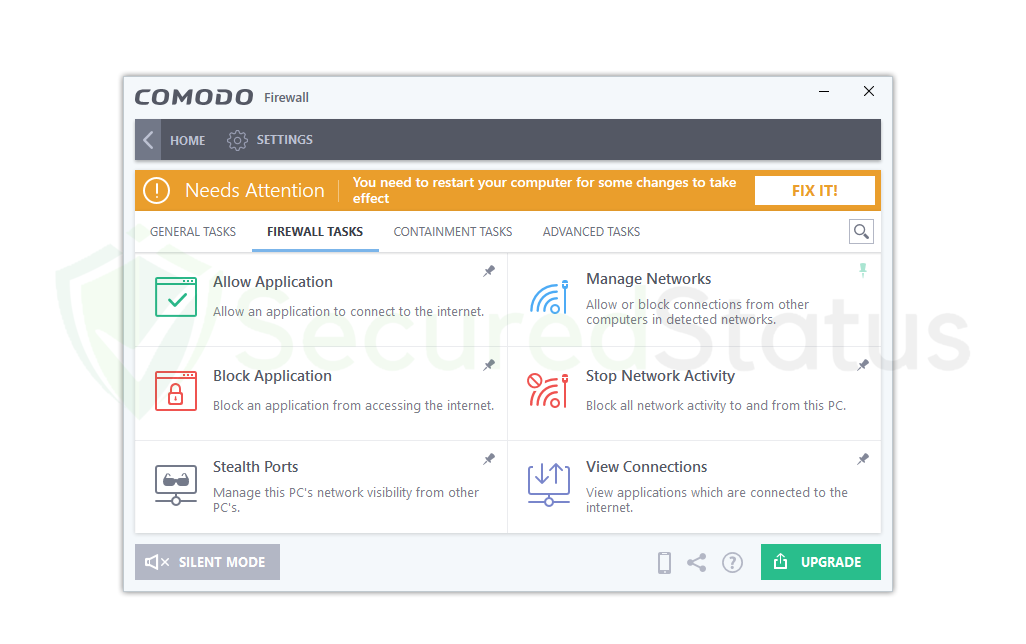
Stealth Ports:
Ports on a computer connected to the Internet are concealed from view as a security measure to prevent detection of the connection. This feature offers the customer the highest level of network security possible because malevolent hackers cannot see what is happening because it is hidden from their view.
They will assume that your computer is offline and not connected to the internet when that is not the case at all. In contrast to a closed port, this one is truly open but concealed from view by public networks and computers.
Manage Networks:
With the use of this useful feature, the computer will be able to observe, control, block, and trust particular networks and computers in its vicinity. Using this tool, you can ban a computer when you unintentionally connect to a malicious network, such as a hacker’s.
On the other hand, you can choose to trust a certain device by doing so in the Manage Networks option if, for instance, a particular connection with another device you are familiar with was inadvertently blocked due to the security features of this program.
Stop Network Activity:
All connections to the device and to any networks it was previously connected to will be completely terminated by this feature. Users may not require this function because it will appear as though access to and from the internet has been completely blocked.
However, when dealing with an unprecedented cyberattack, this will be useful. By blocking all connections, you can ensure that any unauthorized party attempting to access your computer or network remotely will have their connection shut off immediately.
Containment Features
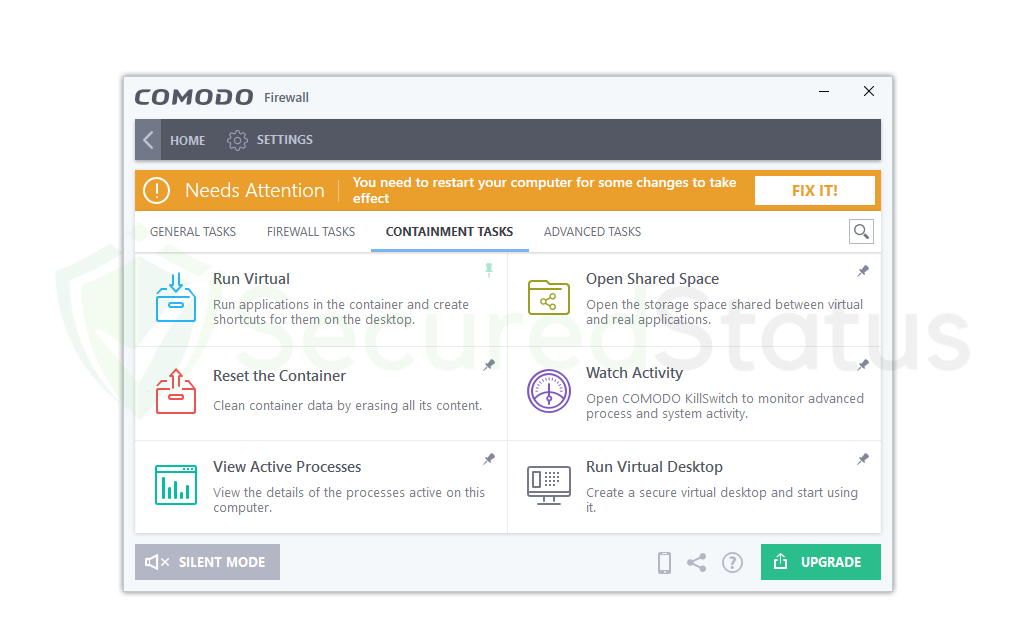
Run Virtual:
This feature is essential for running certain applications in a closed virtual environment. This is used to test virus files and malicious programs by running them on the computer and seeing what they do.
But the good thing is that it is not actually being run on the computer but on a separate testing sandbox, so any actions made by the harmful application will not affect the computer. Basically, this is something of an application testing feature; if you suspect an executable file, you can run it here first to know whether it is safe or not.
Watch Activity:
This function activates the Comodo KillSwitch tool, which is designed to keep an eye on sophisticated computer system operations and processes. Basically, it keeps track of all the activities on the system, including crucial Windows processes, other critical system components, and significant apps.
This will prove to be a useful tool to monitor and discover the malware within system processes and activities if you suspect that your system is infected with malware that is obfuscating normal processes and hiding on the system.
Run Virtual Desktop:
This program is comparable to the Run Virtual feature stated above in that it also creates a sandbox for a specific application that the user wants to test for untoward behavior.
However, this functionality operates a full virtual desktop, which is a different system from the Windows machine users are now using. You can see a different Windows home screen there, where you can perform whatever actions you choose, use the internet, and even test viruses because it won’t harm the main system.
Advanced Features
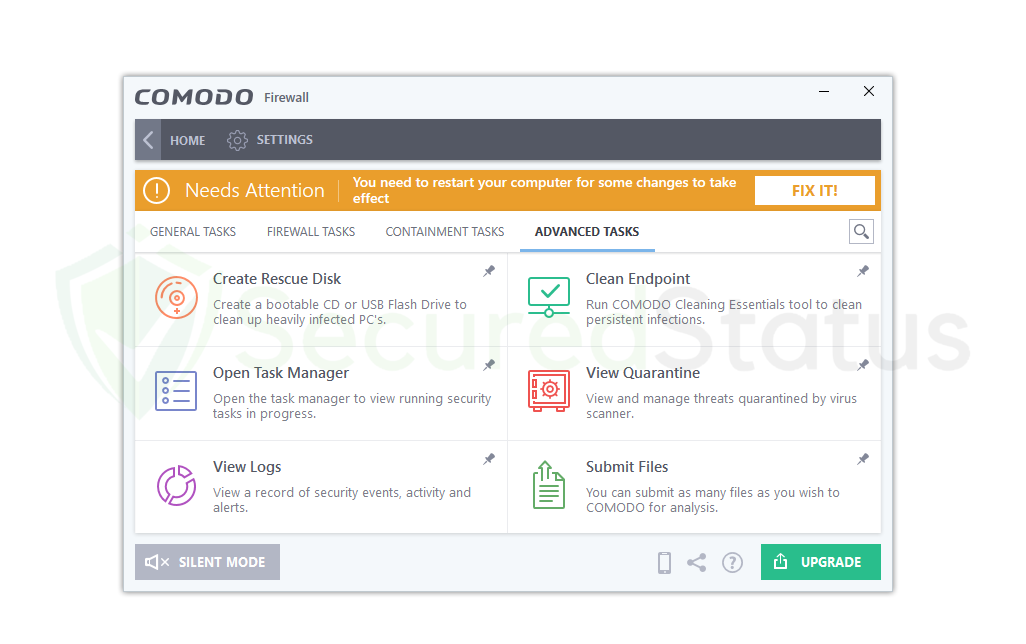
Create Rescue Disk:
When a computer is seriously infested with malware, the Create Rescue Disk capability is used to make a bootable CD or USB Flash Drive on the machine. Users that have a lot of malware on their systems that even antivirus software is unable to discover with complete system scans will find this function beneficial.
With the aid of this function, a bootable utility that scans for malware even during bootup can be created. In addition, it can get rid of malware that initially stops the computer from booting.
Clean Endpoint:
Cleaning persistent malware infections that are resistant to removal by a conventional scan is made easier with the help of the Clean Endpoint function. Similar to Create Rescue Disk, which develops a separate utility inside a detachable, it can assist in the removal of malware from boot processes, although this one focuses on the deeper portions of the system.
If you are infected, you should try both for optimal security. It aids in the removal of dangerous processes from an infected computer. Not to mention that it is portable because it is a component of the Comodo Firewall.
Submit Files:
The Comodo Firewall’s Submit Files function is a special tool that checks a given file for malware signatures to see if it is infested with harmful viruses.
You can use the Submit Files feature to check whether a certain file on the computer is contaminated with malware if you are unsure whether to open it right away. This is particularly useful since it stops users from unknowingly running viruses from unidentified files. Not to mention, you are free to upload and submit as many files as you want.
How to Setup and Use Comodo Firewall
The installation process for the Comodo Firewall is simple, and we’ll walk you through each step of downloading, setting up, and activating it on your computer.
Given the number of functions it contains, it is surprising that the program we have highlighted is available in a free edition. You can also opt for Comodo’s paid version, which contains many more features.
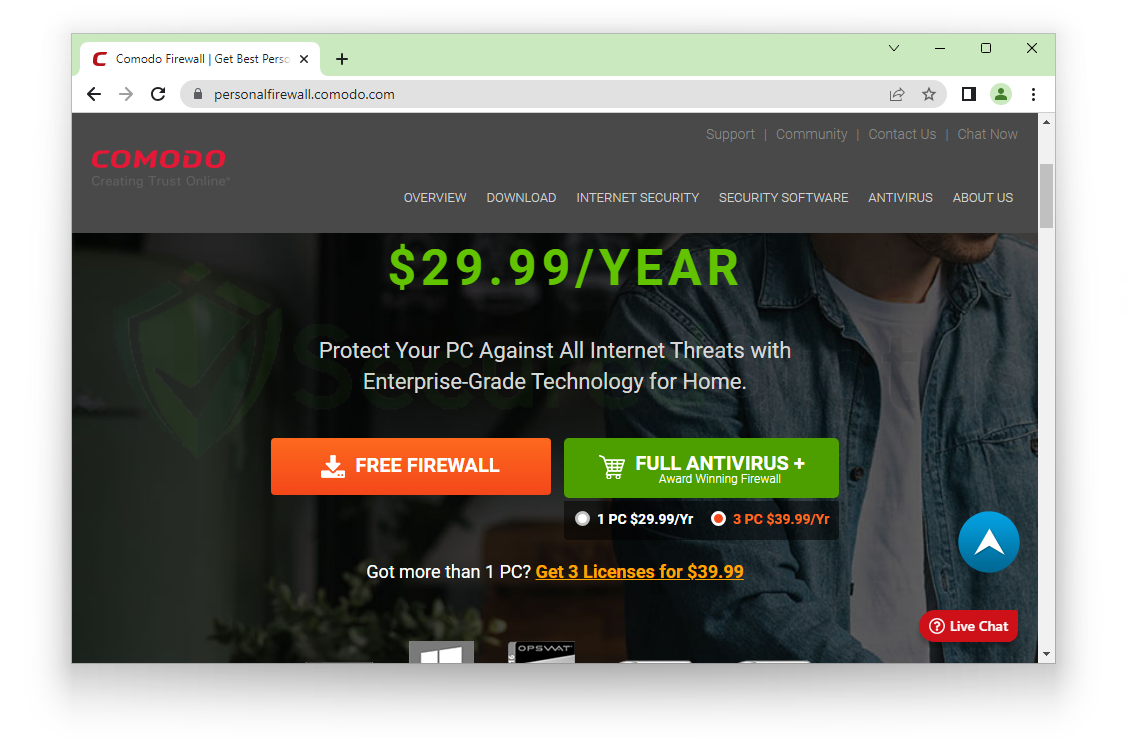
1. Click here to access the official Comodo Firewall download page using your preferred web browser. You can choose between a free firewall and a full antivirus for $29.99 annually. The application we’ve shown is the free firewall, which is all most people would need, so use that unless you’d want a full antivirus if you don’t already have one.
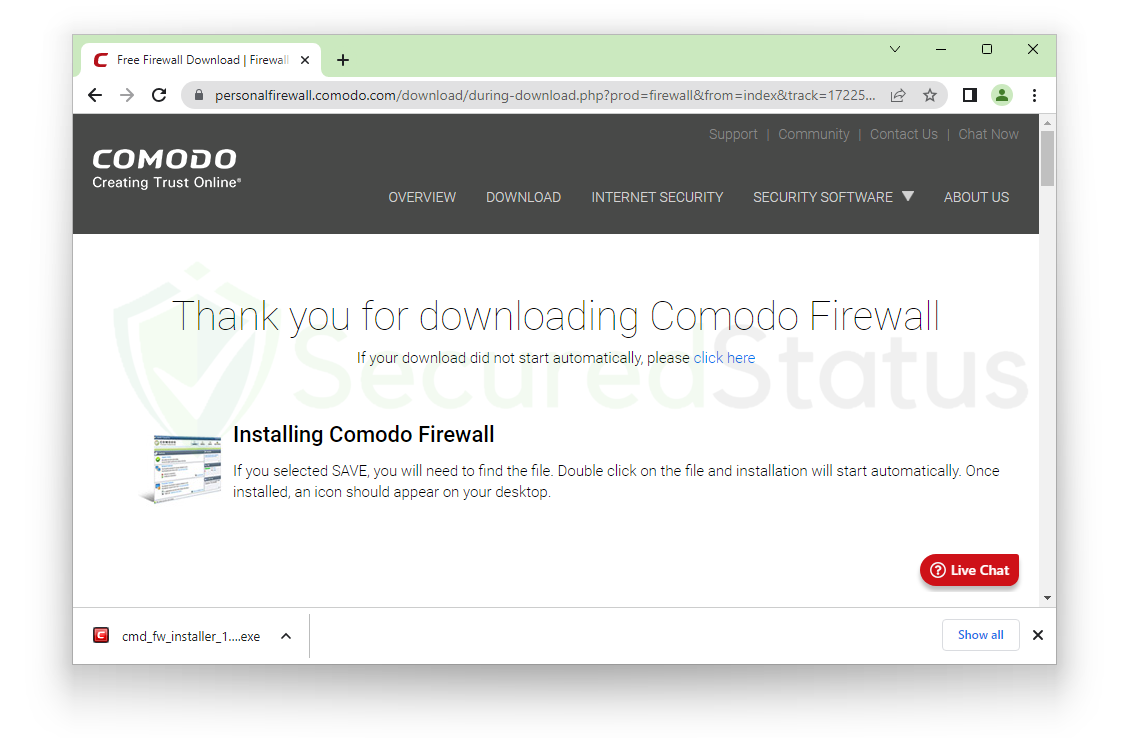
 2. You will get a Thank You for Downloading page after hitting the download button. It would then begin downloading the Comodo firewall installation file. Start the installation file after the download is complete.
2. You will get a Thank You for Downloading page after hitting the download button. It would then begin downloading the Comodo firewall installation file. Start the installation file after the download is complete.
 3. You will be prompted to a User Account Control window after clicking the Comodo Firewall installation file, where you must grant Comodo Security Solutions (Publisher Name) permission to make modifications. As it needs permission in order to properly install the application on the computer, select Yes and grant it.
3. You will be prompted to a User Account Control window after clicking the Comodo Firewall installation file, where you must grant Comodo Security Solutions (Publisher Name) permission to make modifications. As it needs permission in order to properly install the application on the computer, select Yes and grant it.
4. When the Comodo Firewall setup window appears, carefully read the instructions because they mention installing Dragon Browser, a browser that certain users may not require. Although it is not required, you can remove it after the installation is finished. On the other hand, you can choose from the Options not include it, as indicated. Click Accept and Install to continue. 5. Please be patient while the system installs the Comodo Firewall. Given how small the application is, the installation shouldn’t take more than a few minutes, which can vary depending on your computer’s hardware and speed.
5. Please be patient while the system installs the Comodo Firewall. Given how small the application is, the installation shouldn’t take more than a few minutes, which can vary depending on your computer’s hardware and speed. 6. When the Comodo Firewall has finished downloading, the user is greeted with a Congratulations page and an email box in case they want to receive Comodo news and discounts. The checkboxes below are crucial, and we advise selecting only the first three of them. However, the fourth box—which requests that the browser be routed to Yahoo—should be left unchecked because it is not required. Additionally, we do not advise setting Comodo Dragon as your default browser because Chrome and Firefox are both far superior options. After unchecking the boxes, click on Finish to open the firewall application.
6. When the Comodo Firewall has finished downloading, the user is greeted with a Congratulations page and an email box in case they want to receive Comodo news and discounts. The checkboxes below are crucial, and we advise selecting only the first three of them. However, the fourth box—which requests that the browser be routed to Yahoo—should be left unchecked because it is not required. Additionally, we do not advise setting Comodo Dragon as your default browser because Chrome and Firefox are both far superior options. After unchecking the boxes, click on Finish to open the firewall application.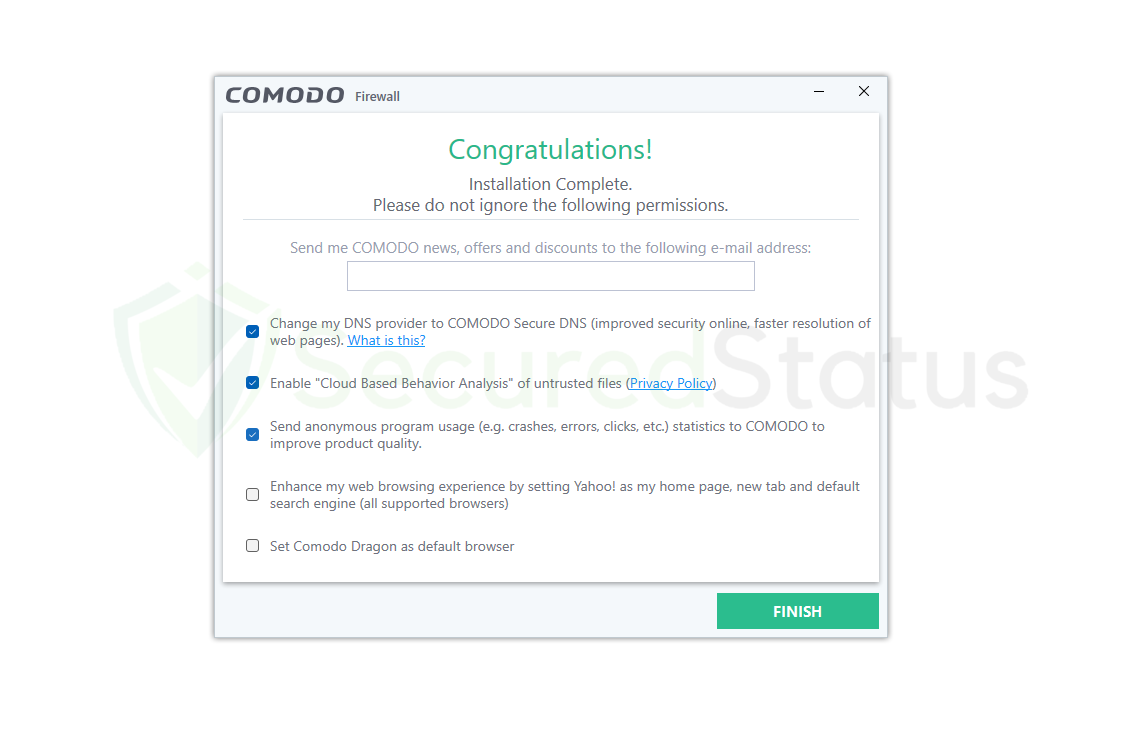 7. You will be able to use all the functions stated above after the Comodo Firewall program has been launched. Since nearly all features are available on the home screen, the interface is helpful for beginners. Users must restart their computers in order for the changes to take effect and to activate the firewall. You can either restart your computer using the standard methods or click the Fix It button on the big window.
7. You will be able to use all the functions stated above after the Comodo Firewall program has been launched. Since nearly all features are available on the home screen, the interface is helpful for beginners. Users must restart their computers in order for the changes to take effect and to activate the firewall. You can either restart your computer using the standard methods or click the Fix It button on the big window.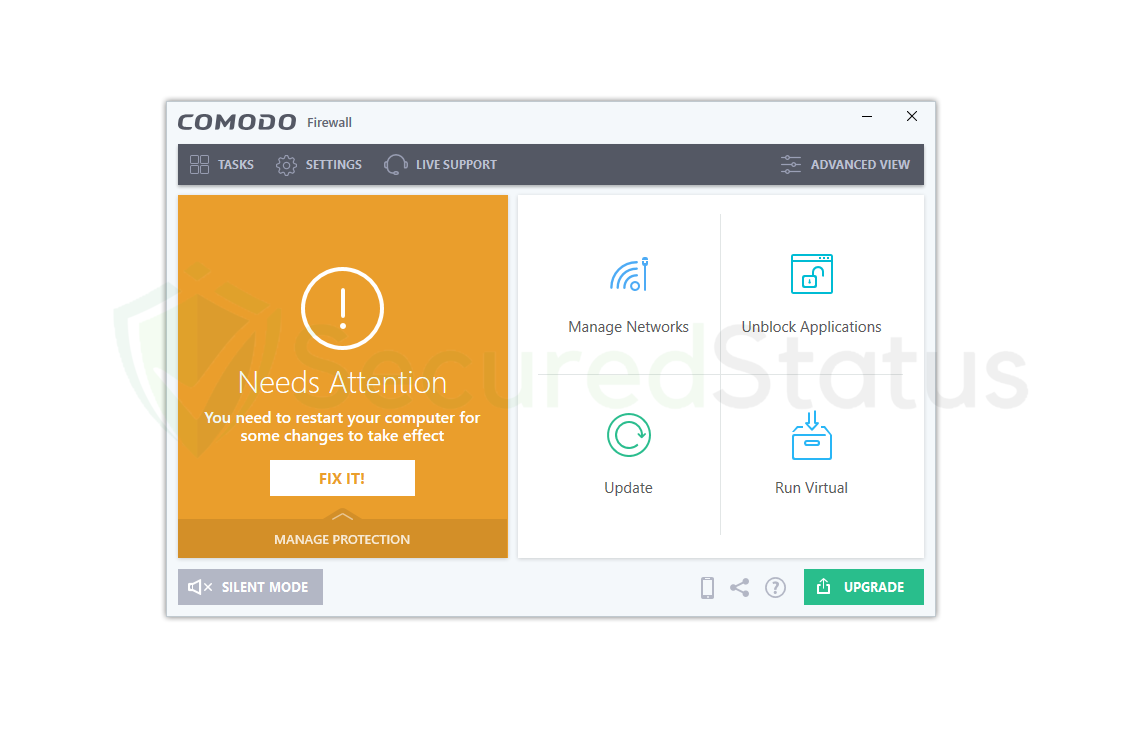 Open the Comodo Firewall after a restart, and it should be fully operational and all green. You don’t need to worry because your network and PC are now secure against online threats and network exploits. Considering that Comodo Firewall is a well-known and effective firewall.
Open the Comodo Firewall after a restart, and it should be fully operational and all green. You don’t need to worry because your network and PC are now secure against online threats and network exploits. Considering that Comodo Firewall is a well-known and effective firewall.
Frequently Asked Questions (FAQs)
Here are some of the most frequently asked questions about the Comodo Firewall that we will answer since we have tested the application.
Is Comodo Firewall completely free?
Every user who wants to utilize the application is free to do so using the version that we have downloaded. Although there is a premium version, it won’t change the functionality of the free version because it is sufficient to guarantee consumers’ security.
Not to mention, this program does not request your credit card information. Additionally, you are not required to create an account or provide your email address. Despite this, there is still a premium version that performs significantly better, but users who liked the free version can decide whether to upgrade.
Does Comodo Firewall work on Windows 11?
Since we have installed Comodo Firewall on a PC running Windows 11, it genuinely functions with the most recent patch. They may be referring to a completely different program or version that can only be seen in forum download links, but they have claimed that it is incompatible even though it still functions.
Not to mention, you can see an incompatibility error when installing the Comodo firewall; nevertheless, after a few delays, the installation wizard will still appear and the installation will proceed normally.
Is Comodo Malware Scanner good?
It is a reliable scanner that can completely get rid of viruses and spyware from the computer. It can identify the most recent frequent browser threats, but since Comodo Firewall is only a firewall and not a full-fledged virus protection system, you are better off using programs like Malwarebytes and Kaspersky.
But if your antivirus program misses a particular threat, you can use it as a sort of backup scanner. It is actually quite unique that Comodo Firewall includes a sandbox and testing environment feature when most antivirus programs do not include this feature.
Can hackers eventually get past the Comodo Firewall?
Hackers can bypass network firewalls like common ones like Windows Defender by injecting malicious code into the firewall through SQL injections, but the odds are small when it comes to Comodo Firewall due to its reliable firewall solution.
Not to mention that it has a kill switch that can halt and stop all incoming and outgoing connections; it will also stop any malicious activity that might be going on at the network computer. The likelihood is low, and using the right Comodo Firewall setup and tools will make your PC impenetrable.
Is there a good alternative to Comodo Firewall?
If Comodo Firewall does not appeal to you for a variety of personal reasons, you may want a different firewall application. Then there is another program that we advise individuals to use.
The only firewall that can compete with Comodo Firewall’s powerful firewall security is ZoneAlarm Firewall, of course, as a competent firewall will almost certainly have rivals. It is also quite simple to use and has a modern user interface.
In the event that you don’t like Comodo, you can try going with ZoneAlarm since they have been producing security items for more than a decade.
