Task Manager is a legitimate Windows program however there may be malware posing with it’s name and icon to disguise itself within the system.
It may cause slowness and overheat to the infected computer. It can perform many actions on the computer such as steal data, track sessions and use the compromised computer’s hardware for the attacker’s own gain by using it to mine crypto.
A coin miner typically spread in the same way that most computer viruses do. Task Manager can infiltrate a computer system in a number of methods, but the following are the most typical ones:
Spam email attachments: It is the most common and widely used strategy. It deceives the intended recipient into downloading malicious software that is attached to the attackers’ email. The files are either bundled together or disguised as documents, movies, and voicemails in the attachments.
Drive-by Download: It occurs when a person visits an infected website that has been injected with a malicious script that causes a random piece of software to be downloaded. Hackers can then use these flaws to obtain unauthorized access to targets’ systems once they’ve been clicked.
Torrent files: It is used by millions of pirates all over the world to obtain pirated movies and records, as well as cracked versions of premium software. If you’re downloading from a torrent site, it’s worth checking the file extension because it’s usual to find that a pirated movie or music is contaminated with a virus if it’s in the.exe format. Moreover, torrent files should be scanned for malware after download.
How does infected/corrupted Task Manager miner work?
Cryptomining malware is a type of harmful virus in which cybercriminals gain access to computers and laptops in order to install malicious software. This malware takes use of the computer’s processing power and resources to mine for cryptocurrencies or perhaps even steal cryptocurrency wallets from users who unintentionally downloaded their bait file.
Cryptocurrency mining refers to the process of generating or merely mining new coins of a certain cryptocurrency. It is quite simple to accomplish, but the resources required for mining must have excellent specifications and a powerful hard drive. If several processors and computers mine at the same time, the total number of mined cryptocurrency increases.
That is why cyber thieves are resolute in developing cryptojacking software to unwittingly mine cryptocurrency using the power of their victims’ computers. People infected with the coin miner malware are likely to encounter high CPU utilization, slow processes, and system overheating.
Methods to Fix Task Manager High CPU and Memory
Each method listed below has been tried and tested by our experts because there could be several factors for this problem. If the first one doesn’t work for you, try the next one until the problem is fixed.
Method 1: Utilize System File Checker and DISM Cleanup
DISM Cleanup and the command-line tool Windows System file checker can be used to verify the stability of all significant system files. Additionally, it checks to determine whether any system files are missing or corrupted by comparing them to their original versions.
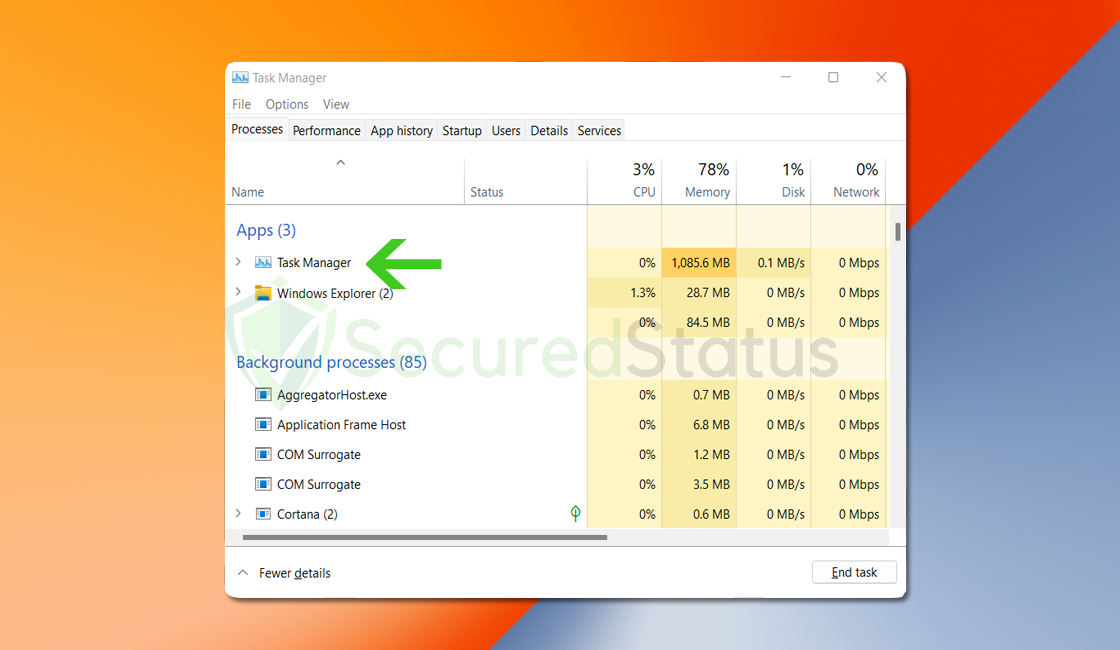
1 Click the Windows Button from the keyboard and search for CMD or Command Prompt.
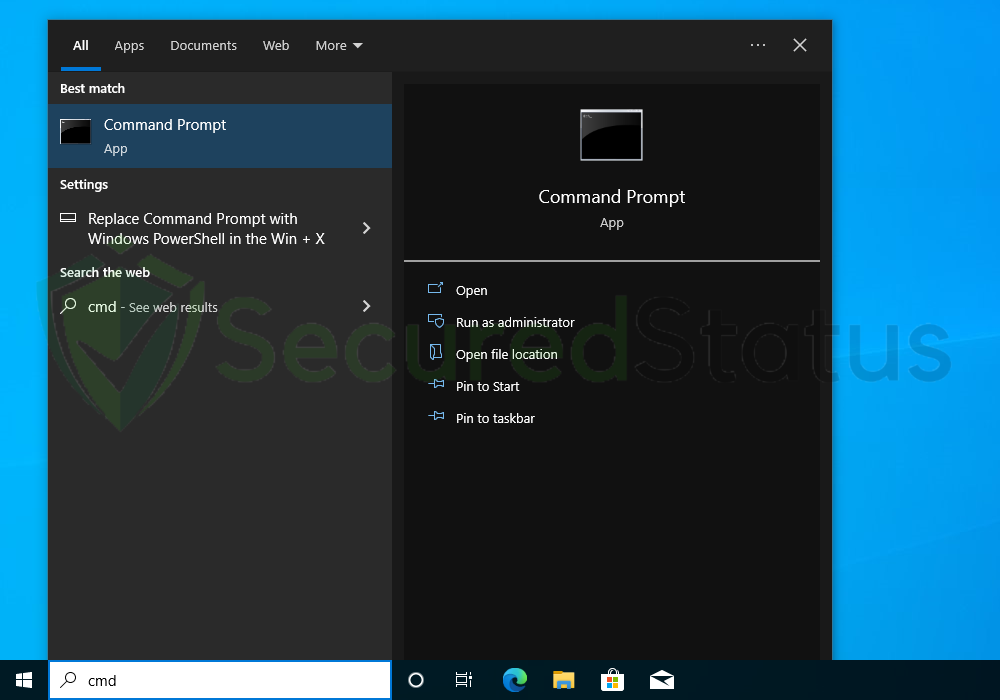
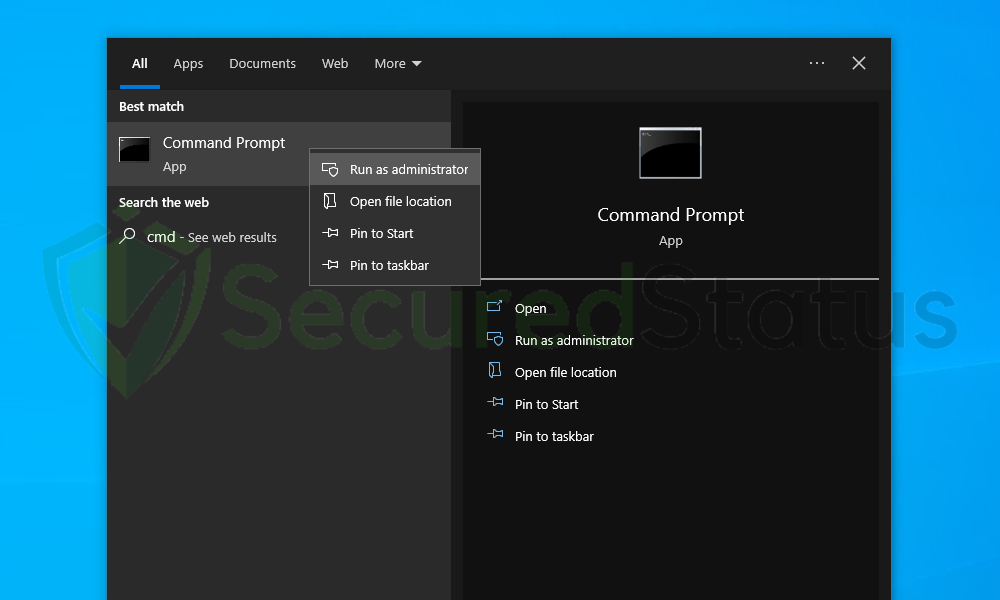
2 Right click the Command Prompt application and select Run as administrator.
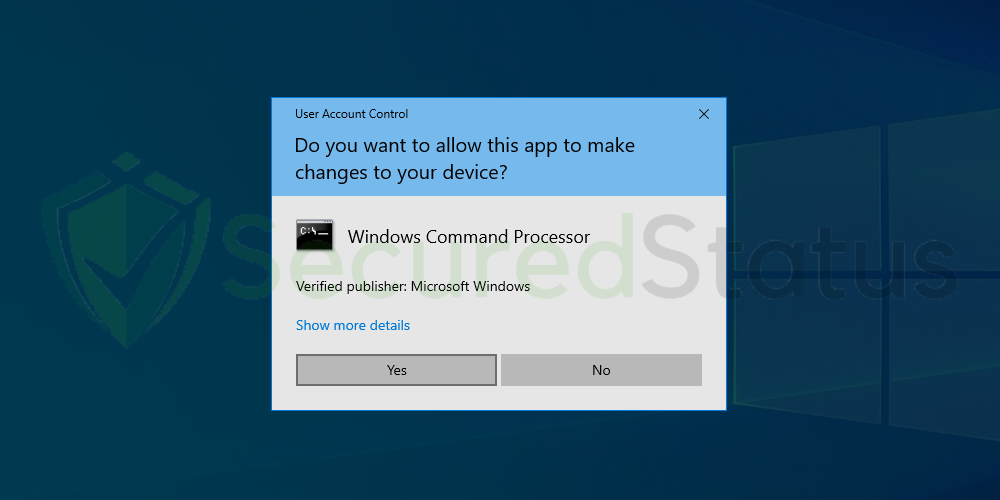
3 The User Account Control confirmation message will pop-up, click Yes to proceed.
4 Once the Command Prompt opens, type sfc /scannow and hit enter. Please be patient for a few minutes as the scan will start and could take some time.
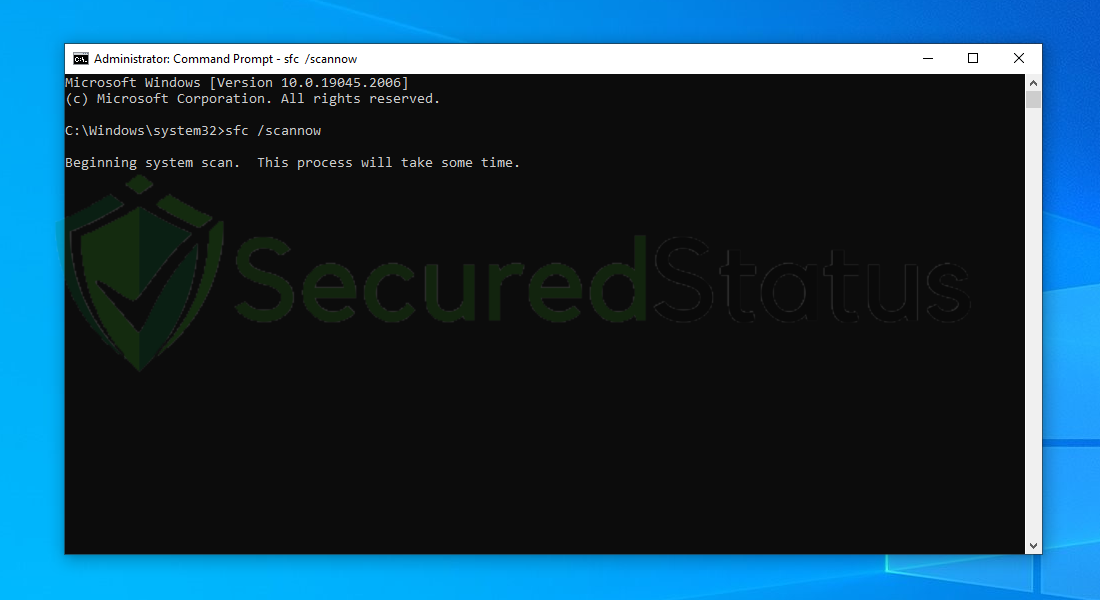
5 After the scanning process it will report that it have successfully found corrupt files and have repaired them.
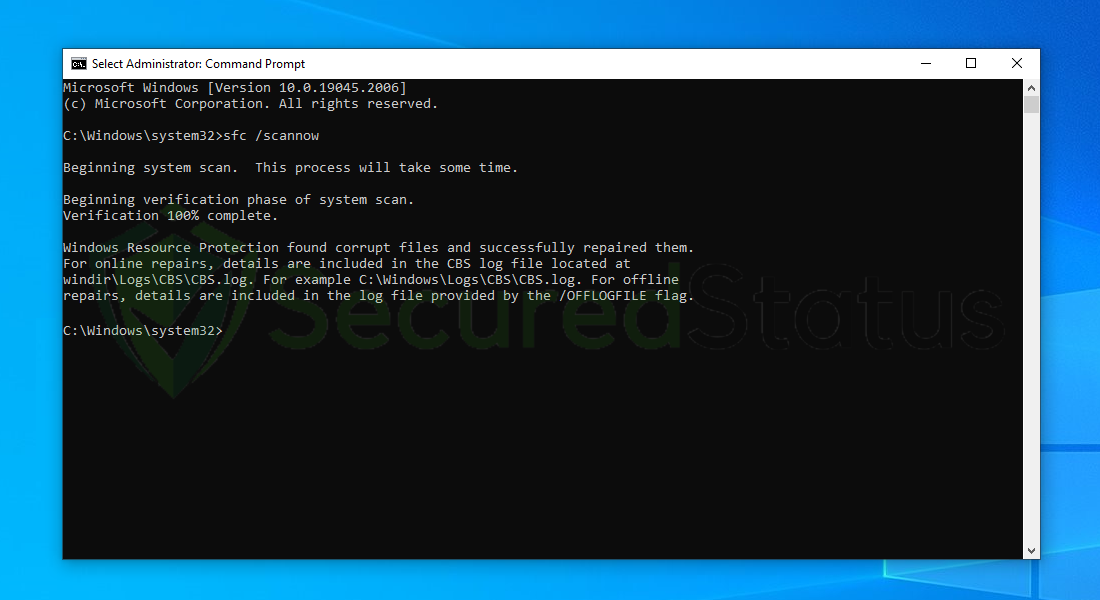
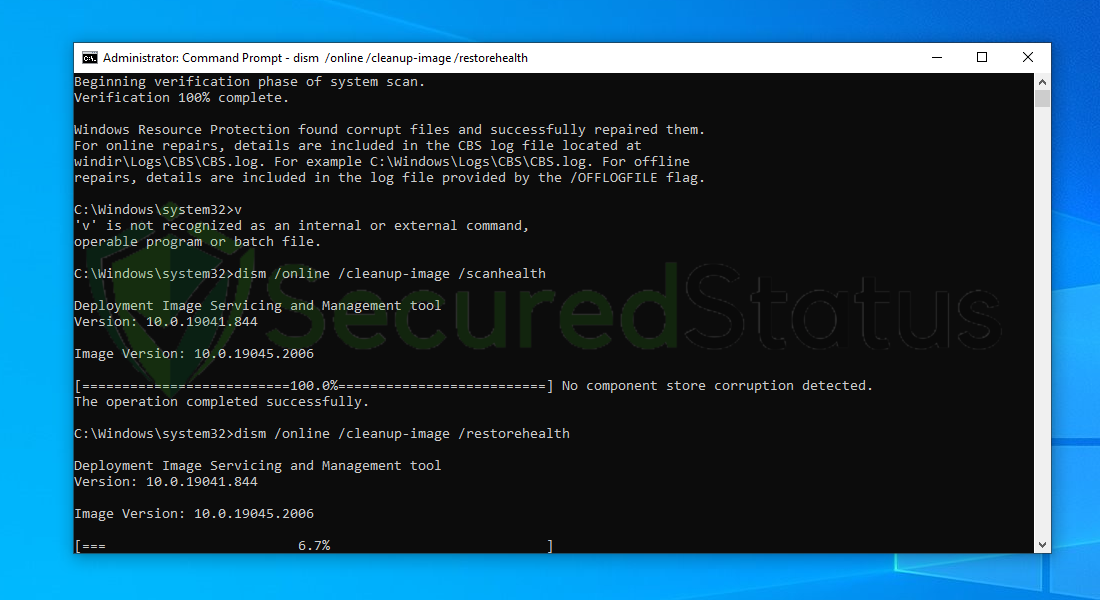
6 Next is to use the DISM Cleanup to patch faulty files in the computer system. Type dism /online /cleanup-image /scanhealth onto the command line and hit enter. Wait for a few minutes while it is scanning.
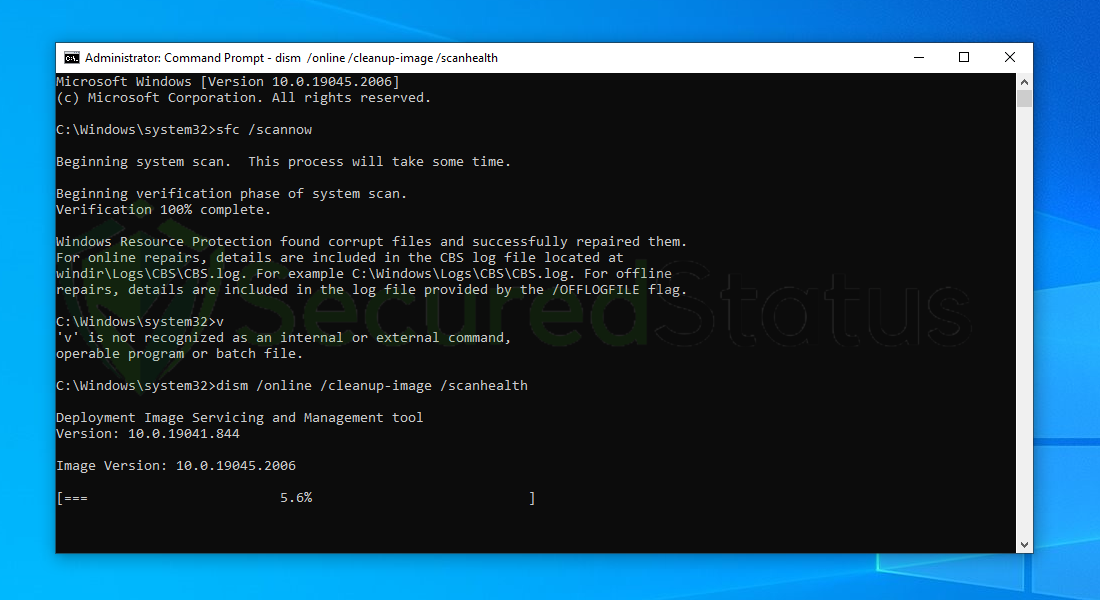
7 After the scan is complete, it will report that the operation is successful and that all corrupted components will be fixed.
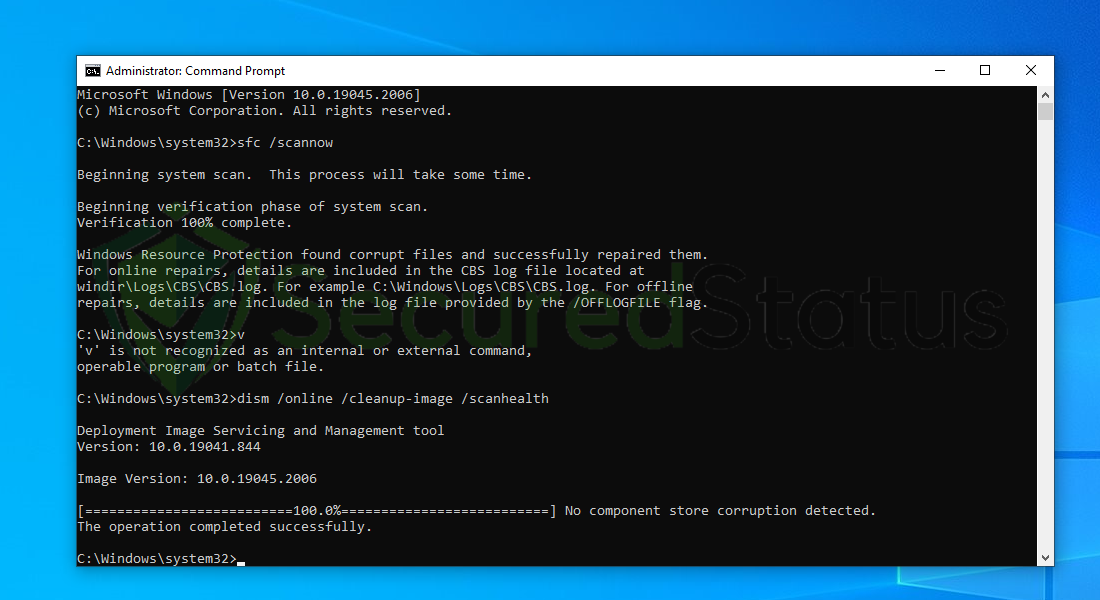
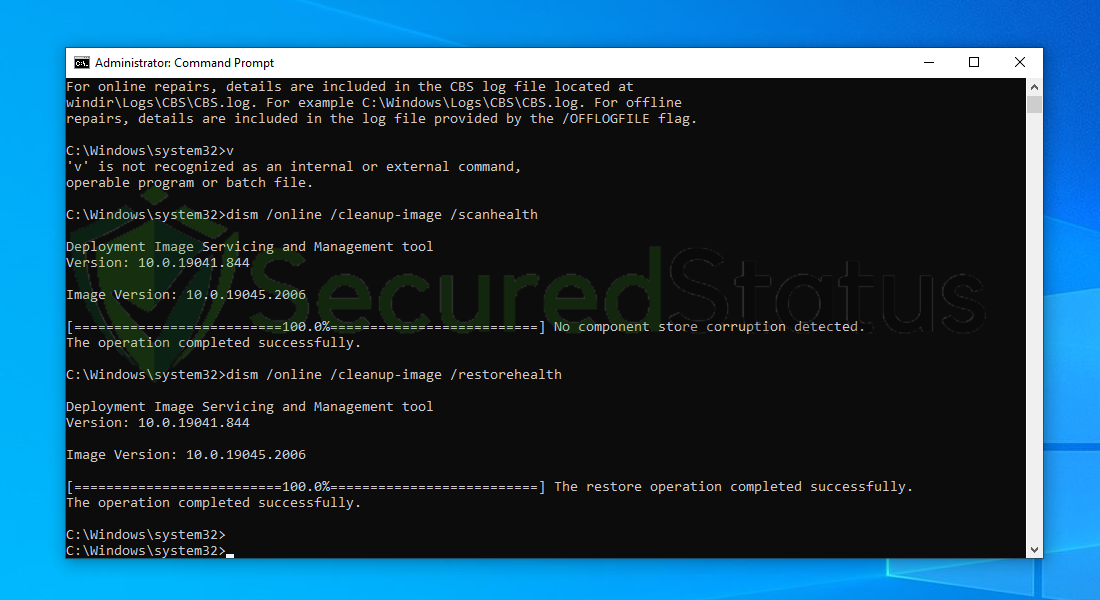
8 Lastly, in order to fix serious windows errors, we will use the restore health command. Type dism /online /cleanup-image /restorehealth and hit enter once again to start the scanning process.
9 Once the scan is complete, it will report that the operation was successful and corrupted files and entries are resolved.
Method 2: Scan for Malware
Most of the time, corrupted system files are caused by malware inside the system. When it comes to removing malware-related problems on the computer, it is best to utilize the anti malware software provided by Malwarebytes.
We have determined that it can remove most types of malicious threats when we conducted malware tests.

Malwarebytes also offers a free 14-day trial when you download it for the first time, so you might want to use the remaining time of the trial to test out the premium features.
1 Click the button above to download the latest version of Malwarebytes Anti-malware.

2 Open the installation file after the download and follow the procedure shown.
3 After following the software setup instructions, wait for the application to finish installing.

4 Once the application is installed, you may now run your first computer scan and wait for it to finish.
5 All discovered malware on the computer will be displayed on the screen, and you can eliminate them by pressing the “quarantine” button.
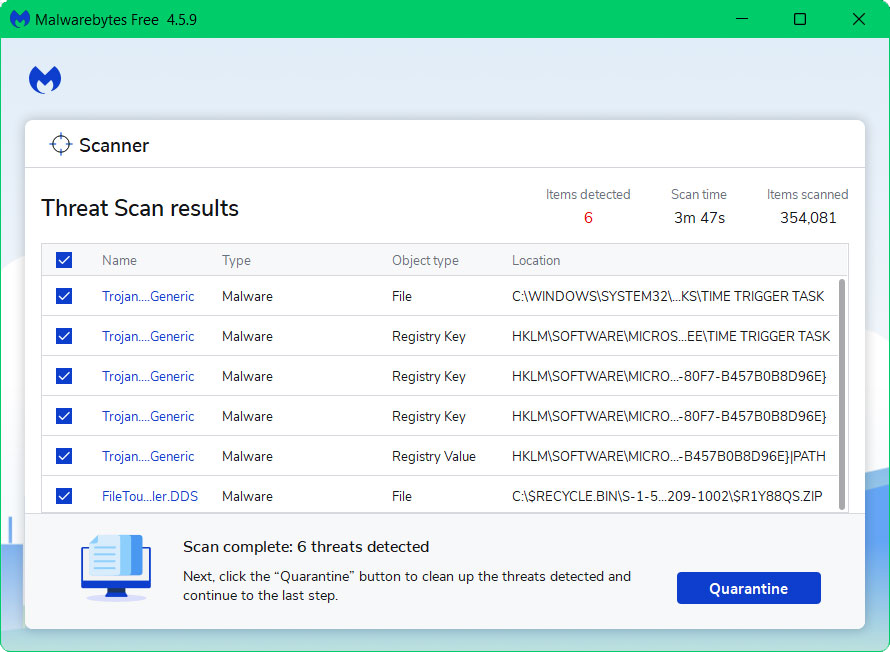
Any potential malware that may have been hiding on your system has now been eliminated, and the modifications it made to the system have been undone. You can check if Task Manager is back to normal after a malware scan.
Alternative: Kaspersky Antivirus
If you visit numerous forums and websites, you will see most users agree that Kaspersky is one of the best antivirus tool available.
There is a chance that malware may still be present in the computer system specially if you have already encountered drive-by download malware.

Since each antivirus application has its own threat database, Kaspersky’s detection technology may be able to find viruses that the prior program missed.
To ensure sure the malware is completely removed from the system, we advise running a scan just in case. If you are downloading the application for the first time, you will also receive a 31-day premium trial.
1 Download the Kaspersky Security Cloud by clicking the button above.

2 Once the setup has finished downloaded, open the file and start the installation.

3 Wait until the wizard finds the latest version of the application or click Skip to install the current version stored.

4 Review the License Agreement. If you agree to its terms, click Continue.

5 Follow the installation instructions as shown then finally click install. (You may choose to uncheck the options shown if you do not want those features.)

6 Wait for the application to finish installing, then after the process is complete, click done.

7 Apply the recommended settings then start the application by clicking apply. Feel free to untick the options you do not desire.

8 You will be prompt to create an account and once you are finished, you will be redirected to the main screen. Select the Scan tab then click the run full scan and wait for it to complete. (Before scanning, we recommend you update the database to ensure any new malware variants are detected.)

9 After the scan has finished, the detected threats will be deleted from the computer.

Method 3: Reset the Computer (Optional)
If none of the two previous approaches were successful, this should be the last resort. Reinstalling Windows will essentially solve the issue because it will return everything to default settings as if the computer were brand new.
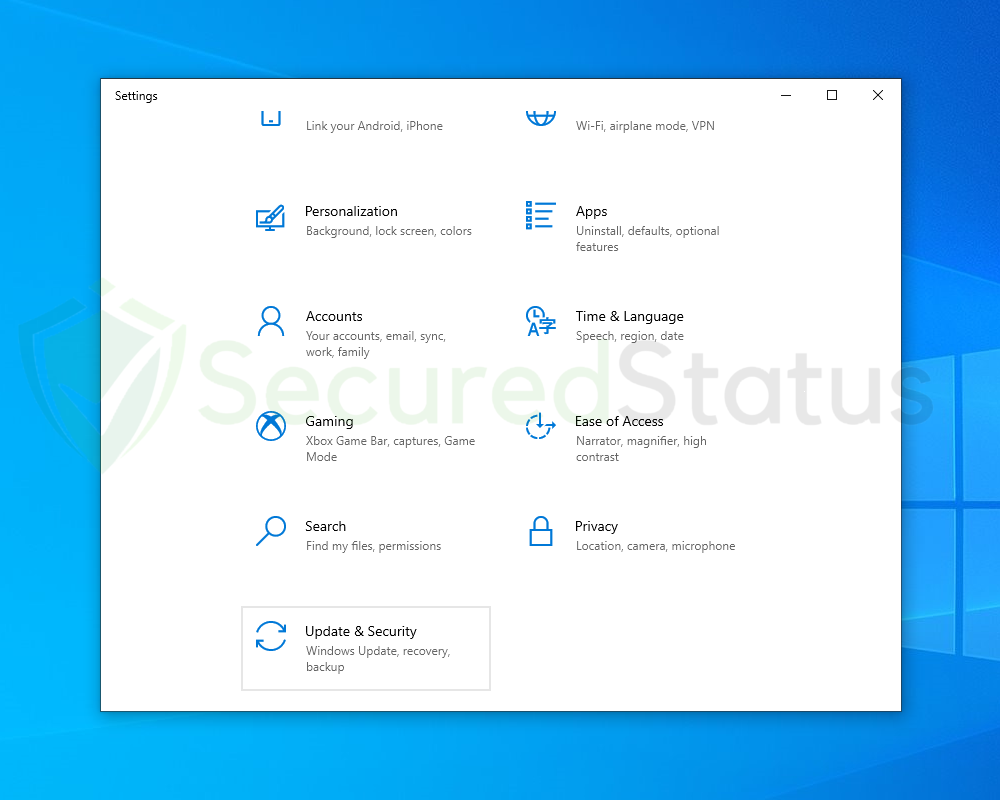
1 Click the Windows Button and select Settings (cog wheel icon) from the left sidebar

2 Once Settings opens up, scroll down and click Update & Security.
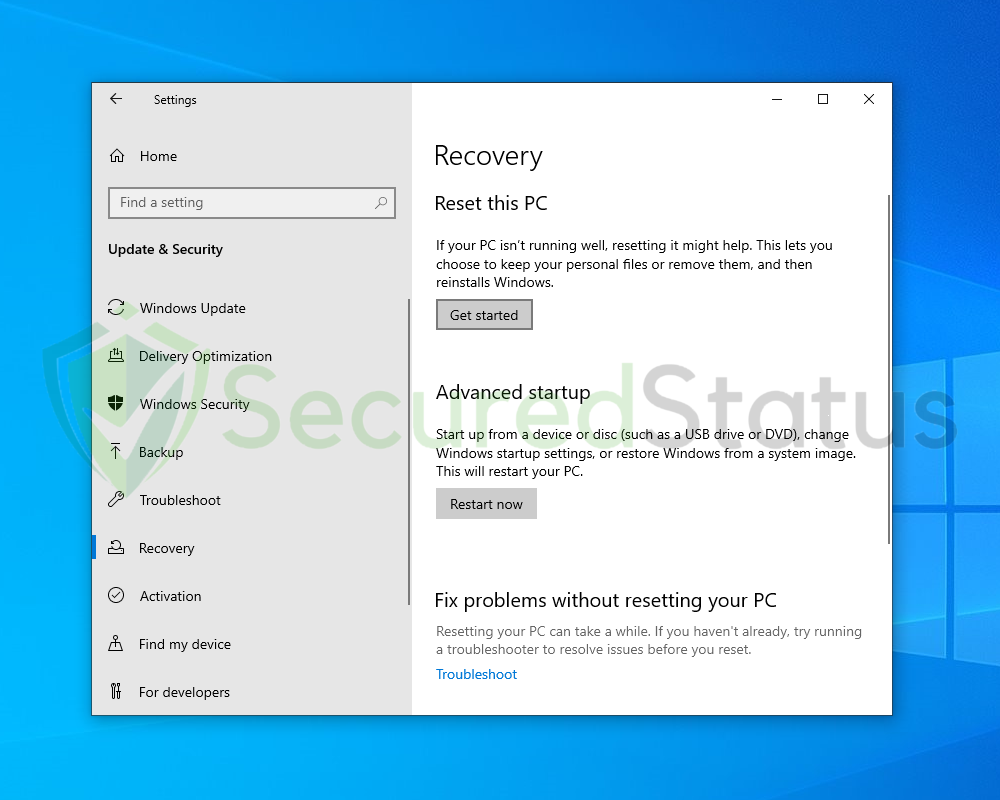
3 Select Recovery from the left sidebar and under Reset this PC, click Get started.
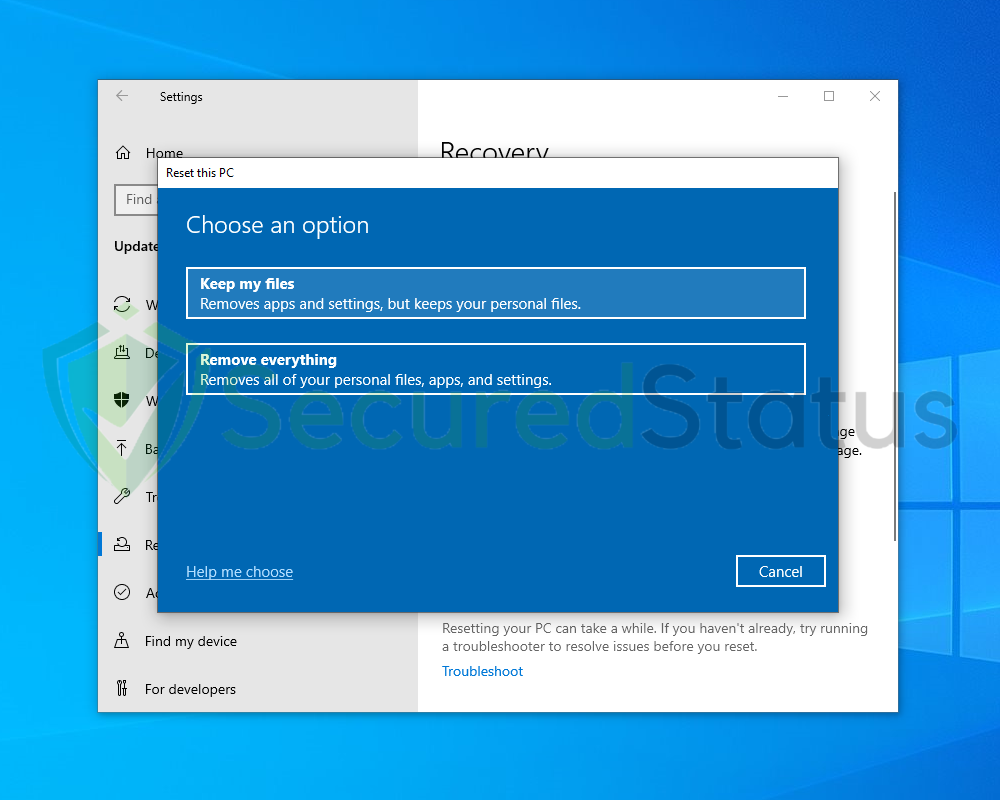
4 You will be presented with two options. Select Keep my files if you wish to retain everything in your computer or choose the later if you would like to reset everything. Follow the instructions and wait until the reset is complete.
Final Thoughts
We hope that this guide has assisted you in resolving your computer’s infected Task Manager. Please forward this article to anyone who is having a similar issue so that it can be fixed. Feel free to contact us if you have any additional questions; we’ll be pleased to assist.
