PUM.Optional.DisableMRT is the detection name given by Malwarebytes Anti-Malware to the threats detected by its software. This type of threat is malicious and can do unwanted actions to the device it infects.
Malwarebytes has informed you of this threat because it had discovered the specific malware on your computer during the program's routine scans.
These detection warnings should not be taken lightly since it means that your device is vulnerable and can be exploited by malicious actors.
You should take appropriate actions once the anti-malware software notices these types of threats on your device. It is always best to get rid of it before it can do much harm to the computer.
These threats are often acquired through spam emails, infected websites, or by clicking on a link in an email. Once installed on the computer system, PUM.Optional.DisableMRT will begin to spread across your PC via Windows System files.
Hackers may be able to view all the data on your computer and even take over its operation once they have been deployed on the system.
Threats like these should not be allowed to remain on the computer for an extended period because they may result in irreparable harm. Malwarebytes will continue to warn you about the malware until you take action to remove it.
Users who have PUM.Optional.DisableMRT on their devices are most likely to face the following problems.
- Sudden issues with internet connection and applications
- Freezing or slowdowns in computer performance
- Difficulties opening documents or accessing files.
- Unusual pop-up ads appear online or when browsing.
- Overheat and high CPU usage.
These kinds of discoveries are particularly risky since they can be used to attack unsuspecting users online by stealing their financial information, privacy passwords, and other data.
It is critical to get rid of this particular virus as soon as you suspect you may have been impacted by it.
Considering that Malwarebytes was the antivirus program that identified and located the malware on your PC. Their software would be sufficient to remove the PUM.Optional.DisableMRT threat.
Unless certain circumstances prevent the anti-malware program to eliminate the said malware, the best solution is to run it in safe mode before trying to eliminate the virus since there could be other processes that prevent the threat from being deleted.
Safe mode only utilizes the system required drivers and software so removing PUM.Optional.DisableMRT in that mode will be much easier.
To remove the detected threat from your system, kindly follow the instructions provided below.
How to Remove PUM.Optional.DisableMRT
You can fix the threat detection issue on your device using the steps provided below. What we share is proven and tested so we guarantee that it will work for you.
Step 1: Enter Safe Mode with Networking
Safe mode is important because it allows you to troubleshoot any problems that may be preventing your computer from operating properly which in this case is malware. This mode will allow users to find and identify malicious threats easily since it only uses essential drivers and software.
To launch Windows Safe mode with networking, click the Windows button + R simultaneously to open the run dialog box.
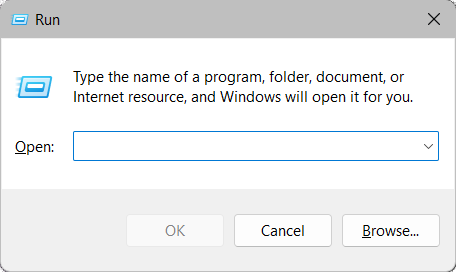
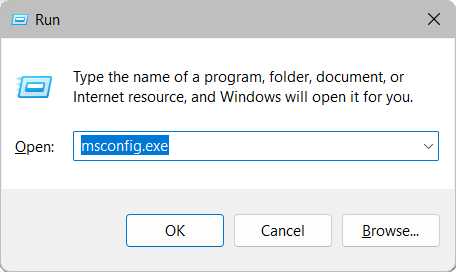
Once the run box is open, type msconfig.exe to open the Microsoft system configuration window.
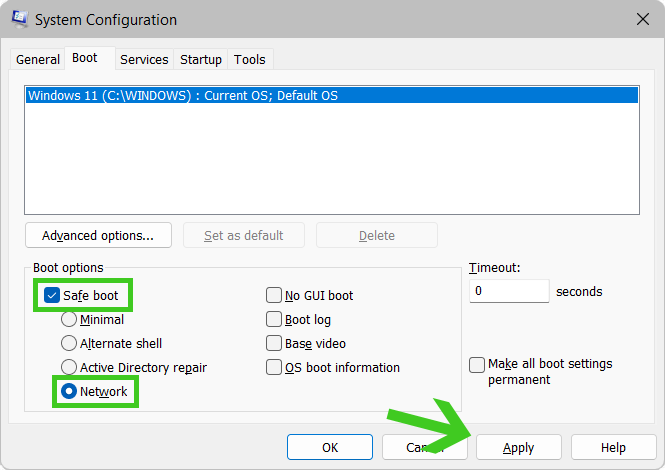
After the system configuration window has opened, click on the Boot option, tick Safe Boot, and then select the option below that indicates Network. You should then be booted into safe mode with networking after clicking apply.
Once you are in the Safe mode, you may now proceed to the next step below which is to remove the malware from the computer system.
Step 2: Use Malwarebytes to Remove PUM.Optional.DisableMRT
This program is one of the most effective anti-malware programs available. They have some of the greatest threat detection software, ensuring that any unwanted threats on your computer are eliminated.

You can utilize this antivirus program to complete the task since it was this program that detected the malicious threat. Furthermore, even if PUM.Optional.DisableMRT is completely removed from the computer, we recommend that you run a complete scan just in case.
1 Visit the antivirus website or click the button above to download the most up-to-date version of the software that best suits your requirements.
2 Follow the software installation instructions until they are completed.
3 Run a complete malware scan on the machine and wait for it to finish.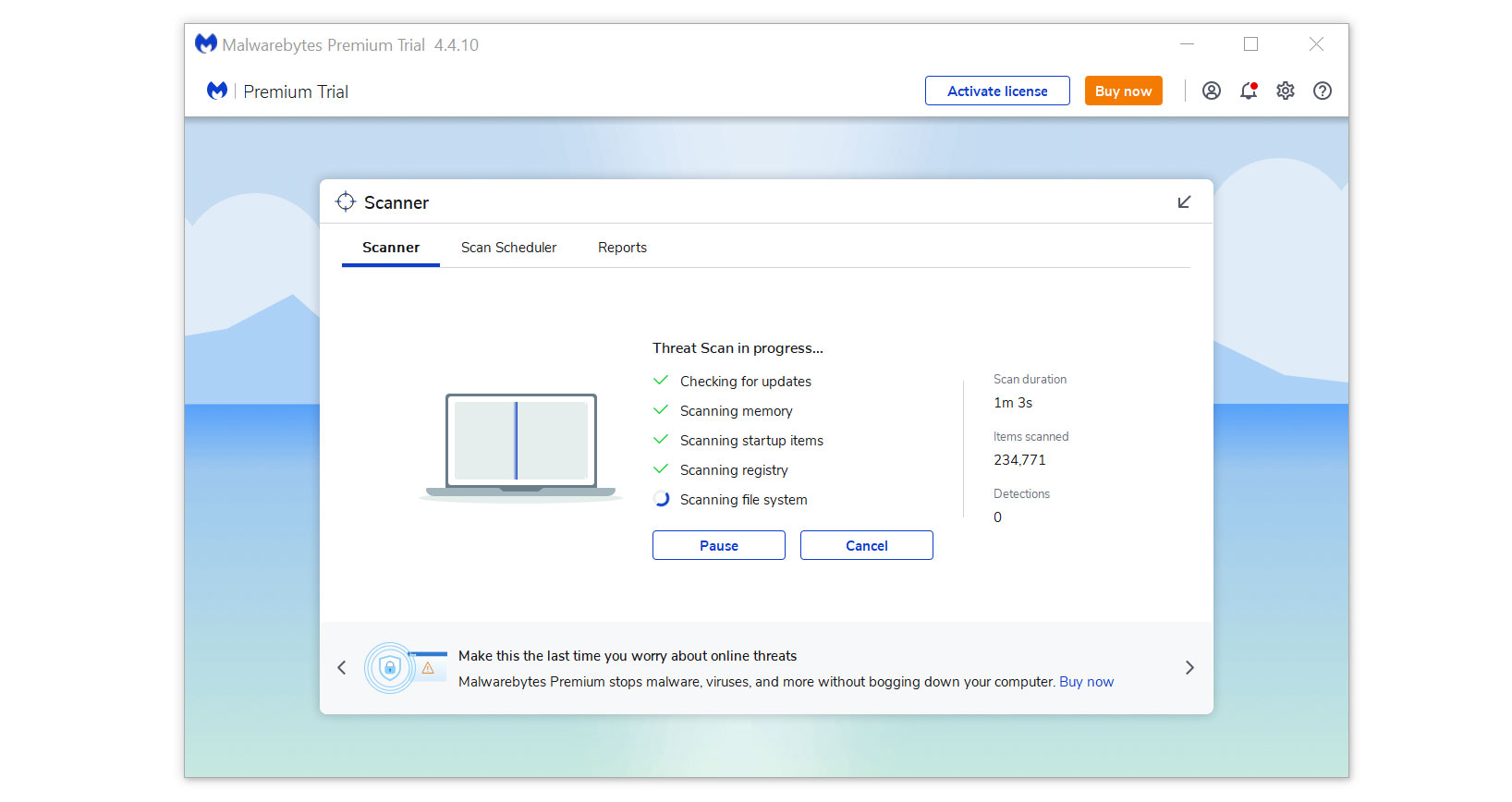
4 All the detected threats found on the computer will be shown on the screen and clicking the "quarantine" button to remove them.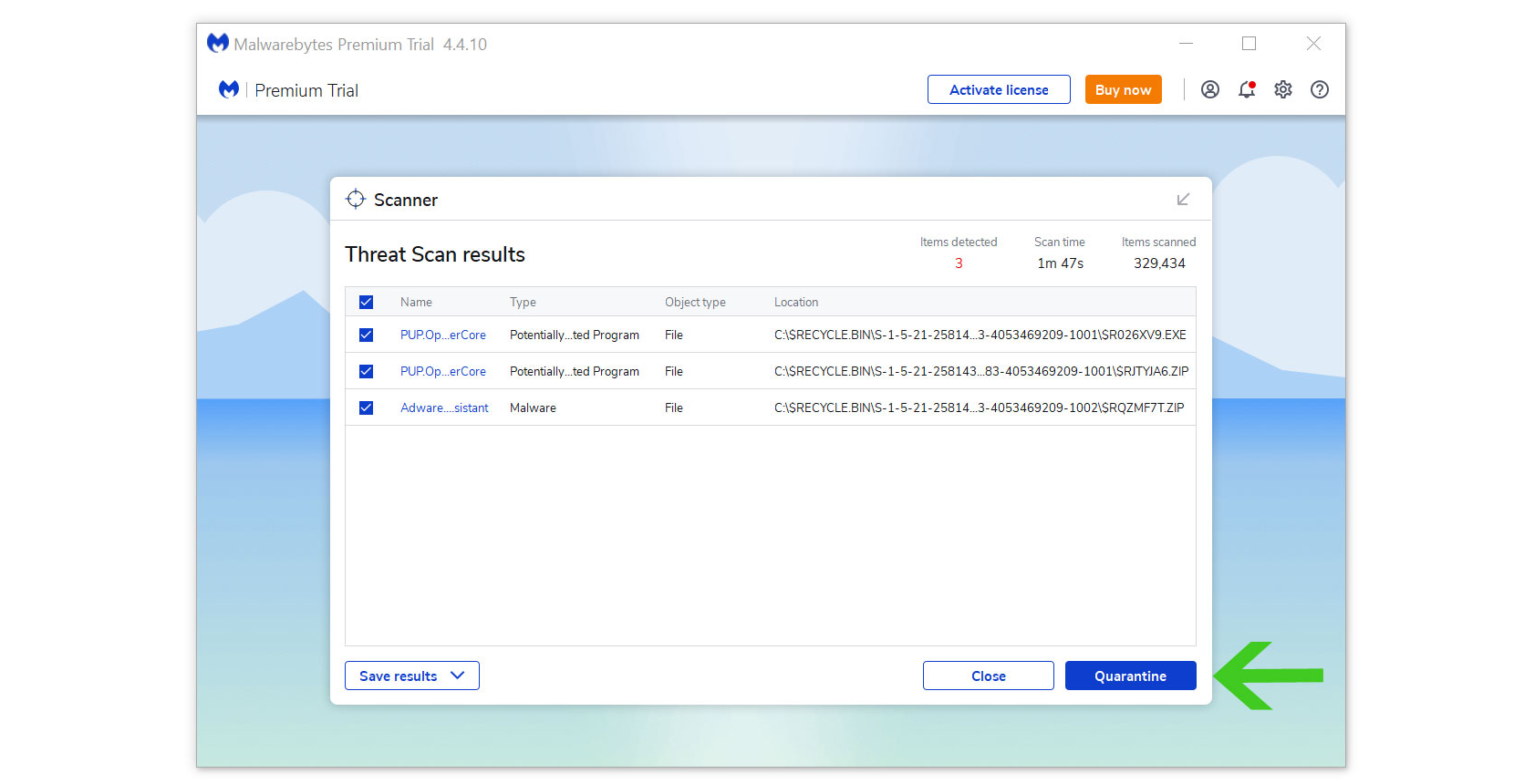
PUM.Optional.DisableMRT, as well as any other harmful threats discovered on the computer, should be eliminated once the process is complete. We also recommend using Malwarebytes Real-Time Protection, which will secure your machine and detect any threats as soon as they appear.
Alternative: Kaspersky Antivirus
There are instances where a different antivirus can find something another antivirus cannot. In this situation, if the first antivirus program didn't work, we advise doing a scan with a different one.
If you visit numerous forums and websites, you will see most users agree that Kaspersky is one of the best antivirus tools available. To use this program, you would have to exit safe mode first.

Since each antivirus application has its threat database, Kaspersky's detection technology may be able to find viruses that the prior program missed.
To ensure sure viruses are removed from the system, we advise running a scan just in case. If you are downloading the application for the first time, you will also receive a 31-day premium trial.
1 Download the Kaspersky Security Cloud by clicking the button above.

2 Once the setup has finished downloading, open the file and start the installation.

3 Wait until the wizard finds the latest version of the application or click Skip to install the current version stored.

4 Review the License Agreement. If you agree to its terms, click Continue.

5 Follow the installation instructions as shown then finally click install. (You may choose to uncheck the options shown if you do not want those features.)

6 Wait for the application to finish installing, then after the process is complete, click done.

7 Apply the recommended settings then start the application by clicking apply. Feel free to untick the options you do not desire.

8 You will be prompted to create an account and once you are finished, you will be redirected to the main screen. Select the Scan tab then click the run full scan and wait for it to complete. (Before scanning, we recommend you update the database to ensure any new malware variants are detected.)

After the scan has finished, the detected threats will be deleted from the computer. Reset the computer if prompted to do so.
Tips to Keep Your Device Safe
- Never download software or programs from unknown sources. This is one of the most popular ways for adware and other malware to infiltrate your computer. Download only from recognized and legal sources. To be secure, avoid torrent downloads and cracked software download sites, as the files will almost always contain viruses.
- One of the most reliable ways to be safe online is to use a firewall. It protects users from potentially hazardous websites by acting as a first line of protection. It keeps intruders out of the user's network and device. In today's world, a firewall will protect a user from the risks that lurk on the huge internet.
- Anti-virus software must be kept up to date. These programs should always be updated on a computer since hundreds of new malware threats are produced every day that aim to infect the machine's weaknesses. Antivirus updates contain the most recent files needed to combat new threats and protect your computer.
- Only visit websites that have a secured connection. A site with an HTTP connection does not encrypt the data it receives and therefore is not considered secure. Entering personal information such as email addresses, phone numbers, and passwords on a website with an HTTP connection is risky since it could be compromised and your information was stolen. Websites with HTTPS connections, on the other hand, are secure since data is encrypted and attackers are unlikely to gain access to information exchanged within the site.

