Android devices are highly susceptible to being infected by malicious programs. To avoid being discovered by users, these programs often use a variety of disguises and other hiding techniques.
What are Hidden and Malicious Apps, And Why Should You Remove Them?
Malware applications such as spyware, keyloggers, and remote access tools have been a major concern for android device users.
Since mobile phones have become standard in this age of advanced technology. Cybercriminals have seized this opportunity to infect consumers with harmful software.

These hackers designed and developed programs with harmful and unethical purposes that could endanger both the android phone and its owner.
When such hidden programs are installed on the Android operating system, they can do actions such as:
– Steal sensitive data from the user’s phone, including email addresses, financial and banking information, contacts, social networking accounts, and other credentials.
– They have the ability to monitor user activity and secretly gather private data while hidden and running in the background of the system.
– Completely disregard user privacy by using the phone’s camera and audio to discreetly record what the user is doing in reality.
– These applications have the capability to delete and corrupt essential phone files, then demand a ransom to recover them.
– If the hardware in your phone is strong enough, they can also use it to mine cryptocurrency while hidden in the background.
Android users need to be conscious of the dangers posed by malicious software and take precautions to safeguard their devices.
This entails creating strong passwords, staying away from dubious sites and keeping the operating system of their device patched with the most recent security updates.
How to Inspect Your Android Device for Hidden Apps
Depending on the user’s tech literacy, one may be able to find hidden programs that are present in the Android system.
These malicious programs have started to employ a wide range of strategies to cover their tracks once they are inside the system.
With that said, we will outline the typical techniques for identifying harmful programs on the Android phone.
Malicious Hiding Apps Employ Generic System Names
These hiding applications typically uses generic names that most Android phones have pre-installed on the system. Some examples of this would be Google Play Services, WiFi, Find My Device, System Update and etc.
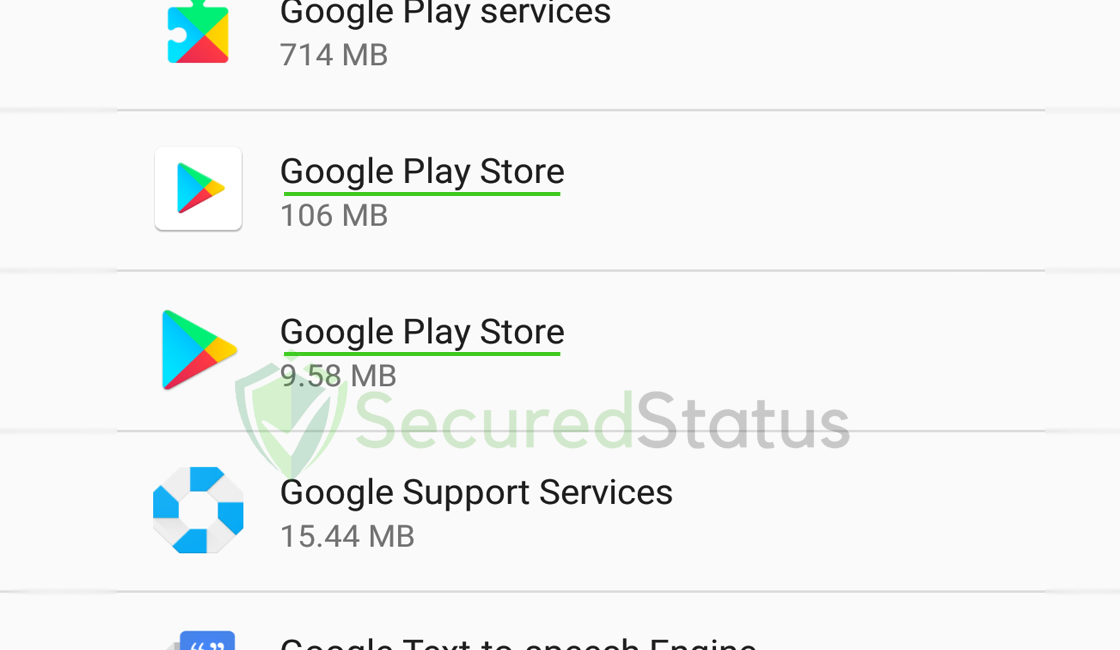
Since there are two Google Play Stores, as can be seen in the screenshot above, the other one is almost certainly a malicious program. Check your device if you have two applications of the same name.
They Use The Default Application Icon
Another aspect to look out for is if they don’t use any application icons and instead have the default icon set for programs.
Since most people don’t even check the programs list in the settings, harmful hackers frequently don’t even bother to create an application icon if it will only run in the background.
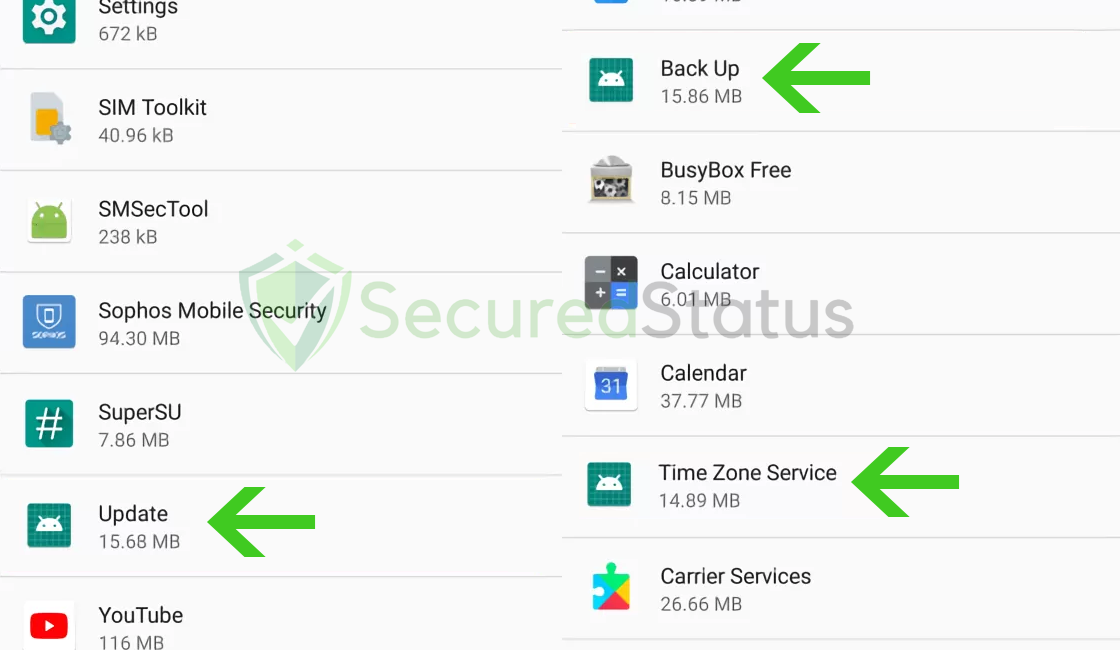
The three applications in the image above all have the same generic application icon and names.
While it may be a system application, the main takeaway is that not only do they have the same default images but the same file sizes as well.
If you can discover an app with a default image in your device’s list of applications, check it out because it might only be malware and not one of the system apps.
They May Take The Appearance Of A Utility Program
Harmful applications operate in the background, but some of them also pretend to be device cleaners, boosters, and VPN programs in order to hide in plain sight.
In truth, these strategies might also be widespread; they spread due to fraudulent websites that fool users into installing them for security or faster phone performance. Below is an image of such websites as an example.

Users are advised to remove any unused utility apps that are unfamiliar or were installed on their phones through dubious methods.
If you have previously browsed such websites, you can quickly locate the applications on the home screen because they don’t conceal themselves but rather take the form of utility programs.
How to Uninstall Malicious Hidden Apps from Your Android Device
If you’ve finally discovered the malicious software that’s been hiding in the system. It’s time to get rid of them as soon as you can to stop further harm from happening to the Android phone, user accounts, and the files inside it.
Don’t worry if you can’t find it; we’ve included an automated detection and removal procedure in one of the methods below.
Here are two proven ways for removing the harmful spyware applications from an Android device completely.
Uninstall Hidden Application Manually
1 Go to the Settings application and head over to the application menu. It is the menu wherein installed applications are seen. Since many android devices are different, there are also different locations for this menu.  2 Scroll down the installed applications and find the malicious application.
2 Scroll down the installed applications and find the malicious application.  3 Once you find the suspicious app, click it and uninstall. For this guide, we are using Smart Cleaner Ultra as an example.
3 Once you find the suspicious app, click it and uninstall. For this guide, we are using Smart Cleaner Ultra as an example.

If you cannot uninstall the malicious hidden application, it is most likely due to the device administrator it was granted.
To remove this permission, go to Settings > Security > Other Settings > Device Administrator. Remove the permission of the malware application then try to uninstall it once again.
Method 2: Delete Hidden App Automatically
Malwarebytes is a renowned anti malware tool and it has one of the best threat detection rate. As we previously said, if you haven’t discovered the malicious application, you can use this tool to perform the detections and have it removed from your android device automatically.
1 First, go to the Google Play store and install Malwarebytes Anti Malware.  2 Once installed, it will ask you for permission to access files. Allow it access to manage the files on the device, it is needed in order to detect malicious threats
2 Once installed, it will ask you for permission to access files. Allow it access to manage the files on the device, it is needed in order to detect malicious threats

3 Click Run a full scan to detect potential threats on the whole device. Since this may take a while, you can simply close the application and let it run on the background. You can see the progress of the scan through the notifications.

4 After the scan is complete, the detected threats will be shown on the screen and all that is left to do is to eliminate them. Click the Remove Selected to get rid of the threats.

We advise you to run a routinely scan of the device to ensure that it is continuously malware free.
We also recommend to use Malwarebytes Real Time Protection, which will secure your machine and detect any threats as soon as they appear.
