Installing applications and programs from unidentified or unverified sources poses a significant risk to your computer’s security.
It’s essential to be cautious as such actions can lead to the inadvertent installation of adware and potentially unwanted applications (PUA). These malicious entities can have detrimental effects on your system and compromise its safety.
Adware refers to software that displays unwanted advertisements, often in an intrusive manner. Once installed, it inundates your computer with pop-up ads, banners, and other promotional content, disrupting your browsing experience and potentially exposing you to further security risks.

Adware can also track your online activities, collect personal information, and share it with third parties without your consent.
Similarly, PUAs encompass a wide range of applications that may exhibit undesirable behavior or possess hidden malicious functions.
These programs often bundle themselves with legitimate software or disguise themselves as helpful utilities, tricking users into installing them.
Once on your computer, PUAs can cause various issues, such as slowing down system performance, modifying browser settings, redirecting web searches, or even harvesting sensitive data.
Removing adware and PUAs can be challenging, as they are designed to evade detection and resist traditional uninstallation methods.
They may leave behind residual files, registry entries, or employ deceptive tactics to regenerate themselves. Additionally, some PUAs employ rootkit techniques to hide their presence deep within your system, making them even more difficult to eradicate.
To safeguard your computer and mitigate the risks associated with adware and PUAs, you may follow the methods we have provided below.
How to Avoid PUP/Adware From Being Installed
Our team has attempted and tested each of the techniques listed below because this issue may have numerous primary causes. Try the following one if the first doesn’t work for you until the issue is resolved.
Method 1: Install Malwarebytes Anti-Malware to Automatically Block Incoming PUA
Utilizing antivirus software is the simplest and most effective method to prevent the installation of potentially unwanted applications (PUAs) and adware.
When an installation program attempts to install such programs, Malwarebytes, a trusted antivirus solution, will automatically block them.
By employing Malwarebytes or similar antivirus software, you create a robust defense against the infiltration of PUAs and adware.
These security tools continuously monitor your system for any suspicious activities, including unauthorized installations or attempts to modify critical settings.
When an installation program initiates the setup of a PUA or adware, Malwarebytes swiftly intervenes, preventing their installation from proceeding.
This proactive approach ensures that your computer remains protected against these potentially harmful entities, safeguarding your system and personal data.
 They also have some of the greatest threat detection software, ensuring that any unwanted threats on your computer are totally eliminated.
They also have some of the greatest threat detection software, ensuring that any unwanted threats on your computer are totally eliminated.
How to Run a Malware Scan with Malwarebytes:
- Visit the antivirus website or click the button above to download the most up-to-date version of the software that best suits your requirements.
- Follow the software installation instructions until they are completed.
- Run a complete malware scan on the machine and wait for it to finish.
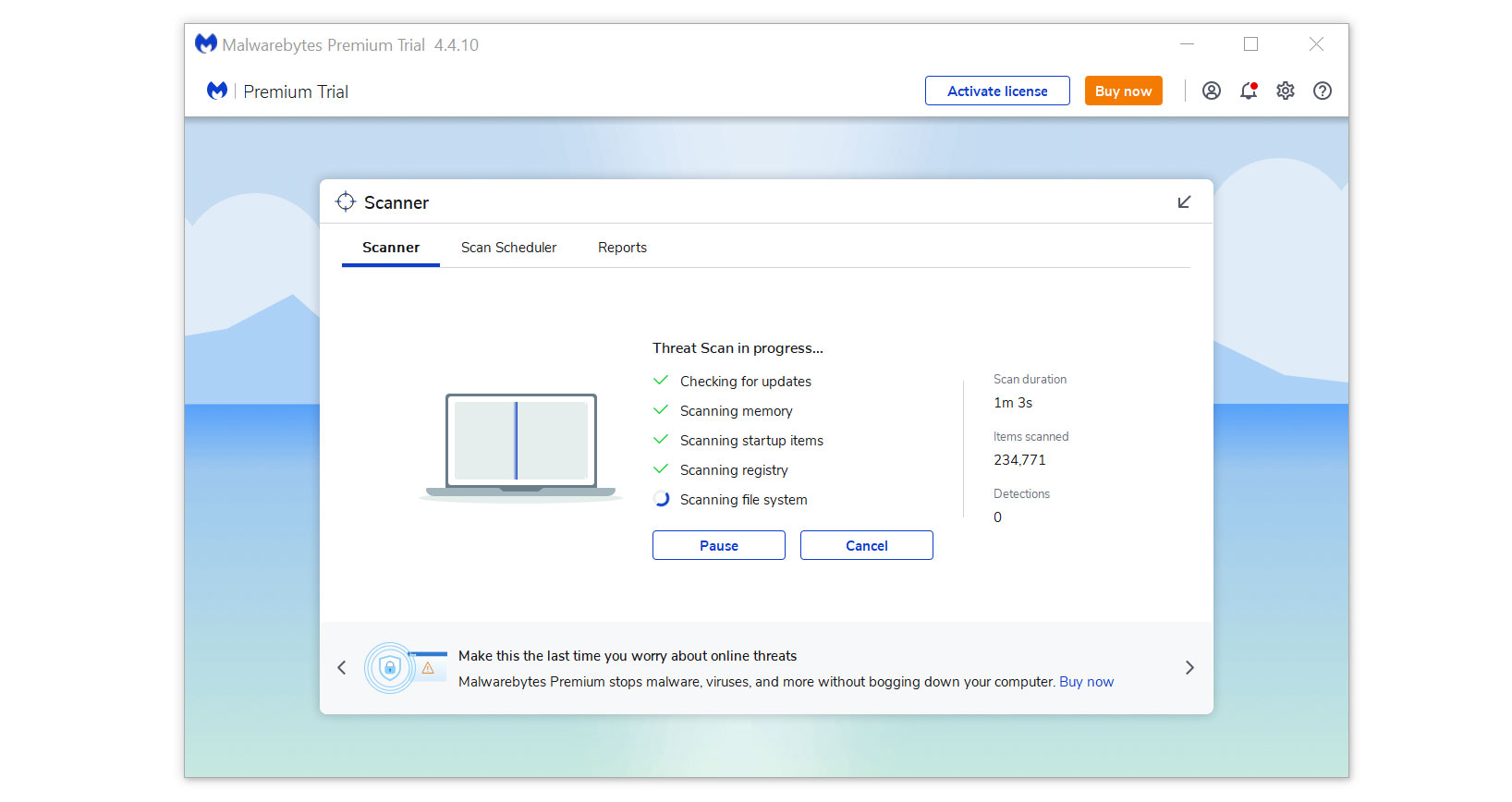
- All the detected threats found on the computer will be shown on the screen and clicking the “quarantine” button to remove them.
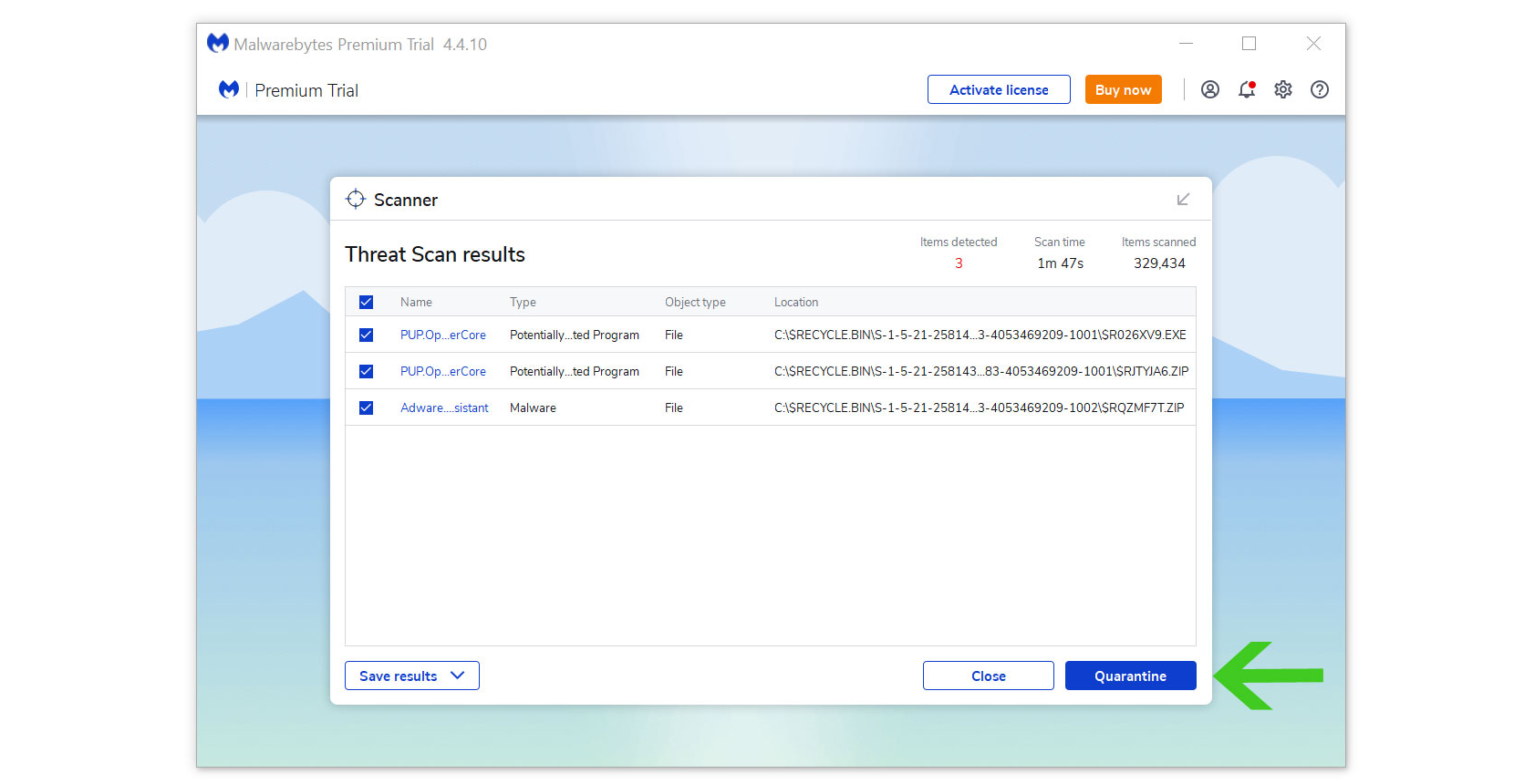
While uninstalling Malwarebytes will disable Windows Defender Real Time Protection, following the removal of Malwarebytes, you can follow this article to reactivate it again.
Alternative: Kaspersky Antivirus
If you frequent several forums and websites, you will always see the majority of people concurring that Kaspersky is among the top antivirus programs on the market.
You may also try Kaspersky Antivirus other than Malwarebytes should you choose the later application.

Since each antivirus application has its own threat database, Kaspersky’s detection technology may be able to find PUAs that the prior program may possibly miss. Additionally, if this is your first time downloading the application, you will get a 31-day premium trial.
How to Run a Malware Scan with Kaspersky
1. Download the Kaspersky Security Cloud by clicking the button above.

2. Once the setup has finished downloaded, open the file and start the installation.

3. Wait until the wizard finds the latest version of the application or click Skip to install the current version stored.

4. Review the License Agreement. If you agree to its terms, click Continue.

5. Follow the installation instructions as shown then finally click install. (You may choose to uncheck the options shown if you do not want those features.)

6. Wait for the application to finish installing, then after the process is complete, click done.

7. Apply the recommended settings then start the application by clicking apply. Feel free to untick the options you do not desire.

8. You will be prompt to create an account and once you are finished, you will be redirected to the main screen. Select the Scan tab then click the run full scan and wait for it to complete.(Before scanning, we recommend you update the database to ensure any new malware variants are detected.)

9. After the scan has finished, the detected threats will be deleted from the computer.

Step 2: Find and Remove Possible Malware Program
PUAs and adware applications can potentially be installed by existing programs on your computer. Certain programs have the capability to install additional applications, which may include adware.
Consequently, if you have any programs from unfamiliar or unknown developers, it is advisable to uninstall them to prevent the sudden installation of unknown applications.
You may locate the program by utilizing the Task Manager and finding suspicious applications that are currently running when you are facing the browser hijacker symptoms.
Remove Program via Control Panel

- Search Control Panel in the Windows search bar then click it.
- The Control Panel should open, from there click Programs then Programs and Features.
- A list of installed software will show on the screen after a moment.
- Scroll down and find suspicious applications then right click the application and select Uninstall.
Utilize Revo Uninstaller
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a very useful tool for Windows users.
This uninstaller not only removes programs from the computer but it also deletes their changes from the Windows Registry, Host File and etc.
- Click the button above and download the latest software that is compatible with your system.

- Open the downloaded file and it should guide you through the setup.
- Follow the installation procedure and wait until the installation of the software is complete.
- After the installation is finished, tick the box that says Launch Revo Uninstaller then click finish.
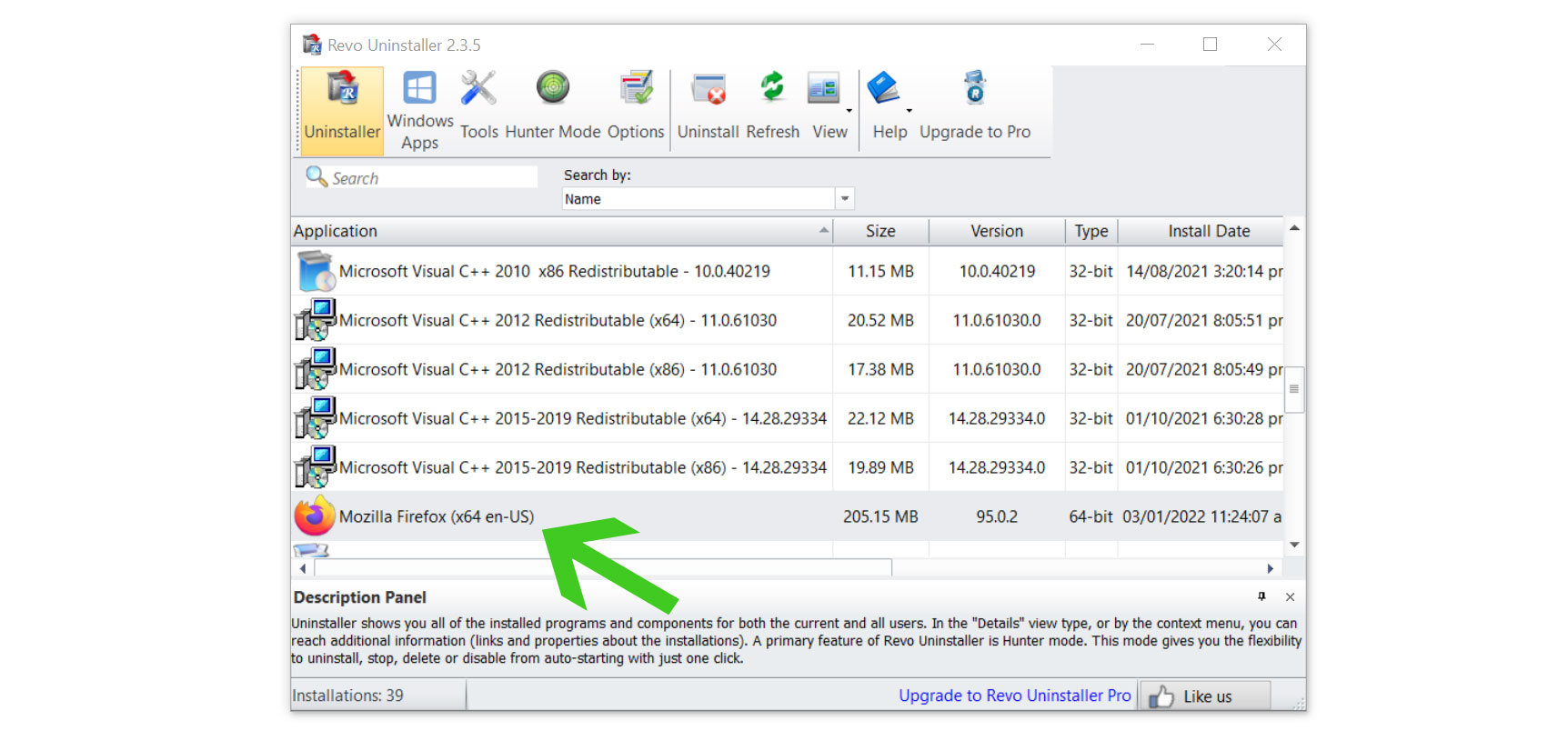
- Once the software has launched, find the unwanted application that is needed to be removed, double click the program to uninstall.
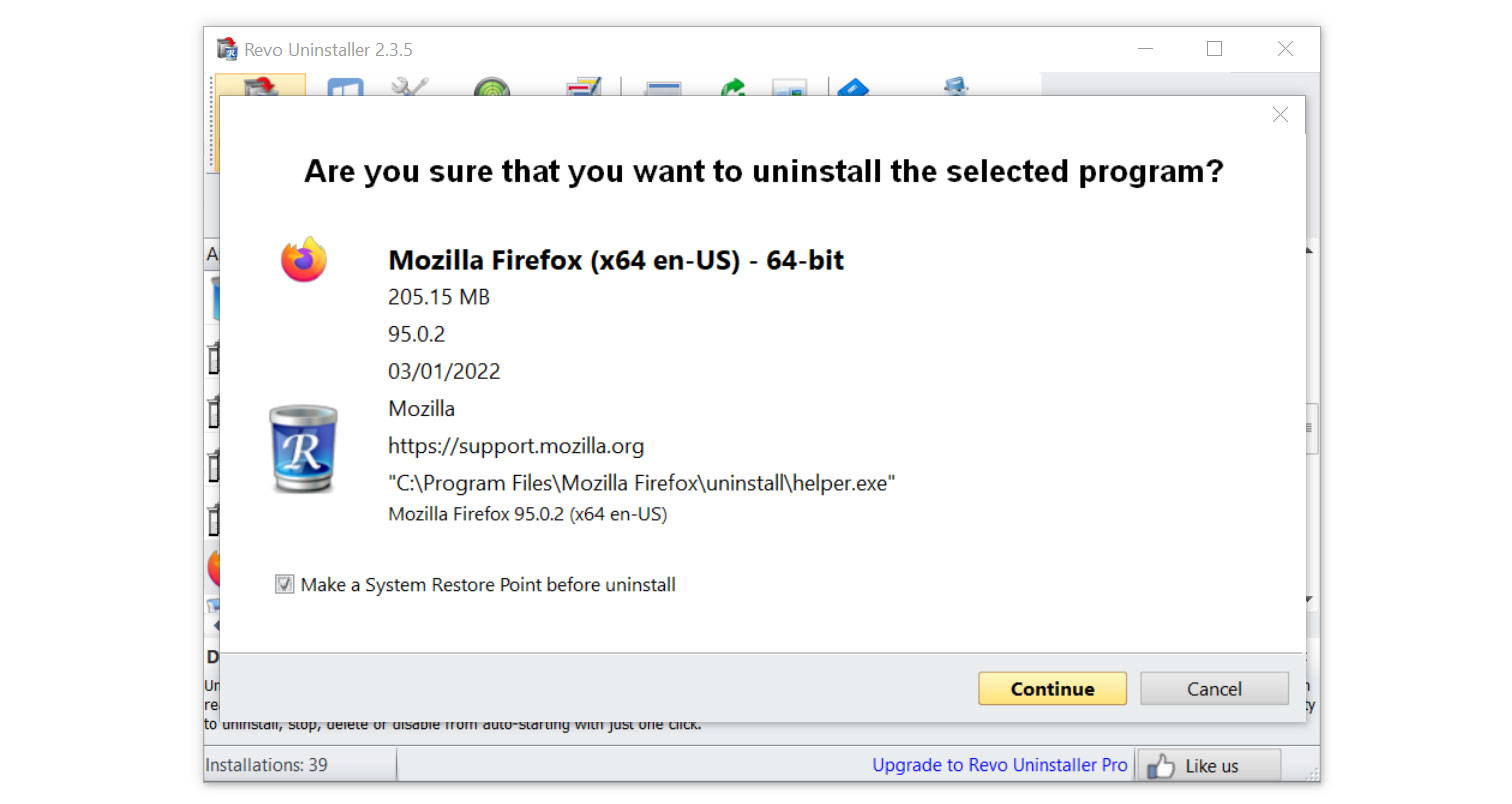
- Click on the Continue button and follow the procedure to start uninstalling the program.
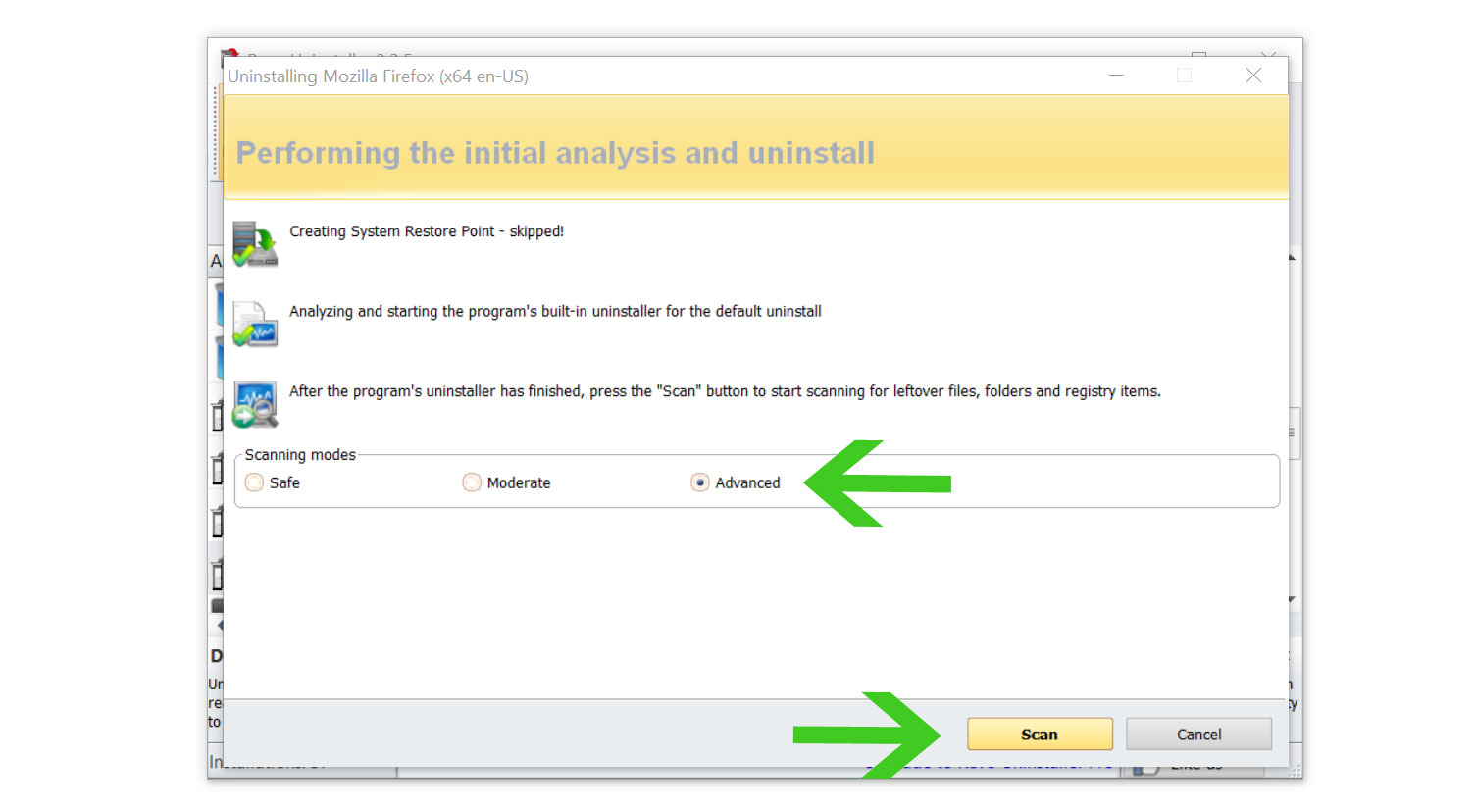
- Once it is uninstalled, a window will pop-up. Select the Advanced option for the scanning mode then click Scan to find remnants of unknown applications.
- A window will pop-up and show all of the leftovers and changes made by the program uninstalled a while ago.
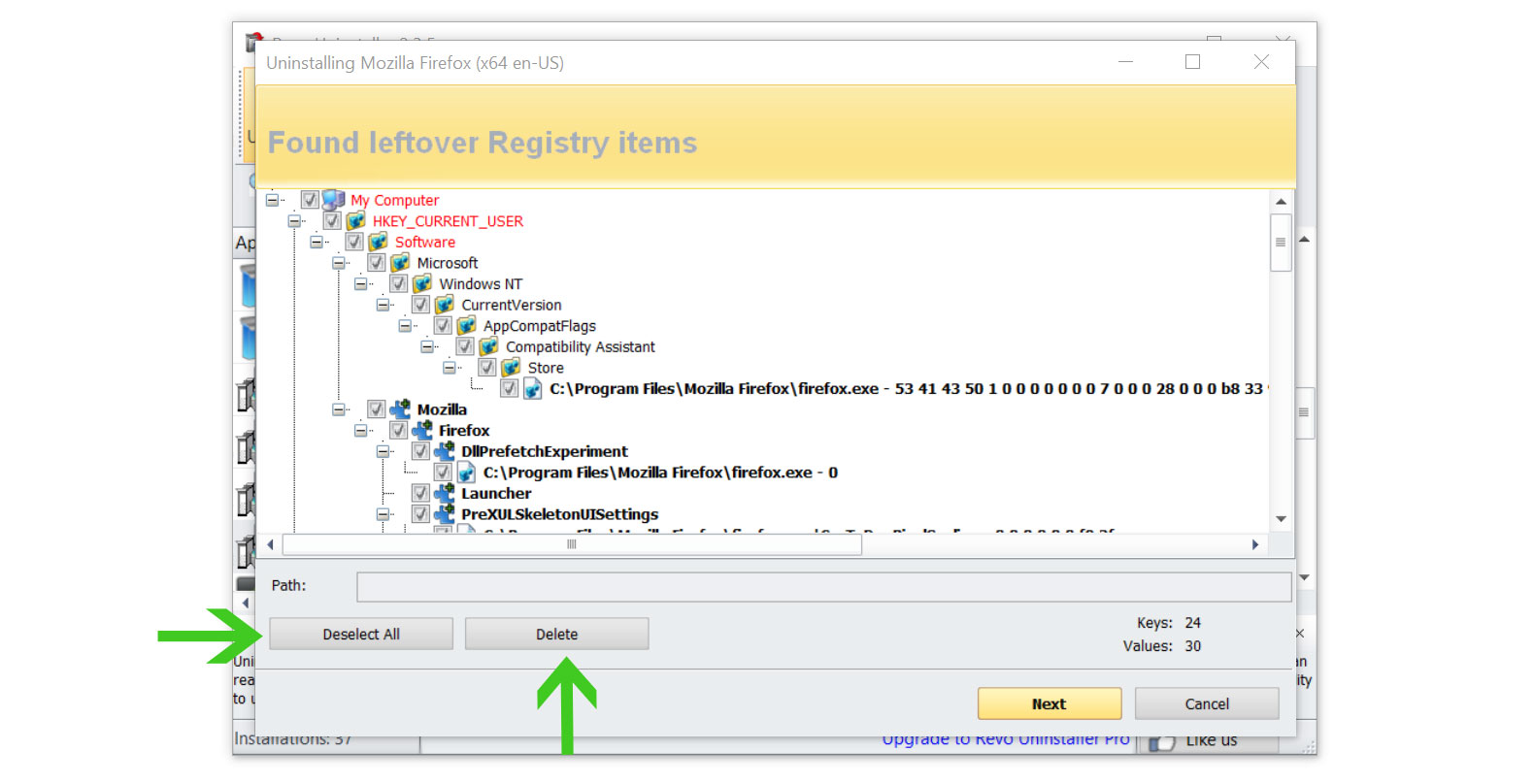
- Click the Select All button and hit Delete to remove the leftovers found on the Windows Registry.
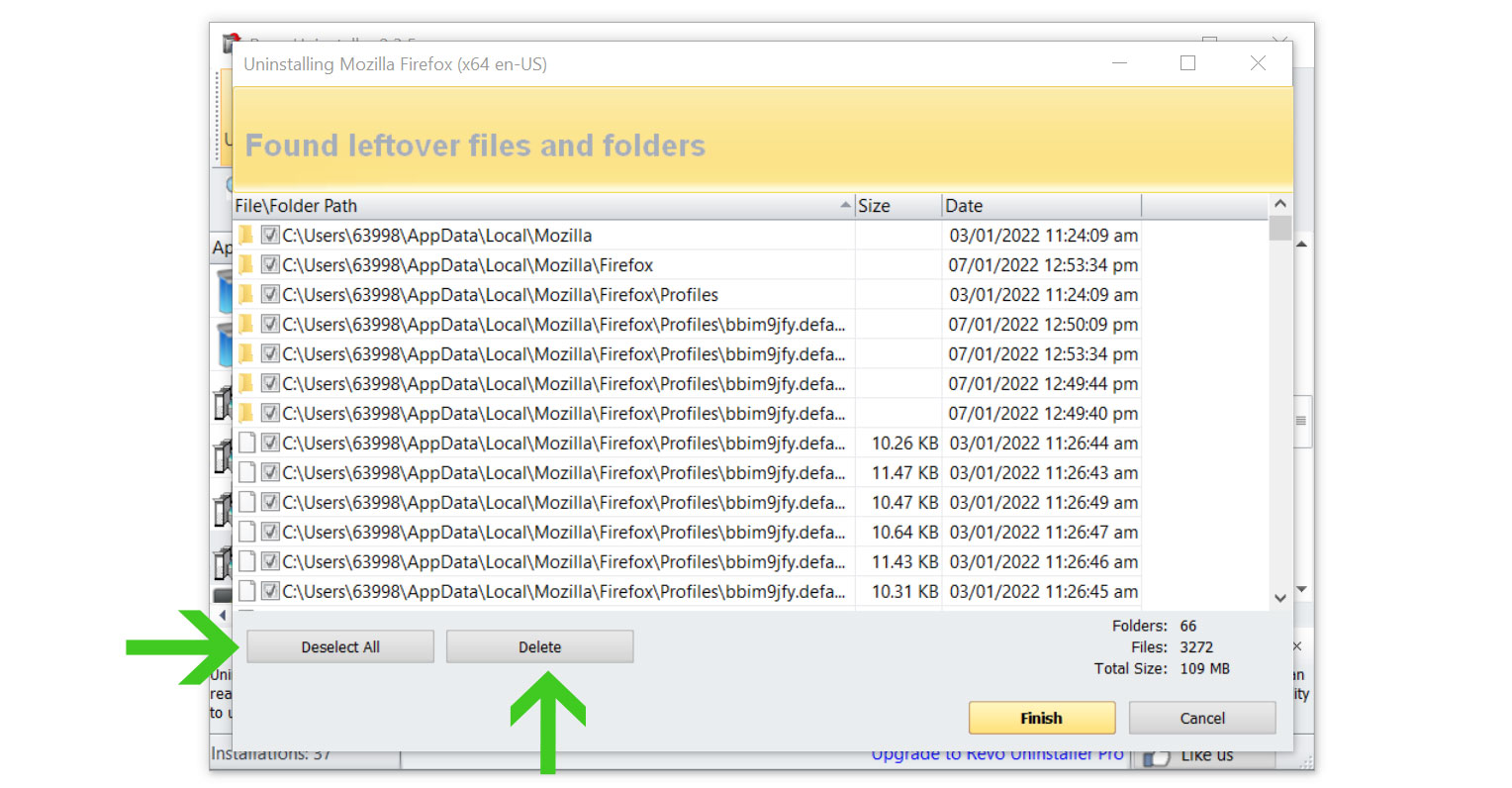
- Some leftover files may be found, click Select All then Delete them as well.
- Once the window closes, you have successfully removed the adware threat from your system.
Simple tips to be safe online
- Never acquire software or programs from unknown sources, as this is one of the most common ways for adware and other types of malware to attack your computer. Only download from reputable and legitimate websites. To be safe, stay away from torrent downloads and cracked software download sites, as there will always be malware in the files.
- Using a firewall is one of the most foolproof ways to be safe online. It serves as a first line of defense against dangerous websites, shielding visitors from potential risks. It protects the user’s network and device from intruders. A firewall will safeguard a user from the threats hiding on the vast internet in today’s age.
- It is essential to keep anti-virus software up to date on a computer since hundreds of new malware threats are released every day that target the machine’s vulnerabilities in order to infect it. Anti-virus updates include the most recent files required to counter new threats and safeguard your machine.
- Only visit websites that has a secured connection. A site with HTTP connection does not encrypt the data it receives and therefore is not considered secure. Entering personal information such as email addresses, phone numbers, and passwords on a website with an HTTP connection is risky since it could be compromised and your information stolen. Websites with HTTPS connections, on the other hand, are secure since data is encrypted and attackers are unlikely to gain access to information exchanged within the site.
- Backups are critical for ensuring the safety of your data. Without a thorough backup of the data, several computer dangers and irreversible damage can arise. Backing up your data is a crucial step in ensuring the safety of your information. Having a backup copy of the system and data will be extremely useful in the event of a harmful malware attack.
