Many Android users are facing a new issue called “Someone has access to your screen.” This alert suggests that your screen might be shared through a specific app.
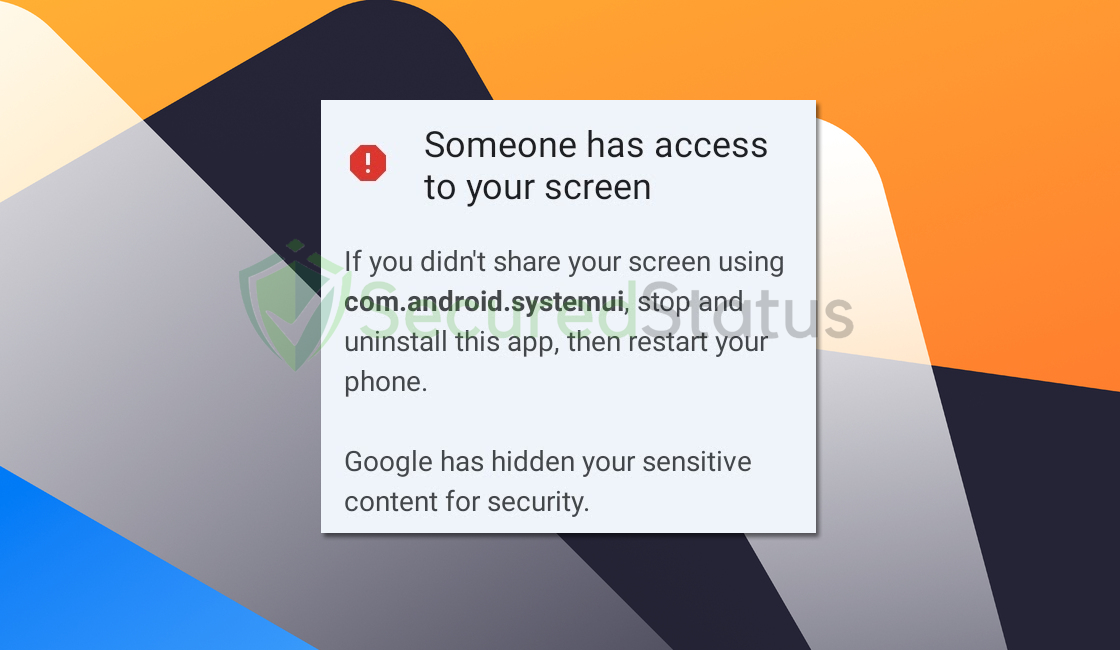
If you haven’t intentionally shared your screen, the alert advises you to immediately stop and uninstall that particular app. However, if you use screen recording or viewing apps intentionally, there’s no cause for concern.
Why does the “Someone has access to your screen” alert appear?
This common problem on Android devices can result from different factors:
Malicious Software Triggering Alerts
Malware may exploit vulnerabilities in the system, leading to unauthorized program launches. The goal of such malware is often data breaches, unauthorized access to sensitive information, or even using the device for larger cyber-attacks.
Users may notice unexpected ‘apps’ appearing without their input, indicating a potential breach that needs quick attention.
Malfunctioning or Corrupted System Processes
The smooth operation of an Android device relies on its system processes. Issues or corruption within these processes can cause unexpected behaviors, like the sudden appearance of an ‘app’ tab.
Failures in system operations may result from software conflicts, lack of updates, or hardware faults. Correcting these system-level faults requires a thorough diagnostic process to restore the device’s stability.
False Positives Within Legitimate Applications
Even trusted apps may behave unpredictably due to errors, unexpected interactions, or code faults. Legitimate apps might be mistakenly flagged for sharing screen access.
Users might be confused by this unintentional activation, which seems to occur without direct user activity. Identifying the app causing this behavior requires a systematic effort to discover the root cause of the app’s functionality.
If you encounter alerts stating “Someone has access to your screen,” please proceed to follow the steps below to resolve the issue.
How to Fix “Someone has access to your screen” Alerts
Following these steps will help you eliminate both the undesired alerts and their source. Be assured that the information provided below has been tested and proven effective.
Step 1: Remove the Application from the Device.
It is preferable to delete all unused, and unidentified apps from the user’s smartphone since the aforementioned application has not yet been located.
1 Go to the Settings application and head over to the application menu. It is the menu wherein installed applications are seen. Since many Android devices are different, there are also different locations for this menu. Note: You can also remove the application from the home screen should you prefer to do so.

2 Scroll down the installed applications and find suspicious ones that you might not recognize or installed.

3 Once you find the suspicious application, click it and uninstall it. For this guide, we are using Smart Cleaner Ultra as an example.

After this step, you may now turn off the Airplane mode since the following steps would require internet connectivity.
Step 2: Scan with Malwarebytes Anti Malware (Optional)
Malwarebytes is a renowned anti-malware tool and it has one of the best threat detection. After removing Chinese Text Alerts from uninstalling the application, it is important to scan the device for potential threats just in case.
Every device should be scanned every once in a while. With this tool, not only Chinese Text Alerts but also other threats that are lurking on the device can also be eliminated.
1 First, go to the Google Play store and install Malwarebytes Anti Malware. If you are using an Apple device, you can simply go to the App Store and download it from there.

2 Once installed, it will ask you for permission to access files. Allow it access to manage the files on the device, it is needed to detect malicious threats

3 Click Run a full scan to detect potential threats on the whole device. Since this may take a while, you can simply close the application and let it run in the background. You can see the progress of the scan through the notifications.

4 After the scan is complete, the detected threats will be shown on the screen and all that is left to do is to eliminate them. Click the Remove Selected to get rid of the threats.

We advise you to run a routine scan of the device to ensure that it is continuously malware-free. We also recommend using Malwarebytes Real-Time Protection, which will secure your machine and detect any threats as soon as they appear.
Tips to be safe online
- It is preferable to avoid websites with unique domain extensions other than .com, .org, .net, and. Because most infected websites have extremely distinct TLDs, always verify the last part of a domain to ensure that you are visiting a safe site, unless the site has been reputable ever since.
- Only visit websites that have a secured connection. A site with an HTTP connection does not encrypt the data it receives and therefore is not considered secure. Entering personal information such as email addresses, phone numbers, and passwords on a website with an HTTP connection is risky since it could be compromised and your information stolen. Websites with HTTPS connections, on the other hand, are secure since data is encrypted and attackers are unlikely to gain access to information exchanged within the site.
- Only download from reliable sources. Everything you download from the internet cannot be guaranteed safe and malware-free. It has been known ever since that one of the main ways malware can get into a device is through cracked downloads and torrents. It is preferable to download only from Google Play and similar verified markets. As wise people say, it is always better to be safe than sorry.
