What is “Duck”
“Duck” is a malicious extension that redirects and hijacks the user’s browser. It can cause the browser to do unwanted actions and it can even log the data being sent and received while browsing.
Since it violates the privacy of the user, this type of extension is flagged as malware and should not be kept in the browser. This malware that spreads through Google Chrome is called ChromeLoader.
It takes the form of a web plugin with a cog wheel icon. Every time this threat is updated, it alters and assumes many different names. There have been many variations of the aforementioned extension.
This has become a nuisance to many people because the extension and it’s source folder are both very difficult to delete. The “Duck” extension’s symptoms are particularly annoying to computer users.
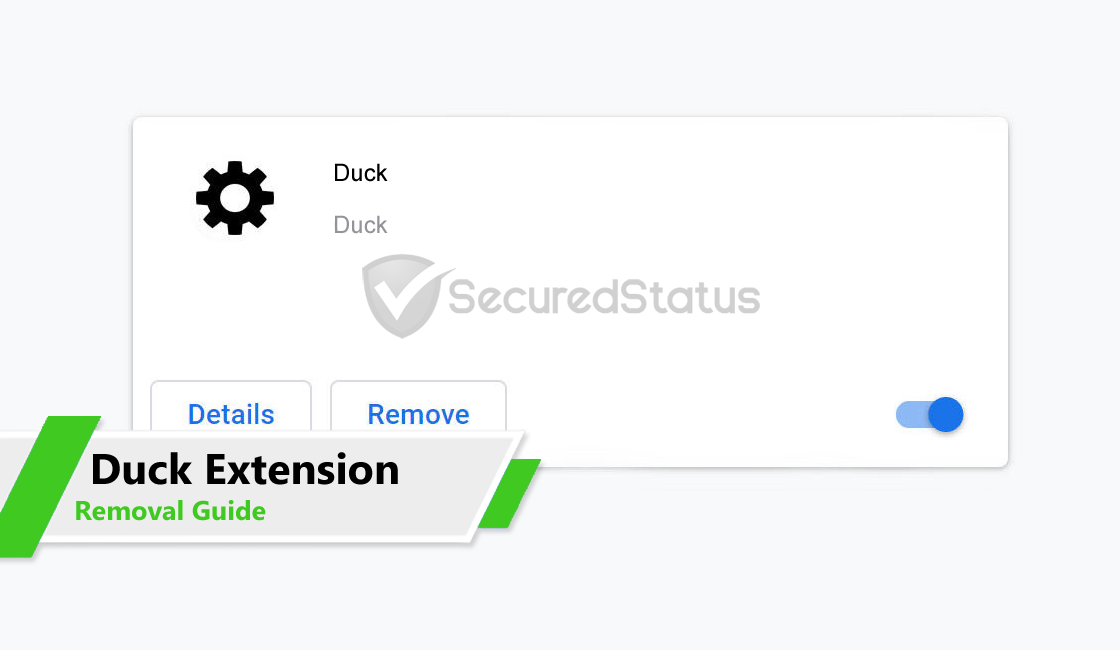
Addition to that, it can also be dangerous because the virus has the ability to steal information. The following are typical effects of browser hijacker malware:
- It sends the compromised browser to many unknown websites.
- When you conduct a search in Google, it will redirect you to a domain like Goog.example.com then it will send you to Bing. • Constant pop-up advertisements on the browser and computer.
- The web browser frequently crashes and becomes slower than usual.
- Unknown extensions are installed unexpectedly. It is advisable to remove it off the computer because keeping it exposes the device to several security risks.
However, despite numerous users’ attempts, the malicious extension consistently resurfaces after being deleted from its source folder.
You might have followed many removal instructions, but they were unsuccessful in getting rid of the extension infection from your computer. We’ll be happy to show you the way to remove the malicious extension and make sure it does not come back again.
“Duck” Removal Instructions
This procedure will assist you in removing the malicious extension as well as any dangers related with the browser hijacker infection. You can rest assured that the information provided below has been tried and tested.
Step 1: Remove the “Main Source” of the Extension Malware
Whether you want to believe it or not, the malicious extension is not primarily sourced from the Chrome folder. Although this step may have been mentioned numerous times, users constantly struggle with the problem of “I don’t know what to delete.”
The answer is you would need to delete unknown programs with names like Markets.exe, Energy.exe, Bloom.exe, and Travel.exe since they are the real source of the problem. We should note that on your computer, a different name might appear, but you should eliminate unidentified programs that use the same naming convention. You may find the said program inside the AppData\Roaming directory.
1 Search and find the malicious exe file like the names mentioned above.

2 Open the file location and delete all the contents of the folder.

3 Make sure you have removed all the files in the folder or remove the folder itself.
STEP 2: Remove the Time Trigger Task set by the Virus
The main reason why the the “Duck” extension and the folder keeps coming back after deleting it is because there is a time trigger task set every five minutes to check to see if any of the contents have been erased, so even after removing everything, it keeps returning.
Now that the installer program has been removed, you ought to be able to finish this procedure.
1 Click on the Windows button and search Task Scheduler.

2 Once the program has opened, get rid of time triggers with names similar to the malicious chrome folder. (Example: Chrome_Bookmarks)

3 Click on the task and select right click delete to get rid of it.

STEP 3: Remove the Chrome extension folder
For the step that most users have found difficult to do. Now that the malware’s other components have been taken out, we can move on and permanently delete the extension as well as it’s folder.
1 Go to the Appdata/Local and go to the Chrome extensions folder.

2 Right click the Chrome folder and delete it. Now that the source folder is removed, the browser extension should not function anymore and will be removed from the browser since it does not exist anymore.

STEP 4: Scan with Malwarebytes (Optional)
If you want to double check your device if the browser extension virus still remains. You may utilize Malwarebytes Anti-malware to scan your devices for traces of the said virus.

They have some of the best threat detection tools, ensuring that any malicious malware on your computer is completely removed.
1 Visit the official anti-malware website or click the button above to download the most up-to-date version of the software that best suits the requirements of your computer. You will also be getting a 14-day trial of the premium program as you download the application for the first time.

2 When prompted to choose between personal and organizational use, click the personal option unless you are downloading it within your company. From then on, follow the installation procedure given on your computer’s setup screen.
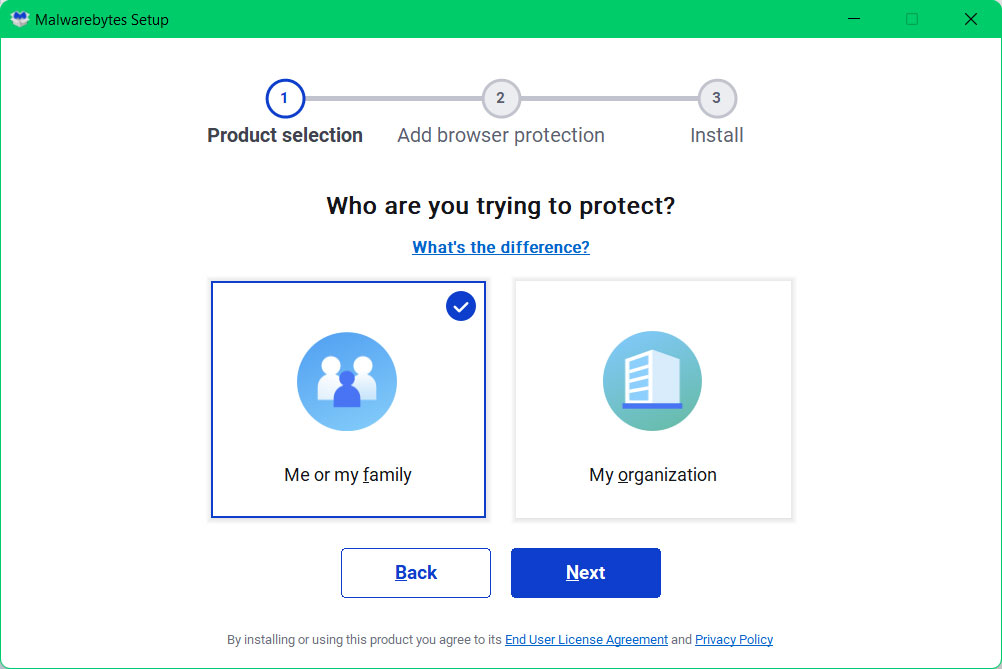
3 After following the software setup instructions, wait for the application to finish installing.

4 Once the application is installed, run your first computer scan and wait for it to finish.
5 All discovered malware on the computer will be displayed on the screen, and you can eliminate them by pressing the “quarantine” button.
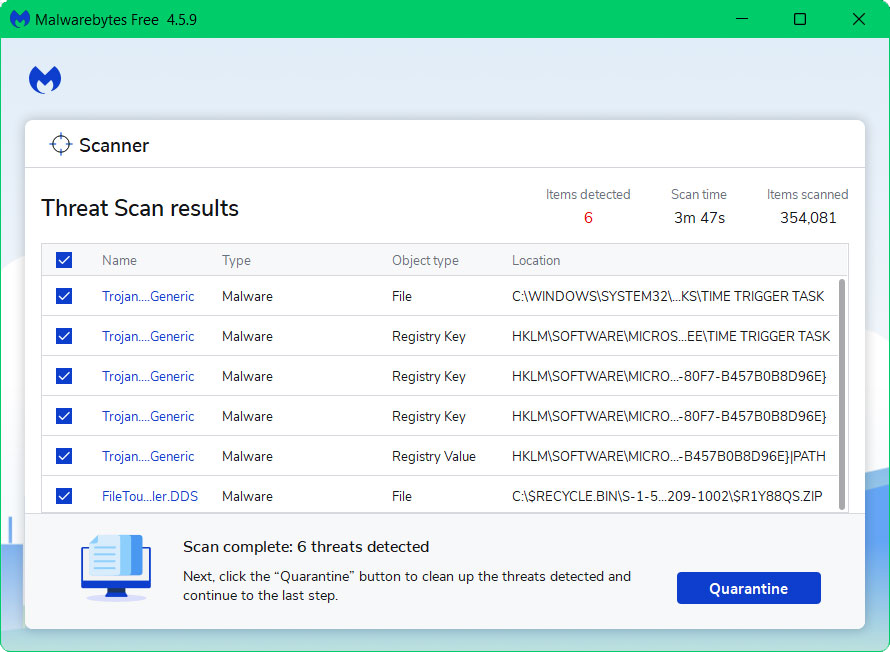
Once the process is complete, the “Duck” extension, as well as any other malicious threats found on the computer, should be removed. Activating Malwarebytes Real Time Protection is also recommended, as it will secure your computer and detect potential threats as soon as they surface.
Concerned that it might return? There is no longer a need to do this because we promise it won’t return. A few users have also claimed that the installation of BlueStacks and other similar emulators led to the installation of this malicious extension on their computers.
You should also remove the emulator program and its associated files for best security. Here are a few things to keep in mind to make sure your device is safe and well protected against malicious threats.
Some Internet Safety Tips
- Websites with distinctive domain extensions should be avoided. Domain extensions other than .com, .org, .net, and .edu should be avoided because most infected websites have very distinct TLDs, always check the last section of a domain to make sure you’re on a safe site, unless it’s been reputable for a long time.
- Never download software or programs from unknown sources. This is one of the most popular ways for adware and other malware to infiltrate your computer. Download only from recognized and legal sources. To be secure, avoid torrent downloads and cracked software download sites, as the files will almost always contain viruses.
- One of the most reliable ways to be safe online is to use a firewall. It protects users from potentially hazardous websites by acting as a first line of protection. It keeps intruders out of the user’s network and device. In today’s world, a firewall will protect a user from the risks that lurk on the huge internet.
- Anti-virus software must be kept up to date. These programs should always be updated on a computer since hundreds of new malware threats are produced every day that aim to infect the machine’s weaknesses. Antivirus updates contain the most recent files needed to combat new threats and protect your computer.
- Visit only websites with a secure connection. Since HTTP connections do not encrypt the data they receive, they are not considered secure. Entering personal information like email addresses, phone numbers, and passwords on a website that uses an HTTP connection is hazardous since your information could be stolen. Websites that use HTTPS connections, on the other hand, are more secure because data is encrypted and attackers are less likely to obtain access to information shared within the site.
