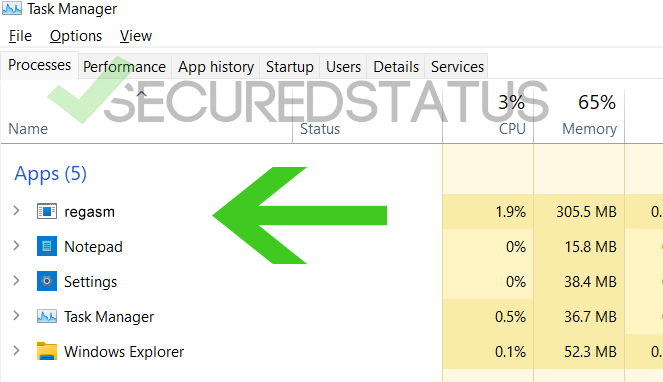
What is Regasm.exe?
Regasm.exe is a malicious application that is disguising as the legitimate .NET utility process. It is often bundled along with malicious loaders and adware and it may bring harm to the computer system so it is better to remove it as soon as possible.
If your computer is acting weird than usual then this application may have gotten inside your system before you know it. Malicious hackers uses a wide range of techniques to implant their dangerous programs inside the victim’s computer.
One of the main ways of getting in to the computer is through software bundling wherein their malicious program is tagged along in a legitimate software like Adobe Photoshop and Microsoft Word. So when the user installs the program, the malware will be injected into the system as well.
Another common way on how malicious files like Regasm.exe is injected into the system is through suspicious email attachments, many people get infected in this type of approach since malware developers use intriguing content to make the user click on the malicious attachment inserted on the email. Once it is clicked, the virus will then spread throughout the computer and the user’s privacy and data will be compromised.
If you are infected by the unknown Regasm.exe, you may experience lag and system overheat every time you use the computer. Windows PowerShell and Command Prompt popping up and closing every few minutes is another indication that the system has a great likely hood of malware infection. Please head over to the next section below and follow the removal guide presented to eliminate threats like Regasm.exe from the computer system.
How to remove Regasm.exe
This procedure will assist you in removing Regasm.exe as well as any dangers related with the threat infection. You can rest assured that the information provided below has been tried and tested.
Step 1: Find and Remove Unwanted Program
Since this type of computer threat takes the appearance of an application, it’s essential to try and locate the malicious program and remove it from the system as soon as possible to avoid further harm.
It’s worth noting that locating the program can be tricky because many adware programs disguise as legitimate programs or system files. In that case, using an antivirus scanner will be of help to detect the threat from the computer and eliminate it. An antivirus guide may be found below for a quick malware removal, but first here are the methods to remove the app manually.
Method 1: Remove Program via Control Panel

- Search Control Panel in the Windows search bar then click it.
- The Control Panel should open, from there click Programs then Programs and Features.
- A list of installed software will show on the screen after a moment.
- Scroll down and find Regasm.exe or any suspicious programs you did not download then right click the application and select Uninstall
Method 2: Utilizing Revo Uninstaller
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a very useful tool for Windows users.
This uninstaller not only removes programs from the computer but it also deletes their changes from the Windows Registry, Host File and etc.
- Using your browser, head over to their official website (click here) and download the latest software that is compatible with your system.

- Open the downloaded file and it should guide you through the setup.
- Follow the installation procedure and wait until the installation of the software is complete.
- After the installation is finished, tick the box that says Launch Revo Uninstaller then click finish.
- Once the software has launched, find the unwanted application that is needed to be removed, double click the program to uninstall.
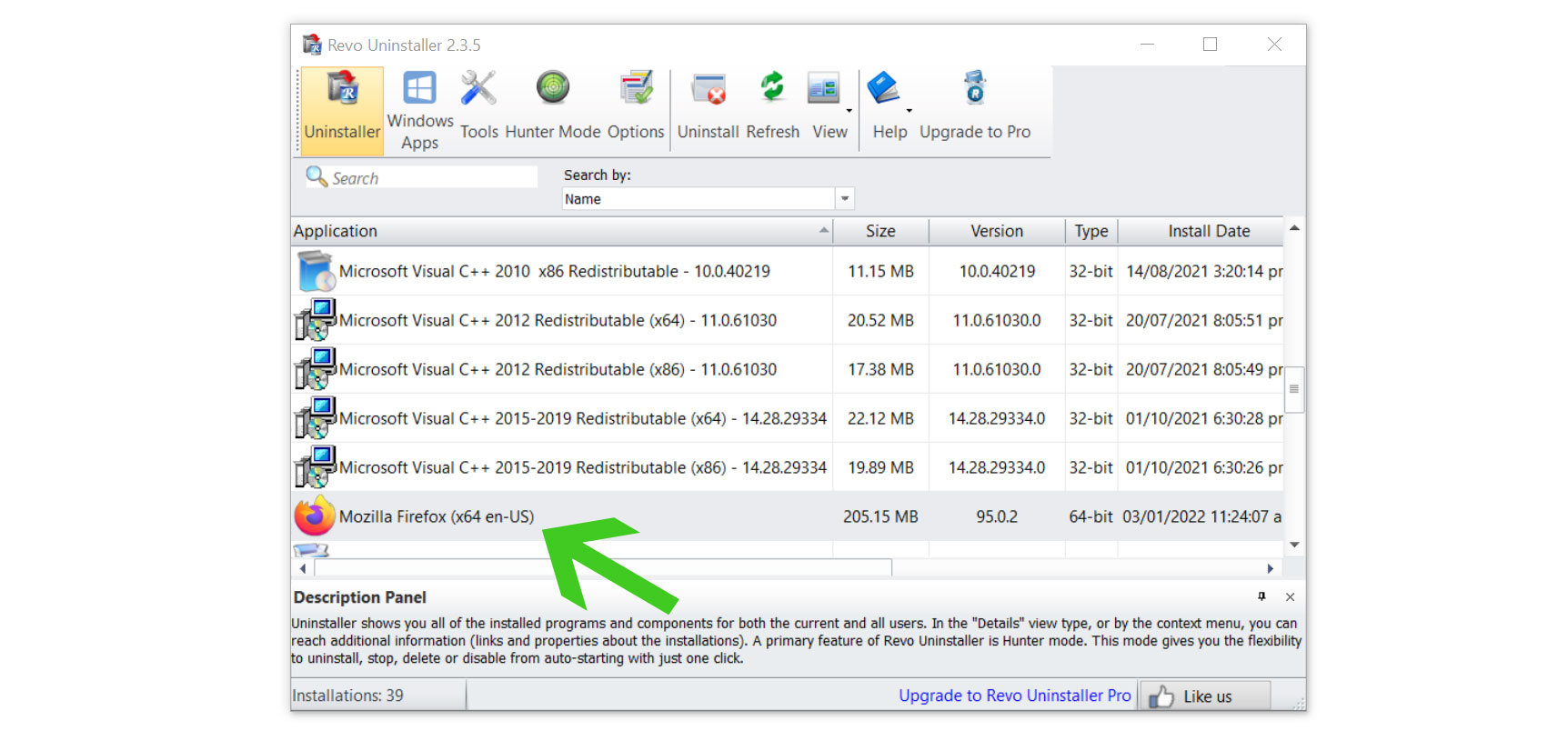
- Click on the Continue button and follow the procedure to start uninstalling the program.
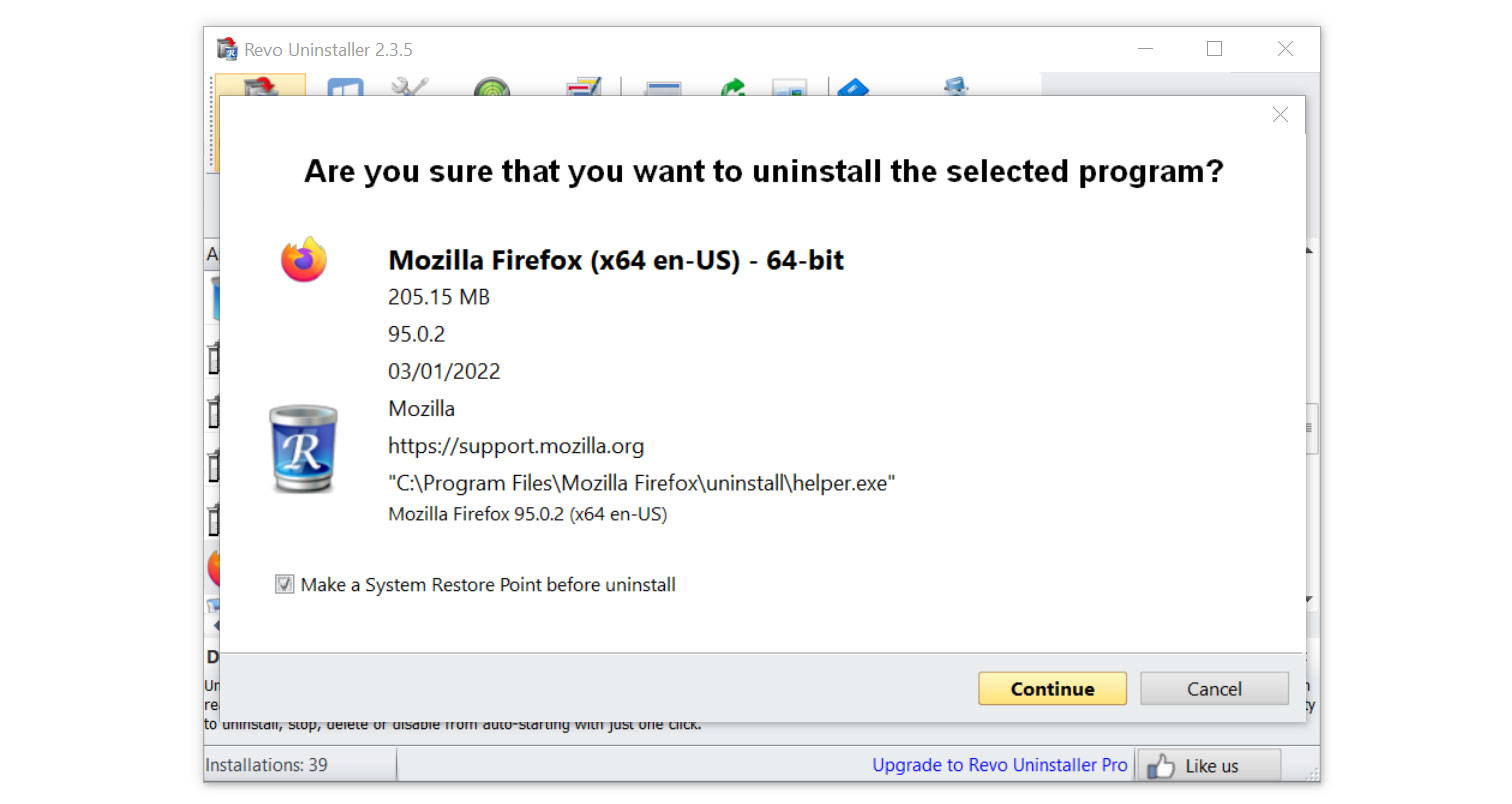
- Once it is uninstalled, a window will pop-up. Select the Advanced option for the scanning mode then click Scan to find remnants of Regasm.exe.
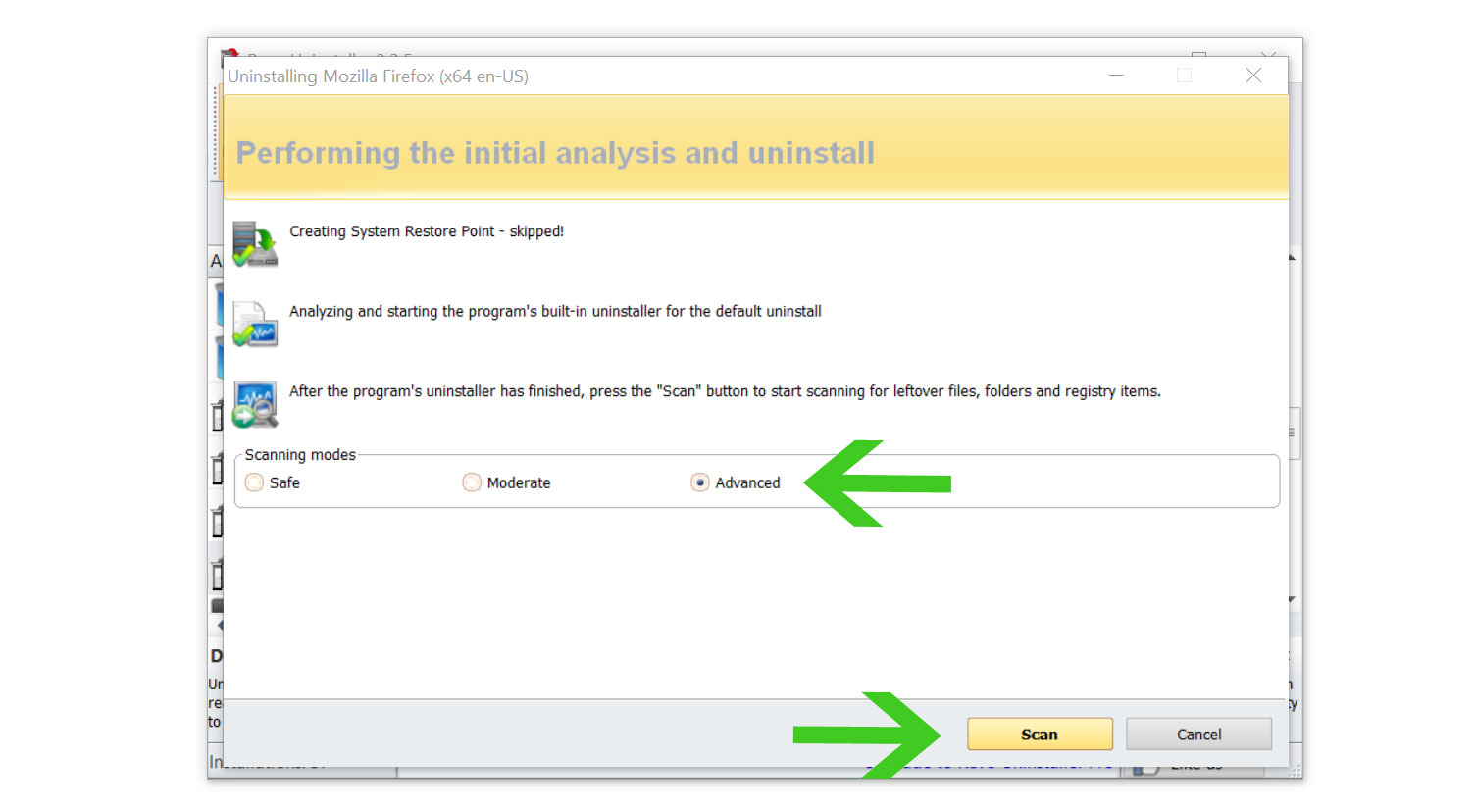
- A window will pop-up and show all of the leftovers and changes made by the program uninstalled a while ago.
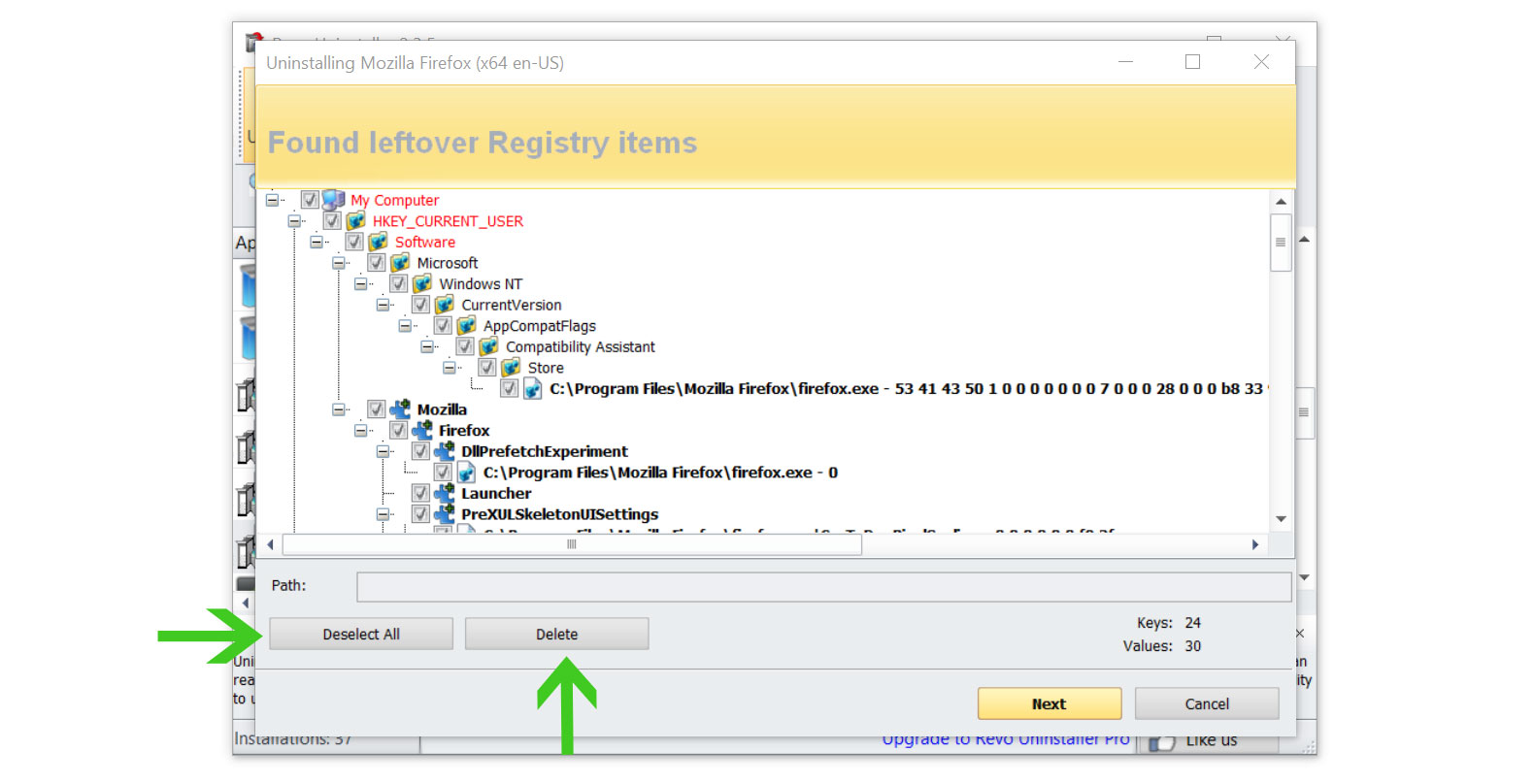
- Click the Select All button and hit Delete to remove the leftovers found on the Windows Registry.
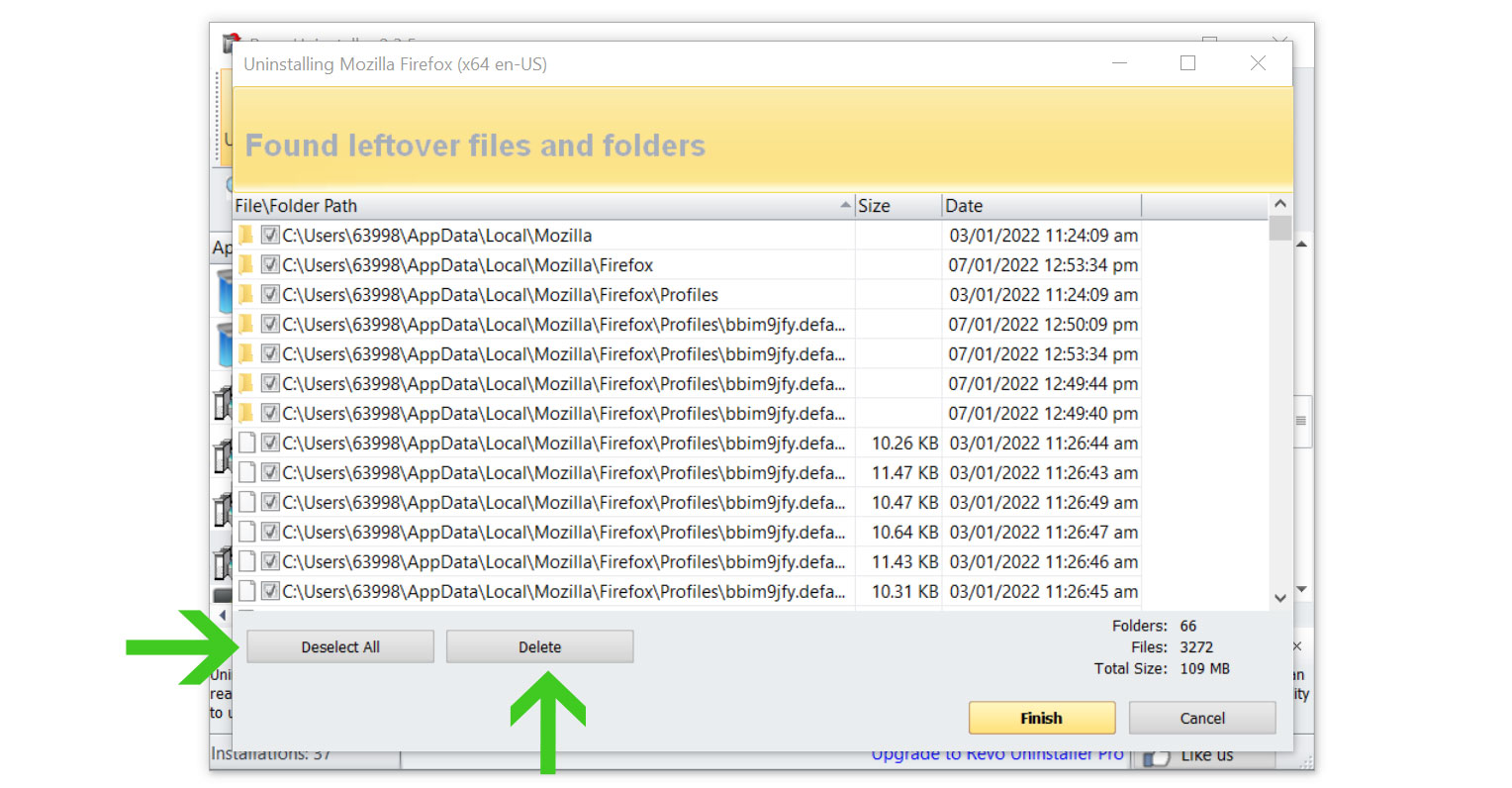
- Some leftover files may be found, click Select All then Delete them as well.
- Once the window closes, you have successfully removed the adware threat from your system.
Step 2: Reset the Browser to Default Settings
Once Regasm.exe has been removed from the system, we need to make sure that the changes it made from the browser should be turned back to normal. Rather than changing the default homepage and permissions manually, it is much easier to reset the browser to it’s default settings.

Google Chrome
- Open Google Chrome and click the three dots in the upper right corner of your screen to access the Google Chrome menu.
- Click the Settings button, then click the Advanced menu on the left side of the screen from the settings screen.
- On the drop down menu, select Reset and Clean up
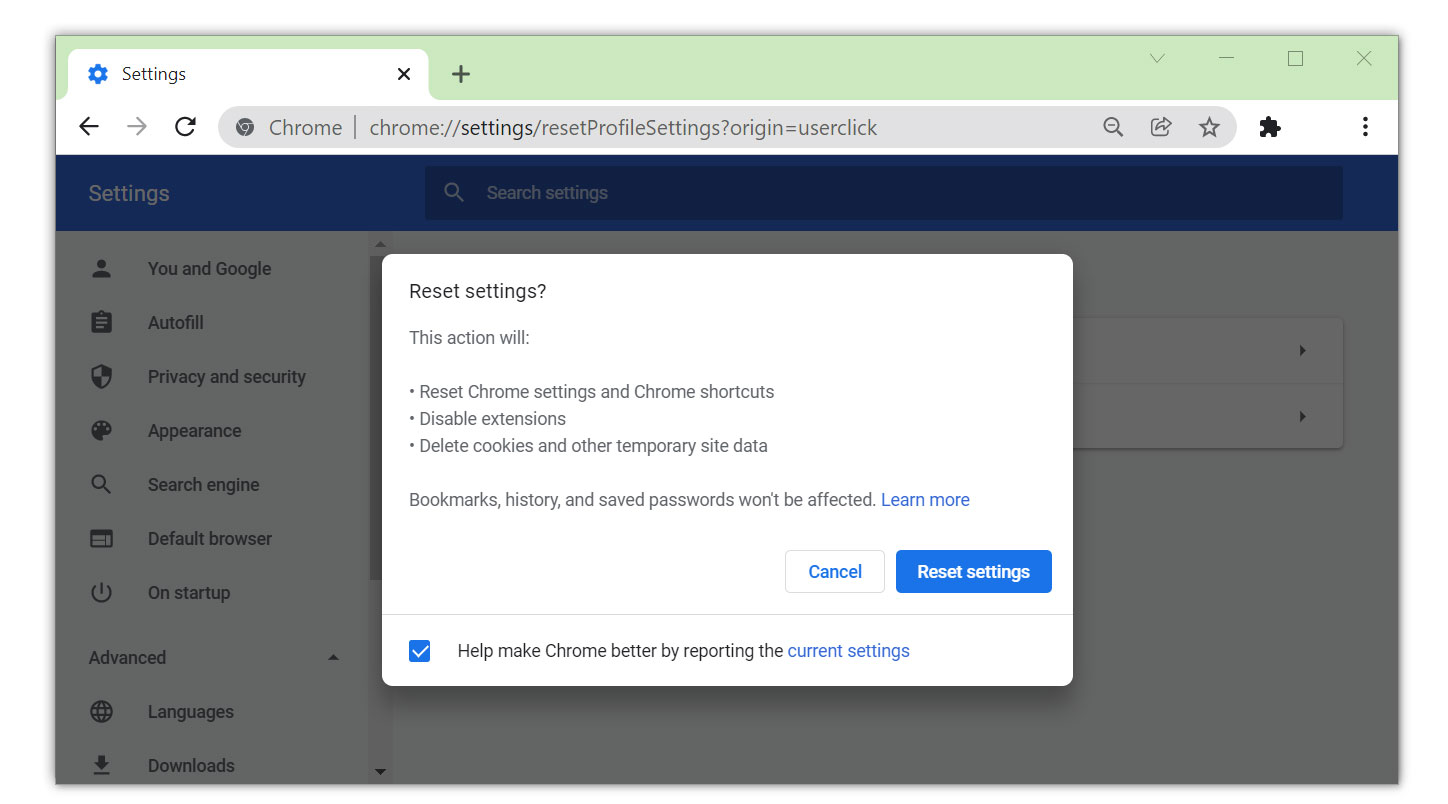
- Click on the Restore settings to their original defaults.
- Then a small window will appear and click the Reset Settings.

Mozilla Firefox
- Launch Mozilla Firefox browser then open the menu by clicking on the three horizontal lines located in the upper right corner.
- Navigate down and click Help then select More Troubleshooting Information from the options given.
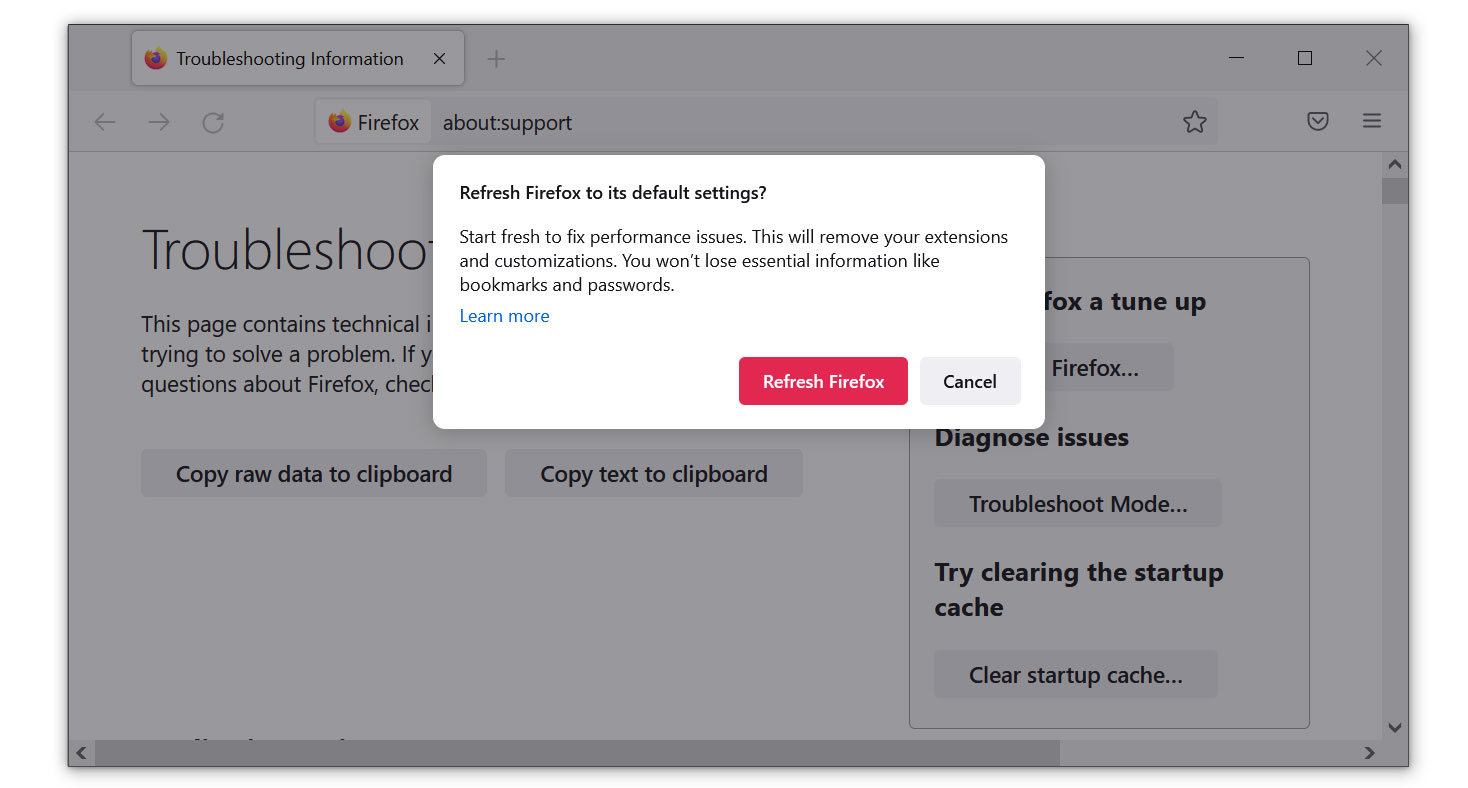
- Select the Refresh Firefox button.
- Click Refresh Firefox on the confirmation window that appeared.

Microsoft Edge
- Run Microsoft Edge on the computer and click three dots icon on the upper right corner.
- Click on the Settings button from the drop down menu.
- Find and click the Reset Settings from the left sidebar.
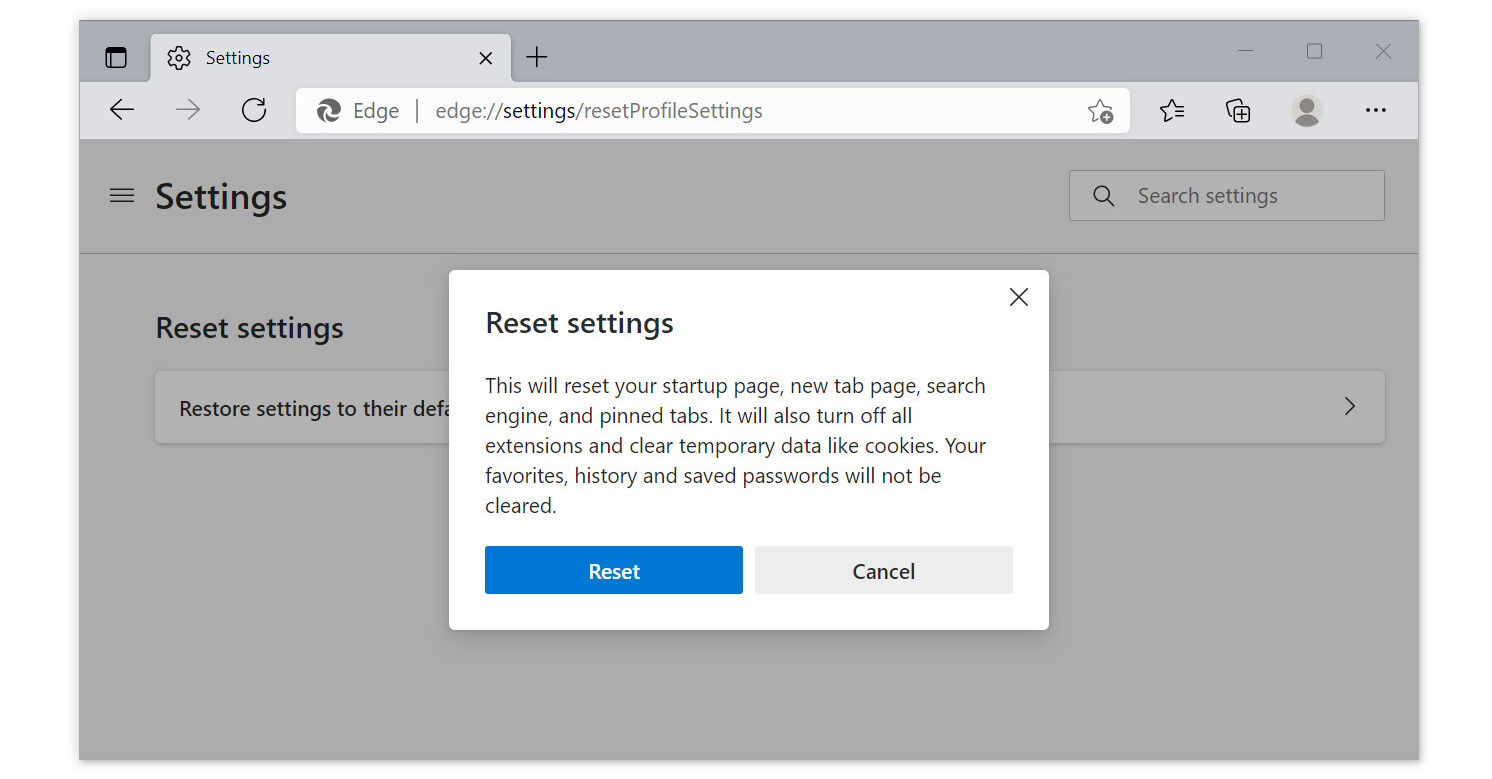
- Then click on the option Restore settings to their default values.
- A warning window will appear that you are about to reset the browser, click Reset and the browser should return to it’s default settings.
Step 3: Use Malwarebytes Anti-Malware
As stated earlier, if you have not found the adware threat in the system, you may utilize a powerful antivirus software. Malwarebytes Anti-Malware is one of the most effective anti-malware programs available.  They have some of the greatest threat detection software, ensuring that any unwanted threats on your computer are totally eliminated. If neither of those methods work, you can utilize this antivirus program to complete the task. Furthermore, even if Regasm.exe is completely removed from the computer, we recommend that you run a complete scan just in case.
They have some of the greatest threat detection software, ensuring that any unwanted threats on your computer are totally eliminated. If neither of those methods work, you can utilize this antivirus program to complete the task. Furthermore, even if Regasm.exe is completely removed from the computer, we recommend that you run a complete scan just in case.
- Using your preferred web browser download Malwarebytes Anti-Malware.
- Visit the antivirus website (click here) and download the most up-to-date version of the software that best suits your requirements.
- Follow the software installation instructions until they are completed.
- Run a complete malware scan on the machine and wait for it to finish.
- All the detected threats found on the computer will be shown on the screen and clicking the “quarantine” button to remove them.
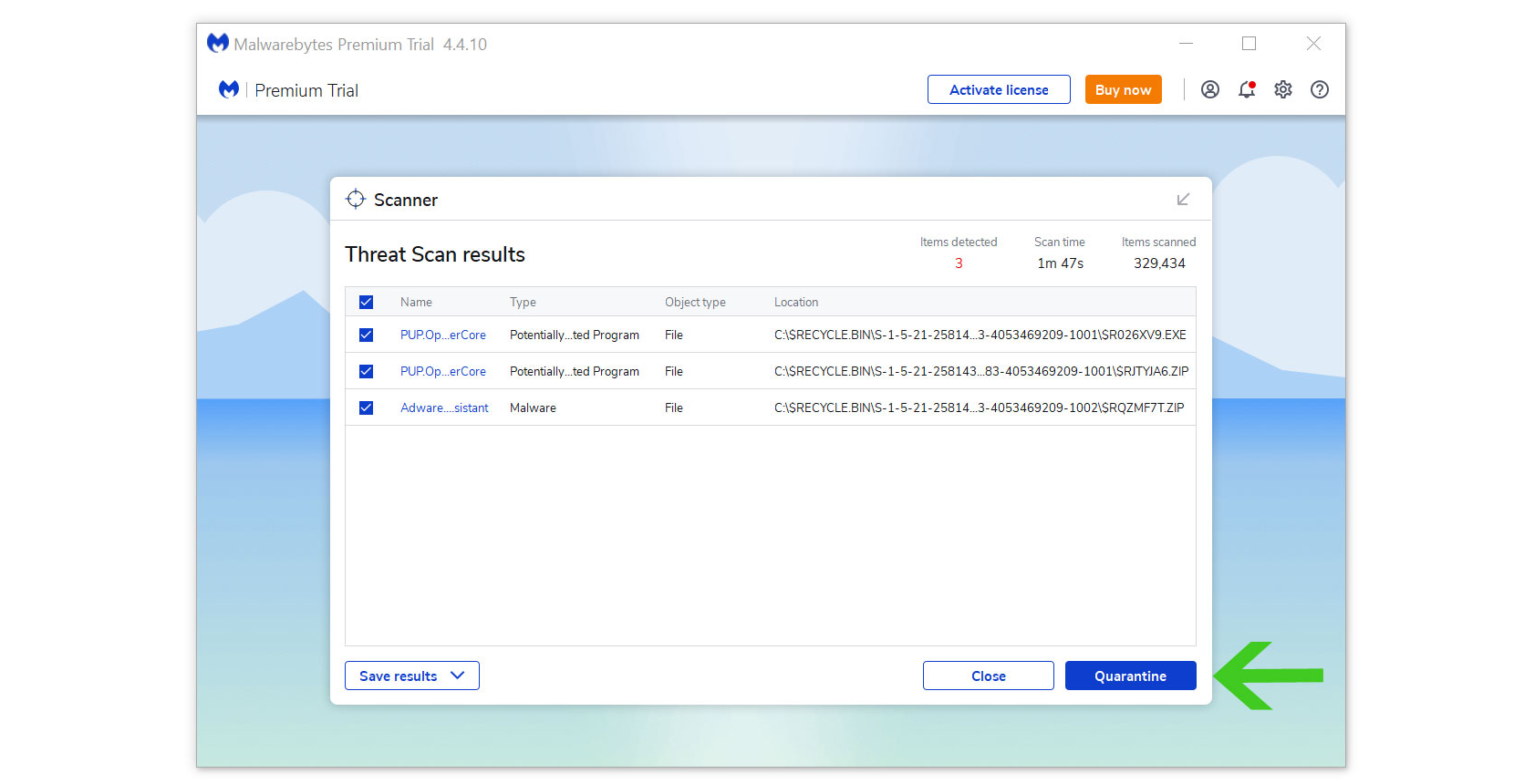
Regasm.exe, as well as any other harmful threats discovered on the computer, should be eliminated once the process is complete. We also recommend to use Malwarebytes Real Time Protection, which will secure your machine and detect any threats as soon as they appear.
Simple tips to be safe online
- Never acquire software or programs from unknown sources, as this is one of the most common ways for adware and other types of malware to attack your computer. Only download from reputable and legitimate websites. To be safe, stay away from torrent downloads and cracked software download sites, as there will always be malware in the files.
- Using a firewall is one of the most foolproof ways to be safe online. It serves as a first line of defense against dangerous websites, shielding visitors from potential risks. It protects the user’s network and device from intruders. A firewall will safeguard a user from the threats hiding on the vast internet in today’s age.
- It is essential to keep anti-virus software up to date on a computer since hundreds of new malware threats are released every day that target the machine’s vulnerabilities in order to infect it. Anti-virus updates include the most recent files required to counter new threats and safeguard your machine.
- Only visit websites that has a secured connection. A site with HTTP connection does not encrypt the data it receives and therefore is not considered secure. Entering personal information such as email addresses, phone numbers, and passwords on a website with an HTTP connection is risky since it could be compromised and your information stolen. Websites with HTTPS connections, on the other hand, are secure since data is encrypted and attackers are unlikely to gain access to information exchanged within the site.
- Backups are critical for ensuring the safety of your data. Without a thorough backup of the data, several computer dangers and irreversible damage can arise. Backing up your data is a crucial step in ensuring the safety of your information. Having a backup copy of the system and data will be extremely useful in the event of a harmful malware attack.
