Glimtors.net is a harmful website that is typically accessed through other domains that advertise malicious content or advertisements.
Once permission is granted, it will show pop-up adverts to website visitors, frequently by redirecting them to other pages or using the notifications tab.
This type of rogue advertising is heavily used by many third parties to advertise their products and services online.
However, since it is very effective in having visibility, malicious hackers have also been known to use it for malicious purposes.
These advertisements can be obtrusive and disruptive to the user experience, and they may even direct users to dangerous websites or prompt the download of more malware.
In some circumstances, the malware may potentially steal personal data from users who accessed the malicious website.
How did Glimtors.net get on my device?
There are many different ways that these dangerous pop-ups and redirect viruses can infect both your browser and your computer. In the future, keep an eye out for the following causes:
- Getting an advertisement-supported software (adware) on your computer. You may have obtained it by torrenting or downloading software from unreliable sites.
- Have you checked your extensions? The malware may be hiding in your browser as a plugin. Review the information and browser access for each plugin. Get rid of it right away if it says "redirect searches to Yahoo" or something similar.
- Malicious software might also be installed if you click on a malicious button or link. If you recently visited a suspicious website, you should run a malware scan on your computer.
Given the possibility of additional malware infection, it shouldn't be left in the computer for an extended amount of time. No matter what is shown in the pop-ups or redirections, it is intrusive for them to have the ability to display unwanted adverts on a device.
More information on Glimtors.net
The procedure for obtaining permission to display alerts on a user's device is the same for common pop-up advertisements and redirection websites.
They are usually recognized for coming from malware-infected websites, adult websites, streaming websites, torrenting websites, and other disreputable sites.
Here are a few webpage messages that would lead to having Glimtors.net permission to show pop-up ads on the browser:
- Click allow to verify that you are not a robot
- Click Allow to receive notifications
- Click Allow to download your file
- You need to click Allow to continue
After users click to permit it to send them notifications, it will begin to display fraudulent adverts.
Since alerts appear roughly every few minutes, most users find them annoying, and their browsing experience suffers as a result.
Not to mention that several adverts from Glimtors.net would consume a lot of device resources, especially if they appear frequently.
Technical Details of the Threat:
| Domain Name | Glimtors.net |
| Threat Classification | Pop-up ads, Push Notification, Advertisements, Redirect Chain, Redirections |
| Symptoms |
|
| Common Advertisements | Dating websites, Tech support scams, Drive-by Download Malware, Survey giveaway websites, Fake virus alert webpages |
| Best Technical Solution | Removing Unwanted Notification Permission in Settings & Scanning with powerful antivirus software. |
Glimtors.net Contents and Redirection
Malicious pop-up ads and redirection chain malware infections can cause a browser to be sent to several different websites.
However, it's crucial to remember that the majority of the websites it refers to are malicious and could represent a serious risk to the browser and computer.
As a result of our research into Glimtors.net pop-up ads and redirects, we have provided a detailed removal guide for you if you have the aforementioned malware in your browser.
Glimtors.net Removal Procedure
The methods provided below are intended to help you remove any potential malware, trojans, rootkits, and viruses from the computer system, in addition to stopping the malicious Glimtors.net pop-ups and redirections.
We have inspected and confirmed that the provided steps are up-to-date and currently work efficiently.
Removing malware from the system and the browser should be thorough and carefully executed; therefore, please follow every step provided.
We made the instructions below easy to understand so non-tech-savvy users can still remove the browser threat without needing help from tech support or a computer technician.
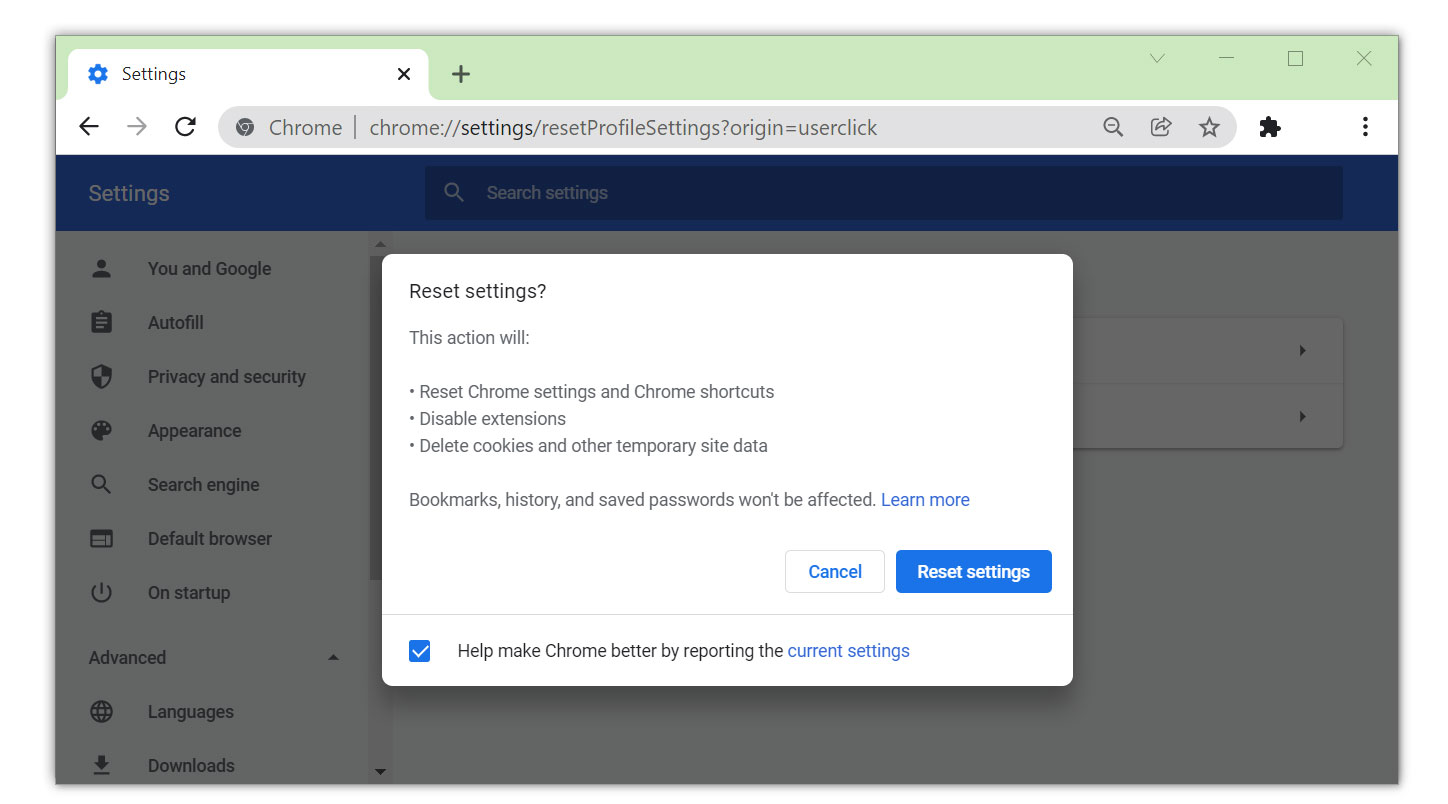
Step 1: Reset the browser to its default settings
Resetting the browser includes complete reversal and wiping out history, homepage settings, default search engines, and browser permissions, which may be used by malicious actors to show pop-ups and redirect the user to the Glimtors.net domain.
In addition, the browser reset does not include the favorites tabs, bookmarks, or saved passwords in some cases. To reset your browser to its default settings, please follow the steps below for the browser you are using.

Google Chrome
1. Open the Google Chrome browser and click the three dots in the upper-right corner of your screen to access the drop-down menu.
2. From the menu presented, select the Settings button, then click the Advanced menu on the left side of the screen from the settings.
3. On the drop-down menu presented on the screen, select Reset and Clean up.
4. Click on the Restore settings to their original defaults.
5. Then a small confirmation window will appear; click the Reset Settings.

Mozilla Firefox
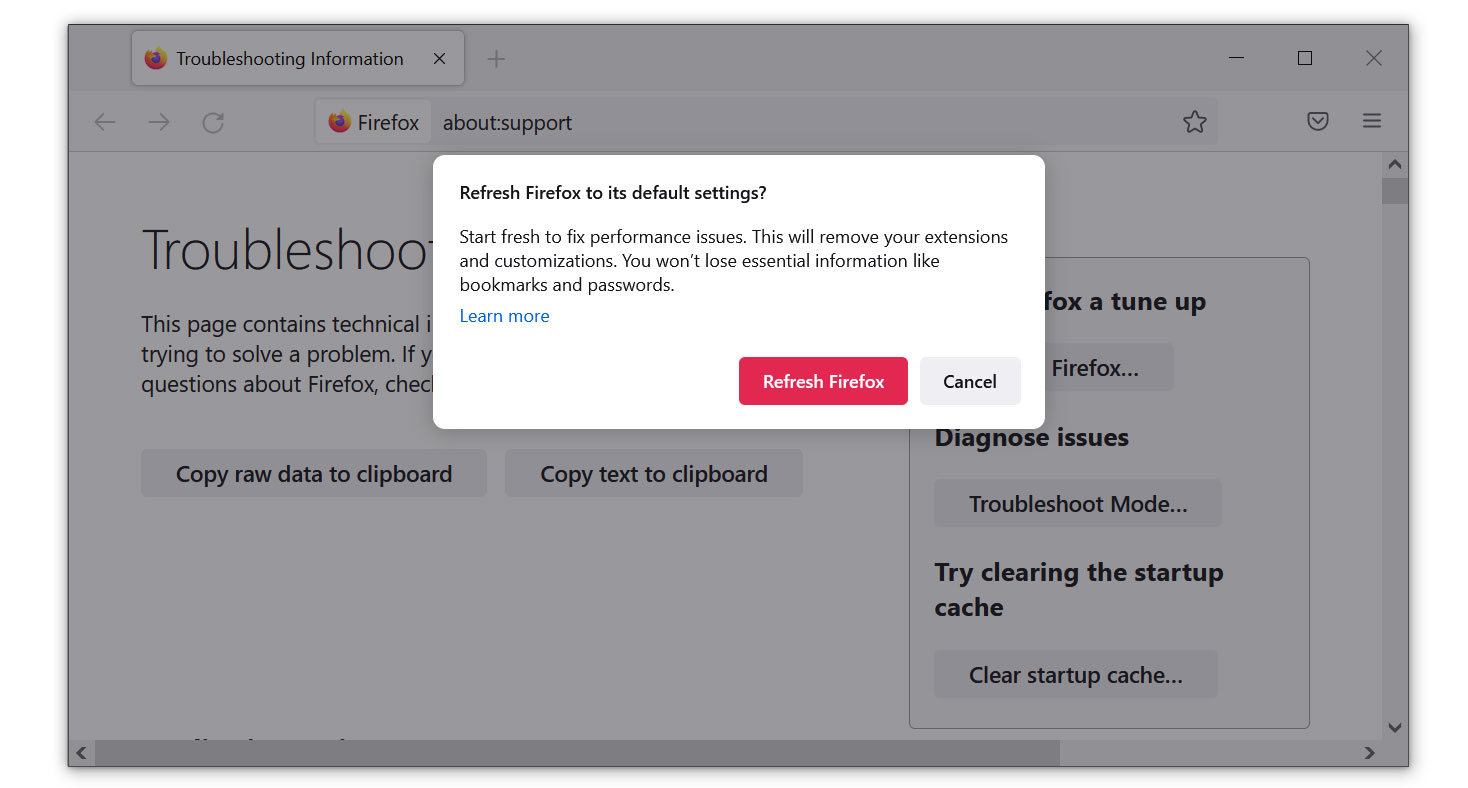
1. Launch the Mozilla Firefox browser, then open the menu by clicking on the three horizontal lines located in the upper-right corner.
2. Navigate down and click Help, then select More Troubleshooting Information from the options given.
3. Select the Refresh Firefox button. Then click Refresh Firefox on the confirmation window that appears.

Microsoft Edge
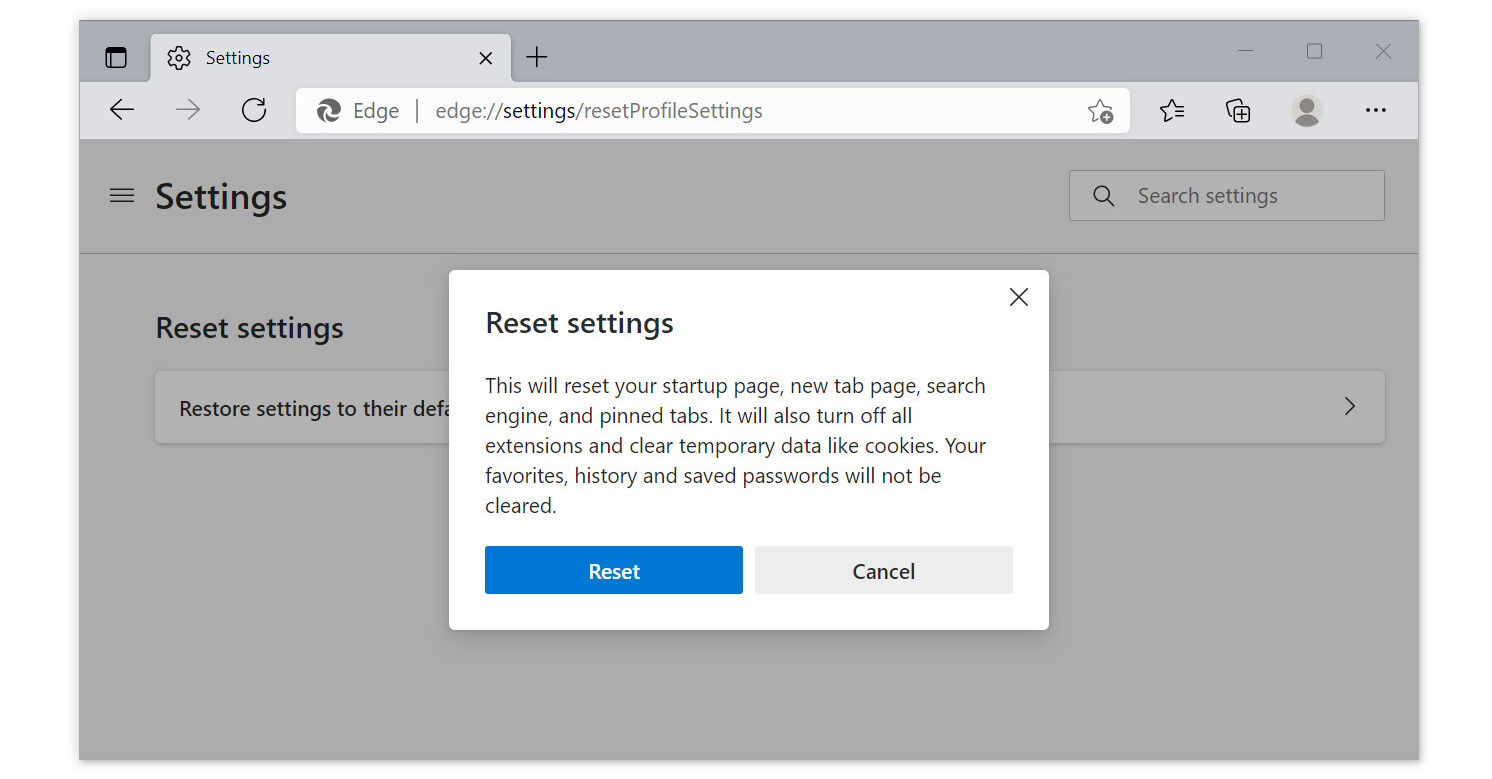
1. Run Microsoft Edge on the computer and click the three-dot icon in the upper-right corner.
2. Click on the Settings button from the drop-down menu.
3. Find and click Reset Settings from the left sidebar. Then click on the option Restore settings to their default values.
4. A warning window will appear, telling you that you are about to reset the browser. Click Reset, and the browser should return to its default settings.
The configurations added by adware and browser hijackers have all been removed, and your browser has now been entirely reset to the settings it had when you initially installed it. You can use your browser with complete security now. Rest assured that pop-ups from Glimtors.net as well as the redirections won't appear again.
Now that the redirects have been removed, our attention will turn to removing any malware that may have been installed on the computer while the redirections were active.
Step 2: Uninstall unwanted programs from the computer
Adware, often known as advertisement-supported software, is the main culprit behind most browser-related issues which can include the Glimtors.net virus. If the redirections persist even after the browser has been reset, the adware may have been installed on the system.
Many users may not know this, but adware can automatically configure the browser to show pop-ups and redirect web pages. When it detects that users have removed the current configuration, it will immediately replace it again without requesting the users' consent.
Additionally, malware can also be implemented through these redirections, which is why it's crucial to verify the applications that are already installed on your computer to determine whether any malware has possibly been installed.
How will I know what to uninstall?
Giving the exact name of the malicious program may be complicated, but there are ways to make it easier to detect it. One of which is to simply remove all unknown programs you do not recognize or think you have not installed. You may have applications that you don't even know the use for; that is a sign that they can be malware.
Unless it is a system process, which you can see by checking the developer of the application, some trojan viruses also use recognized and legitimate names to obfuscate their programs. If the publisher name or source of the program is unknown to you, it is best to uninstall it.
Another thing to do is to look at the version number; the majority of adware and dangerous programs will have version 1.0 because they don't need to be updated and are merely running as background applications.
To remove malicious programs from your computer, we have provided two ways to do so: one is through normal uninstallation, and if that does not work, we also provide an advanced uninstall method to make sure it will be removed without issues.
Remove software via the Control Panel
The most common way to remove malware from your computer is to uninstall the program through the Control Panel. You may view all of your installed apps as well as the developer's name in the list of applications.
You can eventually remove the cause of Glimtors.net malware and other adware-related browser troubles by uninstalling the programs you do not recognize.
1. From the Windows search bar at the bottom of your screen, search for Control Panel and click the result that matches the same application.
2. You will see different options, such as System and Security, as well as User Accounts. But what you want to click is the Uninstall a program under the Programs section. Depending on your Windows version, hovering over the uninstall section will be relatively the same.
3. Now that you are on the Programs and Features page, it will show you all the installed programs. There will be filters you may want to use, such as viewing them in lists with details such as the publisher, version number, and when they were installed.
4. Right-click the suspected virus program and click Uninstall to get rid of it (We will be using Adaware as an example). It will then proceed to remove the application, or you will be presented with an uninstaller that will guide you to remove it; either way, it will be removed.
There is a chance that the program may not be uninstalled successfully, and when that happens, it is important to use the power of an uninstaller program such as Revo Uninstaller.
It is widely known to be enough to remove malicious programs that are evading uninstallation. If you encounter such an issue when proceeding to uninstall the app, you may utilize the uninstaller to do the job for you.
Remove malicious programs via Revo Uninstaller
For computer users who are not sure of what to do. You may resort to using Revo Uninstaller since it is much more effective and easy to use. Revo Uninstaller is a handy tool for Windows users.
This uninstaller not only removes programs from the computer but also deletes their changes from the Windows Registry, Host File, etc. The steps below will guide you on how to install and use Revo Uninstaller to get rid of the source of Glimtors.net pop-ups and redirects.
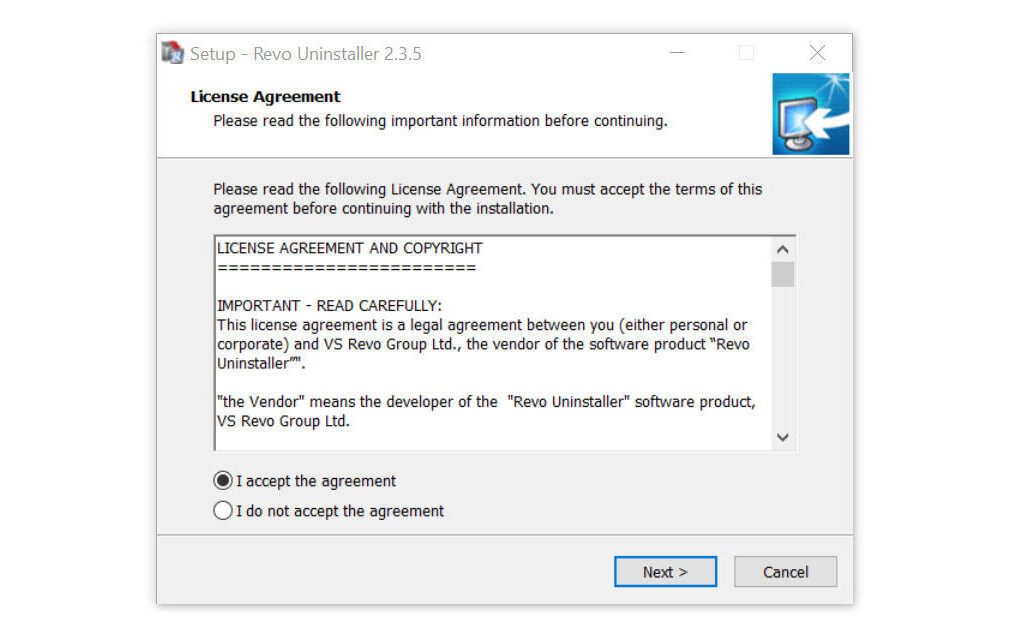
1. Click the button below to proceed with installing Revo Uninstaller on your computer since we have made an in-depth guide on how to use it on the following page. On the other hand, you can also head over to Revouninstaller.com and download it from there.
2. After the setup file (revosetup.exe) has finished downloading, run the installation wizard, read the license agreement, and click agree to proceed to the next step of the installation. Follow the procedure and wait until the installation of the software is complete.
 3. Once the software has launched, find the unwanted application that needs to be removed and double-click the program to uninstall it. (We will be using the Mozilla Firefox browser as a demonstration.)
3. Once the software has launched, find the unwanted application that needs to be removed and double-click the program to uninstall it. (We will be using the Mozilla Firefox browser as a demonstration.)
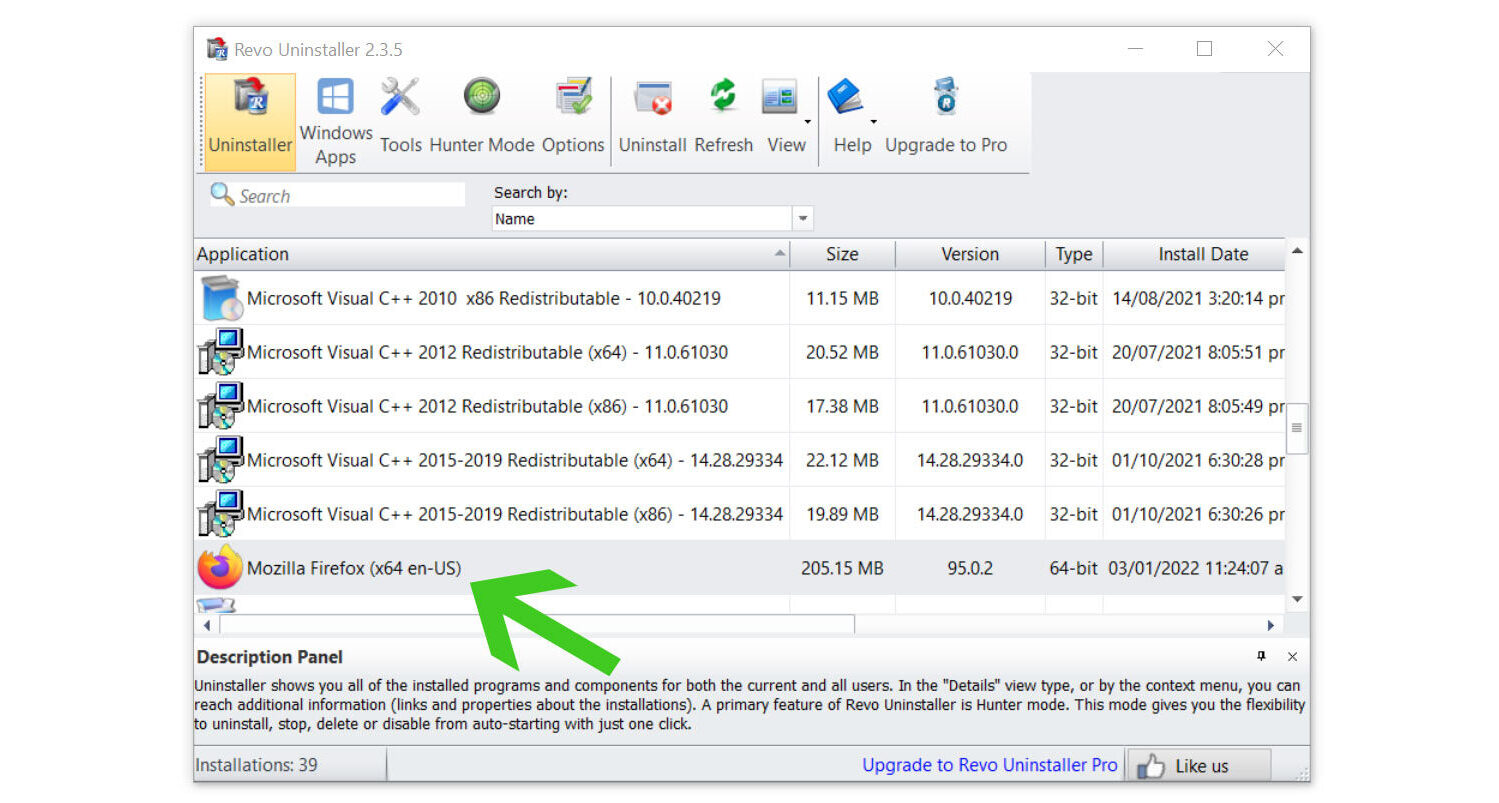
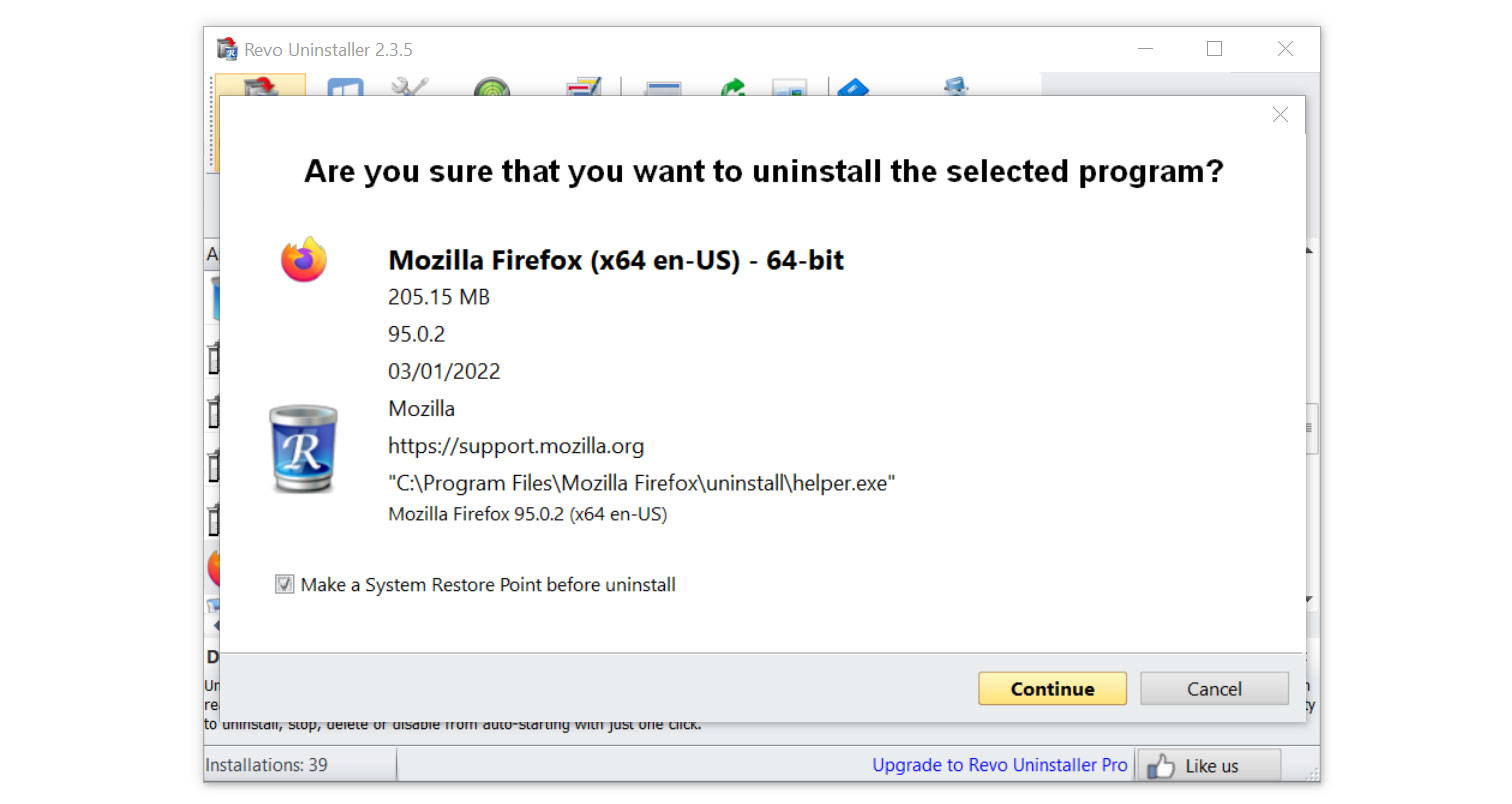
4. Click on the Continue button and follow the procedure to start uninstalling the program. It is also advised to make sure that a System Restore Point is made before the uninstallation, just in case.
5. You will be prompted to choose a scanning mode. From the three options available, select Advanced mode, then click Scan.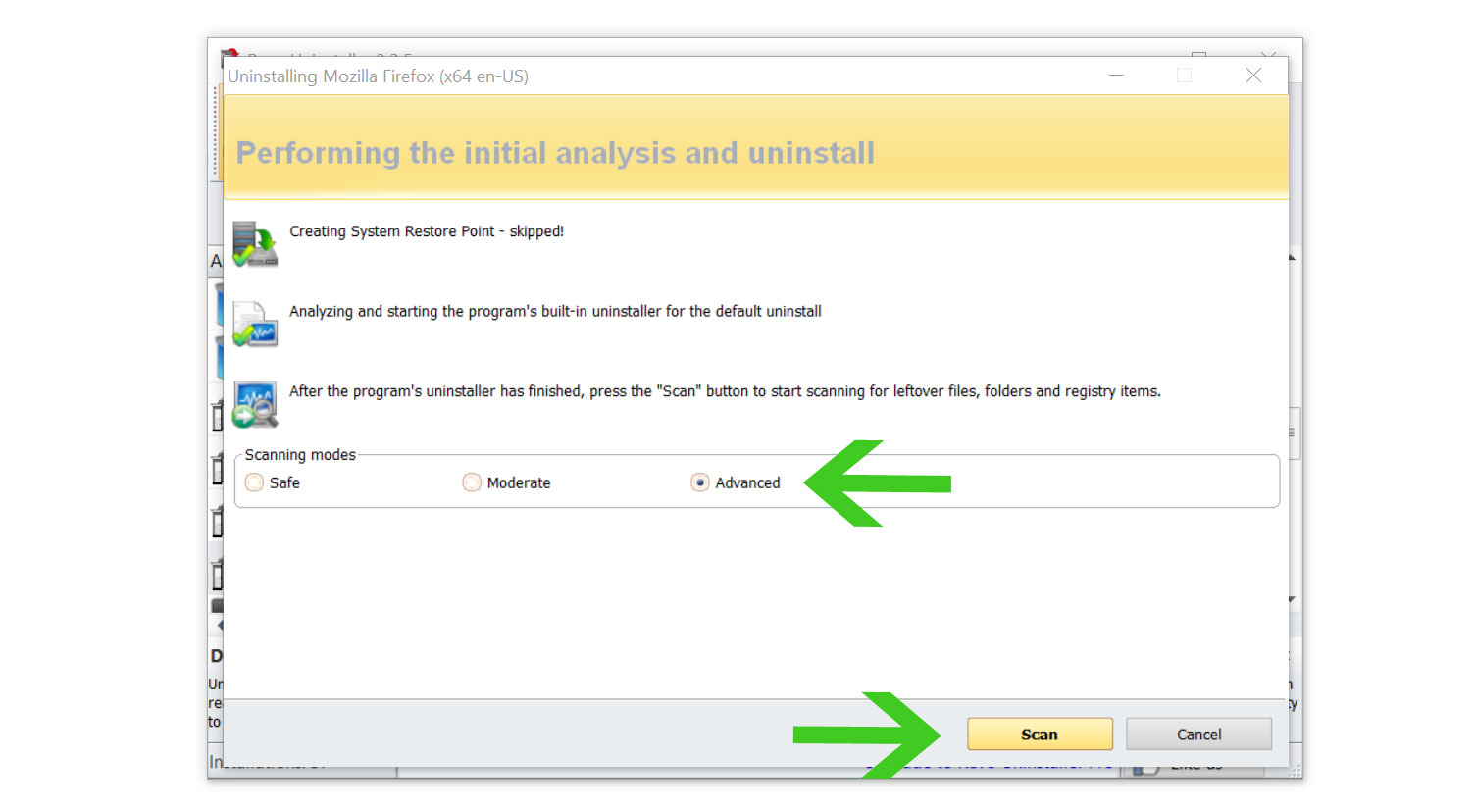 6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
6. A window will pop up and show all of the leftovers and changes made by the uninstalled program. Click the Select All button and hit Delete to remove the leftovers found in the Windows Registry.
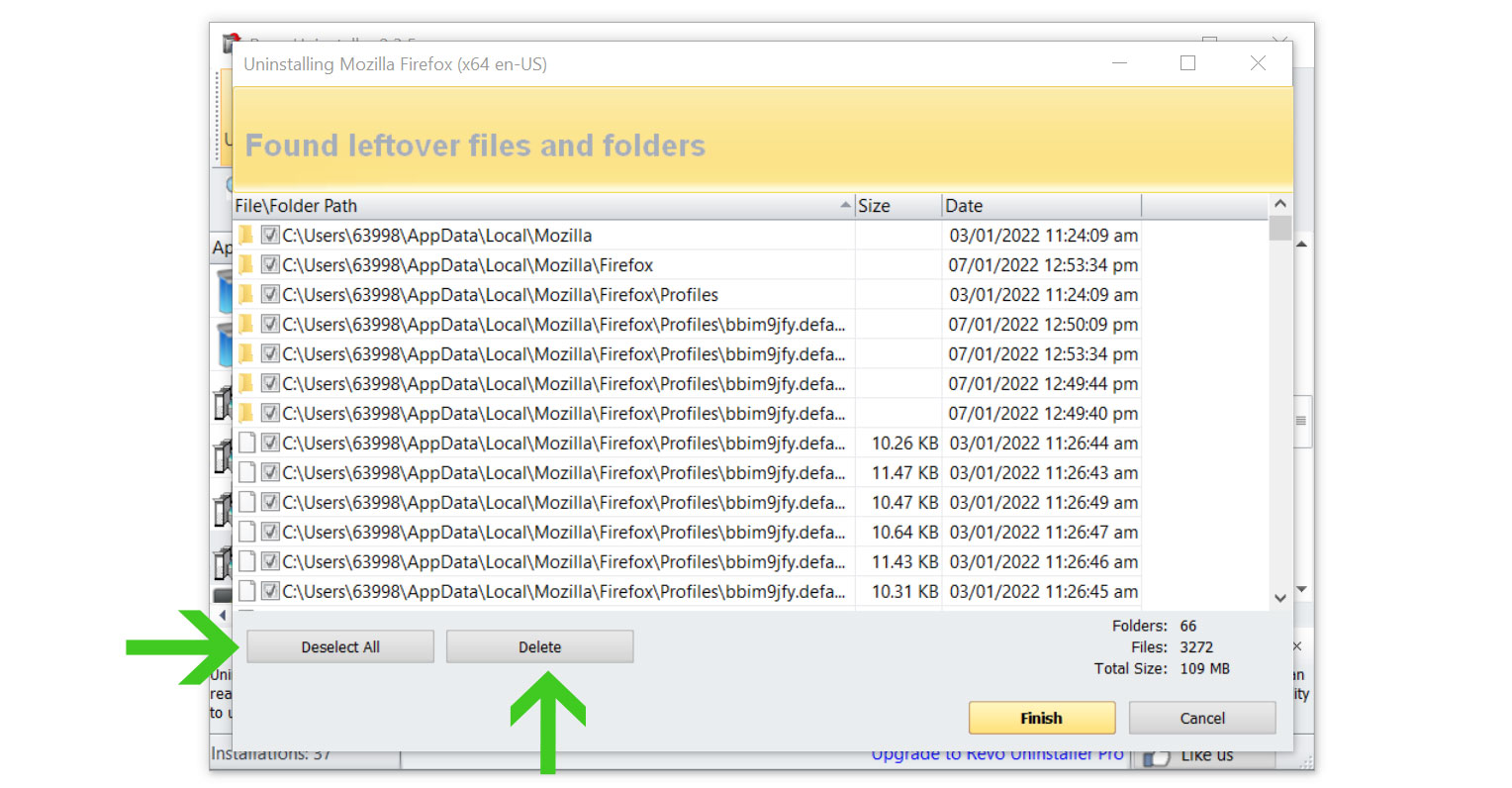
Once the window closes, you have successfully removed the malware threat from your system. We believe with absolute certainty that once the malicious program has been removed, the Glimtors.net browser issue will now be fixed, and you can continue browsing the web without being redirected to unknown sites.
Step 3: Scan with powerful malware removal software
Glimtors.net pop-ups and redirects may seem to only affect the browser, but leaving them there makes the symptoms worse.
Highly damaging malware could have been installed on the computer. They can conceal themselves within the system files and registry, making them resistant to browser reset and software uninstallation.
For these virus threats, we recommend running a full system malware scan with Malwarebytes Anti-Malware. This program is widely known and recognized by security experts when it comes to removing viruses from the system.
Remove Glimtors.net with Malwarebytes Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common browser threats as shown from our tests with the software, and we assure you that it can remove Glimtors.net as well as other malware hiding on your computer.
Not to mention, it is free to use and does not come at any cost to remove the viruses it finds on your computer.
To use Malwarebytes and remove malicious threats from the computer, follow the steps below:
1. Download Malwarebytes by clicking the button below, as we have made an additional and in-depth tutorial on how to use it. Otherwise, you may go to their official website via Malwarebytes.com (Avoid misspelling as it may lead to scams).
Download Malwarebytes Anti-Malware
2. Visit their download section and start a Free Download to begin installing the software on your computer.
3. Once the Malwarebytes setup file (MBsetup.exe) has finished downloading, open the executable file in File Explorer, then right-click the setup and select run as administrator to give the highest system authority and make sure Malwarebytes is installed correctly.
4. Make sure to carefully follow the installation setup wizard's instructions and provide the relevant information it requires. You will be prompted with questions such as Personal or Business Use, Email Address, and others.
5. From the application's home screen, go to the scan tab and begin running a system scan. This will scan the whole computer, including memory, startup items, the registry, and the file system. This is done so that not only Glimtors.net but also other trojan viruses hiding in the system can be detected.
6. Since it can take a while, you should either relax and wait for it to finish or find something else to do. The length of the scan depends on the size of the files you have and the hardware capabilities of your computer. Here are some ways to make scanning faster.
7. Once the scan is finished, Malwarebytes will show the malicious viruses and threats it found on your PC. Glimtors.net will also show up on the detection results, and it will be given a threat name such as PUP.Optional.Wave, and many more.
8. Select all the detected files from the report and click the quarantine button to remove the malicious items from the computer into the protected safe quarantine zone of the anti-malware program so that they would not affect and do malicious actions to the PC again.
9. After placing the virus files in the program’s quarantine, it may prompt you to restart the computer to finalize the full system scan procedure. Please restart your computer if prompted, as it is essential. After the restart, Malwarebytes will open and display a message that the scan was complete.
Note: Don't forget to delete the quarantined files afterward.
Simply quarantining the malware files is not enough to make sure they are completely removed. This is a very common misconception: once you click the quarantine button, it is all good and gone.
But, while its effects and harmful activities are halted, the malware is still in the system, only placed in the anti-malware program's quarantine folders. To completely remove it from the computer, go to Detection History from the home screen, select all Quarantined items, and click Delete.
You have successfully removed Glimtors.net as well as the hidden threats on your computer. Rest assured they would not resurface again since Malwarebytes offers a premium trial for 14 days, so you could take advantage of it for free and prevent malware from infecting your system.
While the detection and removal of malware is free for Malwarebytes, the premium versions include real-time protection that ensures your computer is safe all the time. Although we encourage you to use the premium trial, you are free to purchase the full version if you find it useful.
The program is an anti-malware that removes harmful threats like trojan horses, worms, stealers, miners, keyloggers, and many other forms of malware and computer viruses.
For a better and safer web browsing experience, we've provided a few security measures and advice below that will safeguard your browser and computer from harmful threats like worms, malware, trojans, keyloggers, stealers, and other kinds of computer viruses that will harm user data.
Protective measures for better overall security
Removing trojan viruses and malware from the device is one thing; keeping it secure for the future and for a long period is a different thing and will require certain things to make sure you are secured, especially if you do not know most of the ins and outs of the device you are using.
Cybercriminals are always stepping up their game to make sure they infect users and extract data and money from them.
We encourage you to take the actions listed below to ensure complete security before leaving this page because we strongly promote web security and having a secure online presence.
Safeguard your privacy and data by using a VPN application
VPNs, also known as virtual private networks, guarantee your safety and complete anonymity while you browse the internet.
In contrast to a firewall, which monitors and blocks potentially harmful connections in the network, A VPN hides the user's connection via a tunnel so that it would appear to third parties as a different IP address and location.
This ensures that your data won't be leaked because the program hides it. Be aware that visiting infected websites may cause your IP address and location to be disclosed; however, if you use a VPN, this will prevent your true IP address from being revealed to malware actors.
Use an adblocker when browsing the internet
Installing an adblocker on the browser is the best way to get rid of unwanted redirects and pop-ups from Glimtors.net as well as other threats such as browser hijackers, and unwanted toolbars.
Additionally, by blocking malicious websites before users can even access them, it is possible to prevent malware from being downloaded.
In this case, we recommend uBlock Origin, which is an open-source AdBlock extension that comes at no cost and is free forever. It is one of the most reliable plugins out there, ensuring that every advertisement on a webpage will be blocked.

For Google Chrome
1. Go to the Chrome Web Store and search for the browser extension, or click here to go directly to the extension page.
2. Click the Add to Chrome button. Then click Add extension when the confirmation window appears.
3. uBlock Origin is now installed in Google Chrome. The adblocker is turned on by default; you can click the power button if you wish to turn it off for a while. The menu can be found by clicking the puzzle icon in the upper-right corner next to the search bar.

For Mozilla Firefox
1. Visit the Firefox Add-ons Store and search for uBlock Origin, or click here to automatically go to the extension's webpage.
2. Click Add to Firefox, and after that, a confirmation window will appear stating the permissions it will grant the addon. Finally, to add it to the browser, click Add.
3. Mozilla Firefox now has uBlock Origin installed. The adblocker is activated by default; if you want to disable it for some reason, simply click the power button. The menu can be found in the upper-right corner of the web browser, next to the search bar.

For Microsoft Edge
1. Go to the Edge Addon Store and search for the said browser extension. You can also click here to go directly to the plugin page of the Adblocker.
2. Click the Get button, and a confirmation window will appear. Continue installing the extension by selecting Add extension.
3. Now that uBlock Origin is installed on the browser, you can choose to disable the Adblocker by clicking the power button. The menu can be accessed by hovering over the extension's icon next to the search bar.
The majority of pop-up advertisements, whether they include malware or not, will be filtered by the extension and no longer be displayed to you. Currently, uBlock Origin is not available for Mac or iOS users, but there are plenty of free options on the market, such as AdBlock for Safari.
Utilize a firewall to prevent cyber attacks
A security firewall is required for every internet connection that is made. It is an essential tool that enhances security and stops online attacks. Through a security mechanism, it controls incoming and outgoing network connections on your system and network and filters the undesirable ones. Consider it a further barrier against malicious assaults and zero-day exploits.
Bottom Line
While this may appear to be typical advice, we recommend users not visit illegal streaming or torrenting websites and more importantly, do not download anything from them because doing so may result in the installation of malware and viruses.
Because these websites are illegal, they are unable to make a profit from legitimate advertising. As a result, they host questionable advertisements from unidentified marketers who want to publicize their content, which are most likely dangerous codes being propagated by cybercriminals.
Always make sure that your device is protected against sneaky exploits and stealthy cyberattacks. While taking precautions and avoiding dubious websites are crucial, having a solid line of defense is essential to ensuring the security of your network and data.
The threat posed by Glimtors.net is not the only one on the internet, and there are many more surfacing every day. We are glad to have assisted you in resolving your browser-related problem and are proud of our expertise in this area.
If you experience another virus attack on your device, please visit our website to find a malware removal solution for your problem or get in touch with us, and SecuredStatus will be happy to assist you once again.

