Fractureiser, a malicious software, has emerged as a significant concern within the Minecraft modding community. This malware, discovered in various Minecraft mods, has been spreading uncertainty among users, prompting security experts to take notice.
The Fractureiser malware has recently been found infecting both Windows and Linux systems, using the CurseForge platform as its primary distribution channel.

Bitdefender, a renowned cybersecurity company, has recently shed light on the Fractureiser malware. In an informative blog post, they outlined the prevalence of this threat and its connection to Minecraft mods.
This discovery has raised awareness within the gaming community and highlighted the importance of maintaining vigilance while downloading and installing mods from unofficial sources.
Fractureiser Exploiting CurseForge
The latest reports suggest that Fractureiser is leveraging the CurseForge platform to propagate its malicious activities. CurseForge, a popular marketplace for Minecraft mods, has unwittingly become a breeding ground for this insidious malware.
It is imperative for users to exercise caution and only download mods from trusted sources or official repositories to minimize the risk of infection. Fractureiser has shown a notable ability to target both Windows and Linux operating systems.
Its cross-platform capabilities allow it to exploit vulnerabilities in these environments, potentially compromising users’ sensitive data and system integrity.
Utilize Antivirus to Remove Fractureiser Malware
To ensure the safety of your computer from the Fractureiser malware, it is crucial to run thorough scans using reputable antivirus software. Perform both full system scans and targeted scans to check for any threats.
In this case, we recommend Malwarebytes Anti-malware. This program is one of the most effective anti-malware programs available.
They have some of the greatest threat detection software, ensuring that any unwanted threats on your computer are totally eliminated.

You can utilize this antivirus program to complete the task since it was this program that detected the malicious threat. Furthermore, even if you think malware is completely removed from the computer, we recommend that you run a complete scan just in case.
1 Visit the antivirus website or click the button above to download the most up-to-date version of the software that best suits your requirements. For mobile devices, download the application from the Google Play Store or Apple App Store.

2 Follow the software installation instructions until they are completed.
3 Run a complete malware scan on the machine and wait for it to finish.
4 All the detected threats found on the computer will be shown on the screen and clicking the “quarantine” button to remove them.
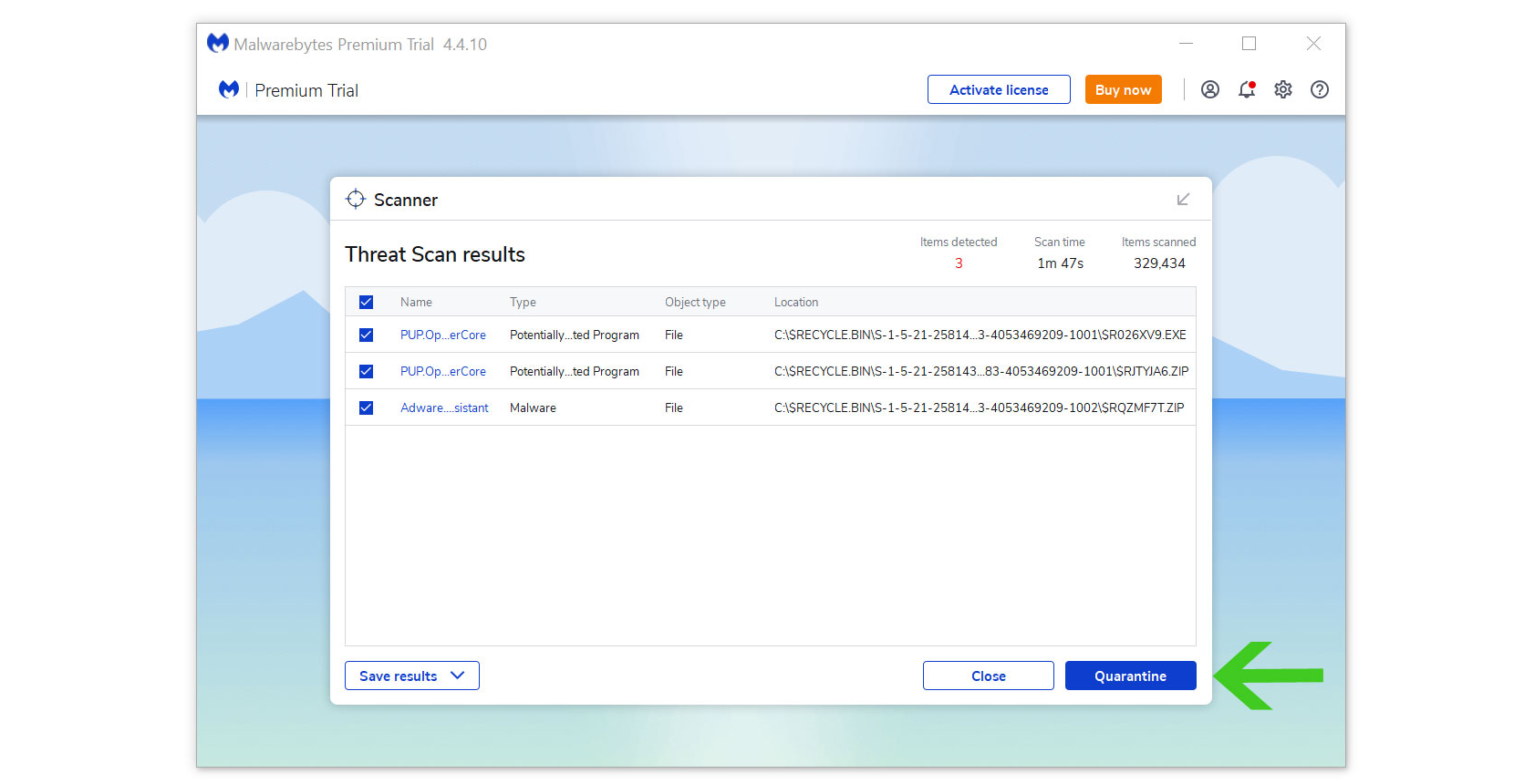
Any other harmful viruses discovered on the computer, should be eliminated once the process is complete. We also recommend to use Malwarebytes Real Time Protection, which will secure your machine and detect any threats as soon as they appear.
Alternative: Kaspersky Antivirus
There are instances where a different antivirus can find something another antivirus cannot. In this situation, if the first antivirus program didn’t work, we advise doing a scan with a different one.
If you visit numerous forums and websites, you will see most users agree that Kaspersky is one of the best antivirus tool available.

Since each antivirus application has its own threat database, Kaspersky’s detection technology may be able to find viruses that the prior program missed.
To ensure sure viruses are removed from the system, we advise running a scan just in case. If you are downloading the application for the first time, you will also receive a 31-day premium trial.
1 Download the Kaspersky Security Cloud by clicking the button above.

2 Once the setup has finished downloaded, open the file and start the installation.

3 Wait until the wizard finds the latest version of the application or click Skip to install the current version stored.

4 Review the License Agreement. If you agree to its terms, click Continue.

5 Follow the installation instructions as shown then finally click install. (You may choose to uncheck the options shown if you do not want those features.)

6 Wait for the application to finish installing, then after the process is complete, click done.

7 Apply the recommended settings then start the application by clicking apply. Feel free to untick the options you do not desire.

8 You will be prompt to create an account and once you are finished, you will be redirected to the main screen. Select the Scan tab then click the run full scan and wait for it to complete. (Before scanning, we recommend you update the database to ensure any new malware variants are detected.)

After the scan has finished, the detected threats will be deleted from the computer. Reset the computer if prompted to do so.
