Malwarebytes Anti-Malware is a powerful malware removal program that is available for Windows, Mac, and Android devices.
A practical malware removal tool is essential nowadays to get rid of malware that may cause data loss and harmful security breaches, as millions of users become infected with malware every day as it continues to evolve.
Since we have consistently recommended this program in our malware removal guides, we believe that simply stating that it is an excellent application is insufficient and that users should be provided with clear and precise information.
As a result, we conducted this test to find out how Malwarebytes performs against the most common threats that are currently lurking on the internet.
Users will see how we test this program for removing malware on the computer from our point of view. A fundamental understanding would be that Malwarebytes identified the threat when we downloaded malware ourselves, hence we suggest users use it.
However, allow us to delve more into additional threats and share our perspective on the application with users for better understanding.
We will be testing with the main Malwarebytes program as well as the Browser Guard extension because, while the Real-Time Protection feature is a paid plan, the browser extension is completely free.
Their primary application is anti-malware, which is the main tool that will help users remove malware, so we will focus on that in this article.
How do Malwarebytes defend against browser threats?
Since individuals are connected online and the internet is the source of the majority of malware installations, this means that users are more vulnerable to malware and other computer viruses.
Torrenting websites, illicit streaming services, and other unrecognized websites that use unidentified third-party advertisements that promote malware are examples of websites where users may become infected.
If internet users are not cautious when browsing, they may accidentally get on a website that abruptly reroutes them to a bogus “click allow to download the file” or “click allow if you are +18” alert, allowing the browser to display harmful pop-up advertisements.
Internet users need to be cautious of a lot of dangerous content, but if you have Malwarebytes, your security will be much better protected because the results below will show you that it can stop such browser attacks.
Protection against torrenting sites and illegal streaming platforms
We have tried to enter multiple illegal streaming websites, and the results are as follows. Of the 60 sites we visited, 53 of them had malicious elements blocked by Browser Guard as soon as the page was loaded. As was the case for GogoAnime, as seen in the image below, the Goomaphy.com domain was blocked from the site for the malicious element to not be clicked.
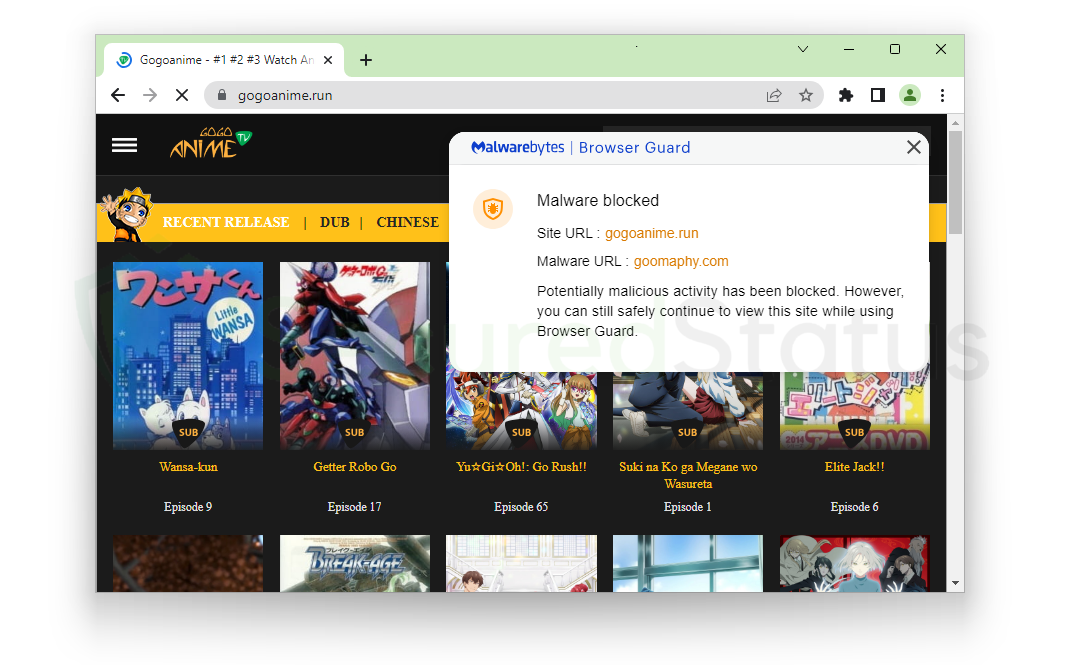
Additionally, we have already researched on the prohibited site in question and found it to be a malicious redirect domain, so blocking it was the proper move.
On the other hand, websites like Fmovies.co and six others which make up the rest of the websites we tested, were entirely blocked off by the Browser Guard, and it displayed a warning that the aforementioned website is malicious and users should not proceed.
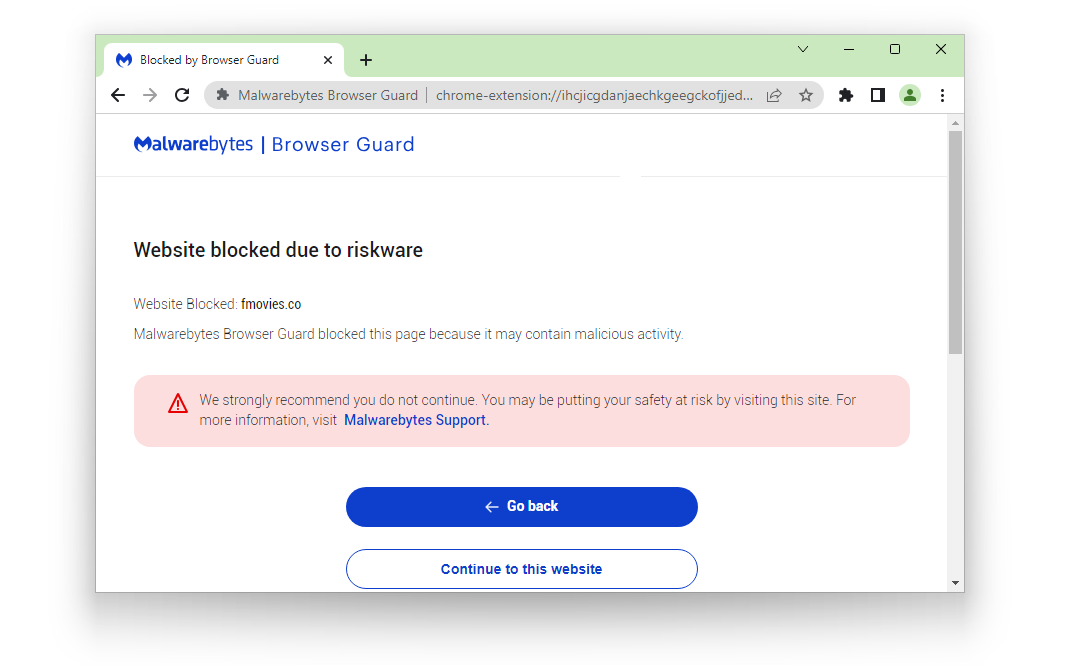
This is the case if too many malicious clickable elements are harmful and could pose a threat. If users encounter this situation, it is better not to force the browser to enter the website at all.
But to be sure, we tried to click on the Continue with this website button to see what would happen. Fortunately, the connection was restricted by the main program, Malwarebytes Anti-Malware, and a message claiming that it had prevented a connection as well as an ERR_SSL_PROTOCOL_ERROR from the browser was displayed.
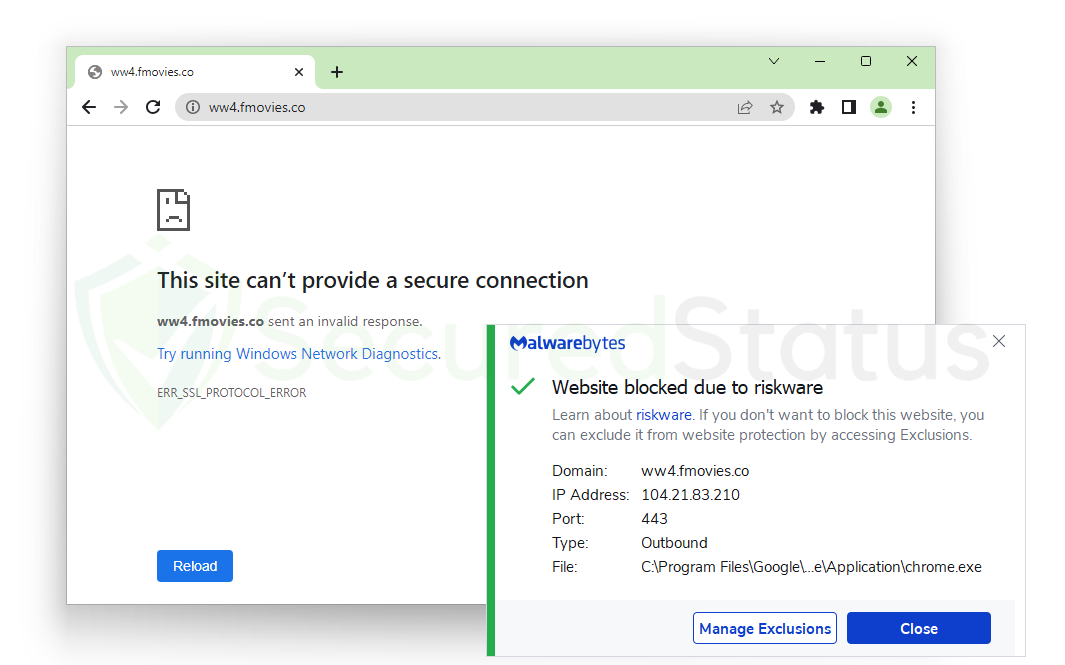
This is especially helpful if people do not know where they are going; forcing the web browser not to connect to a malicious site is what is important for an anti-malware program.
When entering less popular illegal streaming websites such as Kinox.run, the web browser was able to enter the said website; however, as usual, Malwarebytes Browser Guard blocked the malicious elements.
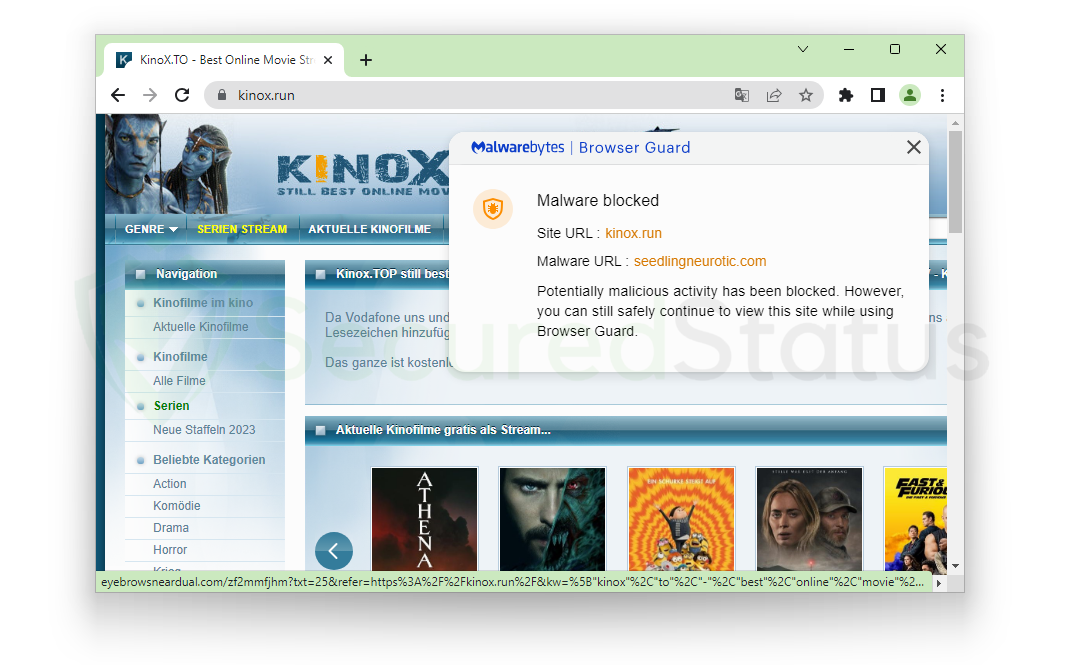
Additionally, the primary application blocks malicious domains that managed to sneak their way through as Malvertising. The name comes from the fact that it can advertise malware and install it on the computer.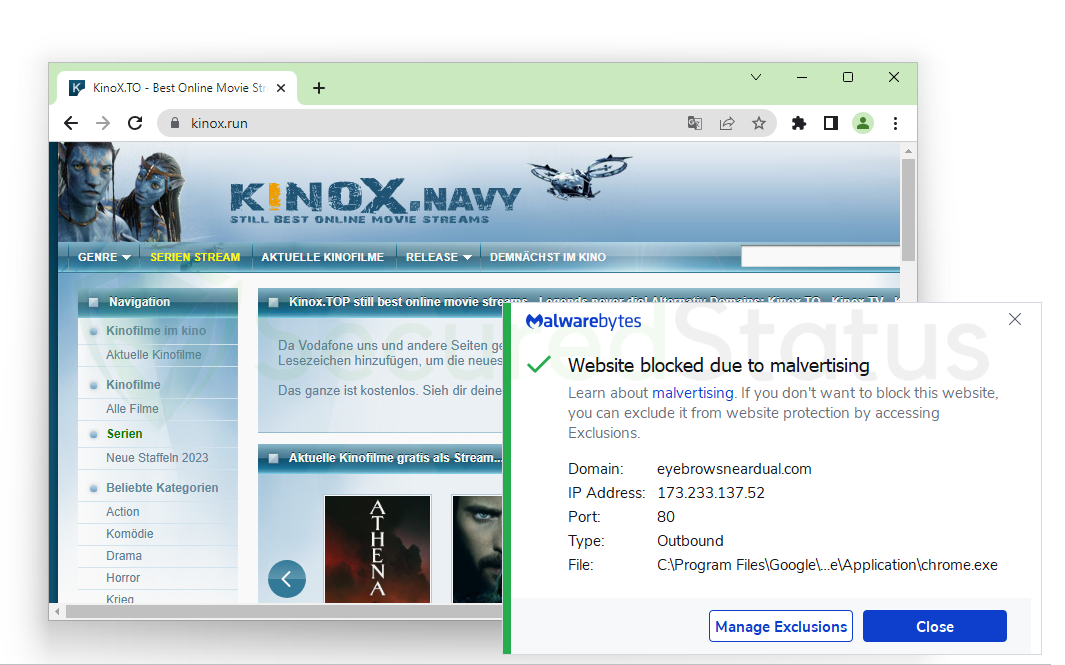
In addition, when a malicious element goes unblocked when the webpage first loads, users may suddenly see a new tab open up, which is the first thing that redirects malware will do.
However, loading it would not be the case since Browser Guard may be your first line of defense, but it is not your entire defense system at all. When this is the case, Malwarebytes Anti-Malware will step in and block it to ensure you will not be met with unwanted web pages on the new tab.
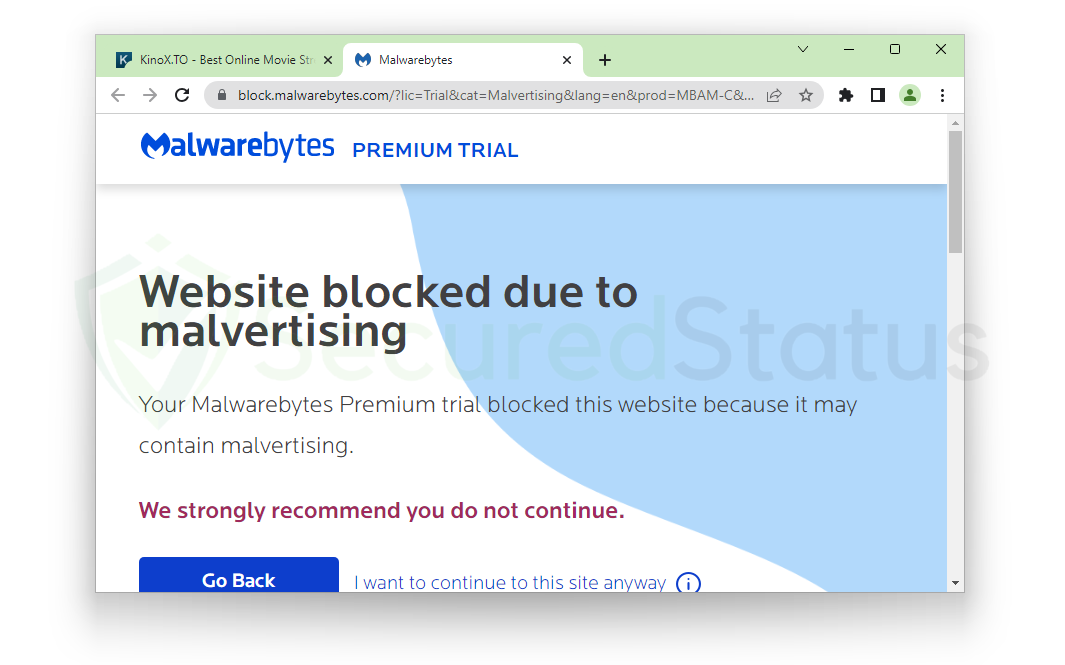
However, you might be wondering: it can block malicious URLs and domains, but where do those malicious links lead? To answer your question, we have disabled Real-Time Protection as well as the Browser Guard, which helped us block many threats, to see where these redirections lead us.
As you can see from the screenshot below, the redirection caused us to install a browser add-on called Wild Nature New Tab, which is a somewhat dubious plugin that modifies the home tab and search engine of your browser. Not as harmful as ransomware, but also not as mild as pop-ups.
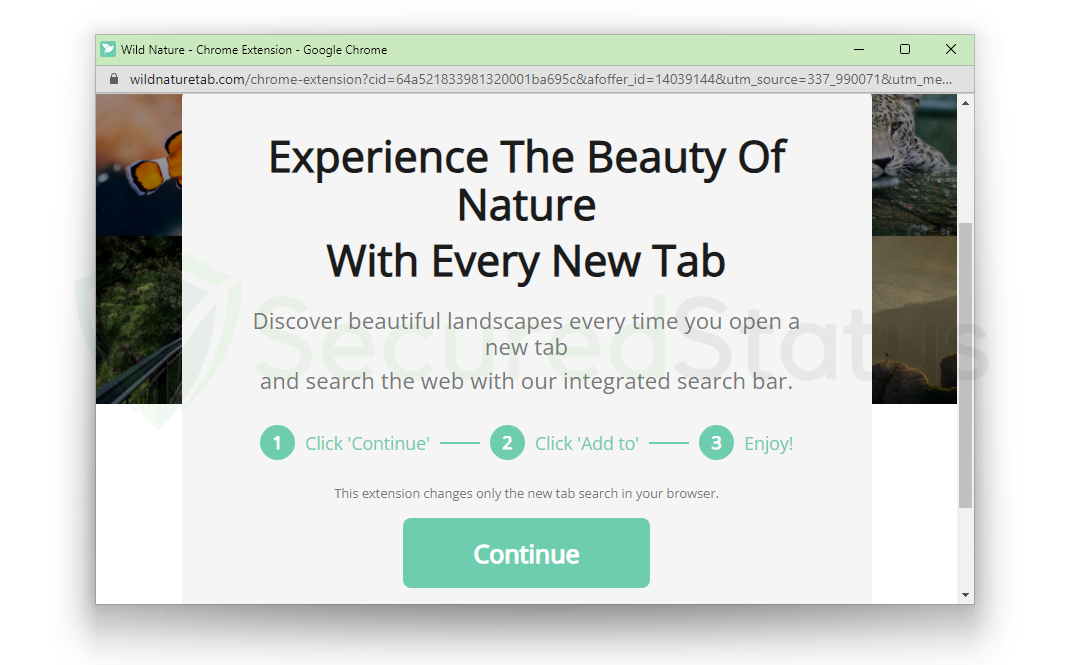
Malwarebytes must blacklist the aforementioned domains because one of those redirects might potentially result in a malware infection.
These redirections can range from plugin installations, adware downloads, and even malware executable installations and drive-by downloads.
Does it block pop-up advertisements?
Pop-up ads are very common on the internet, and allowing them to show notifications and alerts can be done with a single click, so having them blocked is a necessity for users who are not knowledgeable in using technology.
But how will we find malicious websites that cause pop-up advertisements? Simple, we will just do the same thing we do every time there is something we do not know: by searching for it.
We can easily identify websites that request push notifications as the source of pop-ups by searching for the term itself, which will automatically uncover websites that do so. See the image below for further understanding.
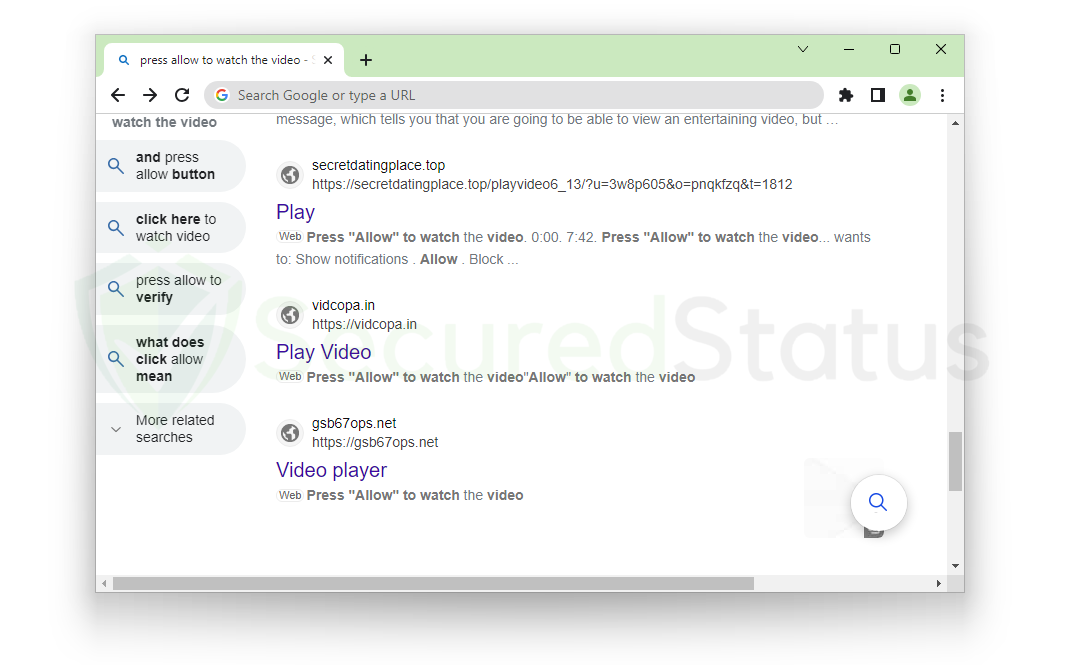
As seen from the image, the websites on the query results page of Bing are websites that will initiate pop-ups on the browser when given permission. We have initiated this test with all the pop-up websites that show up in the search query.
So when we click it, does it lead us to the website? The answer is… no. Malwarebytes blocked it due to excessive requests for notification permission, which is one of the main identifiers of these pop-up websites.
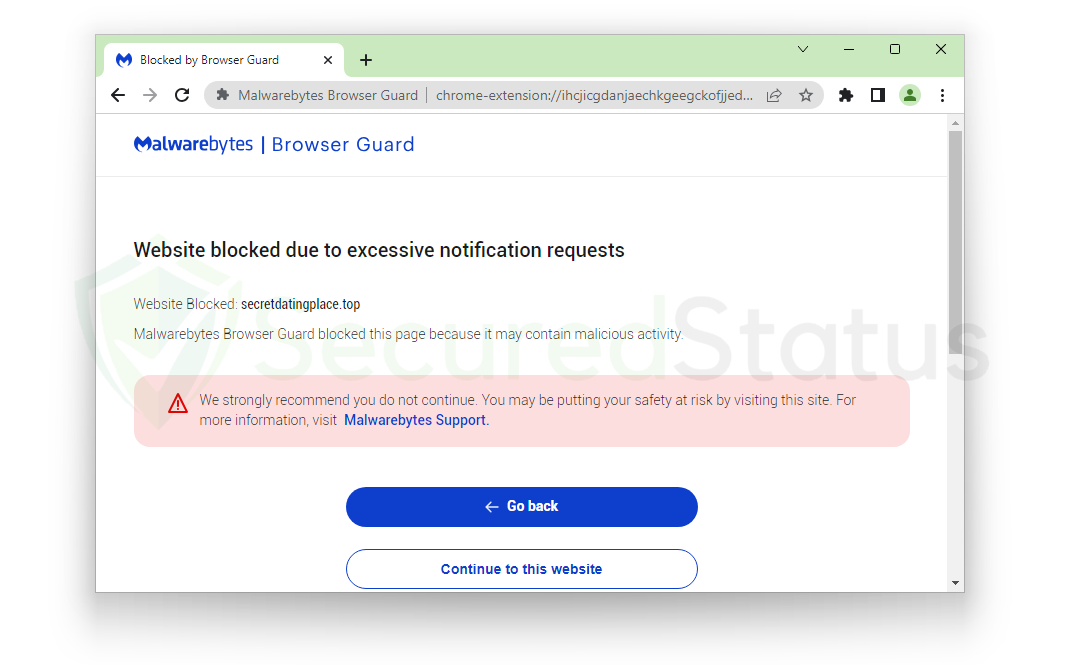
This leads us to the conclusion that Malwarebytes can automatically block dangerous websites that request permission for an excessive number of notifications. This is a clear indication that it can almost immediately block all websites that ask for permission repeatedly.
Pop-up advertisement websites require this to display alerts through the web browser, and if Malwarebytes can identify these websites that request it, the browser will be protected from them, and pop-ups won’t appear while the anti-malware is installed and guarding the device.
Now let us try a different approach. What will happen if the pop-ups are already permitted to show notifications? Does it block them then? Let’s find out. To do so, we will first disable both Browser Guard and the anti-malware and then grant the pop-ups permission without having them blocked at the initial stage.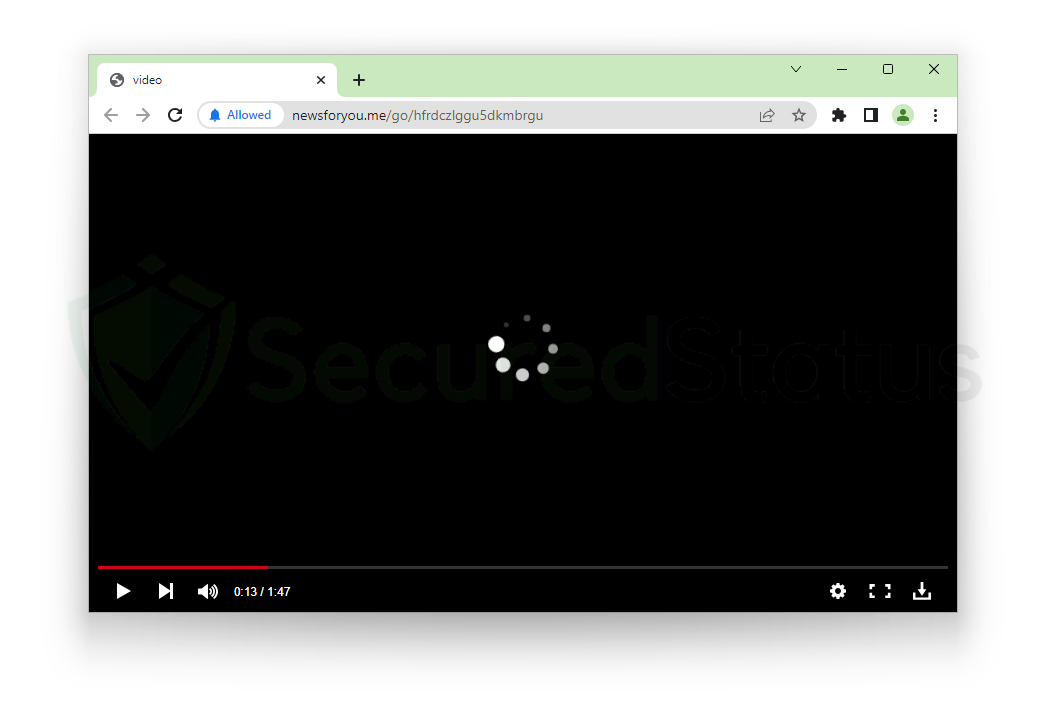 The pop-up was permitted by the browser, as can be seen in the image above. You now anticipate browser notifications to be displayed, correct?
The pop-up was permitted by the browser, as can be seen in the image above. You now anticipate browser notifications to be displayed, correct?
For the first few seconds, that would be the case, but as soon as I restarted Browser Guard and Malwarebytes Anti-Malware, every connection was blocked, and the pop-ups did not reappear.
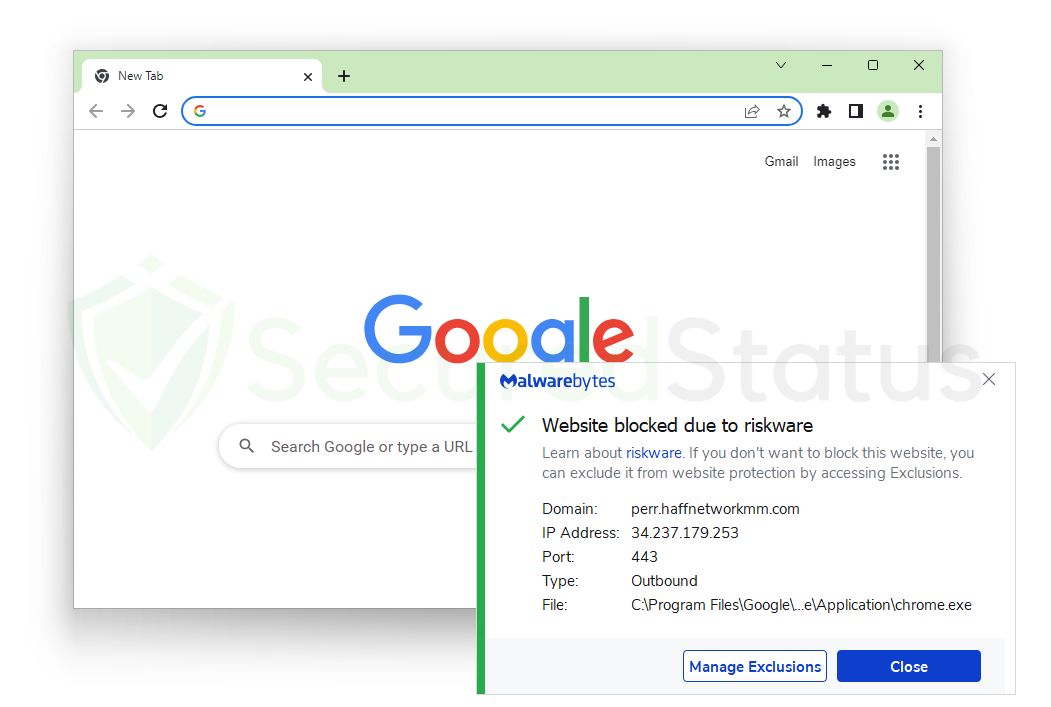
With websites related to pop-up advertisements blocked, users will no longer receive the irritating contents that come along when you click allow for it to show notifications.
However, you should note that activating Malwarebytes will surely block the pop-ups, but the permission to show notifications is still allowed on the browser, so you should head over to Site Settings and block the notifications manually to make sure they do not appear even when you uninstall the anti-malware.
chrome://settings/content/notifications
This can also be done by going to the following directory, as shown above. Click on the three dots near the unwanted site and select Remove.
How do Malwarebytes fare against computer threats?
Computer threats range from different variants of malware and computer viruses, so detecting them will require signatures and a database of their threats to find them.
Even though malware often comes into the computer via the internet, which can be blocked by both Browser Guard and the Anti-malware, some come in payload via injections on unknown software, but the connections from that can be blocked as well.
Malwarebytes will be put to the test in this scenario by utilizing malware that is regularly downloaded on the computer. We’ll see if Malwarebytes can identify the malware both during and after installation because doing so can stop the virus from spreading at all.
Malwarebytes vs. Crypto mining malware
We’ll be testing Malwarebytes against crypto mining malware using the most popular crypto mining program that hackers frequently employ to infect computers.
XMRig is widely used by hackers to trick users’ devices into mining cryptocurrency on their behalf. They will have configured the cryptocurrency to land in their wallets, and it’s important to remember that XMRig isn’t malware; rather, cybercriminals utilize it as a mining tool.
This app is used by miners as well, so if you are mining cryptocurrency with it, you are secure. However, if this app suddenly appears on your computer and it has been lagging ever since, your device is probably being mined.
Starting, we won’t be getting the XMRig application straight from their main website; instead, we’ll be downloading it using payloads that contain malware that has been set up to install XMRig and was created by cybercriminals instead.
Now that we have a sample of the XMRig malware, it appears that Malwarebytes is unable to recognize the malware once it has been downloaded into the system at hand.
But as can be seen from the image below, the anti-malware was able to discover it after scanning. It reports that a BitcoinMiner.Trojan.Miner.DDS with the same name as those on the desktop has been found.
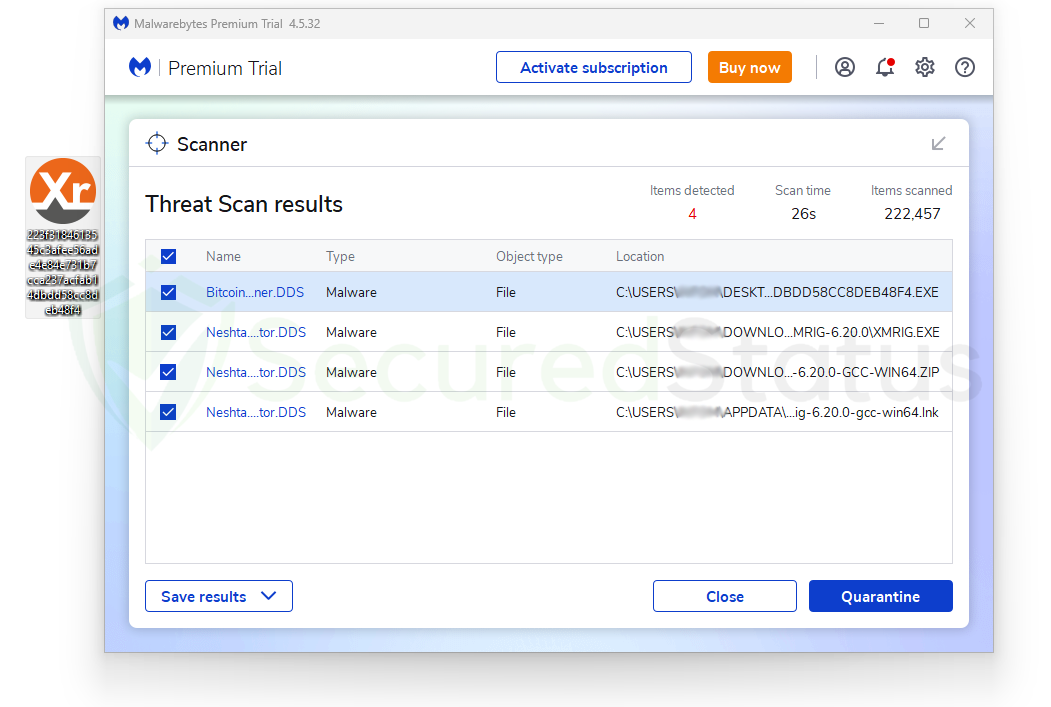
Users without Real-Time Protection must manually scan for malware before Malwarebytes can detect it; if Real-Time Protection is activated, it will scan it automatically on the subsequent routine scan.
Additionally, even if we attempted to run it from the computer without first scanning it, it would still prevent us from doing so. As a result, even without scanning, it is ultimately unable to run.
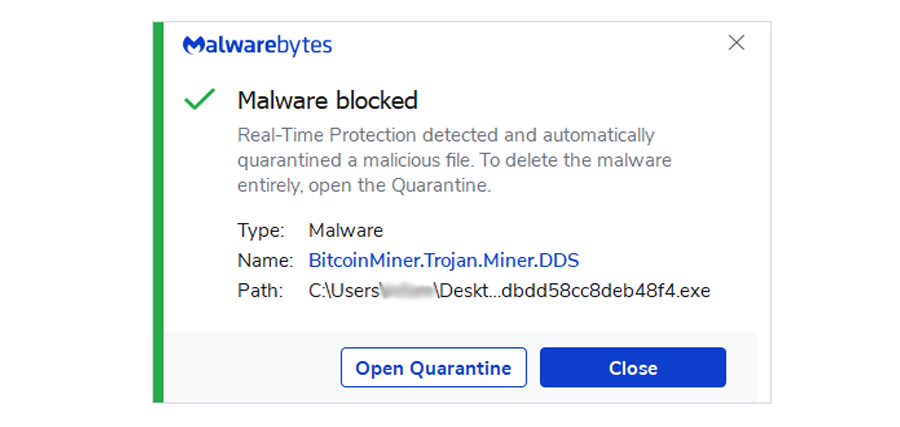
It has stopped the miner virus that we had on the computer’s desktop, as can be seen in the image above. This ensures users that such threats will not be able to run from the computer.
Now, what would happen if we turned off Malwarebytes first, let the miner run, and then turned it back on?
For this test, we will have to first deactivate Malwarebytes and run the miner program on the computer for a few seconds to a minute before running a Malwarebytes scan to make sure the malware has loaded and run successfully.
Now let us begin running the maliciously configured XMRig malware, and we will test it by running a malware scan rather than relying on Real-Time Protection and see how it goes.
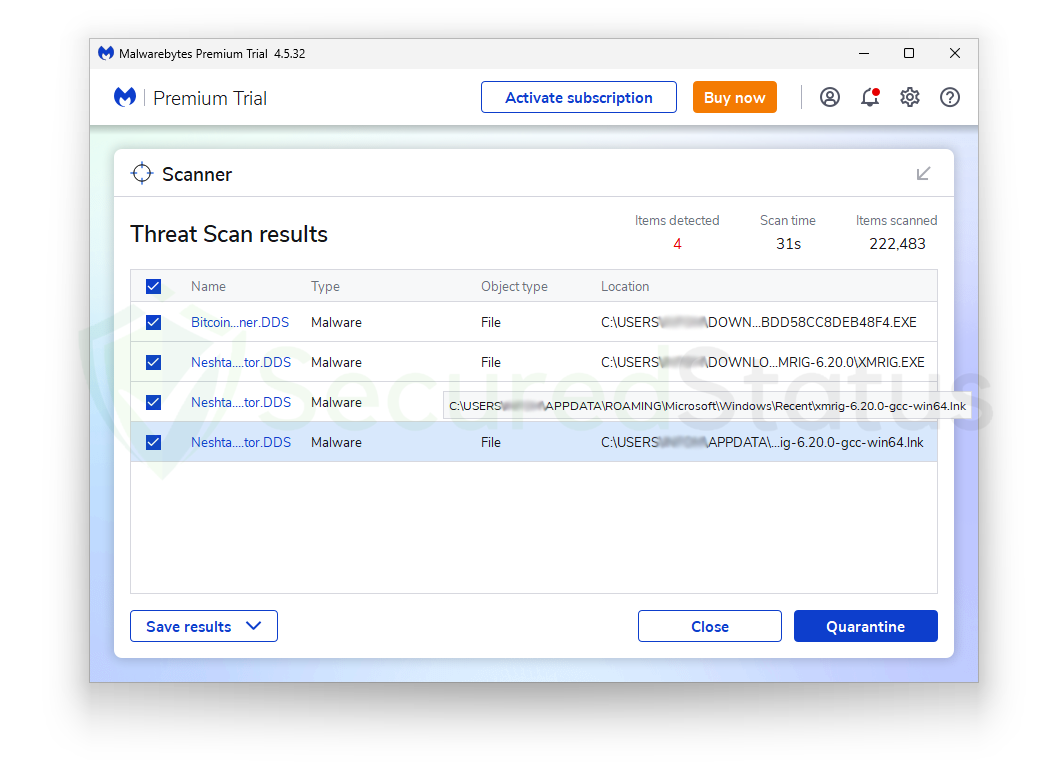
As can be seen from the image above, it has discovered the malware once more because it has different file locations from the prior scan.
We can infer that it can delete and stop harmful miner malware from the computer because it has discovered new places where malware has been dropped.
Protection against trojan viruses
Even if Malwarebytes is an anti-malware, the terms of an antivirus and the latter are probably the same, so it can additionally identify such dangers on the computer. Trojan malware is a serious type of malware and is classified as a virus.
For this test, we will be utilizing RedLine Stealer, AgentTesla, Formbook, LokiBot, and other known trojan viruses in the test environment to see if Malwarebytes can detect them.
As expected, it was able to detect the malicious malware on the computer yet again. We have tried to run it first and then scan it without running the file to check if both can be detected.
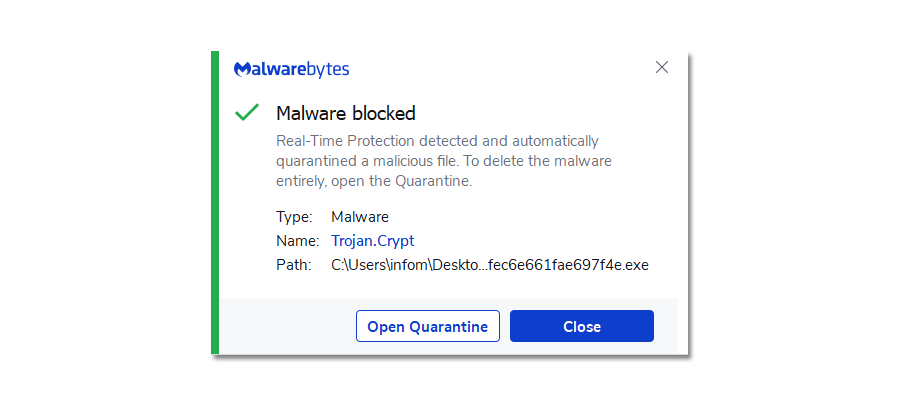
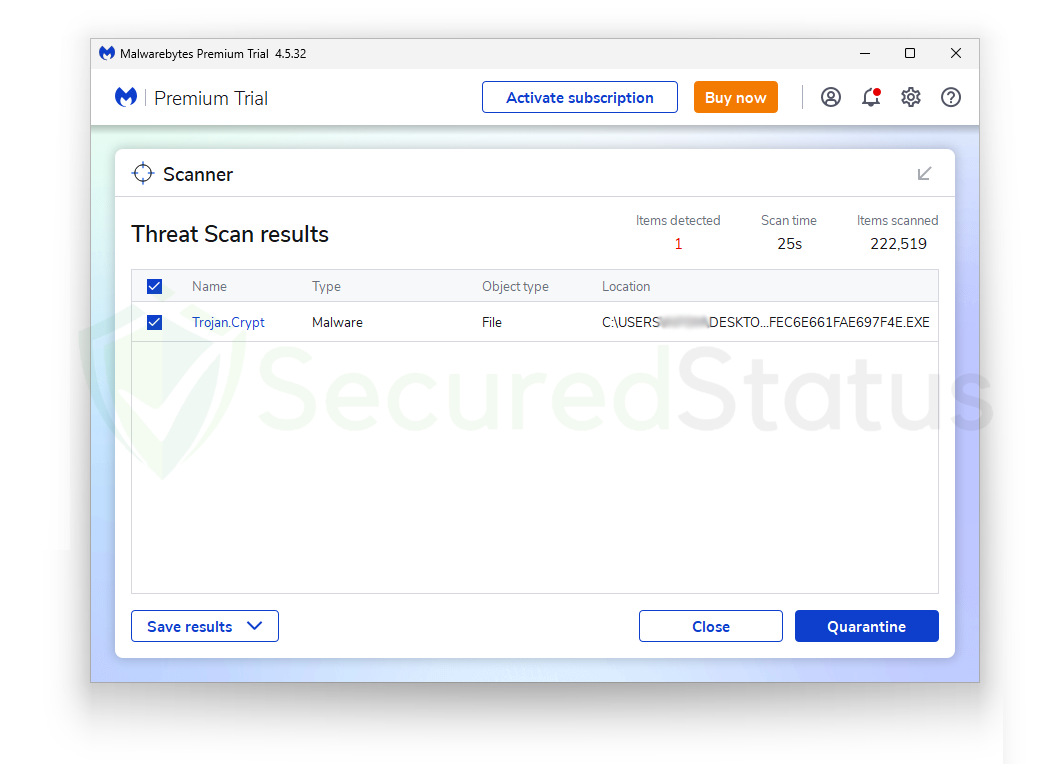
The same may be stated for the other computer-running trojan viruses. Please take note that Malwarebytes was able to identify newly created malware because the following malware samples were the most recent ones that could be located online.
The image above shows just a fraction of the malware threats we loaded onto the computer when we first started our search. The majority of the early malware that we have examined has been detected and removed by Malwarebytes.
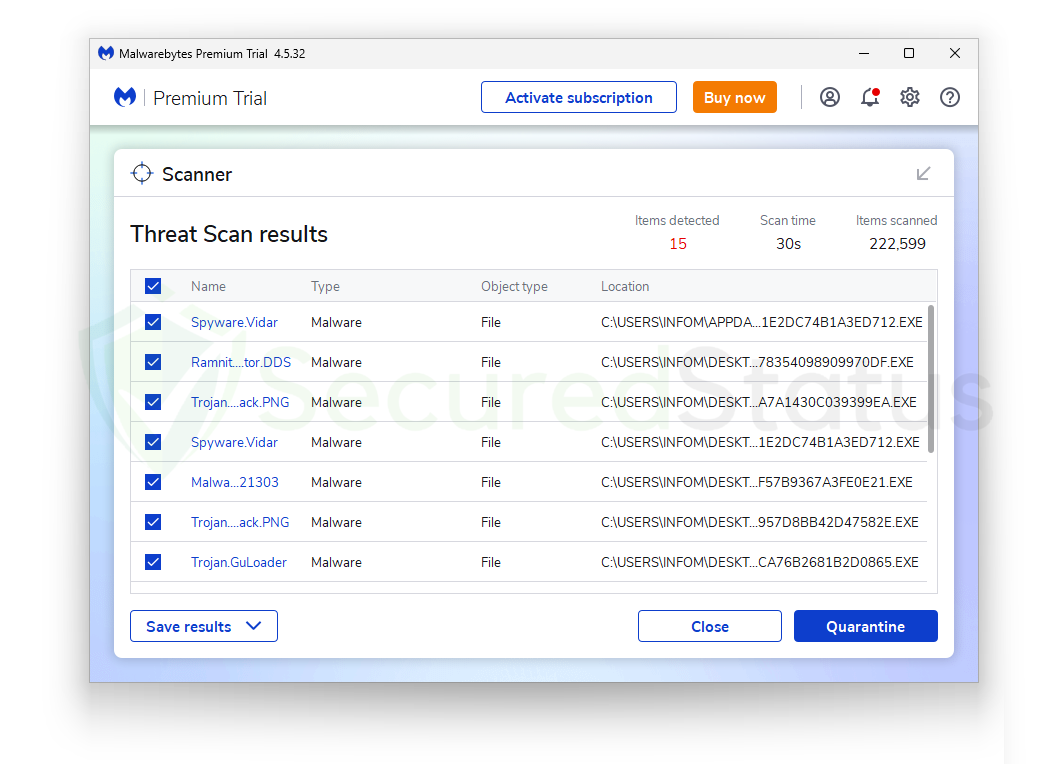
However, those were not the only trojan viruses we tested with the application; because we cannot simply provide all the images in one article, we tested it with 200 live malware and created a data table about the detections of the threats, which is shown below.
| Trojan Virus | Total Threats | Detected Threats | Undetected Threats | Detection Percentage |
|---|---|---|---|---|
| Coin Miners | 20 | 19 | 1 | 95% |
| RedLine Stealers | 16 | 16 | 0 | 100% |
| RemcosRAT | 9 | 8 | 1 | 88.9% |
| FormBook | 18 | 16 | 2 | 88.9% |
| AgentTesla | 50 | 45 | 5 | 90% |
| DCRat | 12 | 12 | 0 | 100% |
| Amadey | 15 | 14 | 1 | 93.3% |
| ObserverStealer | 4 | 3 | 1 | 75% |
| RaccoonStealer | 24 | 22 | 2 | 91.7% |
| LokiBot | 26 | 24 | 2 | 92.3% |
| IcedID | 6 | 5 | 1 | 83.3% |
Malwarebytes’ overall detection rate after gathering everything is 92%, which is fairly respectable for an anti-malware application.
Viruses from pirate sites and cracked files were utilized to collect the data. We categorized them with the aid of Any.run, which displays malware classification alongside the detection provided by VirusTotal security vendors.
We avoided using malware samples and sources that were used in past tests because that would prove there was no point in using research that was already done.
There are hundreds more malware variations, but because we focused on threats that are constantly encountered online, that is why there are only a few variants.
This particular test is accomplished by manual scanning rather than Real-Time Protection because we can’t be certain that every user will purchase the paid version at some point; instead, we concentrated on what they can expect from the free version.
Naturally, the premium product will perform better because it will automatically block connections from payloads and ultimately stop threats from being downloaded in the first place.
How it protects against potentially unwanted applications
Users may obtain potentially undesirable applications or programs from third-party application installers, where something is bundled with the software they wish to download.
Since many users download from these unsecured sites, cybercriminals often inject dubious programs or adware into them; this is most likely the case with illicit torrenting applications and cracked software downloads.
For this case, we will first try and install some rogue applications, such as PC Accelerate Pro, as many users have been seeing these on their computers.
To make things simple, we attempted to install the application from its main website. However, as soon as the website was attempted to be browsed, Malwarebytes immediately canceled the connection. Ensuring that you will have no opportunity to install it at all.
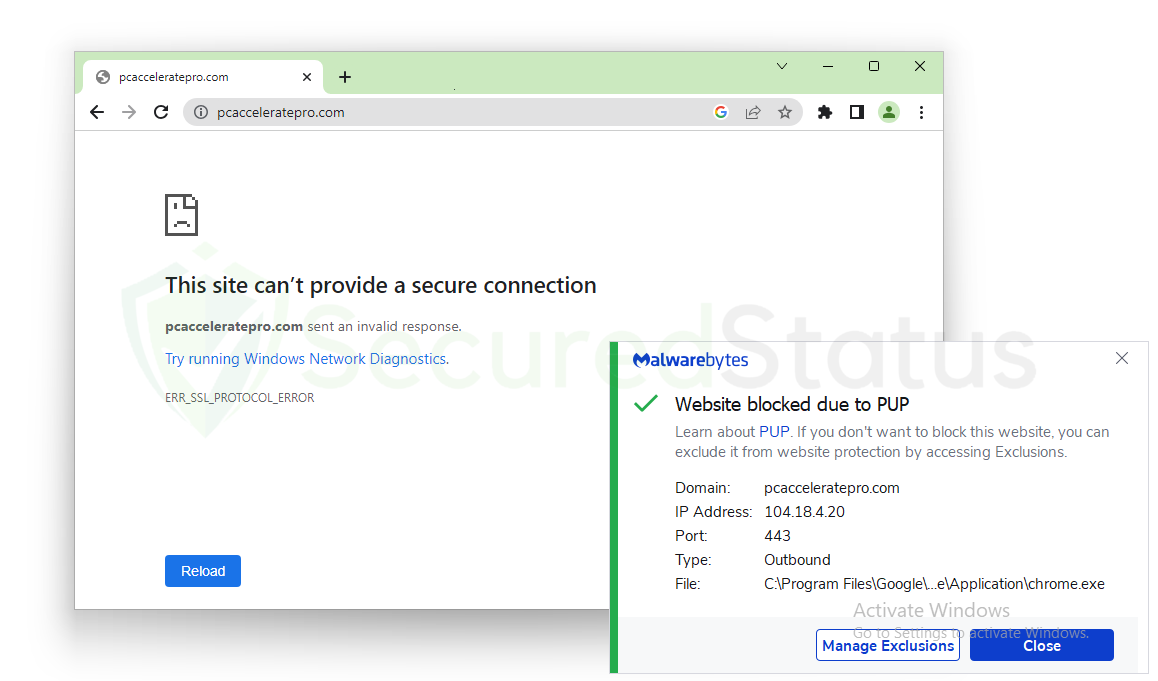
Since Malwarebytes has this application in its database and it has been identified as a PUP, let’s try another rogue program to see whether Malwarebytes can identify it.
We tested it and discovered that Adaware WebCompanion is something that Malwarebytes initially misses because the website was reachable and you could download the malware without Malwarebytes preventing it.
Even though the executable file could be downloaded, it was impossible to run the software after downloading it because the connection to the installer was cut off, preventing it from opening.
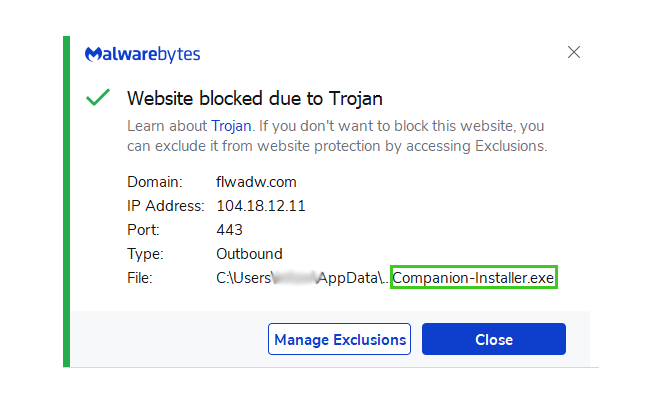
It seems to be blocking any applications that it deems to be unwanted, which should be the case as it is needed for users’ protection.
Additionally, we have downloaded and attempted to install other undesirable apps like GCleaner and reputable programs that bundle unwanted applications with their installation. We permitted them to install the included programs, and the outcomes are as shown below.
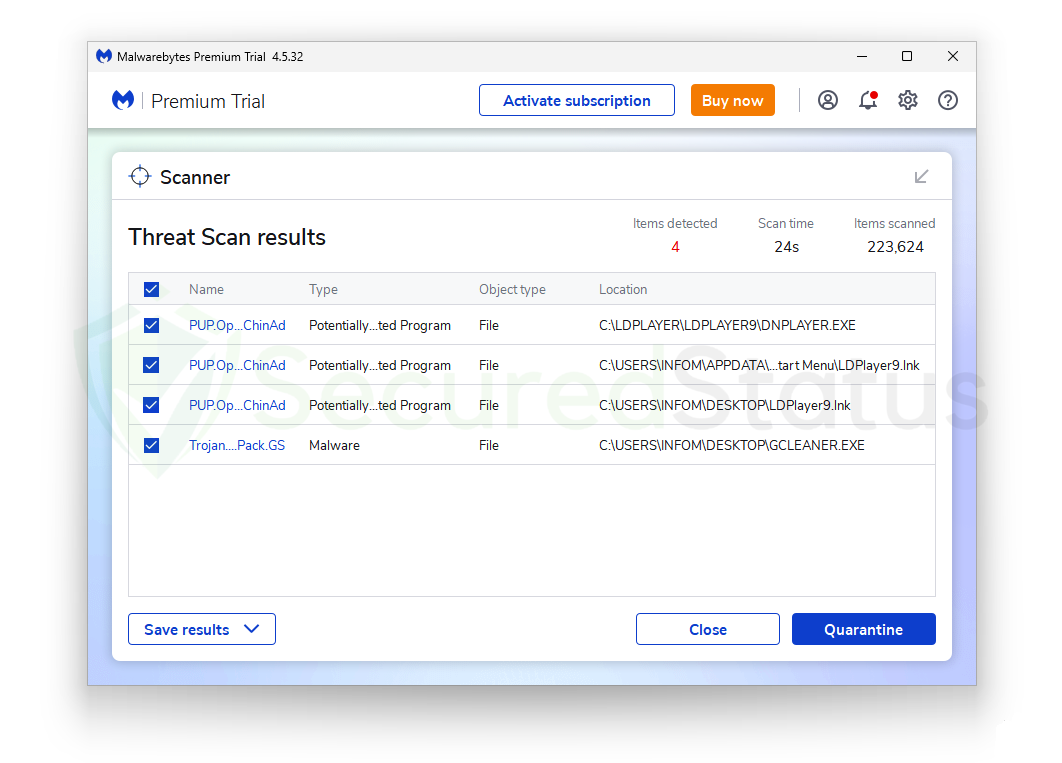
LDPlayer, which is by no means an unwanted program but installs bundled programs along with their primary program, was also detected. Malwarebytes picked this up since it happens when bundled applications are installed alongside the main program.
This will be the case with other programs that also offer bundled programs upon installation, so you can be assured that PUA and adware will not be installed on your computer as long as Malwarebytes is installed.
Bottom Line
You now understand why Malwarebytes is recommended as a program for eradicating all varieties of malware thanks to the information we have provided in this article. It can detect threats before they are downloaded, during installation, and even after malware has already been started and installed on a computer.
With that being said, if you’re interested in giving Malwarebytes a shot for your computer’s security, click on the button above. As can be seen from the tests, it performs well on the latest malware found in the wild and will continue to be effective for years to come.
