STOP/DJVU Ransomware – What is it?
The STOP/DJVU ransomware is a malicious family of file-locker viruses that encrypts the user’s files, rendering them worthless.
It was developed to take advantage of vulnerabilities in a user’s computer system and demand ransom money in return for the release and decryption of the encrypted information.
Since many people keep essential documents and files on their computers, those who become infected with the ransomware are compelled to pay the requested ransom to restore access to their vital material.
Being the target of a dangerous virus like STOP/DJVU ransomware is very destructive to a computer system and its network-connected devices. Since it can also move from one pc to another through an internet connection. If an infected device is connected to a network, then the malware could spread through other devices connected to the same network.
Most of the new variants of this unruly file locker virus are impossible to decrypt independently and even some experts are still having difficulties in finding a recovery for these encrypted files which is why most people are resorting to the only option.
To give you a brief understanding of this particular malware, here is a summary of the threat:
| Name | STOP/DJVU |
| Extension | CCYU, CCEO, CCWQ, VVYU, DNET, OOXA, OORI, and 500+ previous versions |
| Classification of Malware | Ransomware, File Locker |
| Malware Group | STOP/DJVU |
| Attacker’s Email | manager@time2mail.ch & supportsys@airmail.cc |
| Ransom Amount | $490 – 980 via Cryptocurrency (Bitcoin) |
| Ransom Note | _readme.txt |
| Symptoms | – A given 4-letter extension will be added to all files on the computer making it useless and unable to open. – Sometimes, additional malware is also deployed into the system such as data stealers and keyloggers to track the user’s session, history, and login information. |
The ransomware usually leaves behind a note (_readme.txt) stating that it demands $490 in Bitcoin for the decryption of the files and the amount will be doubled after 72 hours.
The use of crypto payments is commonly used by malware operators to prevent being tracked by the government. Alongside the note, they will also leave a link for a demonstration of the file decryption and will give you the chance of decrypting 1 sample file for free as proof that their decryption tool is working. (STOP/DJVU ransom note is as shown below)

ATTENTION!
Don’t worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-6Ti2DxXR3I
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
manager@time2mail.chReserve e-mail address to contact us:
supportsys@airmail.ccYour personal ID:
*******************************************************
How does STOP/DJVU Ransomware Lock Your Files And Why?
The malware will begin performing malicious acts on the victim’s computer as soon as it is started. One of the first things it would do is turn off the computer’s antivirus software so it could carry out its operations without having to worry about the security system.
In other words, it will render the system entirely susceptible to any kind of infection, giving online thieves a significant advantage over a PC with even the most minimal defense.
The STOP/DJVU ransomware will also make changes to the computer’s system such as the host file and the registry files. It takes advantage of adding registry entries to Windows system locations so that the malware will persist even after a reset of the computer.
After these actions, the ransomware virus will now scan the computer system for valuable files such as videos and documents.
Some of the files that are typically encrypted are financial documents, business papers, and important family pictures. After scanning the system for files, it will then encrypt the files with a 4-letter extension to make the file useless and unable to be opened.
Online Key to Decrypt STOP/DJVU Locked Files
If your files are infected by the STOP/DJVU Ransomware, whether your files can be decrypted depends on whether you have the online or offline version of the ransomware virus. The offline virus is used by the ransomware when it is unable to connect to its control and command server.
The key given by the offline version may differ from user to user however if enough decryption key is collected, it may also help another victim who is infected with the same particular key.
In comparison to the online key in which decryption may seem impossible due to the very unique key given to each victim, it is worth checking which version of the STOP/DJVU ransomware has infected your device.
To check whether you are infected with the online key or offline key, go to the main Windows directory C: disk and click the SystemID folder.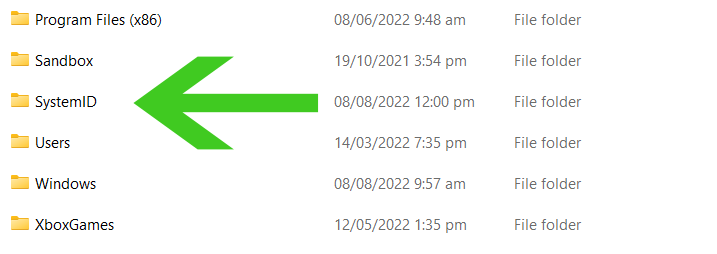 Then once inside the folder, click the PersonalID.txt and check whether the key ends with a t1 since that means you have the offline version of the virus and decryption may be possible.
Then once inside the folder, click the PersonalID.txt and check whether the key ends with a t1 since that means you have the offline version of the virus and decryption may be possible.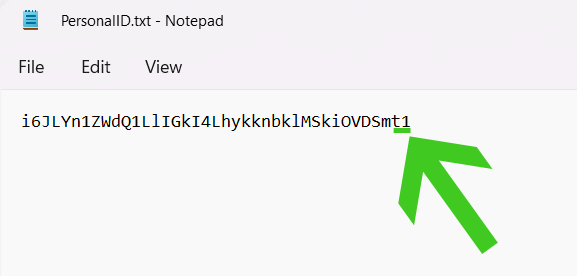
How to Decrypt STOP/DJVU Locked Files
Due to the ongoing emergence of new strains of this ransomware, decrypting STOP/DJVU Ransomware files can be difficult, making it challenging for cybersecurity specialists to design a decryptor.
In addition, the ransomware organization has been releasing updated versions since 2019, each of which encrypts data with a different four-digit letter.
As of right now, the Emsisoft decryption program can only decrypt earlier versions of the virus; subsequent versions will have to wait. Additionally, individuals who have the offline key infected will be able to decrypt their data, however, those who have the online key infected will not be able to do so unless they have a previous backup.
To test if your files are decryptable, follow the instructions below on how to install and use the application:
- Go to the official website (click here) and click the download button on the page to get the program file.

- Click the arrow icon beside the downloaded file then select Show in folder.

- Once the downloads folder shows, right-click the setup file then run as administrator. When the user account control screen pops up, click Yes.

- Read the license agreement’s terms as well as the disclaimer before using the program, then proceed to the next step.

- Once the application starts, select the folder wherein the infected files are stored. Then click decrypt and wait for the program to finish the process.

After the program finishes the decryption process, a message will show whether it has successfully decrypted the files or not. If the program was unsuccessful in decrypting the infected files, refer to the Results tab to know the reason why the decryption was not possible. The following messages as well as what it means are shown below:
- Unable to decrypt a file: It means that decryption is unsuccessful because there are no data about the malware within their servers.
- This ID appears to be an online ID, decryption is impossible: An online ID is a unique key that is impossible and cannot be decrypted by the program and the only way is to pay for the ransomware attacker’s demands.
- This ID appears to be an offline ID. Decryption may be possible in the future: Since it is a new variant of the STOP/DJVU group, a file recovery may be possible in the future once enough keys are fetched that match the one you have. It is important to note that it may take months and even years for a decryption to be possible.
If you cannot wait that long to recover your files, you may resort to using other alternative recovery tools that are available out there.
Alternative Decryption Tools to Use:
These alternative tools can help you recover your files after a ransomware strike. Although some of the tools listed below may be complicated to use, there are a ton of online tutorials that can help. It should be noted that the decryption of STOP/DJVU ransomware files is not guaranteed by the tools listed below.
Shadow Explorer
ShadowExplorer is a file recovery program that allows you to recover prior versions of files that have been altered or overwritten. The application accesses the location in which the documents or files are located and retrieves them from there.
For your information, Windows saves a copy of the files you updated with its restore points, but you won’t be able to access them until you have the feature turned on. Restoring your data with software like ShadowExplorer, on the other hand, can be a lifesaver especially when facing a ransomware virus.
How to Use Shadow Explorer:
- Open the application and select the drive and backup time of the restore point.
- Choose which files and folders to restore.
- Right-click the selected files and choose Export.
- Create or specify where the restored files will be stored after recovery then click ok.
In a matter of seconds, the application will display all of the recovered copies. Whatever sort of file you need to restore, ShadowExplorer will find the overwritten copies in any format. This application is extremely useful since it could simply pull up a backup copy of the infected data and get it back. It would be as if it wasn’t infected at all, as long as there is a shadow copy of the files it could do just that.
PhotoRec
Photo Rec is primarily a photo recovery program. It allows you to recover photographs from a variety of digital devices, including laptops, video cameras, mobile phones, external drives, and more.
The tool can also recover corrupted photos, making it suitable for occasions such as ransomware attacks.
Since corrupted photos can be lost or unrecoverable. PhotoRec comes in handy here. The application is a digital picture recovery utility that allows you to recover photographs and images from a variety of devices, even if they have been corrupted by system or file damage.
How to Use Photorec:
- Run photorec_win.exe after extracting the program folder.
- Choose the disk where the tool is stored then click Enter.
- To scan a disk partition, hover over it and use the keyboard to hit Enter. Repeat this process for each partition on the drive, if there are many.
- Decide on a file system type then hit Enter.
- Search the disk space where the infected files are, and click enter to proceed.
- Create and Name the folder where the decrypted files should be saved.
- Wait till the procedure is over.
- The decrypted files should be saved in the folder you created/specified.
The program is open-source and free. It recovers missing files from a system using text-based data recovery algorithms. However, do note that this application cannot ensure that your infected photos will be completely decrypted.
Internet Safety Tips To Keep Your Device Safe
- Websites with distinctive domain extensions should be avoided. Domain extensions other than .com, .org, .net, and .edu should be avoided because most infected websites have very distinct TLDs, always check the last section of a domain to make sure you’re on a safe site unless it’s been reputable for a long time.
- Never download software or programs from unknown sources. This is one of the most popular ways for adware and other malware to infiltrate your computer. Download only from recognized and legal sources. To be secure, avoid torrent downloads and cracked software download sites, as the files will almost always contain viruses.
- One of the most reliable ways to be safe online is to use a firewall. It protects users from potentially hazardous websites by acting as a first line of protection. It keeps intruders out of the user’s network and device. In today’s world, a firewall will protect a user from the risks that lurk on the huge internet.
- Anti-virus software must be kept up to date. These programs should always be updated on a computer since hundreds of new malware threats are produced every day that aim to infect the machine’s weaknesses. Antivirus updates contain the most recent files needed to combat new threats and protect your computer.
- Visit only websites with a secure connection. Since HTTP connections do not encrypt the data they receive, they are not considered secure. Entering personal information like email addresses, phone numbers, and passwords on a website that uses an HTTP connection is hazardous since your information could be stolen. Websites that use HTTPS connections, on the other hand, are more secure because data is encrypted and attackers are less likely to obtain access to information shared within the site.


