“Brace yourself for something truly astonishing” is an ongoing email fraud campaign that scares recipients who receive the mail. Its contents advise you to pay a sizable sum of money to a cryptocurrency wallet in exchange for the security of having your files kept from the public.
An email is merely a form of blackmail or a ransom note that asks recipients to pay money in return for their safety and privacy.
This email scam is particularly similar to the “Greetings! I have to share bad news with you” and maybe a newer version with the same scammers operating behind it.
However, since there is no concrete proof that the senders of these emails possess recipients’ private photos and data, it is most likely a hoax and users should not believe whatever these scammers say.
Here is the text transcript of the aforementioned scam email that has been circulating the web:
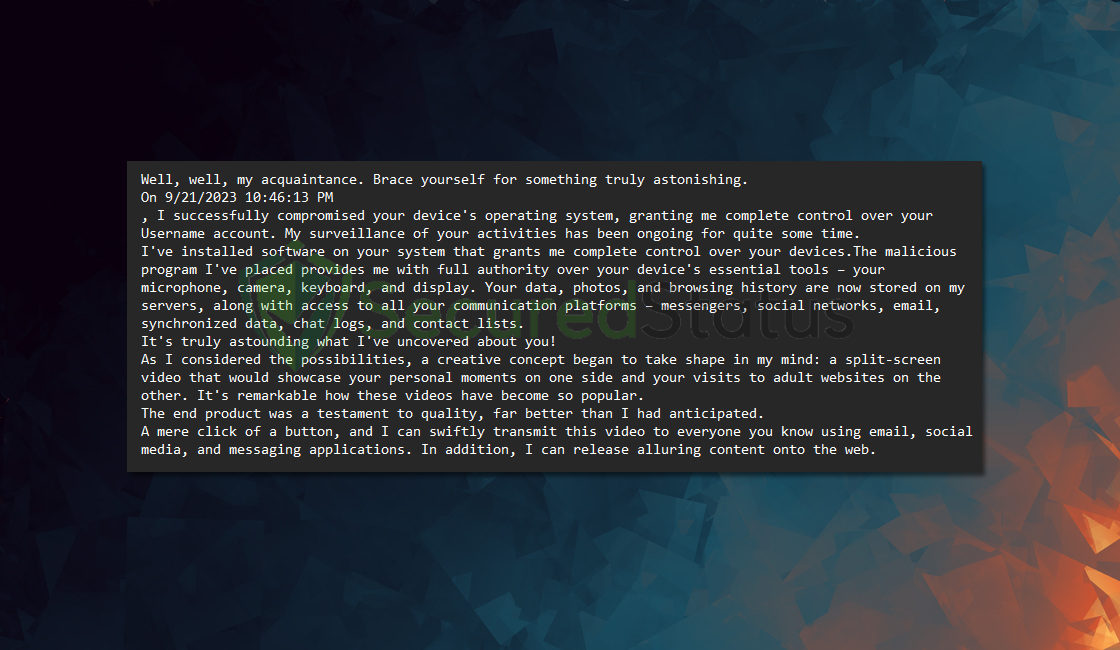
Well, well, my acquaintance. Brace yourself for something truly astonishing.
On 9/21/2023 10:46:13 PM
, I successfully compromised your device’s operating system, granting me complete control over your Username account. My surveillance of your activities has been ongoing for quite some time.
I’ve installed software on your system that grants me complete control over your devices.The malicious program I’ve placed provides me with full authority over your device’s essential tools – your microphone, camera, keyboard, and display. Your data, photos, and browsing history are now stored on my servers, along with access to all your communication platforms – messengers, social networks, email, synchronized data, chat logs, and contact lists.
It’s truly astounding what I’ve uncovered about you!
As I considered the possibilities, a creative concept began to take shape in my mind: a split-screen video that would showcase your personal moments on one side and your visits to adult websites on the other. It’s remarkable how these videos have become so popular.
The end product was a testament to quality, far better than I had anticipated.
A mere click of a button, and I can swiftly transmit this video to everyone you know using email, social media, and messaging applications. In addition, I can release alluring content onto the web.If you want to avoid the fallout, the remedy is elementary: forward $1250 (US dollars) to my Bitcoin wallet.
Please provide the funds to this Bitcoin wallet address:
bc1qfsv5nw9dtjfph0sqstzj3l95clnhpe02c037kyI am allowing you exactly two days (48 hours) from the time you read this message to complete the payment.
Once this timeframe is up, and I haven’t received the specified amount, I will initiate the distribution of access to your accounts, visited websites, personal data, and edited videos to everyone without prior warningIf you’re unsure about the steps to fund a Bitcoin wallet, you’ll find plenty of guidance by searching on Google. It’s an uncomplicated procedure.
After the payment has been received, I will swiftly expunge any compromising materials and guarantee that no generated or obtained content is shared. Following this, we can part on civil terms. I am deeply committed to deactivating and erasing all harmful software from your devices. You can trust in my word; I consistently adhere to my commitments. It’s a fair proposition, particularly considering the time and effort I’ve invested in tracking your online activities and digital footprint.
Be aware, I am highly diligent. I strongly recommend you take this situation seriously, given my vast resources. Your response is not obligatory; I’ve used a secure email for this message and won’t be following responses
Trying to expose my identity is a wild goose chase; I’ve obscured it masterfully. Your actions to erase your device or reformat the drive won’t change the fact that I already hold your data.
I wish you the best of luck, so stay composed.
Numerous variations of frightening emails are used in this type of fraud, which has been going around for years, to fool users into complying with the demands of the fraudsters.
Additionally, these scammers frequently attempt to assume the identity of a bank, governmental agency, or other company to support their allegations. In some rare instances, the words might even contain your name to make you believe they are real.
What to do after receiving the “Brace yourself for something truly astonishing” email?
The first thing you need do is to calm yourself because, even though it may appear genuine, it is merely fake and intended to deceive you.
Reporting the sender’s email will allow the address to eventually be blocked and the offender to be identified through an investigation by your country’s cybercrime enforcement agency.
For United States Citizens: You may email spam@uspis.gov or mail the Federal Trade Commission (FTC) at their official website.
For United Kingdom Citizens: You may visit Actionfraud.police.uk and file a report or call their number via 0300 123 2040.
For France Citizens: You may file your report via the Service-Public.fr website.
For Australian Citizens: You can use ReportCyber to file a report or call the Australian Cyber Security Hotline at 1300 292 371.
For Canadian Citizens: Contact the Canadian Anti-Fraud Centre or call their number 1-888-495-8501.
After that, you should block the email address of the sender to ensure that you don’t continue to receive further emails from them.
You should do a malware scan just in case to make sure your device isn’t genuinely infected and that no hackers have accessed your accounts or your data.
For these virus threats, we recommend running a full system malware scan with Malwarebytes Anti-Malware. This program is widely known and recognized by security experts when it comes to removing viruses from the system.
Remove Potential Malware with Malwarebytes Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked many known computer threats as shown from our tests with the software, and we assure you that it can remove viruses as well as other malware hiding on your computer.
 Not to mention, it is free to use and does not come at any cost to remove the viruses it finds on your computer.
Not to mention, it is free to use and does not come at any cost to remove the viruses it finds on your computer.
To use Malwarebytes and remove malicious threats from the computer, follow the steps below:
1. Download Malwarebytes by clicking the button below, as we have made an additional and in-depth tutorial on how to use it. Otherwise, you may go to their official website via Malwarebytes.com (Avoid misspelling as it may lead to scams).
Download Malwarebytes Anti-Malware
2. Visit their download section and start a Free Download to begin installing the software on your computer. 3. Once the Malwarebytes setup file (MBsetup.exe) has finished downloading, open the executable file in File Explorer, then right-click the setup and select run as administrator to give the highest system authority and make sure Malwarebytes is installed correctly.
3. Once the Malwarebytes setup file (MBsetup.exe) has finished downloading, open the executable file in File Explorer, then right-click the setup and select run as administrator to give the highest system authority and make sure Malwarebytes is installed correctly. 4. Make sure to carefully follow the installation setup wizard’s instructions and provide the relevant information it requires. You will be prompted with questions such as Personal or Business Use, Email Address, and others.
4. Make sure to carefully follow the installation setup wizard’s instructions and provide the relevant information it requires. You will be prompted with questions such as Personal or Business Use, Email Address, and others. 5. From the application’s home screen, go to the scan tab and begin running a system scan. This will scan the whole computer, including memory, startup items, the registry, and the file system. This is done so that not only the hidden trojan but also other malware hiding in the system will be detected.
5. From the application’s home screen, go to the scan tab and begin running a system scan. This will scan the whole computer, including memory, startup items, the registry, and the file system. This is done so that not only the hidden trojan but also other malware hiding in the system will be detected. 6. Since it can take a while, you should either relax and wait for it to finish or find something else to do. The length of the scan depends on the size of the files you have and the hardware capabilities of your computer. Here are some ways to make scanning faster.
6. Since it can take a while, you should either relax and wait for it to finish or find something else to do. The length of the scan depends on the size of the files you have and the hardware capabilities of your computer. Here are some ways to make scanning faster.
7. Once the scan is finished, Malwarebytes will show the malicious viruses and threats it found on your PC. Every malware will show up on the detection results, and it will show up in a threat name such as TrojanCrypt.Generic, and many more. 8. Select all the detected files from the report and click the quarantine button to remove the malicious items from the computer into the protected safe quarantine zone of the anti-malware program so that they would not affect and do malicious actions to the PC again.
8. Select all the detected files from the report and click the quarantine button to remove the malicious items from the computer into the protected safe quarantine zone of the anti-malware program so that they would not affect and do malicious actions to the PC again. 9. After placing the virus files in the program’s quarantine, it may prompt you to restart the computer to finalize the full system scan procedure. Please restart your computer if prompted, as it is essential. After the restart, Malwarebytes will open and display a message that the scan was complete.
9. After placing the virus files in the program’s quarantine, it may prompt you to restart the computer to finalize the full system scan procedure. Please restart your computer if prompted, as it is essential. After the restart, Malwarebytes will open and display a message that the scan was complete.
Note: Don’t forget to delete the quarantined files afterward.
Simply quarantining the malware files is not enough to make sure they are completely removed. This is a very common misconception: once you click the quarantine button, it is all good and gone.
But, while its effects and harmful activities are halted, the malware is still in the system, only placed in the anti-malware program’s quarantine folders. To completely remove it from the computer, go to Detection History from the home screen, select all Quarantined items, and click Delete.

You have successfully removed the harmful virus as well as other hidden threats on your computer. Rest assured they would not resurface again since Malwarebytes offers a premium trial for 14 days, so you could take advantage of it for free and prevent malware from infecting your system.
While the detection and removal of malware is free for Malwarebytes, the premium versions include real-time protection that ensures your computer is safe all the time. Although we encourage you to use the premium trial, you are free to purchase the full version if you find it useful.
The program is anti-malware that removes harmful threats like trojan horses, worms, stealers, miners, keyloggers, and many other forms of malware and computer viruses.
We suggest Malwarebytes if you are looking for a removal tool and as a second opinion scanner, but if you want full-fledged antivirus software, we believe that the built-in Windows Defender is sufficient for computer security, or if you want something with a more sophisticated system and better protection: Kaspersky Free.
If you choose to uninstall Malwarebytes, you may suddenly see that Windows Defender Real-Time Protection is turned off. This is a common issue that users may face when uninstalling the software. To fix this issue, you may refer to this article.
Alternative: Kaspersky Free Antivirus
After removing the malicious threats, you may want to install antivirus software to protect your system against malware.
More importantly, running an additional scan with a different program’s threat database will alert you to hidden Trojan viruses and rootkits that were not removed from the prior scan with Malwarebytes. Kaspersky is a widely known antivirus software that has been on the market for as long as the field of cybersecurity has existed. It is acclaimed by professionals in the field and is one of the most effective antivirus programs available. With its advanced internet security protection, it can also remove additional malware from the computer.
Kaspersky is a widely known antivirus software that has been on the market for as long as the field of cybersecurity has existed. It is acclaimed by professionals in the field and is one of the most effective antivirus programs available. With its advanced internet security protection, it can also remove additional malware from the computer.
What is the difference between anti-malware and antivirus? Anti-Malware software is designed to specifically remove malware and its variants. In addition, it employs heuristic-based detection by picking up harmful code from files.
On the other hand, an antivirus uses signature-based detection, which examines data for attacks to protect users from dangerous viruses, including keyloggers, loaders, worms, trojans, and others.
Malwarebytes and Kaspersky are identical, but Kaspersky is a better overall program since Malwarebytes’ main purpose is to remove malware, but Kaspersky has been known for comprehensive computer security protection ever since.
 Based on our experience removing malware, when two different programs are used to scan, various threats are identified by one software but not by the other. Given that their threat databases differ from each other, it might be able to capture harmful viruses, rootkits, and trojans that Malwarebytes has missed.
Based on our experience removing malware, when two different programs are used to scan, various threats are identified by one software but not by the other. Given that their threat databases differ from each other, it might be able to capture harmful viruses, rootkits, and trojans that Malwarebytes has missed.
Please be aware that if you decide to use Kaspersky, you should first uninstall Malwarebytes because having both security programs installed will cause a conflict. If you choose to do so, please remove Malwarebytes first, as it is essential to do so before we get started.
1. Click the button below to start downloading Kaspersky Antivirus on your computer. On the following page, we have provided clear details on how to install it on the computer. On the other hand, you may go to their official website by searching for the software on your web browser or typing Kaspersky.com (Beware of misspellings since cybercriminals typically use these as exploits to redirect users to malicious webpages).
2. Go to the download page for Kaspersky Free Antivirus. Before clicking download, you will be prompted to choose your continent and where your country is located. This is very important, and you should not choose a different country because you will be met with a “Not supported in your region” message during installation. 3. Once you click download, a setup file (startup.exe) will be downloaded on the computer. After it has finished downloading, open its file location, right-click the executable file, and then select Run as administrator. This will ensure that Kaspersky’s installation will be smooth and will not result in certain errors.
3. Once you click download, a setup file (startup.exe) will be downloaded on the computer. After it has finished downloading, open its file location, right-click the executable file, and then select Run as administrator. This will ensure that Kaspersky’s installation will be smooth and will not result in certain errors. 4. The Kaspersky installation wizard will launch, and you can then proceed to install Kaspersky Free by following the setup instructions. If a UAC prompt appears, simply accept it and proceed with the installation.
4. The Kaspersky installation wizard will launch, and you can then proceed to install Kaspersky Free by following the setup instructions. If a UAC prompt appears, simply accept it and proceed with the installation. 5. Please be patient while Kaspersky is being installed on your computer. The speed and length of the installation process will depend on your computer’s specifications. Kaspersky also mentioned that sluggishness or dark displays during the installation of their program are normal and should not be worried about.
5. Please be patient while Kaspersky is being installed on your computer. The speed and length of the installation process will depend on your computer’s specifications. Kaspersky also mentioned that sluggishness or dark displays during the installation of their program are normal and should not be worried about.
6. To use the antivirus program, you must first create an account on the sign-in page that appears after the antivirus application has been successfully installed on the computer. If you’re looking for the sign-up button, simply enter your email exactly as it appears; if you don’t already have an account, one will be created for you. 7. Kaspersky will ask you to decide which plan to use. It will be either the Standard version or Kaspersky Plus. In this case, the standard version is all you need for now. If you want to try the premium version of Kaspersky, you may opt for Kaspersky Plus to try the features for free. You do not have to add a payment method to get started, and after the trial ends, you will be downgraded to the Standard version unless you pay for it.
7. Kaspersky will ask you to decide which plan to use. It will be either the Standard version or Kaspersky Plus. In this case, the standard version is all you need for now. If you want to try the premium version of Kaspersky, you may opt for Kaspersky Plus to try the features for free. You do not have to add a payment method to get started, and after the trial ends, you will be downgraded to the Standard version unless you pay for it. 8. You will be asked if you want to install additional applications, namely Kaspersky Password Manager and a VPN. Feel free to opt for a program you might want to use; otherwise, install both, or choose not to if you do not need them.
8. You will be asked if you want to install additional applications, namely Kaspersky Password Manager and a VPN. Feel free to opt for a program you might want to use; otherwise, install both, or choose not to if you do not need them. 9. Kaspersky will ask you to scan for viruses in the background. Simply choose not to do so because we will be doing a full system scan later; however, doing a scan now will only initiate a quick scan. However, if you want to be safe, you can run the background scan now and proceed with a full system scan after.
9. Kaspersky will ask you to scan for viruses in the background. Simply choose not to do so because we will be doing a full system scan later; however, doing a scan now will only initiate a quick scan. However, if you want to be safe, you can run the background scan now and proceed with a full system scan after. 10. Once the antivirus application has opened, go to the security tab and click the choose a scan button. You will be presented with several different scans; go for the full system scan to ensure full computer security. Always remember to update the database because this will ensure that Kaspersky can detect newly discovered threats and exploits.
10. Once the antivirus application has opened, go to the security tab and click the choose a scan button. You will be presented with several different scans; go for the full system scan to ensure full computer security. Always remember to update the database because this will ensure that Kaspersky can detect newly discovered threats and exploits. 11. A full system scan will take a long time to finish since it will look into all the files on the computer, including the registry, memory, startup applications, and many more. The scanning time will depend on how many files there are on the computer and how big the files are. Additionally, the computer’s hardware and specs will also play into how long the scan will take.
11. A full system scan will take a long time to finish since it will look into all the files on the computer, including the registry, memory, startup applications, and many more. The scanning time will depend on how many files there are on the computer and how big the files are. Additionally, the computer’s hardware and specs will also play into how long the scan will take.
12. After the full system scan is finished, it may detect remnants of the hidden virus as well as other malware hiding in the computer, showing its location along with a detection name (HEUR:Trojan.Multi.Powedon, HEUR:Trojan.Win32.Generic, etc.) given to it. Go ahead and proceed to disinfect and restart the computer. 13. The Advanced Disinfection process will then start, and depending on the amount of RAM the computer has, it could take some time. It will then request a computer restart to complete the operation.
13. The Advanced Disinfection process will then start, and depending on the amount of RAM the computer has, it could take some time. It will then request a computer restart to complete the operation. Your computer will now have finished the entire system scan after restarting. By doing this, you can be sure that the virus and other forms of malware and viruses have been wiped from your computer.
Your computer will now have finished the entire system scan after restarting. By doing this, you can be sure that the virus and other forms of malware and viruses have been wiped from your computer.
You shouldn’t be concerned if the scan turned up no instances of malware or viruses, which indicates that there isn’t any malware on your computer. If two independent programs declare your computer safe, then that’s probably the case.
Protective measures for better overall security
Removing spyware and other tracking malware from your computer is one thing; keeping it secure for the future and for a long period is a different thing and will require certain things to make sure you are secured, especially if you do not know most of the ins and outs of the device you are using.
Cybercriminals are always stepping up their game to make sure they infect users and extract data and money from them.
We encourage you to take the actions listed below to ensure complete security before leaving this page because we strongly promote web security and having a secure online presence.
Safeguard your privacy and data by using a VPN application
VPNs, also known as virtual private networks, guarantee your safety and complete anonymity while you browse the internet.
In contrast to a firewall, which monitors and blocks potentially harmful connections in the network, A VPN hides the user’s connection via a tunnel so that it would appear to third parties as a different IP address and location.
This ensures that your data won’t be leaked because the program hides it. Be aware that visiting infected websites may cause your IP address and location to be disclosed; however, if you use a VPN, this will prevent your true IP address from being revealed to malware actors.
If you already had Kaspersky installed from the previous step, you had the choice to install its integrated Virtual Private Network, which is a good tool that we also advise.
However, if you decide against doing so and instead download a VPN-only program to cloak your web browsing activity, Mullvad, and AirVPN are excellent choices for fast connections and better privacy.
Mullvad VPN

Since user privacy is the main focus of a virtual private network program, Mullvad VPN excels at putting users’ privacy first. You do not need to enter your email address while registering to download their application because they maintain anonymous accounts.
If you wanted to hide or didn’t want your credit card information to be disclosed, they also accept Bitcoin payments. According to their website, they support a free internet that is devoid of surveillance and censorship.
They have also been announcing new server locations to guarantee users a fast connection anytime they want to connect to various areas throughout the world.
AirVPN
AirVPN seeks to provide users with access to the real internet, in contrast to Mullvad, which promises to offer users free internet. Along with masking your IP, they also don’t monitor or log any user data, which is good.
You can use it for a long time without worrying about being disconnected because they don’t impose a traffic or time limit when connecting to their servers. In addition, there are infinite, cost-free server changes with physically fast servers in many different nations.
Additionally, when registering for their program, you are not required to enter your email address. They also offer strong encryption and Perfect Forward Secrecy to ensure that it is difficult to determine the user’s connection.
Use an adblocker when browsing the internet
Installing an adblocker on the browser is the best way to prevent unwanted spyware from tracking your computer from being downloaded in the first place.
In this case, we recommend uBlock Origin, which is an open-source AdBlock extension that comes at no cost and is free forever. It is one of the most reliable plugins out there, ensuring that every advertisement on a webpage will be blocked.

For Google Chrome
1. Go to the Chrome Web Store and search for the browser extension, or click here to go directly to the extension page.
2. Click the Add to Chrome button. Then click Add extension when the confirmation window appears.
3. uBlock Origin is now installed in Google Chrome. The adblocker is turned on by default; you can click the power button if you wish to turn it off for a while. The menu can be found by clicking the puzzle icon in the upper-right corner next to the search bar.

For Mozilla Firefox
1. Visit the Firefox Add-ons Store and search for uBlock Origin, or click here to automatically go to the extension’s webpage.
2. Click Add to Firefox, and after that, a confirmation window will appear stating the permissions it will grant the addon. Finally, to add it to the browser, click Add.
3. Mozilla Firefox now has uBlock Origin installed. The adblocker is activated by default; if you want to disable it for some reason, simply click the power button. The menu can be found in the upper-right corner of the web browser, next to the search bar.

For Microsoft Edge
1. Go to the Edge Addon Store and search for the said browser extension. You can also click here to go directly to the plugin page of the Adblocker.
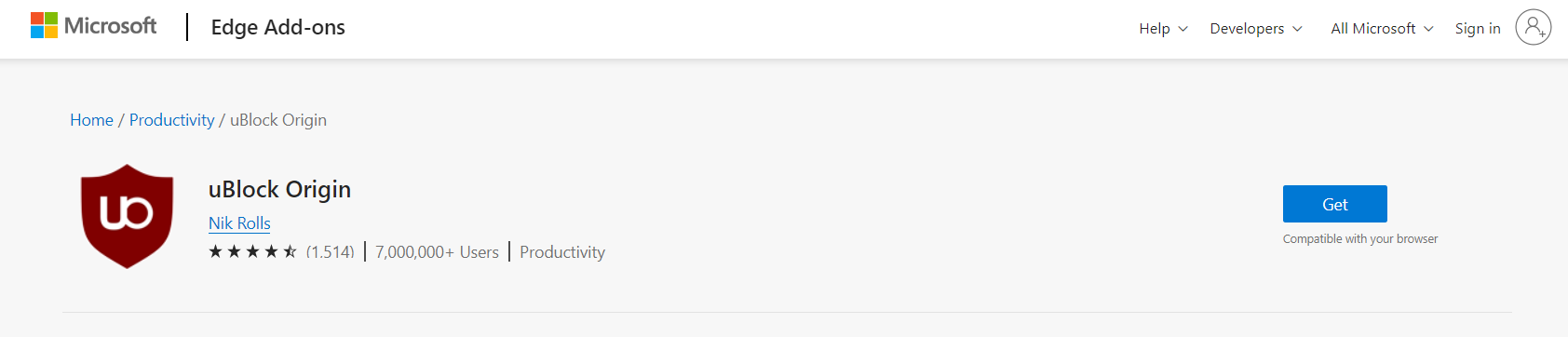
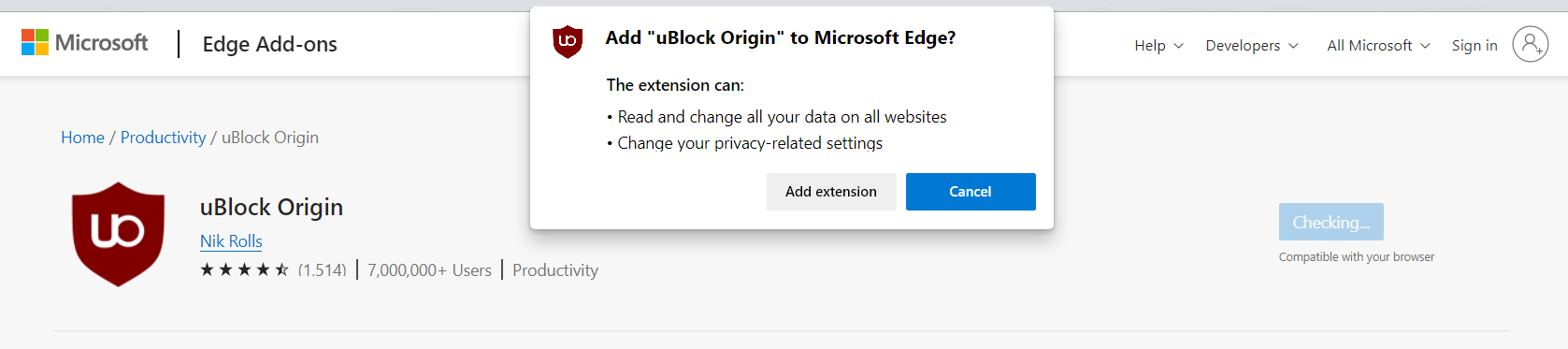
2. Click the Get button, and a confirmation window will appear. Continue installing the extension by selecting Add extension.
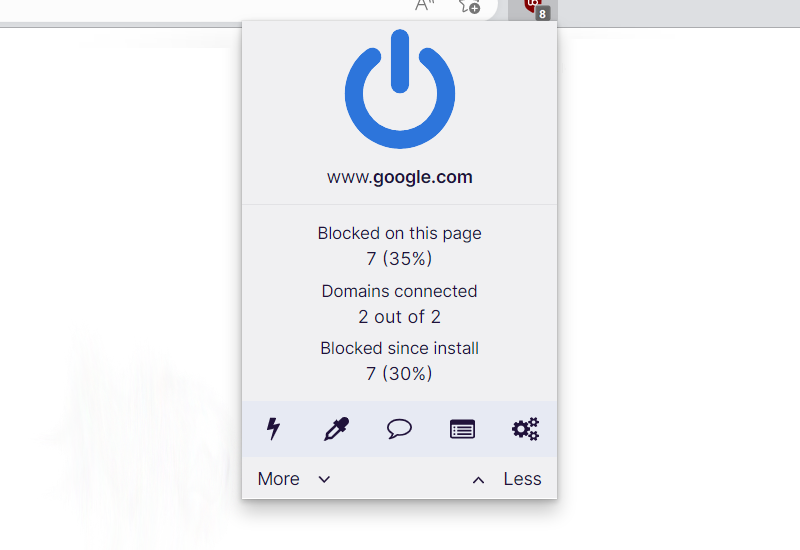
3. Now that uBlock Origin is installed on the browser, you can choose to disable the Adblocker by clicking the power button. The menu can be accessed by hovering over the extension’s icon next to the search bar.
The majority of pop-up advertisements, whether they include malware or not, will be filtered by the extension and no longer be displayed to you. Currently, uBlock Origin is not available for Mac or iOS users, but there are plenty of free options on the market, such as AdBlock for Safari.
Utilize a firewall to prevent cyber attacks
A security firewall is required for every internet connection that is made. It is an essential tool that enhances security and stops online attacks. Through a security mechanism, it controls incoming and outgoing network connections on your system and network and filters the undesirable ones. Consider it a further barrier against malicious assaults and zero-day exploits.
You don’t need to do anything if you installed Kaspersky in the previous step because the program we installed earlier comes with a built-in firewall that is turned on by default.
On the other hand, if you prefer a standalone, fully functional firewall utility application that is exclusively focused on securing the network, we recommend these top two firewall solutions for personal computers: Comodo and ZoneAlarm.
Comodo Personal Firewall

Comodo Firewall is a well-known software program for securing your network and computer. It is a sophisticated tool with a wide range of features.
It is simple to use and doesn’t require complicated configuration to set up. It also functions by being aware of your computer usage habits to avoid interfering with your work.
Additionally, it also claims to offer the highest levels of protection against both inbound and outbound threats. It secures the ports on your computer from hackers and prevents rogue software from sending your sensitive data over the internet.
ZoneAlarm Free Firewall
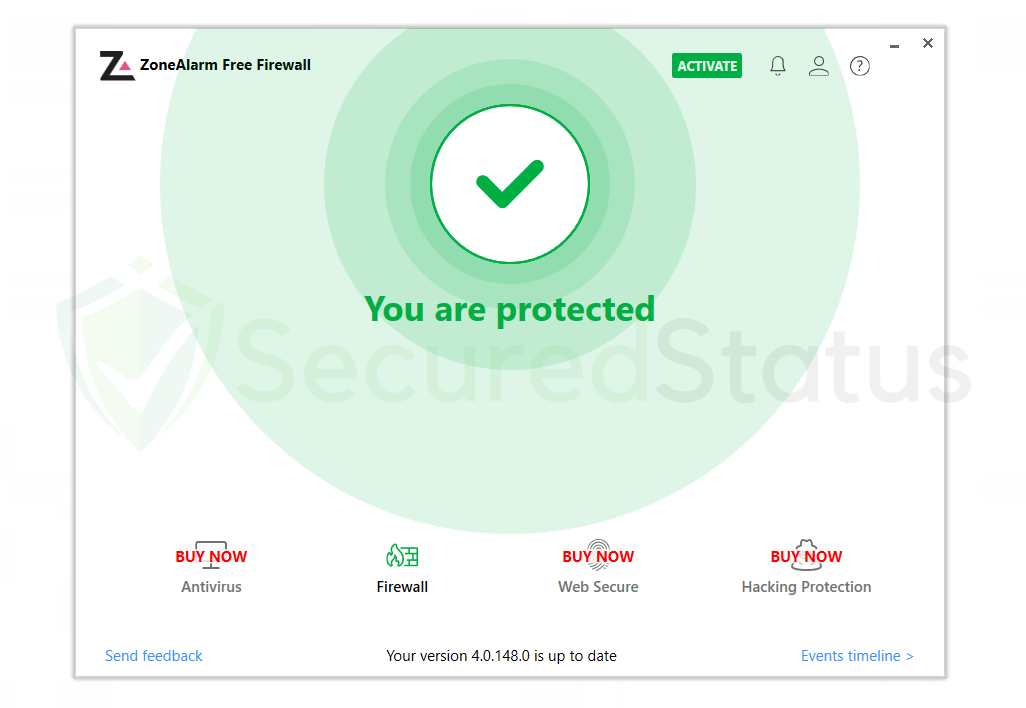
You can also opt for ZoneAlarm Free Firewall as your first line of defense between your device and the internet. The program safeguards your network and blocks any dangers, and you can use the free version of it without paying anything.
It provides a robust two-way protection solution that guards against spyware from disclosing your data online while also hiding your PC from nefarious hackers.
With its cutting-edge anti-bot protection, it also protects your computer from automated cyberattacks in real-time.
Additionally, it protects your computer against spam and dubious websites, and many others. Lastly, it provides real-time defense against automated cyberattacks with its cutting-edge anti-bot security.
Final Thoughts
Even after taking the necessary precautions, it can be very unsettling to have scam email messages that can trick users into sending a large amount of money.
This is why we suggest browsing safely and not entering your email address on random text fields because that is most likely the cause of why you receive such emails.
