What are pop-up advertisements?
Advertisements are the way for businesses and companies alike to promote their content to the user. It is the new way of promotion in this new digital age of the internet and their way of showing the right advertisement to users has also been growing as well.
One of the most common advertisements methods is by showing pop-ups to users, it is considered legit and common practice, however, cybercriminals tend to take advantage of this to show users unwanted pop-ups from unreliable sources, and not only does it show ads but users are forced to see them as a result of a change in the browser and system configuration.
Browser pop-ups and notifications in details
If you see pop-ups and unwanted notifications stating that your browser is infected and other strange pop-ups that are seen to not be normal, then you may have gotten a malicious pop-up advertisement on your browser’s permission.
This in return will show you non-stop advertisements all around the clock as long as you are using your computer. They utilize the browser’s notification to show the advertisements at the bottom-right corner of the screen as seen from the image below.
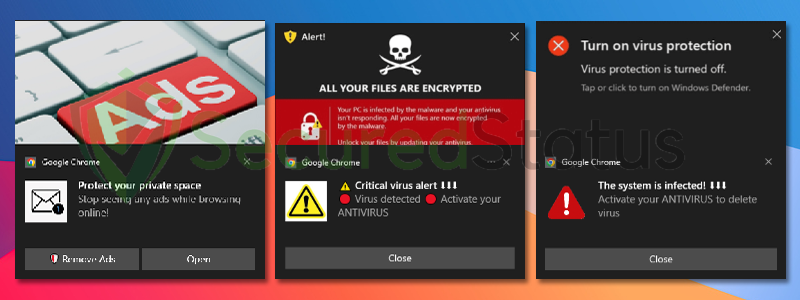
These pop-ups are considered to be unsafe in comparison to the ones promoted by legitimate advertisement platforms since the ones being shown in this case are harmful pop-ups that can cause damage to the user’s computer and data.
That is because clicking on the intriguing ads shown to you will lead to the installation of malware as well as a data breach if you have entered your information on malicious phishing web pages you may have been redirected to.
The initial stage of pop-ups & how they infect users
The way it works is that these pop-ups are frequently seen in suspicious websites such as illegal streaming platforms and cracked software download websites, that is the case because these sites cannot earn money with their site being monetized with legitimate ad platforms so they opt for suspicious ad platforms themselves.
Instead of showing ads to users via their website, clicking on such elements will redirect the browser to the unwanted ads rather than having to see the ads and having the user the option if they want to click the ads or not. This is the case for the video players that when you often click you get redirected to a completely unknown website.
When this happens, the initial pop-up permission requirement page will open and will prompt users to click allow on the notification to begin displaying their unwanted advertisements.
Of course, they would do it in a way to trick users rather than asking for permission in the open since nobody would allow that, so they would show a webpage stating “Click allow to watch the video” or “Click allow if you are not a robot,” which is the case if you are redirected from a malicious software download website.
Here are some of the most common initial web pages that users may encounter when getting redirected from suspicious websites:
Example #1

Example #2

Example #3

After clicking the allow button, the advertisements will then be displayed on the notification bar of the computer. It will look like something that came from the browser, and it will repeatedly show unwanted advertisements filling your computer with ads.
However, advertisements like these are not only acquired via granting the initial webpage access to the notifications, another case for getting the unwanted pop-ups are from installing advertisement-supported software also known as Adware.
This type of software can configure the browser to show such advertisements automatically to users by inputting and placing such websites on the permission automatically without the web user’s consent.
The link between malware and pop-ups
Although these pop-ups can just appear to be annoying at first glance, they can actually lead to the installation of malware on the computer.
This is often known as Malvertising, which is when advertisements are made to promote harmful malware on the computer.
When such pop-ups are clicked, you will be redirected to an unwanted website that can either be a betting website, or a shopping platform, and while there are many more, being redirected to a drive-by download website that will initiate a malware installation is not uncommon.
Pop-ups often show that your computer is infected with malware and users are likely to be triggered to click on such links which invokes panic among the users.
Since the click-through rates of these pop-ups are high, the chance of accidentally stumbling upon a malware download is also high which makes it so that malicious pop-up ads should be removed as soon as possible.
How do cybercriminals utilize malicious pop-ups?
The way this works is that cybercriminals do not own the pop-ups they are showing but instead, they act as a platform or a middleman between the malicious content advertisers to the users.
They get users to allow permission for their maliciously utilized website and in return, they will be paid by the advertisers to display the contents they want directly to the user.
On the other hand, they can also advertise their content should they want to and by doing so, they can install malware to the user’s computer themselves instead of someone else taking advantage of their r0gue advertising method.
Similar to how advertisers receive payment when their ads are clicked on in regular advertising, cybercriminals use this malicious pop-up method with the same process.
However, because the advertising is intrusive and displayed on the user’s computer directly, the click-through rate will be significantly higher and their earnings will exceed those of legitimate ad networks.
Different types of pop-ups on the internet
There are different types of pop-ups and how it affects the computer, however here are the most notable types frequently encountered by users who use the internet.
Newly discovered pop-ups
Our website is committed to providing users with security and ensuring that any malware issues they may have are resolved. Because of this, we are also researching these pop-ups and are always on the hunt for new ones.
| Recently Found Pop-up Ad Domains |
|---|
Users should use caution when visiting the internet to avoid dangerous threats since new malicious pop-up domains are popping up every day.
Webpage alerts & tech support scams
These malicious webpages are particularly made to deceive users into downloading and purchasing unwanted software since these webpages will show that your device may be infected and replicate the exact design of legitimate Windows and antivirus alerts.
They may show warnings such as Critical Virus Alert and that your Antivirus Subscription has expired. By using these alerts, users will be triggered into a state of panic thinking that their device is infected, and will be tricked into buying a certain software to fix this problem.

However, little did they know, the device is completely safe and these warnings are only made by cybercriminals to trick them into doing what they want users to do, which is to pay for the unwanted software.
The same can be said with fake tech support scams, the way they work is that they will also create a webpage that looks similar to system warnings and errors which then they will show a phone number on the screen for users to contact to fix the problem.

Please note that the number shown is a fake one and does not actually redirect to Windows support but instead to the scammers who will take advantage of your computer by asking you for money before fixing the issue which they never do and try to make you download a remote access tool which will let them control your computer remotely.
At the same time, while you are on the page, you will also be prompted to click allow to show notifications which is another feature of the malicious page so that it can show you advertisements alongside tricking you to download specific software and call their fake tech support.
Push notifications and spam ads
Push notifications are the common types of pop-up which is the one that utilizes the computer’s notification screen feature to show advertisements via the browser’s notification permission.
This will look as if the browser is notifying you of something entirely normal however it becomes malicious when it is utilized by cybercriminals to show advertisements.
The notification screen is what you see at the bottom-right corner of the computer screen and it is used by certain applications to show notifications such as there is a new update or something related to the program. While it is used to display notifications, they are not shown multiple times a day and will only show when needed to notify the users.

However, cybercriminals have found a new way to exploit it by showing advertisements via the browser’s notification to the computer. By adding designs and triggering texts to the notifications, users will think that these warnings and pop-ups are true and their chance of clicking it will be high as a result.
These spam advertisements have no limit as to how many times they will appear on the computer, once you click close on one ad, it will eventually open up a new one as fast as you close the other. There is no end to these pop-ups unless you remove them from the browser permission.
Malvertising
Malvertising refers to the practice of infecting users by inserting malicious code into ads and genuine websites, which, when clicked, would download malware. This is risky since it uses vulnerabilities in trusted websites and legitimate ad networks to display their ads.
Therefore, web users who have complete faith in the website they are visiting risk clicking on a dangerous advertisement even though they were never aware it was malware.
Malvertising, on the other hand, promotes malware as a whole and is only intended to infect users with malware in the first place, as opposed to rogue ads and pop-ups that reveal undesired content and may promote malware.
Hackers accomplish this by inserting malware and malicious components on trustworthy websites that may have security holes in their content management systems, such as WordPress, which are known to have been exploited. Infected websites will direct their visitors to malicious websites even if the webmaster is unaware that their site has been compromised.
Stop Unwanted Pop-ups From Chrome, Safari & Edge
The steps provided below will assist you in getting rid of the pop-up ads from the browser as well as any potential malware, trojans, rootkits, and other viruses that may have come with them.
Removing malware from the system and the browser should be thorough and carefully executed; therefore, please follow every step provided.
We optimized the methods below so that less tech-savvy individuals can still remove the browser threat without the need to seek assistance from tech support or a computer expert.
Step 1: Remove pop-up permission from the browser
The majority of the time, pop-up advertisements are brought on by granting an unknown website access to display notifications to the browser.
All you have to do is revoke the permission you granted to the aforementioned website to use the browser notifications to show ads.

Remove Pop-ups from Google Chrome
1. Open the Google Chrome application, then proceed by going to the upper-right corner of the browser window and clicking the three-dot menu button. Once the drop-down opens, select Settings.

2. After the Settings page of the browser has opened, go to the left-side panel and click Privacy and Security from the options available.

3. Once you are on the privacy page, scroll down to the section titled Privacy and Security, then click Site Settings.

4. Scroll down and find the Permissions section of the page. Click on Notifications to see all websites that have notification access in the browser

5. It will then provide a list of sites that are permitted to display notifications under Allowed to send notifications. To remove the site, click the three dots next to the link and then select remove.
 After doing the necessary steps, the browser will now stop showing pop-ups.
After doing the necessary steps, the browser will now stop showing pop-ups.

Remove Pop-ups from Mozilla Firefox
1. Launch the Mozilla Firefox browser, then open the menu by clicking on the three horizontal lines located in the upper-right corner. When the drop-down menu appears, select Settings.

2. After the Settings page has opened in the new tab, hover over Privacy and Security via the left-side panel.

3. Scroll down until you find the Permission section, and click Settings beside Notifications.

4. A window will open alongside websites with permission to show notifications. Remove the pop-ups by selecting the suspicious domain that shows alongside the advertisements and clicking the Remove Website button.

5. There will be an option called Block new requests asking to allow notifications. If you do not wish to allow sites to further ask for notifications, then you may tick the box.
 After making the modifications, click Save Changes. By now, the necessary changes would have been made, and the pop-ups would no longer appear on the browser.
After making the modifications, click Save Changes. By now, the necessary changes would have been made, and the pop-ups would no longer appear on the browser.

Remove Pop-ups from Microsoft Edge
1. Start by launching Microsoft Edge on the computer and clicking the three-dot icon in the upper-right corner. After the drop-down menu has opened, click Settings.
 2. Once the Microsoft Edge settings page has opened in a new tab, select Cookies and Site permissions from the left sidebar.
2. Once the Microsoft Edge settings page has opened in a new tab, select Cookies and Site permissions from the left sidebar.
 3. Scroll down on the Cookies and Data Settings page and select Notifications below the site permission section, as shown.
3. Scroll down on the Cookies and Data Settings page and select Notifications below the site permission section, as shown.

4. Locate the URL that appears with the pop-ups in the Allow area of the Notifications page, then select the three horizontal dots and click Remove.
 After making the necessary changes to the notification permission, pop-ups shouldn’t appear on the browser any longer.
After making the necessary changes to the notification permission, pop-ups shouldn’t appear on the browser any longer.
Step 2: Remove suspicious browser extensions
Now that the pop-ups have been removed, our attention will turn to removing any malware that may have been installed on the computer while the pop-ups were active.
Pop-ups can also lead to the installation of malicious extensions in the browser. Cybercriminals tend to use these extensions to deploy malicious advertisements to unsuspecting users. It may also act as a sort of spyware through which web data can be tracked, such as history, cookies, and saved passwords.
So, to be short, it can lead to browser exploits and data leaks if not prevented and removed as soon as possible. This is why we’ll be investigating the browser extensions that are currently installed on your computer.
If you have a dozen or more plugins installed, it could be challenging to figure out which one is malicious, but there are certain ways and approaches to figure it out.
Malware actors frequently exploit the names of utility programs to mask their dangerous plugins; examples include Volume Booster, YouTube Downloader, Text Reader, and similar names.
More hidden browser spyware will impersonate widely used and reliable plugins like Google Drive. Users won’t suspect the extension because of this trojan-like trait unless they investigate thoroughly and see if it genuinely comes from the same developer.
To know more about which extension should be deleted, we have made a guide stating ways how to find the browser culprit.
Please follow the steps below to remove malicious browser extensions from your web browser and stop the pop-ups, redirects, and other suspicious behaviors that may endanger the user’s data and privacy.
The browser may be controlled by an organization, making it impossible to remove the browser extension when you try to do so. It indicates that the virus has set up a specific configuration to prevent removal. If that’s the case, please use the steps in this article to fix the problem.
Note: The extension used in this step is not malicious and is simply being used as a demonstration of how to get rid of browser extensions.

Google Chrome
1. Open the browser and click on the three horizontal lines at the upper-right corner of the window screen. Once the drop-down menu opens, hover over Extensions and select Manage Extensions on the submenu. On the other hand, you may also type chrome://extensions on the URL bar to directly access the browser extension page. 2. The extensions page will then open in a new tab, showing all installed plugins on the browser. Once you have found it, deactivate the browser extension by toggling the blue switch below its name and description (We will be using AdBlock as an example). After which, you may now click the remove button to get rid of the extension virus from the Chrome browser.
2. The extensions page will then open in a new tab, showing all installed plugins on the browser. Once you have found it, deactivate the browser extension by toggling the blue switch below its name and description (We will be using AdBlock as an example). After which, you may now click the remove button to get rid of the extension virus from the Chrome browser. 3. If the switch is disabled, then you will need to remove it directly from the extensions folder of the browser. To do this, first, you have to select the plugin and look at its ID as shown in the URL bar. (See the image below for an example.)
3. If the switch is disabled, then you will need to remove it directly from the extensions folder of the browser. To do this, first, you have to select the plugin and look at its ID as shown in the URL bar. (See the image below for an example.) 4. Open File Explorer and go to the folder where Chrome stores the browser extension you have downloaded and installed. The default location would be at:
4. Open File Explorer and go to the folder where Chrome stores the browser extension you have downloaded and installed. The default location would be at:
C:\Users\YOUR NAME\AppData\Local\Google\Chrome\User Data\Default\Extensions
 5. You will see a list of folders, each with different hashes. Find the folder matching the ID of the malicious extension, then right-click and delete it. Make sure the browser is closed before proceeding to delete the folder.
5. You will see a list of folders, each with different hashes. Find the folder matching the ID of the malicious extension, then right-click and delete it. Make sure the browser is closed before proceeding to delete the folder.
 The next time you open the Google Chrome browser, you will see that the extension has been removed.
The next time you open the Google Chrome browser, you will see that the extension has been removed.

Mozilla Firefox
1. Launch the Firefox browser and open the menu by clicking the three horizontal lines, which can be located in the upper-right corner of the program. Once the drop-down menu opens, click on Add-ons and Themes. On the other hand, you may also type about:addons on the browser URL bar to enter the Add-ons Manager. 2. From the left-side menu, go to the Extensions page and view all of your browser extensions installed on Firefox. Toggle the blue switch to deactivate the plugin, then click the three horizontal dots beside the toggle and select Remove to get rid of it from the browser (We will be using Adblock Plus as an example).
2. From the left-side menu, go to the Extensions page and view all of your browser extensions installed on Firefox. Toggle the blue switch to deactivate the plugin, then click the three horizontal dots beside the toggle and select Remove to get rid of it from the browser (We will be using Adblock Plus as an example). 3. If the toggle is locked or unable to be removed, then you will have to manually remove the extension from the browser’s extension file directory. Open File Explorer and go to the following directory where Mozilla Firefox keeps its browser extensions; this will be located:
3. If the toggle is locked or unable to be removed, then you will have to manually remove the extension from the browser’s extension file directory. Open File Explorer and go to the following directory where Mozilla Firefox keeps its browser extensions; this will be located:
C:\Users\Your Username\AppData\Roaming\Mozilla\Firefox\Profiles
 4. You will be seeing Mozilla Firefox profiles, and depending on how many browser profiles you have, go to the default ones you have, such as default-release in some cases, and click on the extensions folder inside the profile.
4. You will be seeing Mozilla Firefox profiles, and depending on how many browser profiles you have, go to the default ones you have, such as default-release in some cases, and click on the extensions folder inside the profile. 5. It will be difficult to determine the extensions of the folders you see because they have generated IDs. To make things simple, users should delete every .xpi extension file and make sure the Microsoft Edge browser is closed when you do so.
5. It will be difficult to determine the extensions of the folders you see because they have generated IDs. To make things simple, users should delete every .xpi extension file and make sure the Microsoft Edge browser is closed when you do so. When you open the browser, every extension you have will have been removed. After the virus has been wiped out, install the extensions that you frequently use again.
When you open the browser, every extension you have will have been removed. After the virus has been wiped out, install the extensions that you frequently use again.

Microsoft Edge
1. Open Microsoft Edge and enter the following URL to enter the extensions manager page of the browser: edge://extensions on the other hand, you may click the horizontal three-dot menu and click Extensions from the multiple options shown. Then a small window of extensions will show; click on the Manage extensions to enter the same page. 2. The page will then show all of your installed extensions within the Microsoft Edge browser. Find the one you think may be infected with a virus or is a malicious plugin and disable it by toggling the blue switch (We will be using the AdBlock extension as an example). Then proceed to uninstall it by clicking the remove button right next to Details.
2. The page will then show all of your installed extensions within the Microsoft Edge browser. Find the one you think may be infected with a virus or is a malicious plugin and disable it by toggling the blue switch (We will be using the AdBlock extension as an example). Then proceed to uninstall it by clicking the remove button right next to Details. 3. If you were unable to remove the malware plugin, then you will have to head over to the browser’s extension files via File Explorer to remove it manually. To do so, please head over to the extensions tab first, and now click the details next to the remove option.
3. If you were unable to remove the malware plugin, then you will have to head over to the browser’s extension files via File Explorer to remove it manually. To do so, please head over to the extensions tab first, and now click the details next to the remove option. 4. Open File Explorer and head over to the following directory where all browser plugins within Microsoft Edge are stored:
4. Open File Explorer and head over to the following directory where all browser plugins within Microsoft Edge are stored:
C:\Users\Your Username\AppData\Local\Microsoft\Edge\User Data\Default\Extensions
 5. Now find the folder with the same extension ID as the plugin we want to be removed. It indicates that the following folder contains the files for the particular virus extension: Right-click it and delete it.
5. Now find the folder with the same extension ID as the plugin we want to be removed. It indicates that the following folder contains the files for the particular virus extension: Right-click it and delete it.
 The next time you open the browser, the malware-infected extension has now been completely removed.
The next time you open the browser, the malware-infected extension has now been completely removed.
Step 3: Uninstall unwanted programs from the computer
The advertisements that were previously displayed before we removed the pop-ups from the browser may have also led to the installation of adware, also known as advertisement-supported software. Adware will probably be the culprit if pop-ups start to appear again.
Many users may not know this, but adware can automatically configure the browser to show pop-ups and redirect web pages. When it detects that users have removed the current configuration, it will immediately replace it again without requesting the users’ consent.
Additionally, malware can also be installed in such cases, which is why it’s crucial to verify the applications that are already installed on your computer to determine whether any malware has possibly been installed.
How will I know what to uninstall?
Giving the exact name of the malicious program may be complicated, but there are ways to make it easier to detect it. One of which is to simply remove all unknown programs you do not recognize or think you have not installed. You may have applications that you don’t even know the use for; that is a sign that they can be malware.
Unless it is a system process, which you can see by checking the developer of the application, some trojan viruses also use recognized and legitimate names to obfuscate their programs. If the publisher name or source of the program is unknown to you, it is best to uninstall it.
Another thing to do is to look at the version number; the majority of adware and dangerous programs will have version 1.0 because they don’t need to be updated and are merely running as background applications.
To remove malicious programs from your computer, we have provided two ways to do so: one is through normal uninstallation, and if that does not work, we also provide an advanced uninstall method to make sure it will be removed without issues.
Remove software via Control Panel
The most common way to remove malware from your computer is to uninstall the program through the Control Panel. You may view all of your installed apps as well as the developer’s name in the list of applications.
You can eventually remove the cause of pop-ups and other adware-related browser troubles by uninstalling the programs you do not recognize.
1. From the Windows search bar at the bottom of your screen, search for Control Panel and click the result that matches the same application.

2. You will see different options, such as System and Security, as well as User Accounts. But what you want to click is the Uninstall a program under the Programs section. Depending on your Windows version, hovering over the uninstall section will be relatively the same.
 3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed.
3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed. 4. Right-click the suspected virus program and click Uninstall to get rid of it (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed.
4. Right-click the suspected virus program and click Uninstall to get rid of it (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed. There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
It is widely known to be enough to remove malicious programs that are evading uninstallation. If you encounter such an issue when proceeding to uninstall the app, you may utilize the uninstaller to do the job for you.
Remove malicious programs via Revo Uninstaller
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a handy tool for Windows users.
This uninstaller not only removes programs from the computer but also deletes their changes from the Windows Registry, Host File, etc. Following the steps below will guide you on how to install and use Revo Uninstaller to get rid of the source of pop-ups.
1. Click the button below to proceed with installing Revo Uninstaller on your computer since we have made an in-depth guide on how to use it on the following page. On the other hand, you can also head over to Revouninstaller.com and download it from there.
2. After the setup file (revosetup.exe) has finished downloading, run the installation wizard, read the license agreement, and click agree to proceed to the next step of the installation. Follow the procedure and wait until the installation of the software is complete.
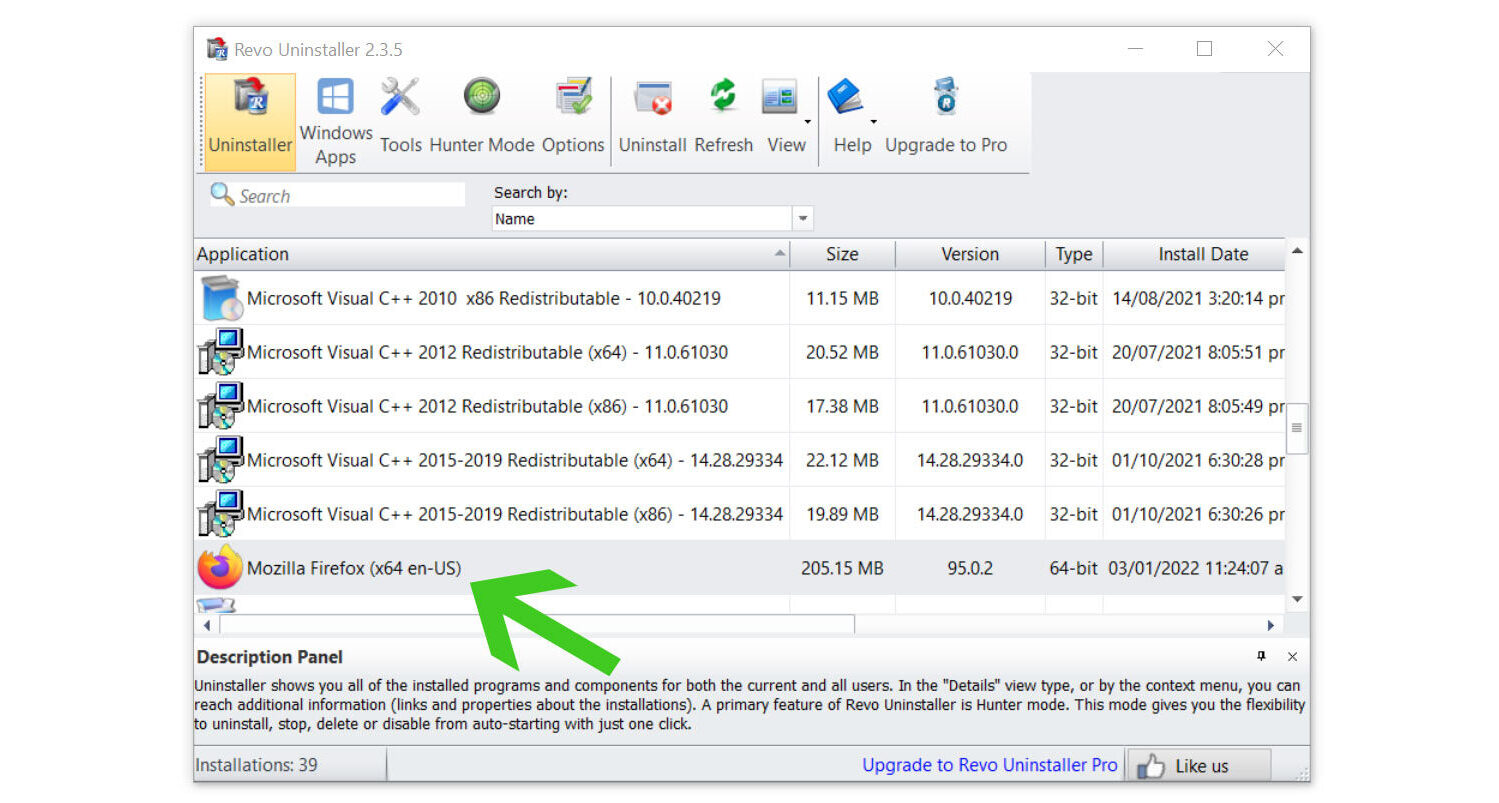
 3. Once the software has launched, find the unwanted application that needs to be removed and double-click the program to uninstall it. (We will be using the Mozilla Firefox browser as a demonstration.)
3. Once the software has launched, find the unwanted application that needs to be removed and double-click the program to uninstall it. (We will be using the Mozilla Firefox browser as a demonstration.)
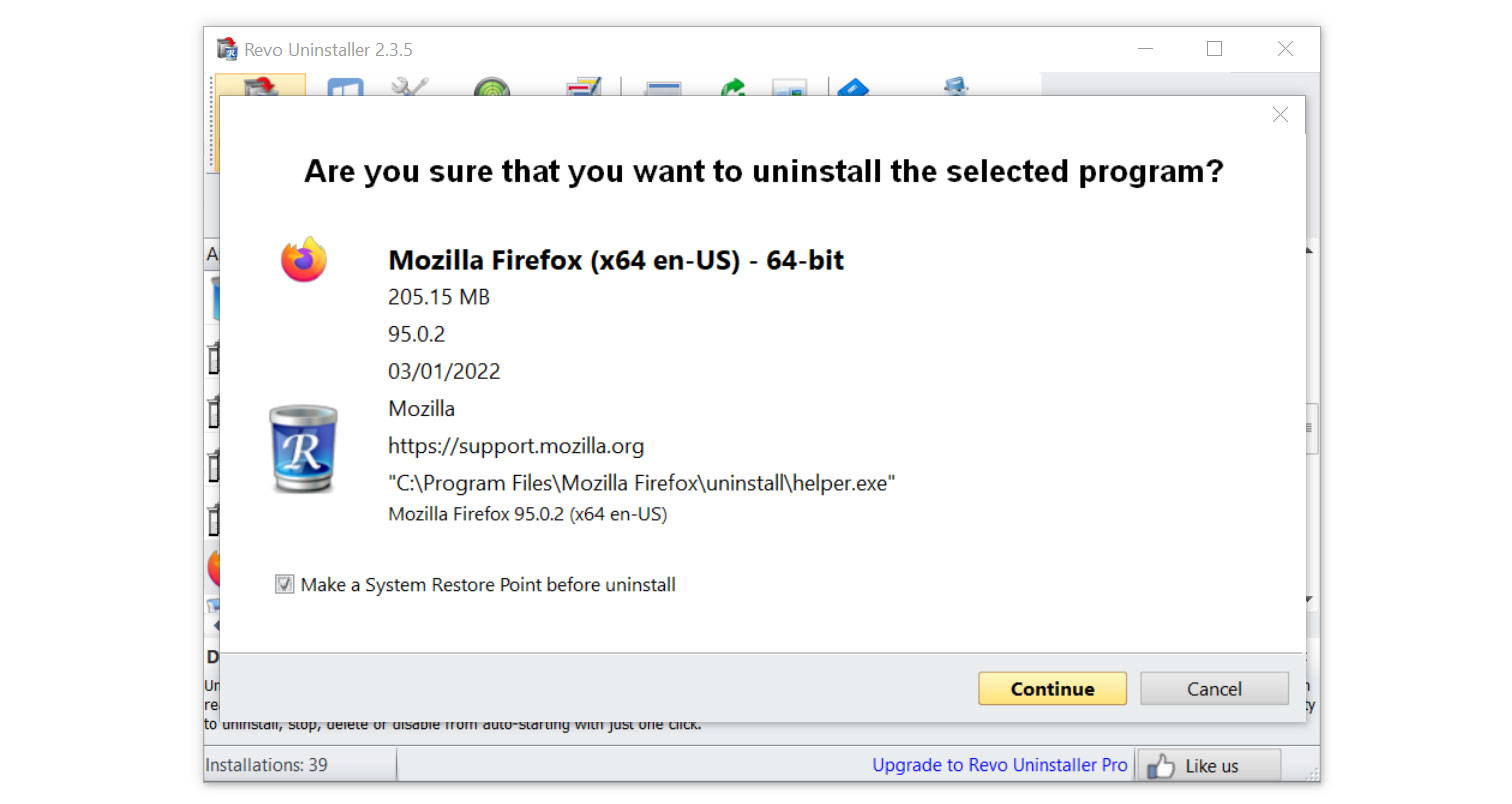
4. Click on the Continue button and follow the procedure to start uninstalling the program. It is also advised to make sure that a System Restore Point is made before the uninstallation, just in case.
5. You will be prompted to choose a scanning mode. From the three options available, select Advanced mode, then click Scan.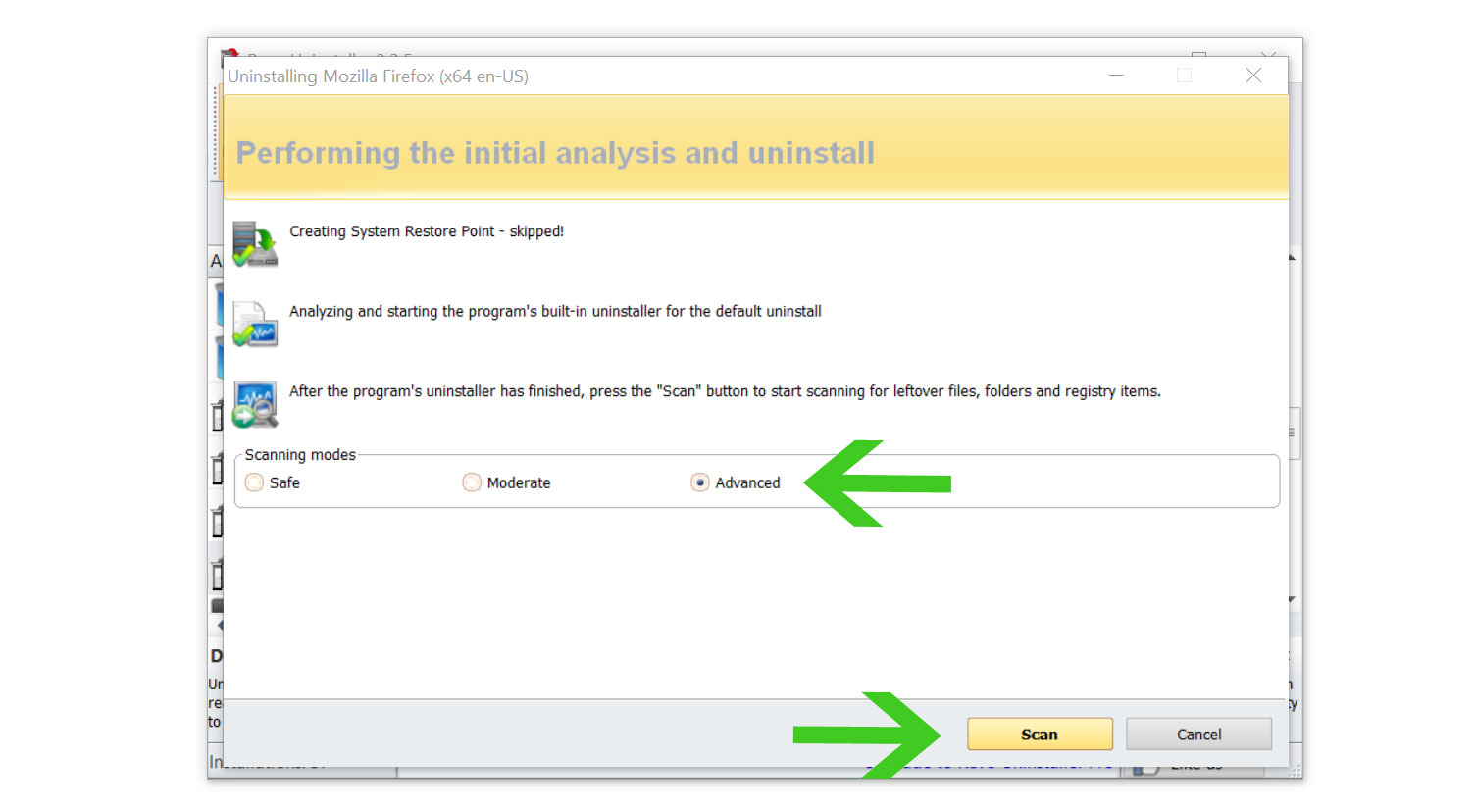 6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
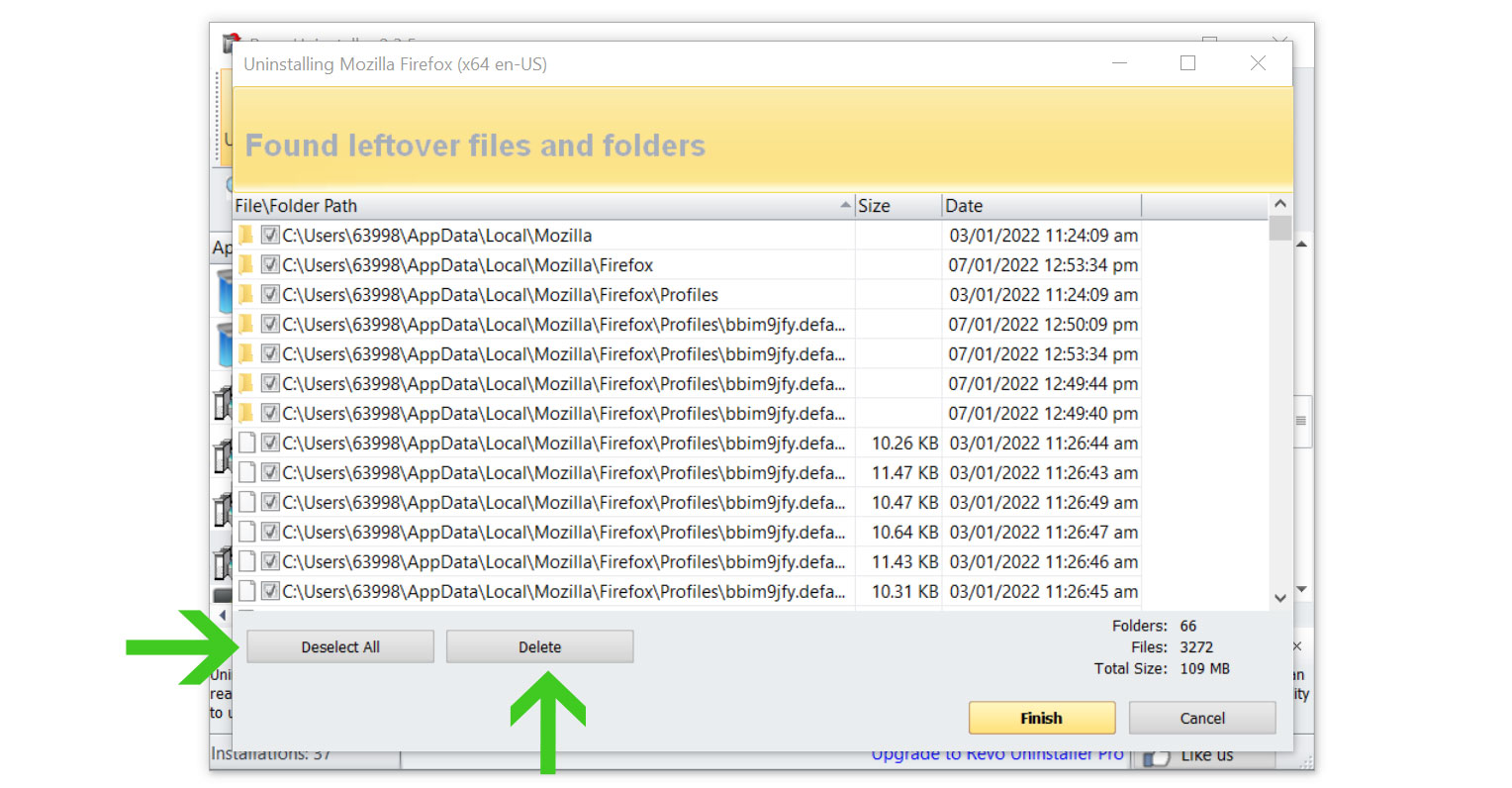
Once the window closes, you have successfully removed the malware threat from your system. And we believe with absolute certainty that once the malicious program has been removed, the browser issue will now be fixed, and you can now continue browsing the web without seeing advertisements.
Step 4: Scan with powerful malware removal software
Malware often hides entirely within the system files and registry, making it impossible to detect it by merely looking at the programs or browser extensions.
Pop-ups are generated by the web browser’s notifications, but because they display pop-ups and redirect the browser, such dangerous malware may have already been installed on the system without the user being aware of it.
The pop-ups might have already installed system-exploiting viruses and possibly time-triggered malware infections if they weren’t immediately removed.
Running a complete system virus scan with Malwarebytes Anti-Malware is advised to remove these malware threats. When it comes to getting rid of viruses from the system, this software is well-known and respected by security professionals.
Doing this step will be the final nail in the coffin for the malware that has infected your computer.
Remove malicious pop-ups with Malwarebytes Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common browser threats as shown from our tests with the software, and we assure you that it can remove the malware brought upon by the pop-up ads.
 Not to mention, it is free to use and does not come at any cost to remove the viruses it finds on your computer.
Not to mention, it is free to use and does not come at any cost to remove the viruses it finds on your computer.
To use Malwarebytes and remove malicious threats from the computer, follow the steps below:
1. Download Malwarebytes by clicking the button below, as we have made an additional and in-depth tutorial on how to use it. Otherwise, you may go to their official website via Malwarebytes.com (Avoid misspelling as it may lead to scams).
Download Malwarebytes Anti-Malware
2. Visit their download section and start a Free Download to begin installing the software on your computer. 3. Once the Malwarebytes setup file (MBsetup.exe) has finished downloading, open the executable file in File Explorer, then right-click the setup and select run as administrator to give the highest system authority and make sure Malwarebytes is installed correctly.
3. Once the Malwarebytes setup file (MBsetup.exe) has finished downloading, open the executable file in File Explorer, then right-click the setup and select run as administrator to give the highest system authority and make sure Malwarebytes is installed correctly. 4. Make sure to carefully follow the installation setup wizard’s instructions and provide the relevant information it requires. You will be prompted with questions such as Personal or Business Use, Email Address, and others.
4. Make sure to carefully follow the installation setup wizard’s instructions and provide the relevant information it requires. You will be prompted with questions such as Personal or Business Use, Email Address, and others. 5. From the application’s home screen, go to the scan tab and begin running a system scan. This will scan the whole computer, including memory, startup items, the registry, and the file system. Ensuring that malware has been inspected for and detected in all of the places where it frequently hides.
5. From the application’s home screen, go to the scan tab and begin running a system scan. This will scan the whole computer, including memory, startup items, the registry, and the file system. Ensuring that malware has been inspected for and detected in all of the places where it frequently hides. 6. Since it can take a while, you should either relax and wait for it to finish or find something else to do. The length of the scan depends on the size of the files you have and the hardware capabilities of your computer. Here are some ways to make scanning faster.
6. Since it can take a while, you should either relax and wait for it to finish or find something else to do. The length of the scan depends on the size of the files you have and the hardware capabilities of your computer. Here are some ways to make scanning faster.
7. Once the scan is finished, Malwarebytes will show the malicious viruses and threats it found on your PC. The program will show the detection results, and the malware it found will be given a threat name such as Generic.Trojan.Injector.DDS, and many more. 8. Select all the detected files from the report and click the quarantine button to remove the malicious items from the computer into the protected safe quarantine zone of the anti-malware program so that they would not affect and do malicious actions on the PC again.
8. Select all the detected files from the report and click the quarantine button to remove the malicious items from the computer into the protected safe quarantine zone of the anti-malware program so that they would not affect and do malicious actions on the PC again. 9. After placing the virus files in the program’s quarantine, it may prompt you to restart the computer to finalize the full system scan procedure. Please restart your computer if prompted, as it is essential. After the restart, Malwarebytes will open and display a message that the scan was complete.
9. After placing the virus files in the program’s quarantine, it may prompt you to restart the computer to finalize the full system scan procedure. Please restart your computer if prompted, as it is essential. After the restart, Malwarebytes will open and display a message that the scan was complete.
Note: Don’t forget to delete the quarantined files afterward.
Simply quarantining the malware files is not enough to make sure they are completely removed. This is a very common misconception: once you click the quarantine button, it is all good and gone.
But, while its effects and harmful activities are halted, the malware is still in the system, only placed in the anti-malware program’s quarantine folders. To completely remove it from the computer, go to Detection History from the home screen, select all Quarantined items, and click Delete.

You have successfully removed the malicious pop-ups as well as the hidden threats on your computer. Rest assured they would not resurface again since Malwarebytes offers a premium trial for 14 days, so you could take advantage of it for free and prevent malware from infecting your system.
Malwarebytes offers free malware detection and cleanup, but its premium version also comes with real-time protection to keep your computer secure at all times. Although we advise using the premium trial, if you find it beneficial, you are encouraged to buy the full version.
The software is an anti-malware solution that eliminates malicious threats including trojan horses, worms, stealers, miners, keyloggers, and several other types of malware and computer viruses.
We suggest Malwarebytes if you are looking for a removal tool and as a second opinion scanner, but if you want full-fledged antivirus software, we believe that the built-in Windows Defender is enough for security or if you want something with a more sophisticated system and better protection: Kaspersky Free.
If you choose to uninstall Malwarebytes, you may suddenly see that Windows Defender Real-Time Protection is turned off. This is a common issue that users may face when uninstalling the software. To fix this issue, you may refer to this article.
Alternative: Kaspersky Free Antivirus
After removing the malware, you may want to install antivirus software to protect your computer against browser threats.
More importantly, running an additional scan with a different program’s threat database will alert you to hidden Trojan viruses and rootkits that were not removed from the prior scan with Malwarebytes. Since the beginning of the cybersecurity industry, Kaspersky has been a well-known antivirus program. It is one of the top antivirus products on the market and is highly praised by experts in the area. It can also get rid of other malware hidden on your computer thanks to its sophisticated internet security protection.
Since the beginning of the cybersecurity industry, Kaspersky has been a well-known antivirus program. It is one of the top antivirus products on the market and is highly praised by experts in the area. It can also get rid of other malware hidden on your computer thanks to its sophisticated internet security protection.
What is the difference between anti-malware and antivirus? Anti-Malware software is designed to specifically remove malware and its variants. In addition, it employs heuristic-based detection by picking up harmful code from files.
On the other hand, an antivirus uses signature-based detection, which examines data for attacks to protect users from dangerous viruses, including keyloggers, loaders, worms, trojans, and others.
Malwarebytes and Kaspersky are identical, but Kaspersky is a better overall program since Malwarebytes’ main purpose is to remove malware, but Kaspersky has been known for comprehensive computer security protection ever since.
 Based on our experience removing malware, when two different programs are used to scan, various threats are identified by one software but not by the other. Given that their threat databases differ from each other, it might be able to capture harmful viruses, rootkits, and trojans that Malwarebytes has missed.
Based on our experience removing malware, when two different programs are used to scan, various threats are identified by one software but not by the other. Given that their threat databases differ from each other, it might be able to capture harmful viruses, rootkits, and trojans that Malwarebytes has missed.
Please be aware that if you decide to use Kaspersky, you should first uninstall Malwarebytes because having both security programs installed will cause a conflict. If you choose to do so, please remove Malwarebytes first, as it is essential to do so before we get started.
1. Click the button below to start downloading Kaspersky Antivirus on your computer. On the following page, we have provided clear details on how to install it on the computer. On the other hand, you may go to their official website by searching for the software on your web browser or typing Kaspersky.com (Beware of misspellings since cybercriminals typically use these as exploits to redirect users to malicious webpages).
2. Go to the download page for Kaspersky Free Antivirus. Before clicking download, you will be prompted to choose your continent and where your country is located. This is very important, and you should not choose a different country because you will be met with a “Not supported in your region” message during installation. 3. Once you click download, a setup file (startup.exe) will be downloaded on the computer. After it has finished downloading, open its file location, right-click the executable file, and then select Run as administrator. This will ensure that Kaspersky’s installation will be smooth and will not result in certain errors.
3. Once you click download, a setup file (startup.exe) will be downloaded on the computer. After it has finished downloading, open its file location, right-click the executable file, and then select Run as administrator. This will ensure that Kaspersky’s installation will be smooth and will not result in certain errors. 4. The Kaspersky installation wizard will launch, and you can then proceed to install Kaspersky Free by following the setup instructions. If a UAC prompt appears, simply accept it and proceed with the installation.
4. The Kaspersky installation wizard will launch, and you can then proceed to install Kaspersky Free by following the setup instructions. If a UAC prompt appears, simply accept it and proceed with the installation. 5. Please be patient while Kaspersky is being installed on your computer. The speed and length of the installation process will depend on your computer’s specifications. Kaspersky also mentioned that sluggishness or dark displays during the installation of their program are normal and should not be worried about.
5. Please be patient while Kaspersky is being installed on your computer. The speed and length of the installation process will depend on your computer’s specifications. Kaspersky also mentioned that sluggishness or dark displays during the installation of their program are normal and should not be worried about.
6. To use the antivirus program, you must first create an account on the sign-in page that appears after the antivirus application has been successfully installed on the computer. If you’re looking for the sign-up button, simply enter your email exactly as it appears; if you don’t already have an account, one will be created for you. 7. Kaspersky will ask you to decide which plan to use. It will be either the Standard version or Kaspersky Plus. In this case, the standard version is all you need for now. If you want to try the premium version of Kaspersky, you may opt for Kaspersky Plus to try the features for free. You do not have to add a payment method to get started, and after the trial ends, you will be downgraded to the Standard version unless you pay for it.
7. Kaspersky will ask you to decide which plan to use. It will be either the Standard version or Kaspersky Plus. In this case, the standard version is all you need for now. If you want to try the premium version of Kaspersky, you may opt for Kaspersky Plus to try the features for free. You do not have to add a payment method to get started, and after the trial ends, you will be downgraded to the Standard version unless you pay for it. 8. You will be asked if you want to install additional applications, namely Kaspersky Password Manager and a VPN. Feel free to opt for a program you might want to use; otherwise, install both, or choose not to if you do not need them.
8. You will be asked if you want to install additional applications, namely Kaspersky Password Manager and a VPN. Feel free to opt for a program you might want to use; otherwise, install both, or choose not to if you do not need them. 9. Kaspersky will ask you to scan for viruses in the background. Simply choose not to do so because we will be doing a full system scan later; however, doing a scan now will only initiate a quick scan. However, if you want to be safe, you can run the background scan now and proceed with a full system scan after.
9. Kaspersky will ask you to scan for viruses in the background. Simply choose not to do so because we will be doing a full system scan later; however, doing a scan now will only initiate a quick scan. However, if you want to be safe, you can run the background scan now and proceed with a full system scan after. 10. Once the antivirus application has opened, go to the security tab and click the choose a scan button. You will be presented with several different scans; go for the full system scan to ensure full computer security. Always remember to update the database because this will ensure that Kaspersky can detect newly discovered threats and exploits.
10. Once the antivirus application has opened, go to the security tab and click the choose a scan button. You will be presented with several different scans; go for the full system scan to ensure full computer security. Always remember to update the database because this will ensure that Kaspersky can detect newly discovered threats and exploits. 11. A full system scan will take a long time to finish since it will look into all the files on the computer, including the registry, memory, startup applications, and many more. The scanning time will depend on how many files there are on the computer and how big the files are. Additionally, the computer’s hardware and specs will also play into how long the scan will take.
11. A full system scan will take a long time to finish since it will look into all the files on the computer, including the registry, memory, startup applications, and many more. The scanning time will depend on how many files there are on the computer and how big the files are. Additionally, the computer’s hardware and specs will also play into how long the scan will take.
12. After the full system scan is finished, it may detect remnants of the pop-ups and other malware hiding in the computer, showing its location along with a detection name (Trojan.Win32.Generic, Exploit.Win32.Generic, etc.) given to it. Go ahead and proceed to disinfect and restart the computer. 13. The Advanced Disinfection process will then start, and depending on the amount of RAM the computer has, it could take some time. It will then request a computer restart to complete the operation.
13. The Advanced Disinfection process will then start, and depending on the amount of RAM the computer has, it could take some time. It will then request a computer restart to complete the operation. Your computer will now have finished the entire system scan after restarting. By doing this, you can be sure that all other forms of malware and viruses have been wiped from your computer.
Your computer will now have finished the entire system scan after restarting. By doing this, you can be sure that all other forms of malware and viruses have been wiped from your computer.
You shouldn’t be concerned if the scan turned up no instances of malware or viruses, which indicates that there isn’t any malware on your computer. If two independent programs declare your computer safe, then that’s probably the case.
Step 5: Reset the browser to its default settings (Optional)
With browser threats such as pop-up ads where potential malware exploits are possible, it may be scary to think of browsing again. So to ease your mind, you can reset the browser to its default configuration to make sure that any suspicious elements within the browser are also removed, even after clearing every speck of malware, trojan, and virus.
If the pop-ups continue to override the permission, resetting the browser also ensures that any additional settings it has set will be deleted, making the browser operate as though it had just been downloaded.
Resetting the browser includes complete reversal and wiping out history, homepage settings, default search engines, and browser permissions, which may be used by malware actors to show pop-ups. In addition, the browser reset does not include the favorites tabs, bookmarks, or saved passwords in some cases.
To reset your browser to its default settings, please follow the steps below for the browser you are using.

Google Chrome
1. Open the Google Chrome browser and click the three dots in the upper-right corner of your screen to access the drop-down menu.
2. From the menu presented, select the Settings button, then click the Advanced menu on the left side of the screen from the settings.
3. On the drop-down menu presented on the screen, select Reset and Clean up.
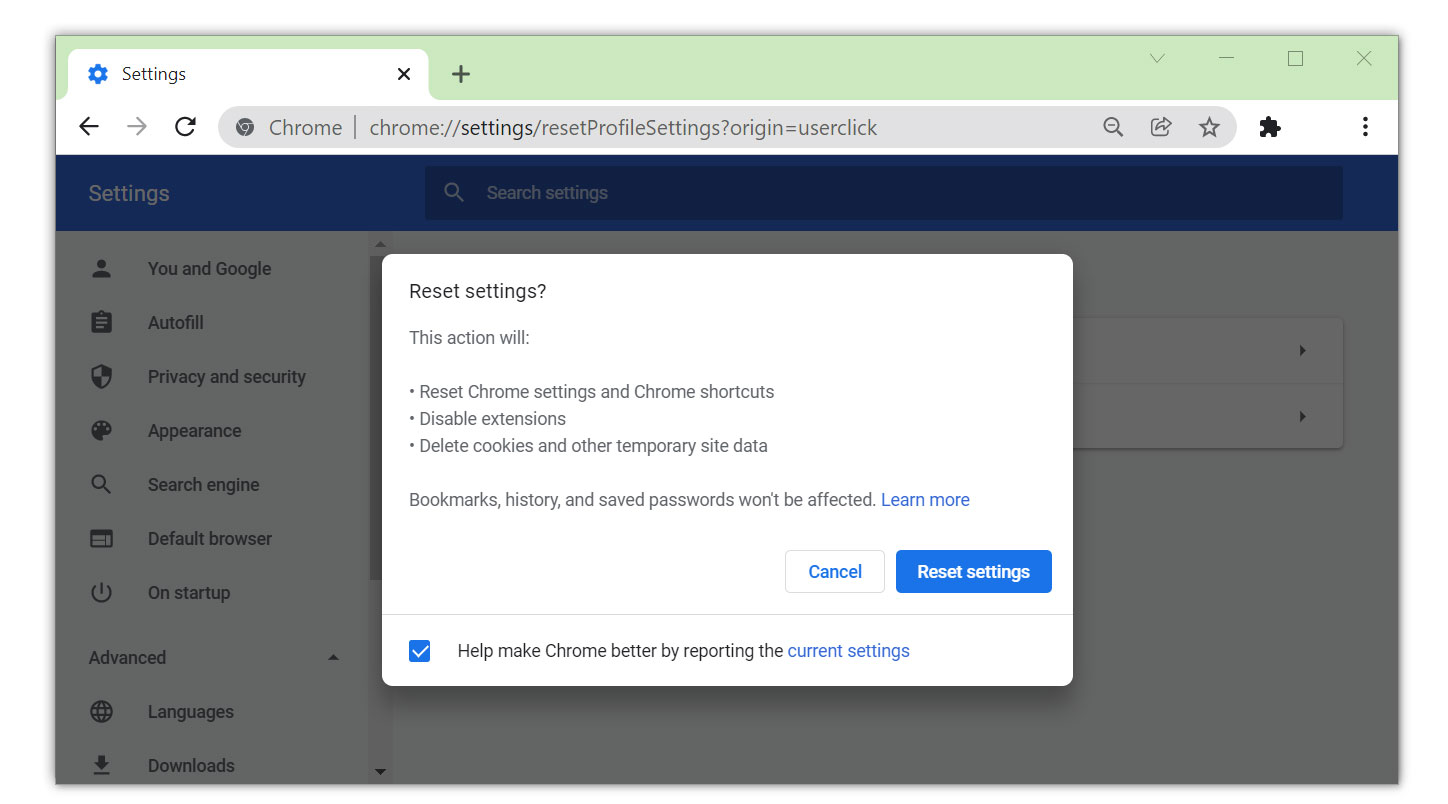
4. Click on the Restore settings to their original defaults.
5. Then a small confirmation window will appear; click the Reset Settings.

Mozilla Firefox
1. Launch the Mozilla Firefox browser, then open the menu by clicking on the three horizontal lines located in the upper-right corner.
2. Navigate down and click Help, then select More Troubleshooting Information from the options given.
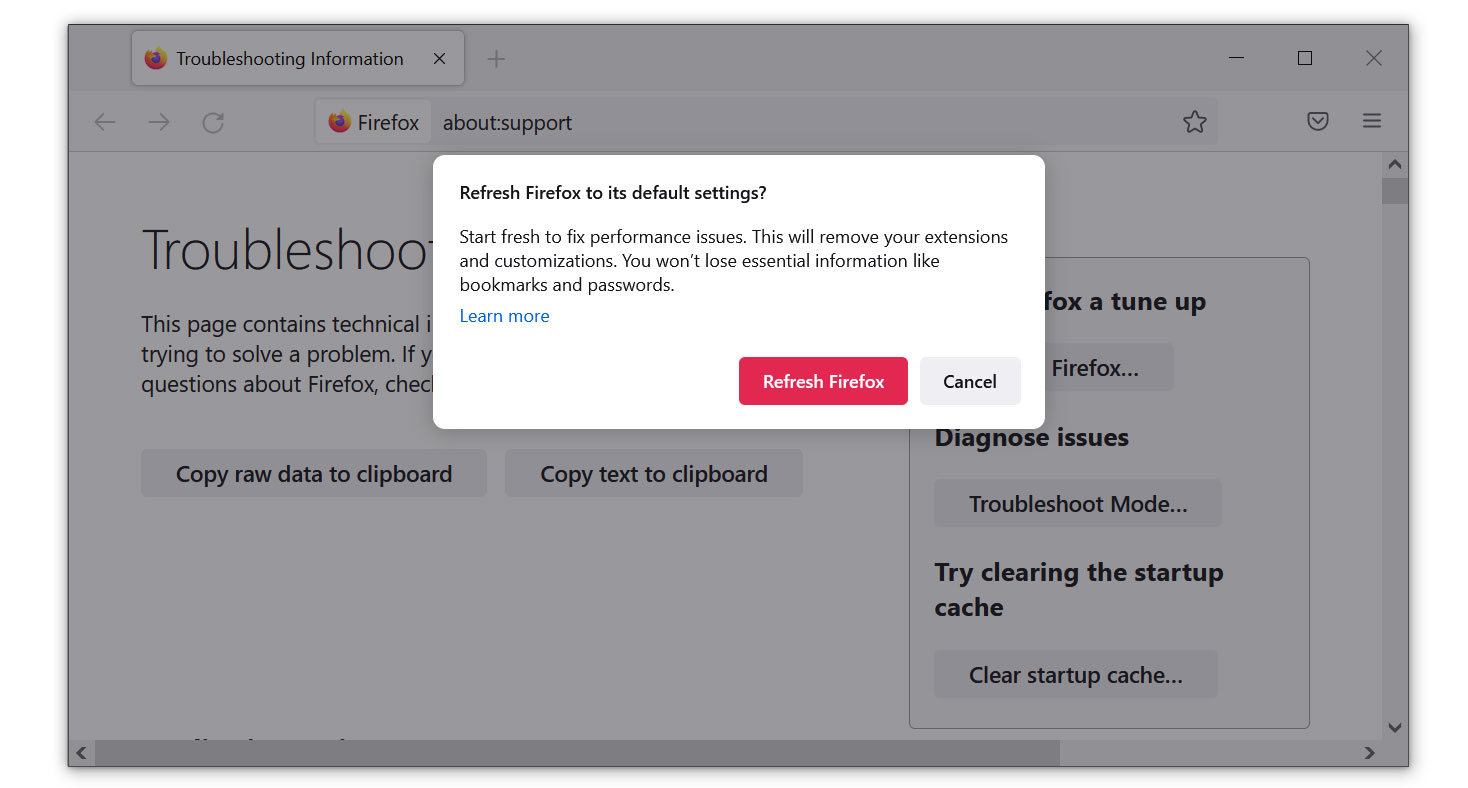
3. Select the Refresh Firefox button. Then click Refresh Firefox on the confirmation window that appears.

Microsoft Edge
1. Run Microsoft Edge on the computer and click the three-dot icon in the upper-right corner.
2. Click on the Settings button from the drop-down menu.
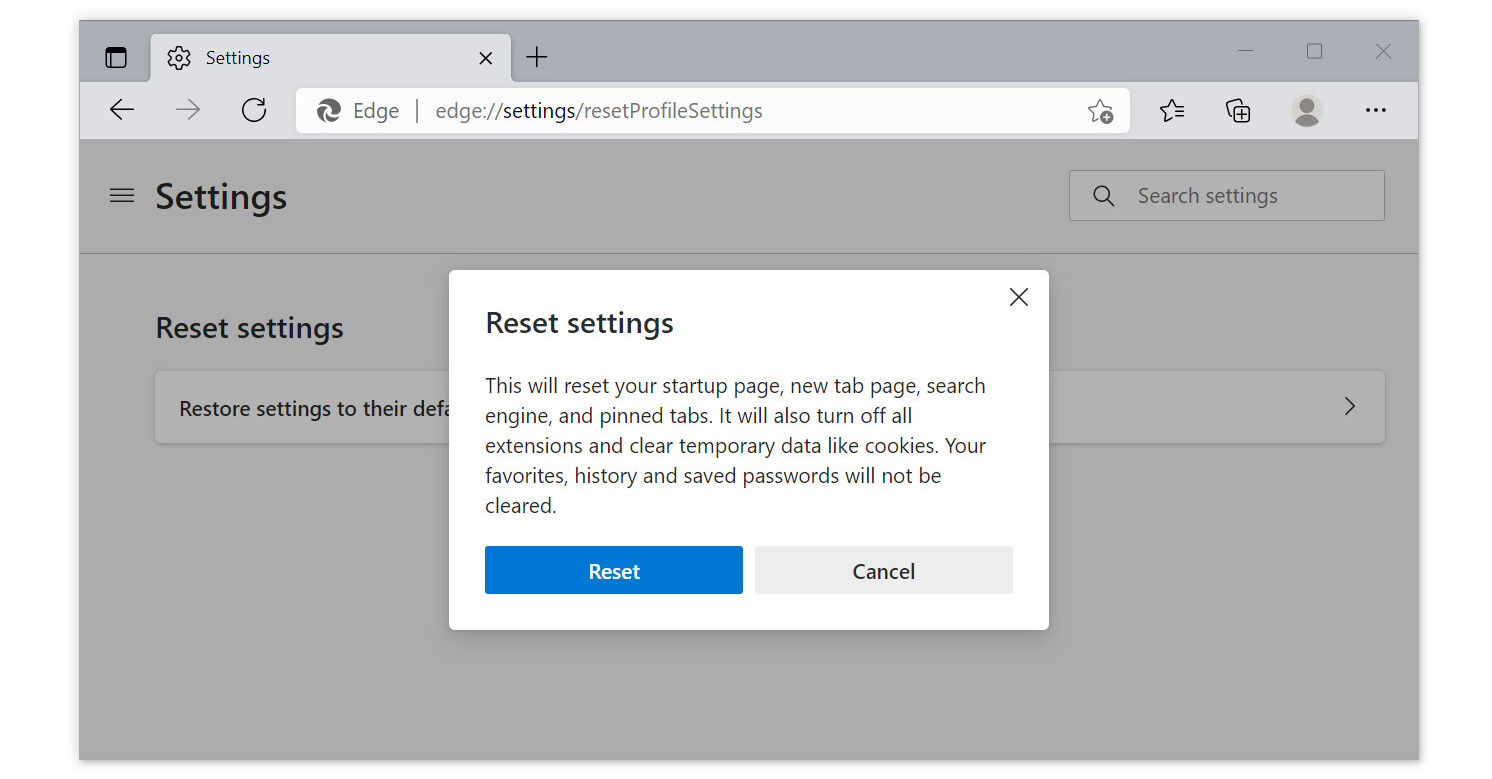
3. Find and click Reset Settings from the left sidebar. Then click on the option Restore settings to their default values.
4. A warning window will appear, telling you that you are about to reset the browser. Click Reset, and the browser should return to its default settings.
The configurations added by adware and browser hijackers have all been removed, and your browser has now been entirely reset to the settings it had when you initially installed it. You can use your browser with complete security now. Rest assured that pop-ups from the browser won’t appear again.
For a better and safer web browsing experience, we’ve provided a few security measures and advice below that will safeguard your browser and computer from harmful threats like worms, malware, trojans, keyloggers, stealers, and other kinds of computer viruses that will harm user data.
Protective measures for better overall security
Removing trojan viruses and malware from your computer is one thing; keeping it secure for the future and for a long period is a different thing and will require certain things to make sure you are secured, especially if you do not know most of the ins and outs of the device you are using.
Cybercriminals are always stepping up their game to make sure they infect users and extract data and money from them.
We encourage you to take the actions listed below to ensure complete security before leaving this page because we strongly promote web security and having a secure online presence.
Safeguard your privacy and data by using a VPN application
VPNs, also known as virtual private networks, guarantee your safety and complete anonymity while you browse the internet.
In contrast to a firewall, which monitors and blocks potentially harmful connections in the network, A VPN hides the user’s connection via a tunnel so that it would appear to third parties as a different IP address and location.
This ensures that your data won’t be leaked because the program hides it. Be aware that visiting infected websites may cause your IP address and location to be disclosed; however, if you use a VPN, this will prevent your true IP address from being revealed to malware actors.
If you already had Kaspersky installed from the previous step, you had the choice to install its integrated Virtual Private Network, which is a good tool that we also advise.
However, if you decide against doing so and instead download a VPN-only program to cloak your web browsing activity, Mullvad, and AirVPN are excellent choices for fast connections and better privacy.
Mullvad VPN

Since user privacy is the main focus of a virtual private network program, Mullvad VPN excels at putting users’ privacy first. You do not need to enter your email address while registering to download their application because they maintain anonymous accounts.
If you wanted to hide or didn’t want your credit card information to be disclosed, they also accept Bitcoin payments. According to their website, they support a free internet that is devoid of surveillance and censorship.
They have also been announcing new server locations to guarantee users a fast connection anytime they want to connect to various areas throughout the world.
AirVPN
AirVPN seeks to provide users with access to the real internet, in contrast to Mullvad, which promises to offer users a free internet. Along with masking your IP, they also don’t monitor or log any user data, which is good.
You can use it for a long time without worrying about being disconnected because they don’t impose a traffic or time limit when connecting to their servers. In addition, there are infinite, cost-free server changes with physically fast servers in many different nations.
Additionally, when registering for their program, you are not required to enter your email address. They also offer strong encryption and Perfect Forward Secrecy to ensure that it is difficult to determine the user’s connection.
Use an adblocker when browsing the internet
Installing an adblocker on the browser is the best way to get rid of unwanted pop-up advertisements as well as other threats such as redirections, browser hijackers, and unwanted toolbars.
Additionally, by blocking malicious websites before users can even access them, it is possible to prevent malware from being downloaded.
In this case, we recommend uBlock Origin, which is an open-source AdBlock extension that comes at no cost and is free forever. It is one of the most reliable plugins out there, ensuring that every advertisement on a webpage will be blocked.

For Google Chrome
1. Go to the Chrome Web Store and search for the browser extension, or click here to go directly to the extension page.
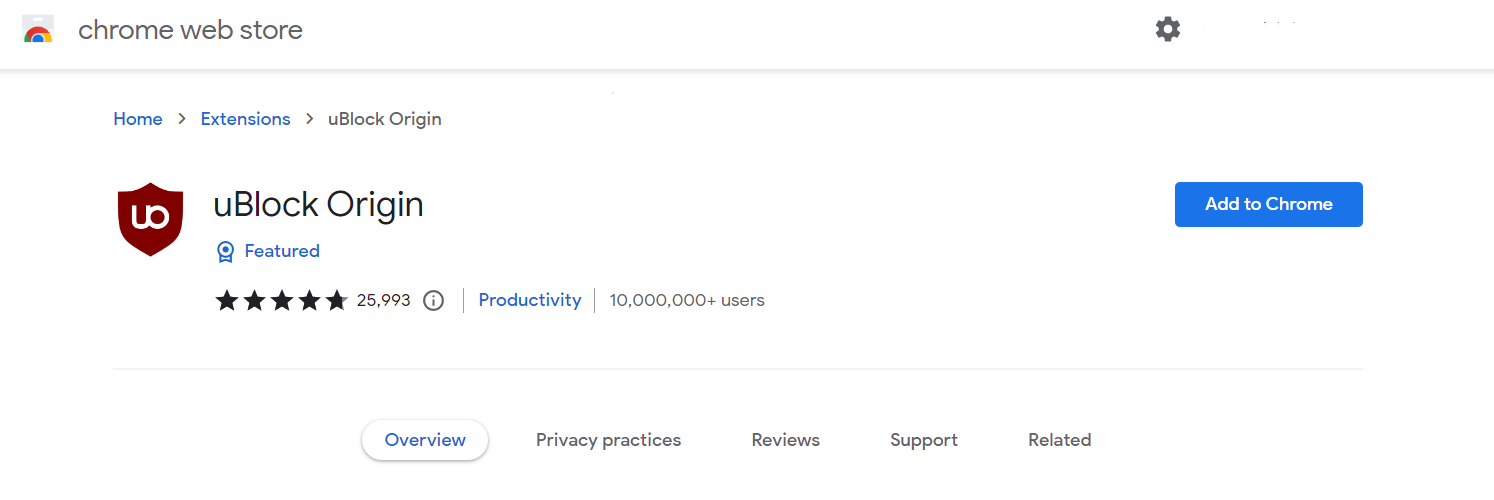
2. Click the Add to Chrome button. Then click Add extension when the confirmation window appears.
3. uBlock Origin is now installed in Google Chrome. The adblocker is turned on by default; you can click the power button if you wish to turn it off for a while. The menu can be found by clicking the puzzle icon in the upper-right corner next to the search bar.

For Mozilla Firefox
1. Visit the Firefox Add-ons Store and search for uBlock Origin, or click here to automatically go to the extension’s webpage.
2. Click Add to Firefox, and after that, a confirmation window will appear stating the permissions it will grant the addon. Finally, to add it to the browser, click Add.
3. Mozilla Firefox now has uBlock Origin installed. The adblocker is activated by default; if you want to disable it for some reason, simply click the power button. The menu can be found in the upper-right corner of the web browser, next to the search bar.

For Microsoft Edge
1. Go to the Edge Addon Store and search for the said browser extension. You can also click here to go directly to the plugin page of the Adblocker.
2. Click the Get button, and a confirmation window will appear. Continue installing the extension by selecting Add extension.
3. Now that uBlock Origin is installed on the browser, you can choose to disable the Adblocker by clicking the power button. The menu can be accessed by hovering over the extension’s icon next to the search bar.
The majority of pop-up advertisements, whether they include malware or not, will be filtered by the extension and no longer be displayed to you.
Utilize a firewall to prevent cyber attacks
A security firewall is required for every internet connection that is made. It is an essential tool that enhances security and stops online attacks. Through a security mechanism, it controls incoming and outgoing network connections on your system and network and filters the undesirable ones. Consider it a further barrier against malicious assaults and zero-day exploits.
You don’t need to do anything if you installed Kaspersky in the previous step because the program we installed earlier comes with a built-in firewall that is turned on by default.
On the other hand, if you prefer a standalone, fully functional firewall utility application that is exclusively focused on securing the network, we recommend these top two firewall solutions for personal computers: Comodo and ZoneAlarm.
Comodo Personal Firewall

Comodo Firewall is a well-known software program for securing your network and computer. It is a sophisticated tool with a wide range of features.
It is simple to use and doesn’t require complicated configuration to set up. It also functions by being aware of your computer usage habits to avoid interfering with your work.
Additionally, it also claims to offer the highest levels of protection against both inbound and outbound threats. It secures the ports on your computer from hackers and prevents rogue software from sending your sensitive data over the internet.
ZoneAlarm Free Firewall
You can also opt for ZoneAlarm Free Firewall as your first line of defense between your device and the internet. The program safeguards your network and blocks any dangers, and you can use the free version of it without paying anything.
It provides a robust two-way protection solution that guards against spyware from disclosing your data online while also hiding your PC from nefarious hackers.
With its cutting-edge anti-bot protection, it also protects your computer from automated cyberattacks in real-time.
Additionally, it protects your computer against spam and dubious websites. Lastly, it provides real-time defense against automated cyberattacks with its cutting-edge anti-bot security.
Bottom Line
While this may appear to be typical advice, we recommend users not visit illegal streaming or torrenting websites and more importantly, do not download anything from them because doing so may result in the installation of malware and viruses.
Because these websites are illegal, they are unable to make a profit from legitimate advertising. As a result, they host questionable advertisements from unidentified marketers that want to publicize their contents, which are most likely dangerous codes being propagated by cyber criminals.
Always make sure that your device is protected against sneaky exploits and stealthy cyberattacks. While taking precautions and avoiding dubious websites are crucial, having a solid line of defense is essential to ensuring the security of your network and data.
The threat posed by pop-up ads is not the only one on the internet, and there are many more surfacing every day. We are glad to have assisted you in resolving your browser-related problem and are proud of our expertise in this area.
If you experience another virus attack on your device, please visit our website to find a malware removal solution for your problem or get in touch with us, and SecuredStatus will be happy to assist you once again.

