While Telegram is widely regarded as a safe messaging network, it is not immune to the threat of malware, and to answer your question, yes, malware may be obtained over Telegram.
Malicious actors can exploit vulnerabilities or trick naive users into downloading infected files. Although Telegram implements strong security precautions, the platform’s open nature allows for possible dangers.
What you need to know about Telegram
Telegram is a versatile messaging program that offers users a variety of communication opportunities. Telegram has been a popular choice for individuals seeking a secure and feature-rich messaging experience, offering everything from private and group chats to file sharing and voice calls.
Its end-to-end encryption preserves the anonymity of communications, but users must be cautious about the information they interact with to avoid potential malware exposure.
The risk stems from Telegram’s file-sharing capabilities, which, while convenient, can represent a risk. Users can exchange a variety of content kinds, including images, movies, and documents.
Unfortunately, cybercriminals can exploit this openness by hiding malware within seemingly harmless files.
To protect your system from potential malware threats on Telegram, take a proactive approach. If you suspect your device has been compromised, you can follow the virus removal instructions in the section below.
Steps to Remove Malware Downloaded From Telegram
We made the instructions below easy to understand so non-tech-savvy users can still remove the threat without needing help from tech support or a computer technician.
Please inform us using our Contact Page if you come across a method that does not appear to be working. We value the feedback you provide and will address the issue as soon as possible.
Step 1: Scan with powerful malware removal software
Highly damaging malware could have been downloaded from Telegram. They can conceal themselves within the system files and registry, making them resistant to browser reset and software uninstallation.
An antivirus application is a one-stop shop for dealing with malware and potentially unsafe websites. It acts as both a preventative and corrective measure, immediately detecting and removing malware from your device.
We cannot overstate the importance of utilizing antivirus software when facing unknown threats.
Furthermore, any malware that may have been installed on your computer unwittingly will be intercepted, and any downloads will be stopped as soon as they begin.
Having antivirus software on your computer offers several significant benefits, including:
- Detection, filtering, and automatic removal of malware ranging from harmless adware to extremely severe ransomware.
- Providing caution and notifications for possibly risky websites that you may visit, helps you in mitigating online risks.
- Antivirus threat databases are regularly updated to ensure the detection of new viruses and the protection of your device.
- Keeping your operating system clean by protecting all files on your computer, assuring their safety and integrity.
But which antivirus should I use?
The answer is based on how you use your computer, as several antivirus software on the market have advantages and disadvantages. Because the majority of them detect and remove malware at the same rate, we recommend making your selection based on research.
For example, if you use your computer for resource-intensive tasks like video editing, you may wish to avoid resource-hogging antivirus software.
Fortunately, various reviews provide detailed comparisons of each antivirus’s advantages and disadvantages. However, for the best of all worlds, we recommend one of the antivirus applications listed below:
The majority of free versions are already sufficient for removing and blocking viruses from your computer. Some antivirus products also provide free trials that allow you to learn more about its capabilities before making a purchase choice. However, in the end, the free version usually provides everything needed to remove malware.
For a better and safer web browsing experience, we’ve provided a few security measures and advice below that will safeguard your browser and computer from harmful threats like worms, malware, trojans, keyloggers, stealers, and other kinds of computer viruses that will harm user data.
Step 2: Uninstall unwanted programs from the computer
Adware, often known as advertisement-supported software, can also be downloaded via the platform, which is why it is important to check the system for applications you do not recognize.
How will I know what to uninstall?
Giving the exact name of the malicious program may be complicated, but there are ways to make it easier to detect it. One of which is to simply remove all unknown programs you do not recognize or think you have not installed. You may have applications that you don’t even know the use for; that is a sign that they can be malware.
Unless it is a system process, which you can see by checking the developer of the application, some trojan viruses also use recognized and legitimate names to obfuscate their programs. If the publisher name or source of the program is unknown to you, it is best to uninstall it.
The most common way to remove malware from your computer is to uninstall the program through the Control Panel. You may view all of your installed apps as well as the developer’s name in the list of applications.
1. From the Windows search bar at the bottom of your screen, search for Control Panel and click the result that matches the same application.

2. You will see different options, such as System and Security, as well as User Accounts. But what you want to click is the Uninstall a program under the Programs section. Depending on your Windows version, hovering over the uninstall section will be relatively the same.
 3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed.
3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed. 4. Right-click the suspected virus program and click Uninstall to get rid of it (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed.
4. Right-click the suspected virus program and click Uninstall to get rid of it (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed.
After doing so, the unwanted program will now have been uninstalled from the computer. There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
Step 3: Reset the browser to its default settings
Resetting the browser includes complete reversal and wiping out history, homepage settings, default search engines, and browser permissions, malware from Telegram typically targets the browser to steal cached data and other personal information.

Google Chrome
1. Open the Google Chrome browser and click the three dots in the upper-right corner of your screen to access the drop-down menu.
2. From the menu presented, select the Settings button, then click the Advanced menu on the left side of the screen from the settings.
3. On the drop-down menu presented on the screen, select Reset and Clean up.
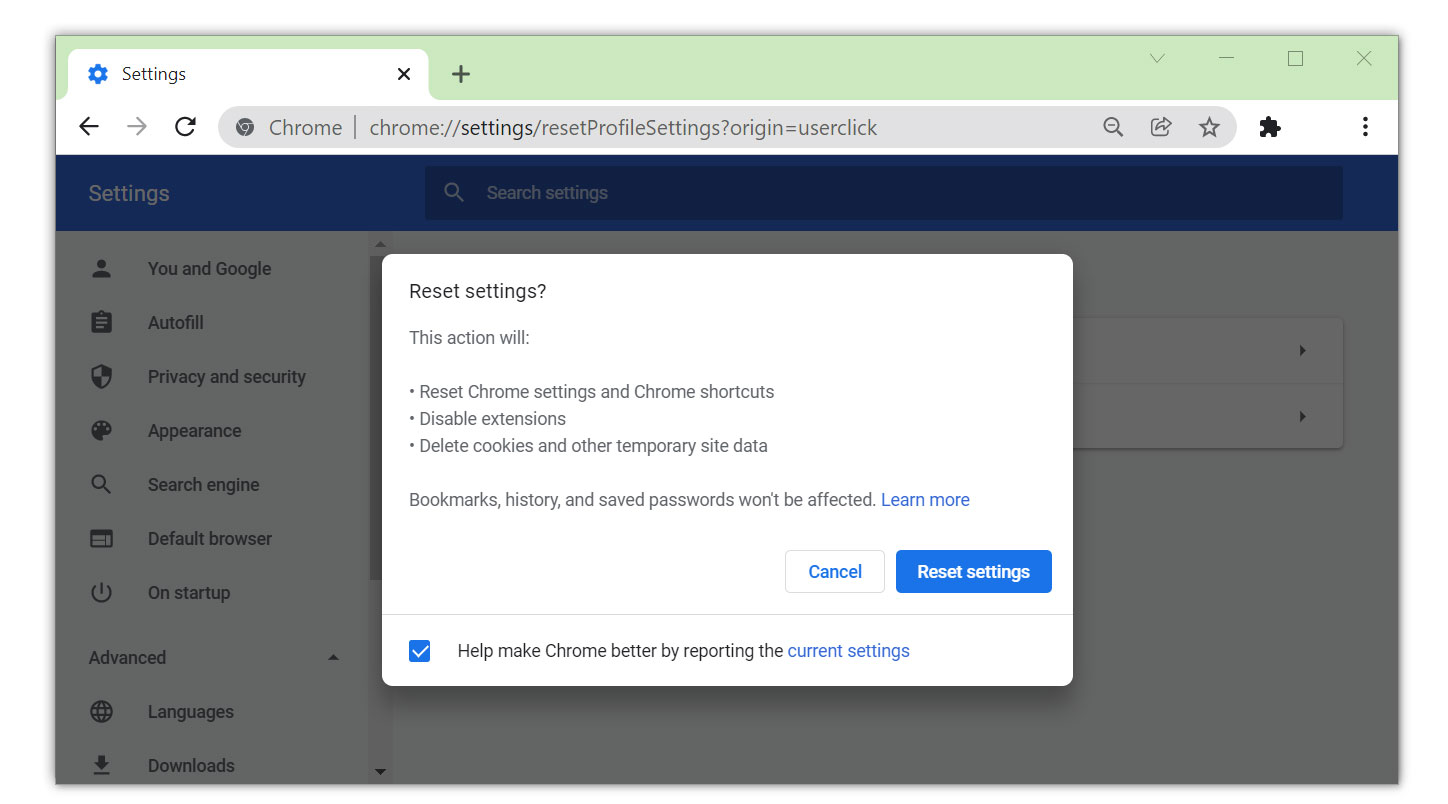
4. Click on the Restore settings to their original defaults.
5. Then a small confirmation window will appear; click the Reset Settings.

Mozilla Firefox
1. Launch the Mozilla Firefox browser, then open the menu by clicking on the three horizontal lines located in the upper-right corner.
2. Navigate down and click Help, then select More Troubleshooting Information from the options given.
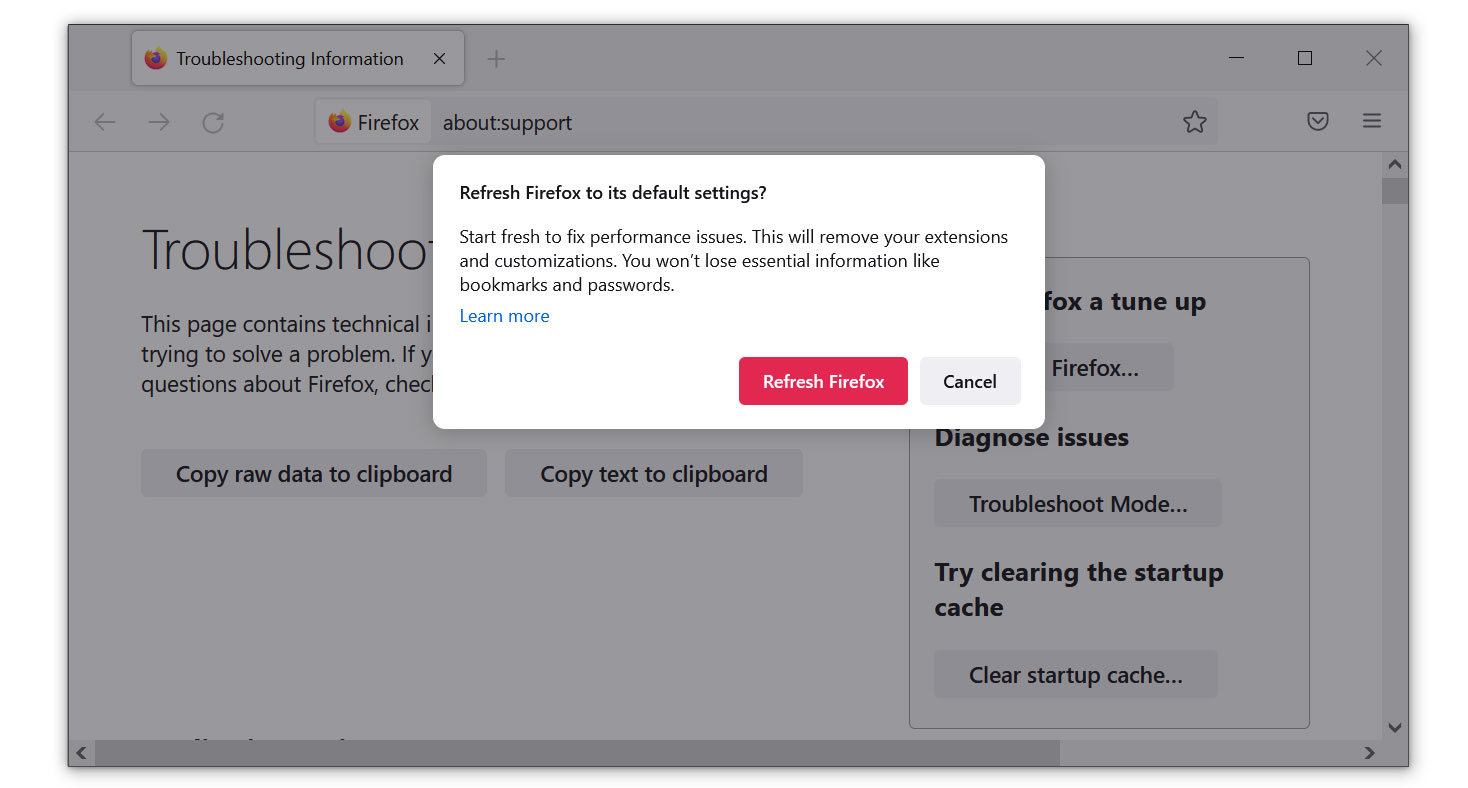
3. Select the Refresh Firefox button. Then click Refresh Firefox on the confirmation window that appears.

Microsoft Edge
1. Run Microsoft Edge on the computer and click the three-dot icon in the upper-right corner.
2. Click on the Settings button from the drop-down menu.
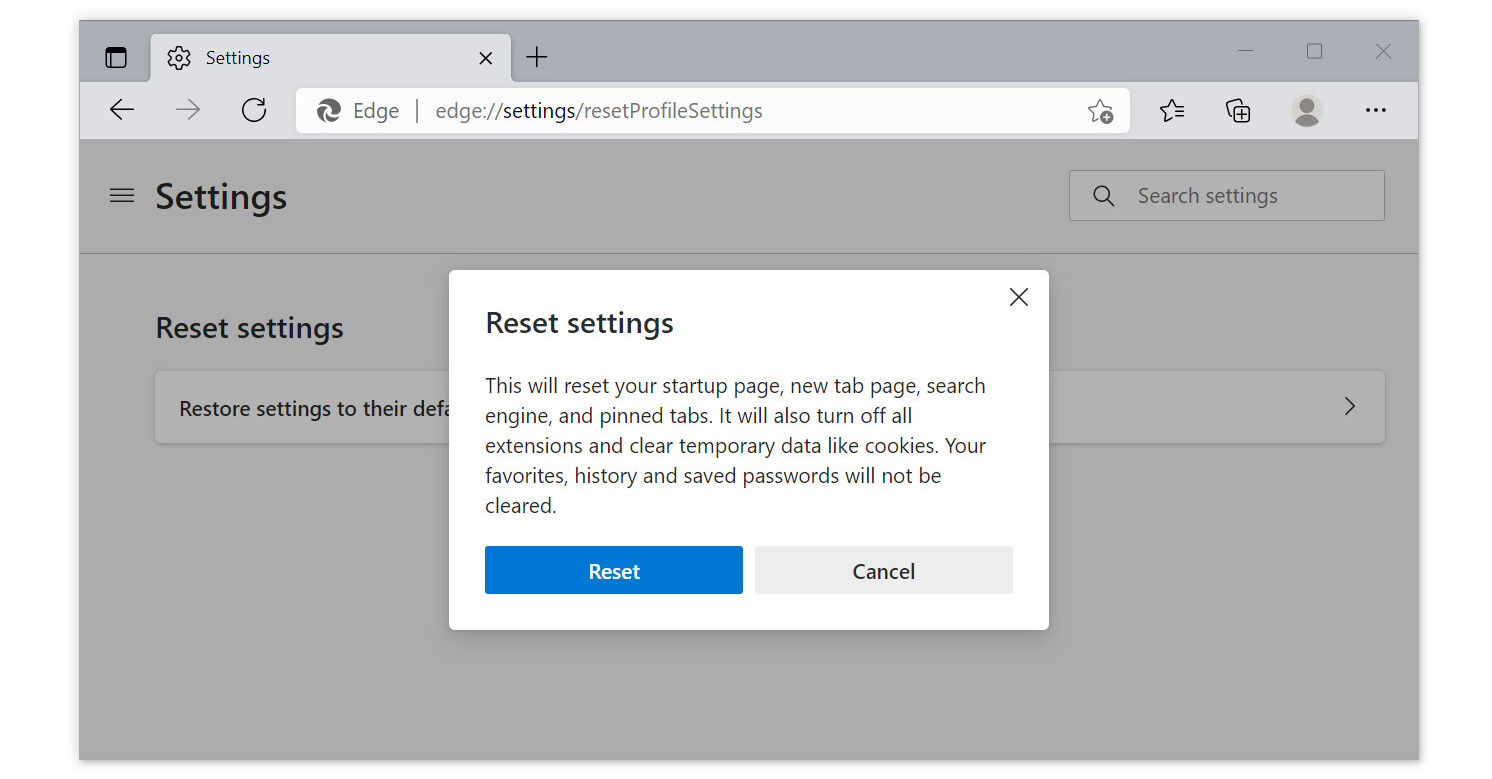
3. Find and click Reset Settings from the left sidebar. Then click on the option Restore settings to their default values.
4. A warning window will appear, telling you that you are about to reset the browser. Click Reset, and the browser should return to its default settings.
The configurations added by the malware to steal data have all been removed, and your browser has now been entirely reset to the settings it had when you initially installed it. You can use your browser with complete security now.
For a better and safer web browsing experience, we’ve provided a few security measures and advice below that will safeguard your browser and computer from harmful threats like worms, malware, trojans, keyloggers, stealers, and other kinds of computer viruses that will harm user data.
Protective measures for better overall security
Removing trojan viruses and malware from the device is one thing; keeping it secure for the future and for a long period is a different thing and will require certain things to make sure you are secured, especially if you do not know most of the ins and outs of the device you are using.
Cybercriminals are always stepping up their game to make sure they infect users and extract data and money from them.
We encourage you to take the actions listed below to ensure complete security before leaving this page because we strongly promote web security and having a secure online presence.
Safeguard your data and privacy online by using a VPN application
VPNs, also known as virtual private networks, guarantee your safety and complete anonymity while you browse the internet.
In contrast to a firewall, which monitors and blocks potentially harmful connections in the network, A VPN hides the user’s connection via a tunnel so that it would appear to third parties as a different IP address and location.
This ensures that your data won’t be leaked because the program hides it. Be aware that visiting infected websites may cause your IP address and location to be disclosed; however, if you use a VPN, this will prevent your true IP address from being revealed to malware actors.
Utilize an adblocker when browsing the internet
Installing an adblocker on the browser is the best way to prevent hijacker viruses such as $$custom_field:vname$$ as well as other threats such as pop-ups, redirects, and unwanted toolbars.
Additionally, by blocking malicious websites before users can even access them, it is possible to prevent malware from being downloaded.
In this case, we recommend uBlock Origin, which is an open-source AdBlock extension that comes at no cost and is free forever. It is one of the most reliable plugins out there, ensuring that every advertisement on a webpage will be blocked.
Use a firewall to prevent cyber attacks
A security firewall is required for every internet connection that is made. It is an essential tool that enhances security and stops online attacks.
Through a security mechanism, it controls incoming and outgoing network connections on your system and network and filters the undesirable ones. Consider it a further barrier against malicious assaults and zero-day exploits.
