Dealing with the issue of Windows Defender restricting access to svchost.exe is a vital responsibility due to the fact that this component acts as the backbone for hosting a wide variety of crucial system functions.
Because of its adaptability, it frequently interacts with a wide variety of apps and services, which might occasionally cause security alarms to be triggered.
Although it is extremely uncommon for svchost.exe to be a virus in and of itself, due to its primary location and wide reach within the computer system, it is sometimes a target for malicious entities.
As a result, fixing any problems that are related to its accessibility requires giving the utmost importance to confirming its legitimacy.
The following is an in-depth and step-by-step tutorial that will assist you in resolving the issue:
How to Fix Windows Defender Blocking Svchost.exe
Each method listed below has been tried and tested by our experts because there could be several factors for this problem. If the first one doesn’t work for you, try the next one until the problem is fixed.
Step 1: Verify the Authenticity of Svchost.exe
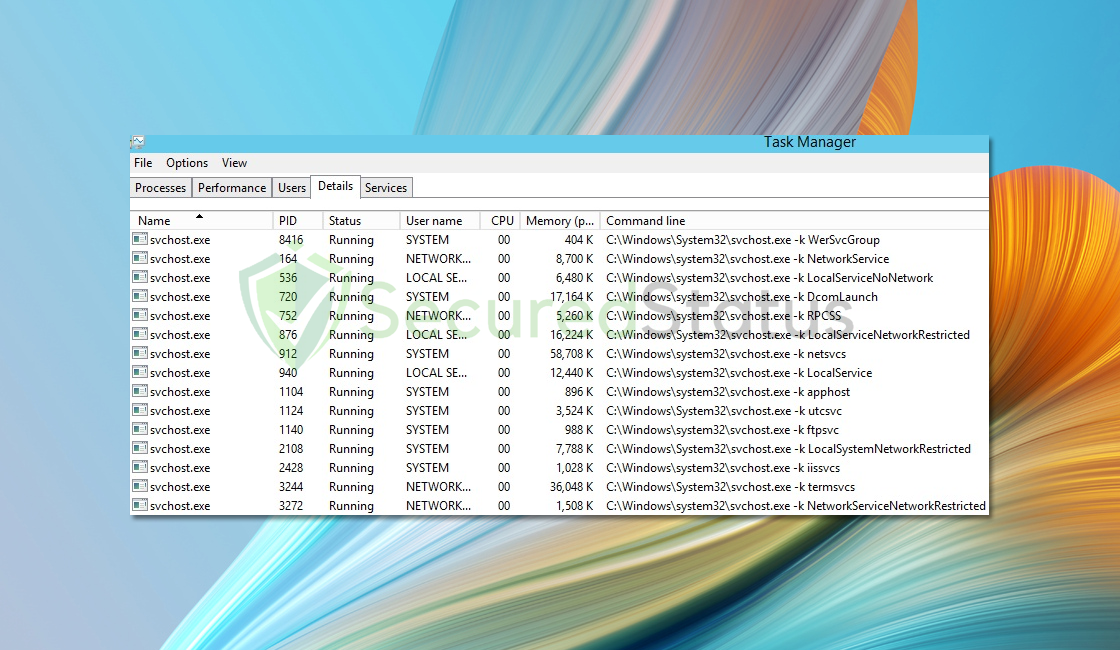
Before moving forward, you need to make sure that the svchost.exe process is legitimate by checking the location of its file. You are able to do this with Task Manager.
1 Press Ctrl + Shift + Esc to open Task Manager. Alternatively, right-click on the taskbar and select Task Manager.
2 In the Processes tab, locate any Service Host processes. These usually appear as svchost.exe.
3 Right-click on any Service Host (svchost.exe) process.
4 From the context menu, select Open File Location.
5 The file explorer will open to the directory where the svchost.exe file is located.
6 Verify if the file is stored in the Windows\System32 folder.
If the file location is within Windows\System32, it’s highly probable that the svchost.exe file is authentic.
Step 2: Consider Scanning With An Antivirus
If there’s still suspicion of a virus and Windows Defender is blocking it, run a scan with a trusted alternative antivirus like Malwarebytes to cross-verify the legitimacy of the Svchost.

Malwarebytes also offers a free 14-day trial when you download it for the first time, so you might want to use the remaining time of the trial to test out the premium features.
Download Malwarebytes
1 Click the button above to download the latest version of Malwarebytes Anti-malware.

2 Open the installation file after the download and follow the procedure shown.
3 After following the software setup instructions, wait for the application to finish installing.

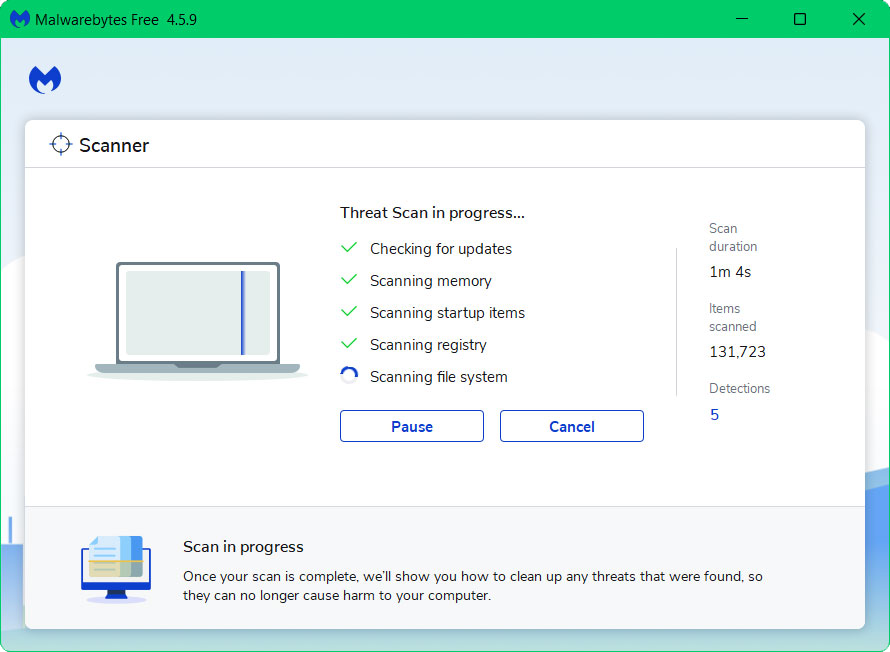
4 Once the application is installed, you may now run your first computer scan and wait for it to finish.
5 All discovered malware on the computer will be displayed on the screen, and you can eliminate them by pressing the “quarantine” button.
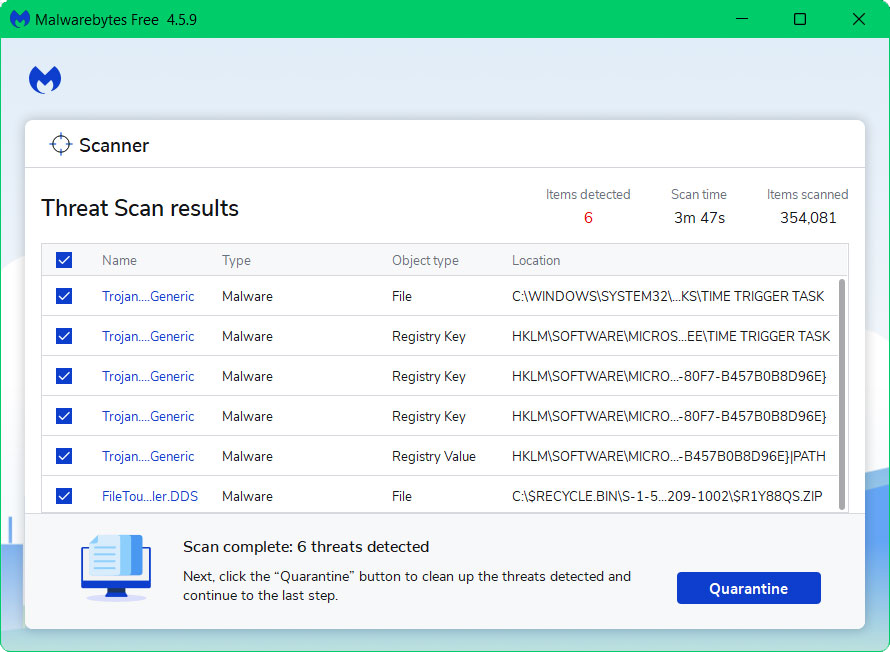
Any potential malware that may have been hiding on your system has now been eliminated, and the modifications it made to the system have been undone.
If the results show no signs of irregularities, it confirms the legitimacy of Svchost.exe, alleviating concerns about potential infections on your computer.
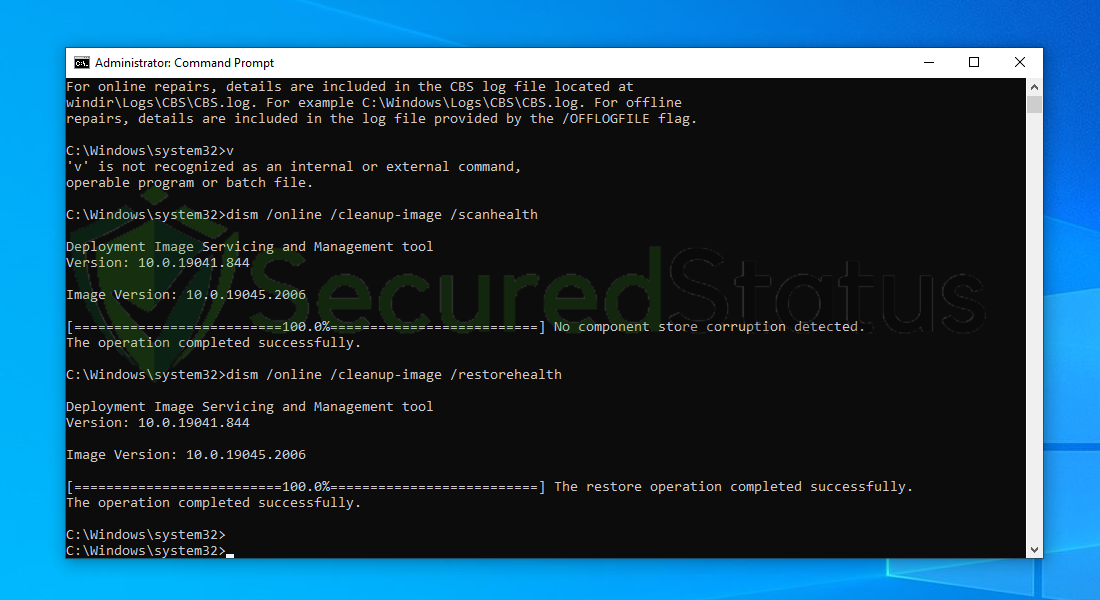
Step 3: Run System File Checker and DISM Cleanup
Utilize the Command Prompt and run ‘sfc /scannow’ to detect and repair any corrupted or malicious svchost.exe files. This could replace them with functional or newer versions.
DISM Cleanup and the command-line tool Windows System file checker can be used to verify the stability of all significant system files. Additionally, it checks to determine whether any system files are missing or corrupted by comparing them to their original versions.
1 Click the Windows Button from the keyboard and search for CMD or Command Prompt.
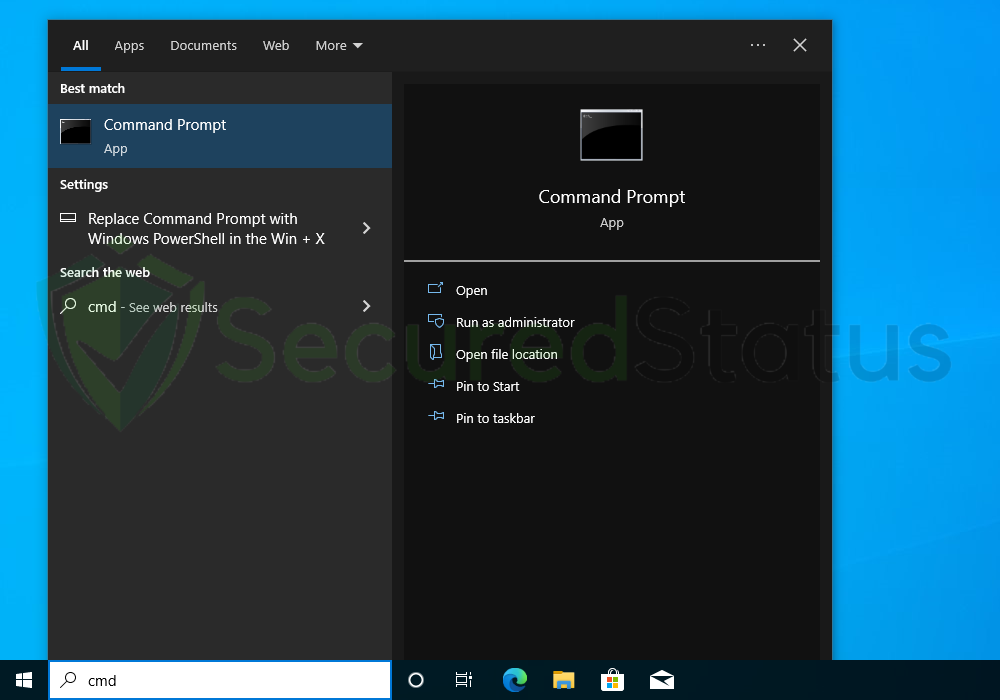
2 Right-click the Command Prompt application and select Run as administrator.
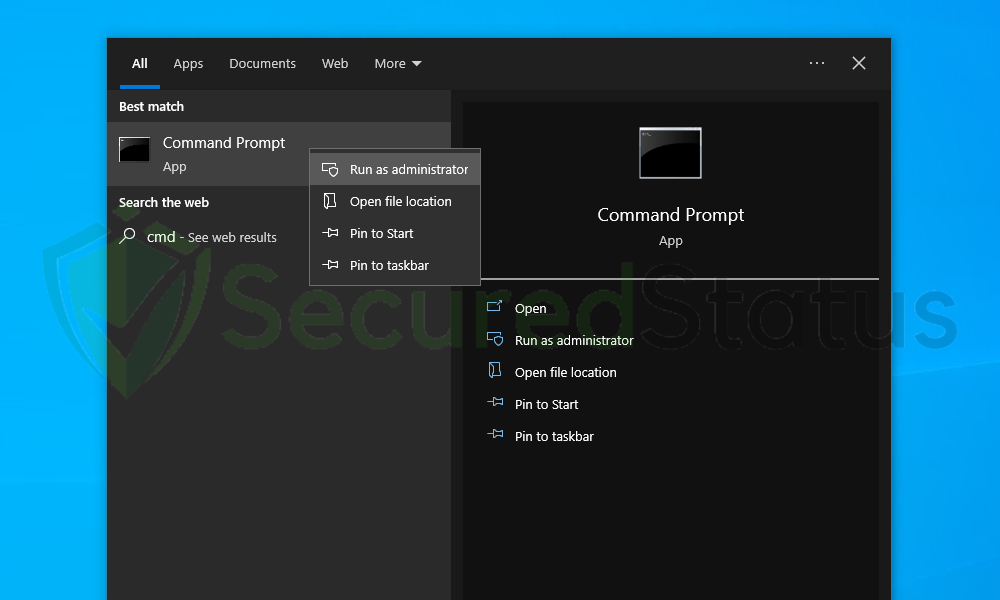
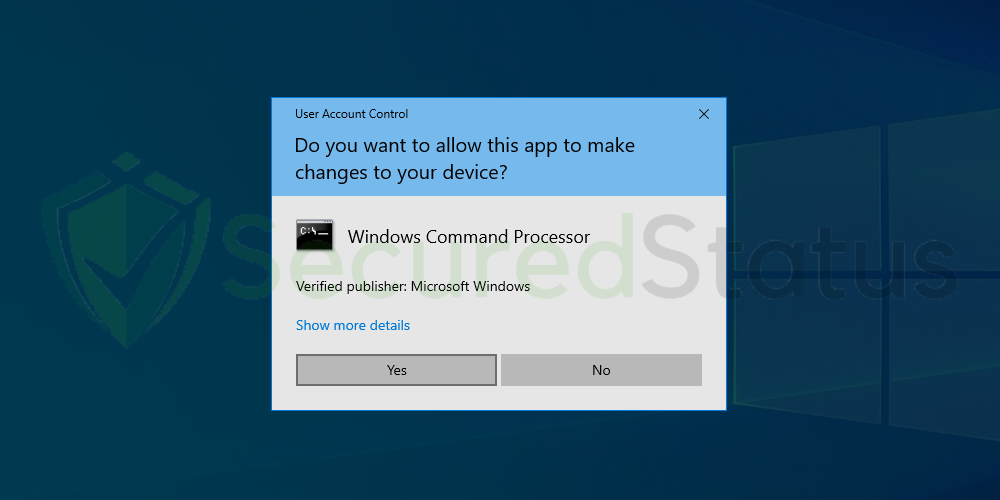
3 The User Account Control confirmation message will pop up, click Yes to proceed.
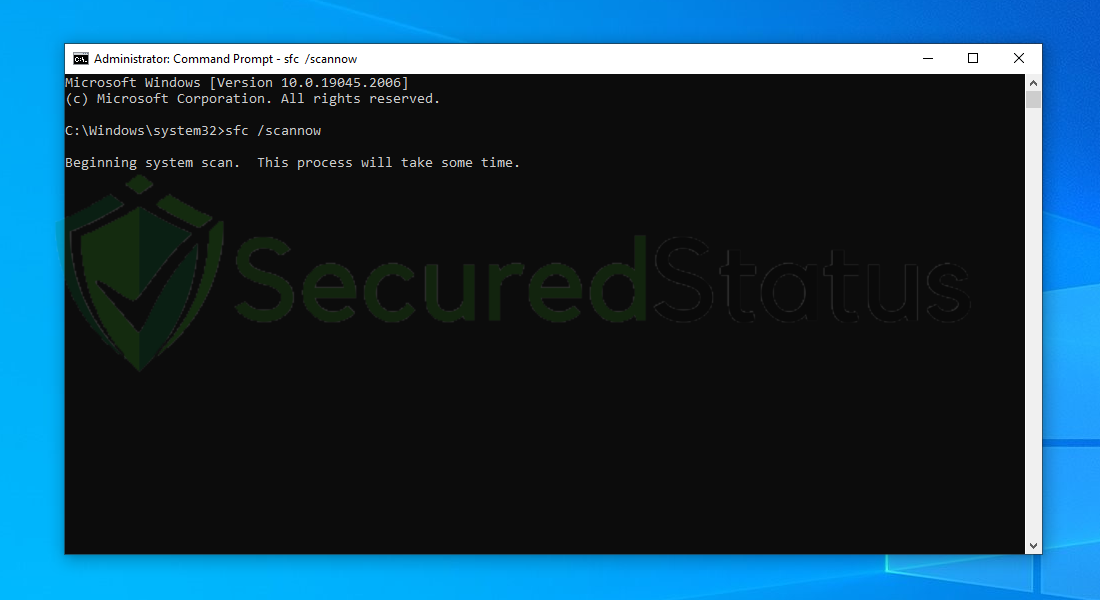
4 Once the Command Prompt opens, type sfc /scannow and hit enter. Please be patient for a few minutes as the scan will start and could take some time.
5 After the scanning process it will report that it has successfully found corrupt files and has repaired them.
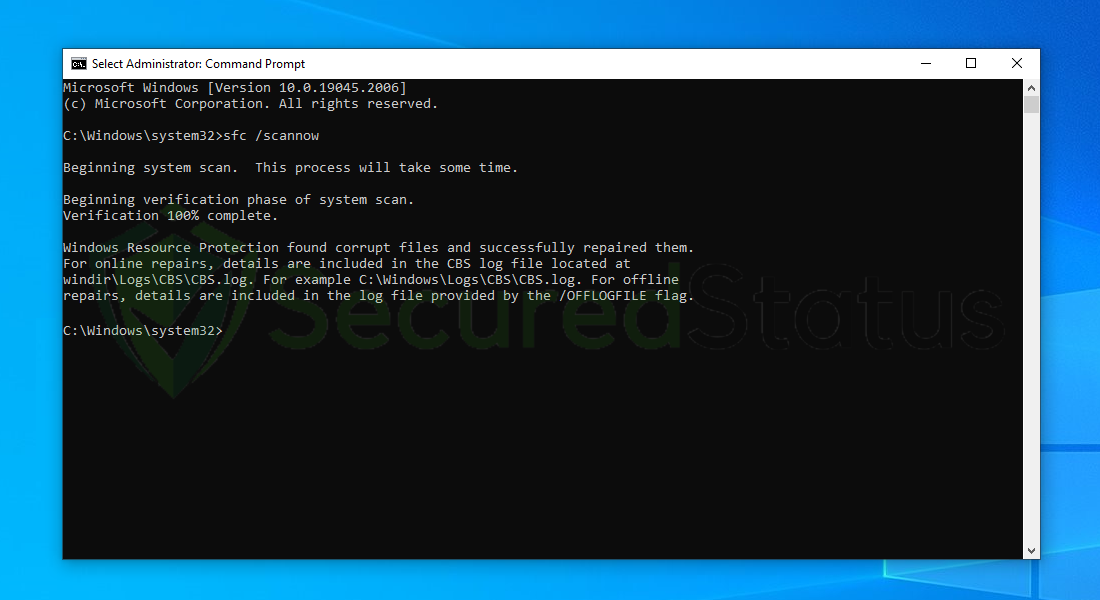
6 Next is to use the DISM Cleanup to patch faulty files in the computer system. Type dism /online /cleanup-image /scanhealth onto the command line and hit enter. Wait for a few minutes while it is scanning.
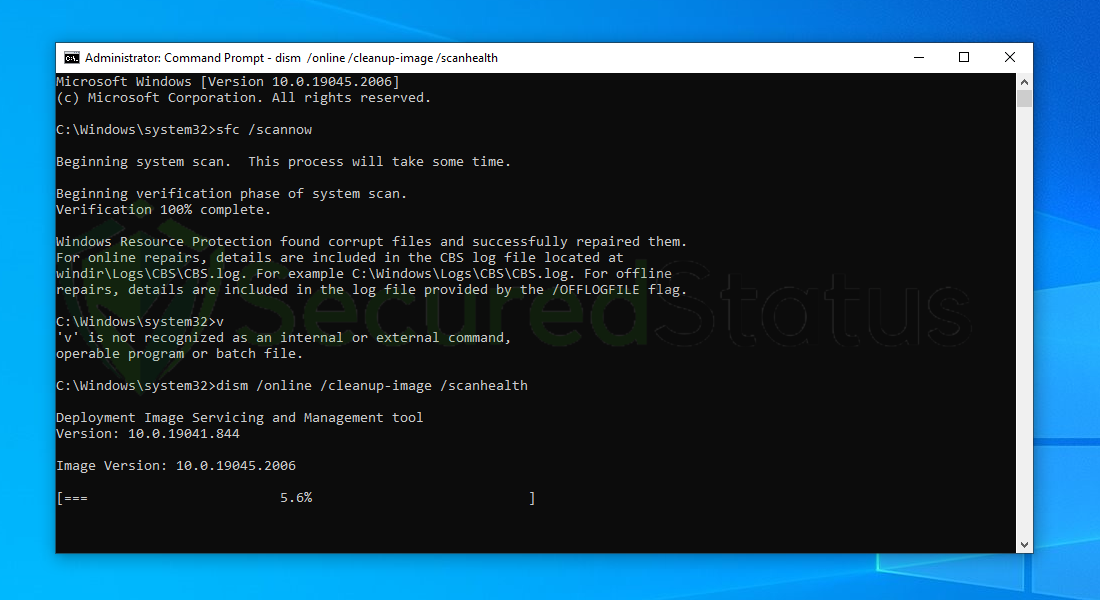
7 After the scan is complete, it will report that the operation is successful and that all corrupted components will be fixed.
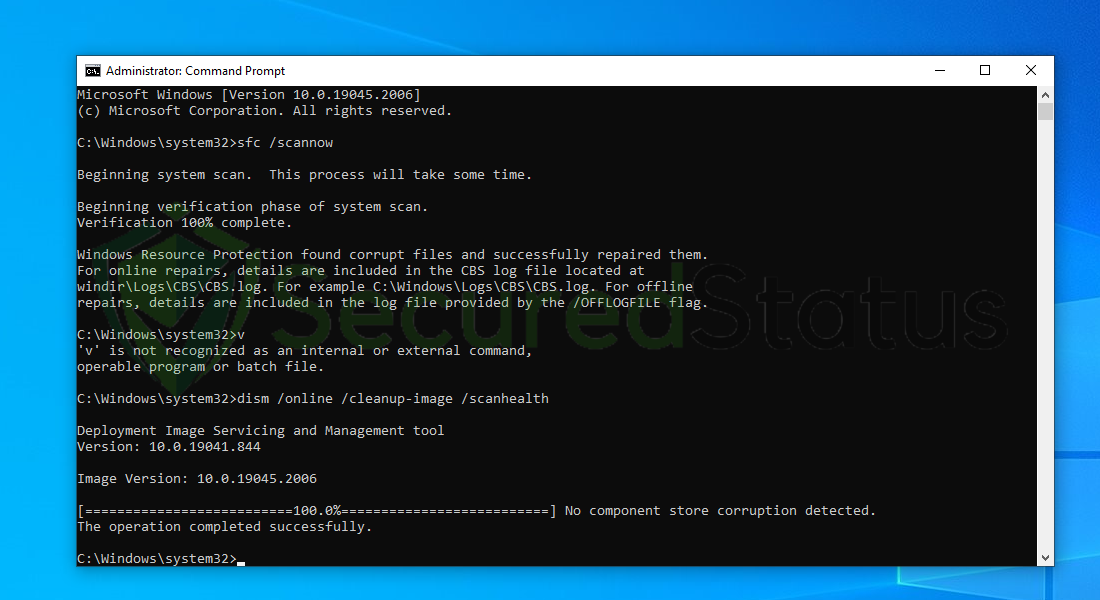
8 Lastly, to fix serious Windows errors, we will use the restore health command. Type dism /online /cleanup-image /restorehealth and hit enter once again to start the scanning process.
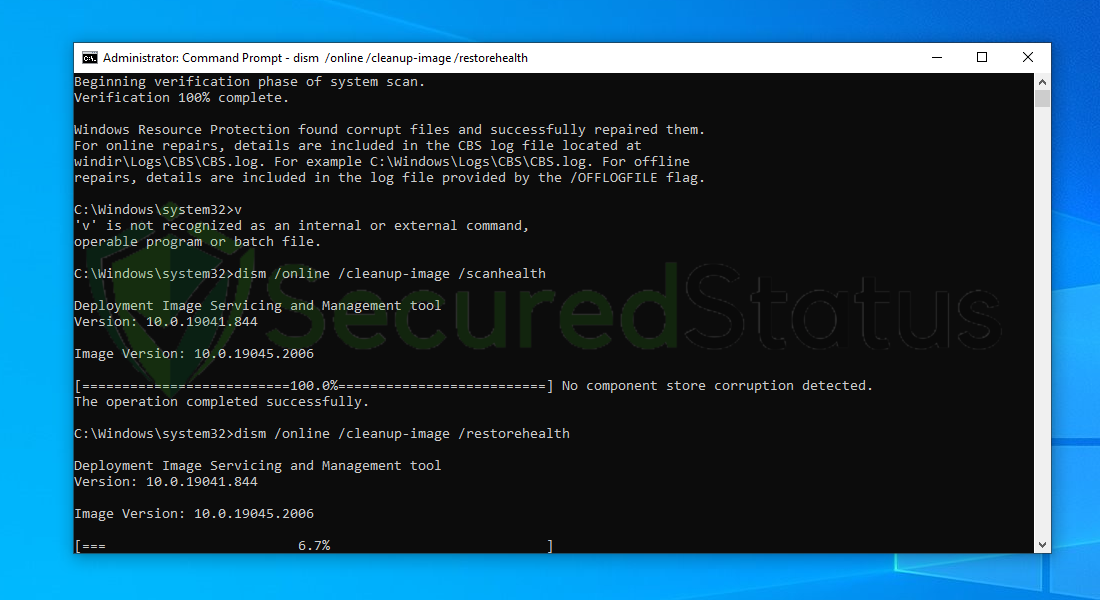
9 Once the scan is complete, it will report that the operation was successful and corrupted files and entries are resolved.
Step 4: Addressing Controlled Folder Access
Controlled Folder Access, a feature within Windows Defender Security, could be triggering the block. This might happen if a service hosted by svchost.exe is not entirely trusted. To address this, please follow the steps below:
1 Navigate to Start and select Settings (the gear-shaped icon).
2 Choose Update & Security and then Windows Security.
3 Within Windows Security, select Antivirus & Threat Protection.
4 Click on Manage Ransomware Protection.
5 Under Ransomware Protection, locate Controlled Folder Access.
6 Choose the option to Manage Controlled Folder Access.
7 Toggle the switch to turn off Controlled Folder Access entirely.
8 To grant specific applications access to protected folders:
- Review the Blocking History to identify blocked access instances.
- Click on the specific blocked access and choose Actions.
- Select Allow on device to grant access to the application.
Note: There is a possibility that disabling Controlled Folder Access will compromise the system’s overall security. Use extreme caution, and make absolutely certain that allowing certain programs access to a folder will not put the security of your system at risk.
Bottom Line
The difficulty encountered when Windows Defender blocks svchost.exe is frequently associated with Controlled Folder Access and the careful approach that it takes towards the protection of folders.
Even while it is of the utmost importance to keep the system safe, there is a possibility of false positives or conflicts with genuine procedures.
















